How to hack instagram acounts
How Instagram accounts get hacked: 6 tactics used by hackers
Every year, cybercriminals generate over $3 billion in revenue from social media attacks alone and hacking constitutes a large portion of these malicious incidents.
To help influencers and business owners protect their Instagram accounts, below we breakdown 6 tactics hackers use to extract personal information and bypass 2-factor authentication.
{{learn-more}}
How do Instagram accounts get hacked?
How do hackers hack Instagram accounts? There are default security features on Instagram, like 2-factor authentication, so how can hackers overcome these?
The general answer to that question is, in most cases, some form of social engineering.
In this context, social engineering refers to the act of manipulating and deceiving Instagram users into willingly providing confidential information.
1. False copyright infringement messages
The tactic
Instagram clearly states that you can only share original content that doesn’t violate copyright infringement laws. That said, it’s possible for you to commit a copyright violation unintentionally, in which case Instagram would take action and reach out to correct the problem.
This has led to many cybercriminals actually impersonating Instagram representatives pretending to address copyright infringement issues. In these cases, a hacker sends a link to your email or through a private message on Instagram and asks you to log in in order to address the issue. This is a real-life example of a message that was used to hack @wandertears:
You can learn more about this case by checking out this article.
The link leads to a fake page that, even though it mimics Instagram’s login page, is actually designed to collect your username and password details. The only difference between the real page and the fake is a small variation in the URL, which is hard to detect.
To avoid raising suspicion, cybercriminals usually redirect you to one of Instagram’s legitimate FAQ pages that discusses the topic of copyright infringement.
The solution
There’s a couple different methods you can use to verify the messages you receive from Instagram. First, urgent Instagram notifications are usually delivered directly through the account interface or via email. If you receive a DM about your account, it won’t be legitimate - even if it’s from a profile that has the name “Instagram” in the username.
Second, Instagram now allows you to see a record of all security and login emails through your account. If you receive a suspicious email directly to your inbox, you should check this part of your Instagram account before opening the message.
From your profile, go to Security>Emails from Instagram. If you don’t see a record of the email, you should delete it right away.
{{subscribe}}
2. Deceitful verified badge offers
The tactic
You’re probably familiar with verified badges, the blue pins at the top of Instagram profiles that have been authenticated by the social network. While valuable, this account feature is also at the center of another social engineering that hackers use to break into Instagram.
While valuable, this account feature is also at the center of another social engineering that hackers use to break into Instagram.
In this scenario, hackers send a private message or email that offers a chance to add a verified badge, linking to a deceitful website that collects your login information. They may request that you don’t change your profile data, like username or password, until the change has taken effect in order to gain enough time to break into your account.
Here’s an example of a verification badge scam email sent to the owners of pillow business, Cuddle Buddy.
The solution
There are a few tell-tell discrepancies here to help you avoid falling for such a scam. For starters, grammar mistakes like excessive capitalization should serve as a warning. Not only this, but the profile the message is being sent from does not belong to an official account nor does it have a verified account. It has the word “Instagram” in the name, but it doesn’t give any indication of being official. Finally, note how the “contact us” text on the blue button is not centered properly, so it’s not consistent with other Instagram content.
Finally, note how the “contact us” text on the blue button is not centered properly, so it’s not consistent with other Instagram content.
To get a blue verification badge right now you need to apply through your profile, and the form you have to fill in should look a little something like this:
3. Illegitimate suspicious activity alerts
The tactic
Hackers that employ social engineering attacks leverage every piece of information they have at their disposal. For example, they sometimes design suspicious activity alerts that look like a legitimate notification from Instagram, but actually contain malicious links.
The solution
According to the Meta-owned social platform, emails from Instagram only come from “@mail.instagram.com” or “@facebookmail.com” addresses. Here’s an example of what a legitimate security email from Instagram looks like:
This security message is for a new login from a device that the user didn’t commonly sign in through. Note how the email address is from a trusted source and how all of the design elements are aligned properly.
Note how the email address is from a trusted source and how all of the design elements are aligned properly.
Even if the emails you receive look legitimate, we advise that you go to your Instagram account and verify that the security email was sent through there.
4. Fraudulent giveaways and brand sponsorships
The tactic
Fraudulent giveaways are especially troublesome because they exist in an ecosystem that is packed with legitimate promotional freebies. This form of social engineering can take two different shapes.
In its most traditional version, this type of hack operates like a false verified badge attack. The difference is that the hacker impersonates a big brand, exciting start-up, or similar renowned company that’s offering a big giveaway to specific social media influencers.
Some scammers even have legitimate-looking accounts that have been active for a while and have thousands of followers. The first message usually includes at least one spoofed link leading to a false Instagram login that’s designed to extract the username and password submitted.
A more complex form of fraudulent giveaways and sponsorships can occur when hackers have collected information about you, but still need a few more details to successfully breach your account. Instead of sending you a link to a spoofed login page, hackers may ask you to fill in a survey that asks for personal information, like your date of birth, mother’s maiden name, and other answers to common security questions.
Below is a real example of the phishing email that led to @FlipFlopWanderers getting hacked. Read their full story here.
The solution
Never rush or feel pressured into clicking links. Take time to investigate if the email looks legitimate: for instance, check for spelling mistakes and hover over the hyperlink to see if the URL leads to a familiar or safe website. To be extra safe, you could even Google the company supposedly sending the email, and contact them to check if they really did send you an email.
5. Counterfeit social media tools
The tactic
Managing a social media profile can take a huge amount of time, especially if you have a large base of followers. There are many tools that can simplify the process, but you also have to evaluate each platform to make sure it comes from a legitimate developer.
There are many tools that can simplify the process, but you also have to evaluate each platform to make sure it comes from a legitimate developer.
Just as with malicious web extensions, hackers can create counterfeit tools that are supposed to improve functionality, but actually pose a security threat.
These tools usually look and feel legitimate, but bring you very little in terms of functionality and practical value. This type of scheme is not as common because it requires a significant amount of resources, but it’s still used by cybercriminals looking for bigger, more valuable targets.
When this type of attack is successful, target users integrate the counterfeit tool into their social media accounts. This fake tool can be used to set up man-in-the-middle attacks, intercept all data, and extract login details, among other data.
The solution
It’s normal to watch your budget, especially in the early stages of your Instagram account. But, working with lesser-known, low-cost tools increases the chances of being targeted by scammers. To avoid this, you should opt for established tools that come from renowned providers or platforms that have been recommended by trusted peers.
To avoid this, you should opt for established tools that come from renowned providers or platforms that have been recommended by trusted peers.
6. Reverse proxy attacks
The tactic
All of the social engineering hacking techniques we’ve covered so far require hackers to manually create fake apps and website pages in order to collect details from their targets. With reverse proxy attacks, hackers don’t need to create a spoof website or app - instead they can automate the theft of credentials.
A reverse proxy attack is a type of man-in-the-middle approach - hackers direct victims to a domain that sits in between the user and the legitimate website. The URL will be very similar to the legitimate page, and the overall appearance in the malicious domain mirrors the legitimate page.
When applied to the Instagram context, you could receive a convincing email from a hacker that directs you to Instagram’s login page. What you don’t realize is that you’ve been sent to do this via a proxy server - so when you enter your credentials and log into Instagram, your information - including 2FA - is being intercepted in real time.
The solution
Be extremely cautious when clicking on links from your email inbox - always verify an email claiming to be from Instagram by checking your Instagram account. From your profile, go to Security>Emails - if the email doesn’t appear there, it’s likely a scam.
What Do Hackers Do After Hacking Your Account?
Now that we’ve answered the question “how do hackers steal Instagram accounts?” let's go over the reasons why these criminals may want to target your profile.
Like other types of criminals, hackers and other malicious actors flock to the most popular platforms because these present the biggest financial opportunities. Today, you can generate a significant amount of revenue from a large base of followers and hackers are eager to benefit from this.
Some of the common things a hacker may do once your account is breached include:
- Demand a ransom
- Scam your friends, family members, and customers. Investment, Bitcoin, and Romance scams are some of the most common.

- Sell your account on the dark web
- Use your account to run a fraudulent operation
- Make various types of illegal requests, like requesting lewd photos
Looking for the Best Way to Protect Your Account?
Hackers use a wide range of approaches and develop new techniques regularly to bypass Instagram’s default security measures. The number of social media scam victims in the US skyrocketed from 46,000 to 95,000 in 2021, and that number shows no signs of slowing down in the near future.
Learning about the different techniques that hackers use and implementing security best practices as a counter are the first steps to keeping your Instagram account safe. Unfortunately, however, there is no way to guarantee your account against hacks - even users with multi factor authentication set up are falling victim. That's why we launched Notch - to finally give creators peace of mind.
{{learn-more}}
What happens with a hacked Instagram account – and how to recover it
Had your Instagram account stolen? Don’t panic – here’s how to get your account back and how to avoid getting hacked (again)
A friend – let’s call her Ellie – recently called me with a devastated tone in her voice. Her Instagram account had been hacked and she was locked out. Her panic was evident as she told me her password had been changed and that the hackers had added two-factor authentication (2FA) to the account.
Her Instagram account had been hacked and she was locked out. Her panic was evident as she told me her password had been changed and that the hackers had added two-factor authentication (2FA) to the account.
She went on to ask me if I knew of any tips to regain control. I had heard of both good and bad outcomes in similar situations, online, but I had never attempted it first-hand. If I’m honest, I was actually a little excited at the opportunity to test Instagram’s recovery methods to see if I could learn anything.
Ellie is quite computer savvy and understands technology; however, she is also very busy with her small business and young children. As a result, she has simply “put off” adding extra security layers to her social media and email accounts. At any rate, when she called, I refrained from “I told you so!” and asked her what had happened.
How things went wrong
Ellie’s first mistake was that she had used a relatively simple password on the account and had reused it on other accounts, so this password was either compromised or attacked via brute force to gain illicit entry.
Her second mistake was that her account was not to set up 2FA, which is free and easy to implement in all social media and email accounts. With this turned on, the hackers would have simply been turned away – even with entering the right password or clicking on the “forgotten password” link (a hacker’s favorite starting block!).
Once into her account, they started the process of locking Ellie out by changing the password, adding 2FA to a Nigerian phone number and a different email address. Also, they added an authenticator app. Additionally, they even added some numbers to the end of the Instagram username, which, at first, I could not work out why. This is presumably done so Ellie would not simply be able to regain control from her phone, should she get that far.
Once they had locked Ellie out, they started the next level of sideways attacks by sending messages to her Instagram friends, presumably to target their accounts and get their 2FA codes and multiply the hack. Luckily, no one else divulged the code but a few were immediately taken in by the messages.
Luckily, no one else divulged the code but a few were immediately taken in by the messages.
The long road to (account) recovery
When Ellie tried to recover her account, she felt like she was at a dead end – even after following the steps on the Instagram help site, she felt stuck. When she requested a login link from Instagram to be sent to her primary email address, nothing genuine came through even though she could still access this account. (You will, of course, need access to the email address connected to your account. If for any reason you cannot access this email account, Instagram will not let you regain access to your Instagram profile.]
I had remembered that hackers can often get into the associated emails via the same reused passcode, and then hide or block recovery emails sent from Instagram regarding the hacked accounts.
To my (relative) shock, this was exactly what had happened. In her Yahoo account, she clicked on the “Blocked List” and three email addresses ending in mail. instagram.com had been blocked.
instagram.com had been blocked.
Once unblocked, she followed the process again and Instagram sent another login link. She was then asked to submit a video selfie to help verify her identity (this was only possible as she has photos of herself on the account).
RELATED READING: Attack of the Instagram clones
Within 20 minutes, she received an email saying that she had now been granted access back into the account and given a small number of one-time recovery codes to use. We both thought we were on the road to victory!
But it was short-lived.
Although Ellie did regain access to the account by following the genuine link and typing in a backup code, the strangest thing is that she was instantly booted straight back out on entry. She retried this process five more times and this frustrating cycle reoccurred. She panicked, as she was only given six backup codes to use. To get more codes, she had to prove her identity again via the video selfie process … which did not work the next time, but after another attempt she passed and was given six more codes.
Interestingly, however, Ellie’s email address started receiving emails purporting to be from Instagram but the grammar errors and strange requests for security codes looked phishy and, luckily, she ignored them. Presumably they could have locked her out of this account, but they wanted to keep her in to potentially hand over the One Time Passcodes (OTPs).
I wondered if there could be a problem with her geo- or network location, or device, potentially banning her from entering the account, so I asked her to send the recovery email to my email address for me to try from my laptop at a location five miles away.
I attempted the process on my laptop and much to her disbelief, I got in straight away and stayed in! Success! Ellie was overjoyed, but before I took a moment to work out why this attempt had worked, I decided to secure the account once and for all.
I turned off the newly assigned 2FA app and the Nigerian phone number the hackers had changed it to; then, I changed the associated phone number to Ellie’s and then turned 2FA back on. I went on to change the password and used a 2FA code sent to her phone via SMS to prove she was now the secure owner of the account.
I went on to change the password and used a 2FA code sent to her phone via SMS to prove she was now the secure owner of the account.
Another thing the bad guys did was change Ellie’s username. This is presumably because when you log back into Instagram from your phone after logging out, it locks the login screen to the previous username and not an email address, making re-entry very tough unless it is still the original username tied to the app. To get Ellie back in, I had to change it back to her original username.
While in her account, I visited her “Login Activity” and it asked me if my current login location was “me”. I clicked “yes” and it stored this location.
My presumption on how she was instantly being booted out of the account is one of two possibilities. Firstly, they had potentially looked at recent login activity and struck off those locations, making Instagram think her home Wi-Fi was in fact a hacker’s location.
Or secondly, the hackers were still in the account and every time Ellie attempted to use the backup codes, they were notified and used their associated 2FA to change the password once again before she could press on any further. Either way, using another IP address from a laptop and navigating the site quickly worked.
Either way, using another IP address from a laptop and navigating the site quickly worked.
Once she was back in, Ellie had a lot of replying to do with all the messaging that the hackers had done.
Fascinatingly, anyone who replied stating they thought Ellie’s account had been hacked, or mentioned on their own stories that Ellie’s account had been hacked, had been blocked by the hackers too!
Luckily, the whole process only took three days but it definitely felt longer for Ellie. She is back in now and after nearly giving up, she mentioned that she has learnt about account protection the hard way. And I will leave it in her words: “I wish I had followed this simple security advice beforehand”.
Recovery process on a compromised Instagram account
- Head to your email account and make sure any email addresses from Instagram do not feature in your blocked list.
- Visit Instagram’s Password Reset page for a login link.
- Follow the on-screen prompts to this Help page and submit a support request to verify your identity. You will be asked to record a video selfie, but the next step will only work if your account already contains photos of you. The recovery link will be sent to your original email address.
- If this does not work, try it again until it verifies you.
- When successful, you will receive an eight-digit code that will be required after clicking on the link sent from Instagram.
- Log into the account on a computer using an IP address not used before with the account.
- Once in, immediately revoke any wrong 2FA implementation.
- Change the password to something strong and unique and not related to you.
- Change the phone number back to yours.
- Turn 2FA back on.
- Consider using a 2FA authenticator app instead of SMS-based 2FA.
- Change the username back on the laptop before re-entering from your phone.
- Finally, check your blocked list in your Instagram account.
 The hackers may have placed some close friends of yours in there.
The hackers may have placed some close friends of yours in there.
Prevention tips for securing an Instagram account
- Use a strong and unique password on Instagram and never reuse it anywhere else.
- Turn on 2FA, both on your Instagram account and on your email account.
- Watch out for phishing emails purporting to be from Instagram.
- Beware of any Instagram messages that start with something like, “Hi, I need your help”, and call your contact to make them aware of the potential compromise.
- Have at least one photo of your face on your account so the video selfie process will work if needed.
Newsletter
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on.
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password.
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It's possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings.
 This will reset the access tokens.
This will reset the access tokens. - Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them. If they managed to do this, change it back to yours.
- Set a new password that is strong and one that you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress.
Tips
Fake financial regulators
In emails, scammers pretend to be representatives of government agencies in order to swindle users of their personal data and money.
Air sellers in online stores
We tell how scammers deceive users of a well-known marketplace using a fake payment page for goods.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site. I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
Hacking Instagram accounts through copyright infringement notices
Got a few thousand followers on Instagram? Even more? Congratulations! You are a real celebrity! But in addition to laurels, well-known Insta bloggers have a greater risk of account theft. Not so long ago, scammers invented a new scheme to hijack popular Instagram accounts. We will tell about it now.
"Your account will be permanently deleted due to copyright infringement," the email reads.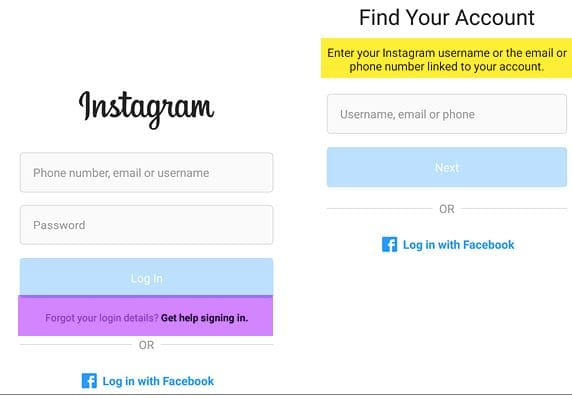 It looks quite official: here you have both the official header and the Instagram logo, and the sender’s address is very similar to the real one – in most cases it is [email protected] or [email protected].
It looks quite official: here you have both the official header and the Instagram logo, and the sender’s address is very similar to the real one – in most cases it is [email protected] or [email protected].
The notice says you have only 24 hours (48 hours in some versions) to file your appeal. In the letter itself, you will also find a button for appealing the complaint - Review complaint. If you click it, you will be taken to an extremely believable phishing page.
This page tells you how much the service cares about copyright protection. But the most important thing is that there is a link on the page, according to which you can allegedly appeal the deletion of your account. To make everything look even more natural, the page has a long list of language choices, but it's there only for show - whatever you choose, the page is displayed exclusively in English.
After clicking on the account deletion appeal link, you will be prompted to enter your Instagram account information.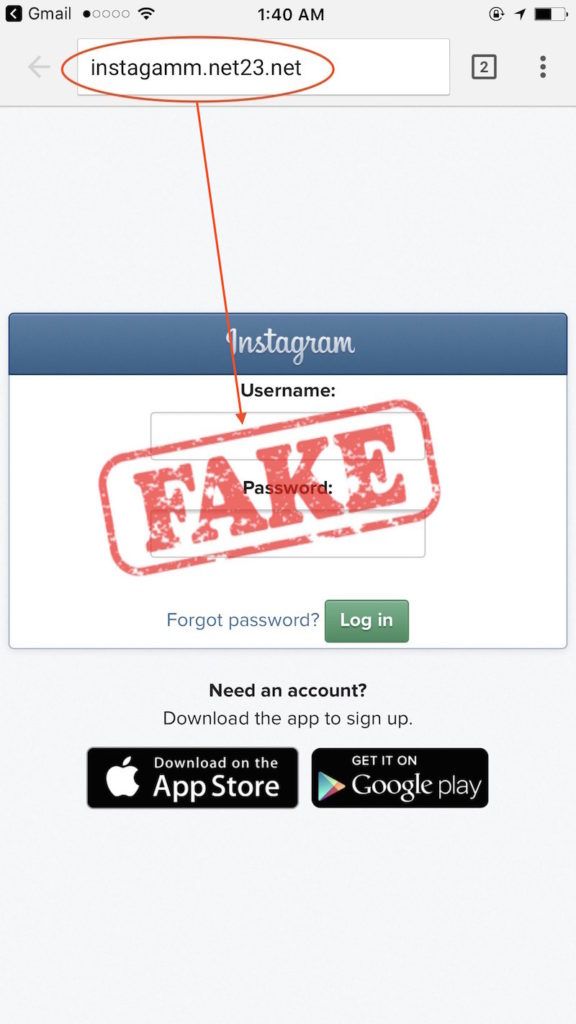 But that's not all - then a new message appears: "We need to authenticate your application and make sure that the email address matches the one specified in Instagram." If you agree to address verification, a list of possible domains will appear on the screen. Selecting one of them, you will see a prompt to enter an email address and (suddenly!) password from it.
But that's not all - then a new message appears: "We need to authenticate your application and make sure that the email address matches the one specified in Instagram." If you agree to address verification, a list of possible domains will appear on the screen. Selecting one of them, you will see a prompt to enter an email address and (suddenly!) password from it.
You will then see a message for just a few seconds that your request is being processed, after which you will be redirected to the real Instagram site. This is another trick that adds credibility to the scam.
This is not the first time popular Instagram users have been targeted by scammers. Recently, a wave of thefts took place under the pretext of obtaining a blue checkmark - a verification badge (Verified Badge).
How to protect your Instagram account
As soon as your username and password are in the hands of attackers, they will gain access to your Instagram profile and be able to change data to recover it. They can then demand a ransom to get the account back, or start sending spam and other malicious content from it. Not to mention what "open spaces" in front of them will open the password from your email.
They can then demand a ransom to get the account back, or start sending spam and other malicious content from it. Not to mention what "open spaces" in front of them will open the password from your email.
Here are some tips to help keep your Instagram account safe:
- Don't click on suspicious links.
- Always check the URL in the address bar. If instead of Instagram.com something like 1stogram.com or instagram.security-settings.com is written there, in no case do not enter any personal data and generally close the page as soon as possible.
- Only use the official social network app installed from the official app store (eg Google Play for Android or App Store for iOS).
- Do not enter your Instagram account information to sign in to other services and applications.
- Turn on two-factor authentication in your Instagram and email service settings.
- Use reliable protection that will filter out suspicious emails and prevent you from opening phishing pages.