How to hack my wifes whatsapp
10 Best Ways to Hack a Whatsapp Account
How Can Hackers Infiltrate Whatsapp Accounts
10 WAYS HOW TO HACK A WHATSAPP ACCOUNT
INTRODUCTION
We all know how this starts, from the beginning of course. Let’s learn how to hack a Whatsapp account. Whatsapp is a cross-platform instant messaging application that allows users to chat, text, share media, for instance, videos and voice messages with individuals or groups. Since its launch in 2009, it has quickly become the most globally popular messaging app with over 1.5 billion monthly active users. The app was created by Brian Acton and Jan Kuom, however, it is presently owned by Facebook.
NB: Learning how to hack a Whatsapp Account is purely for educational purposes.
For more information visit us at https://www.hannibalhackers.su. Contact us at [email protected].
Features of Whatsapp
· Uses an Internet connection to send messages or texts
· Media can be shared between individuals and group chats
· Free voice and video calls
· Users can seamlessly sync their chats to their computers, iPad or Android tablets with Whatsapp Web
· Users may record voice messages
· Users can send documents, spreadsheets, and slideshows without the hustle of file-sharing apps or emails.
· Messages and calls are encrypted
· Built-in camera for capturing memorable moments
· Users can share their location in real-time.
First-time users create an account using their email address and phone number for verification.
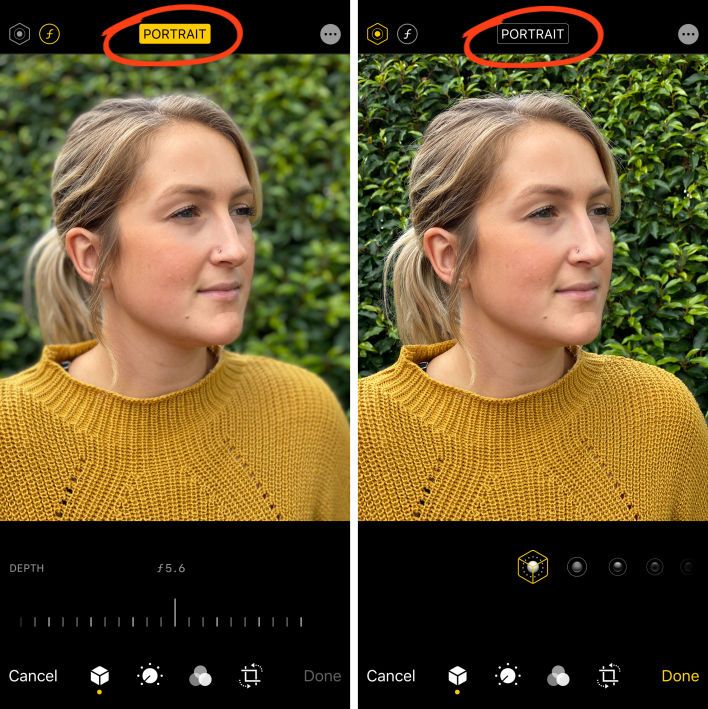
How Secure is Whatsapp? How to Hack a Whatsapp Account.
In light of the end-to-end encryption provided by the app, chats and calls are encrypted ensuring that no third parties can read the messages or listen to them. This is because the messages are secured with a lock, thus only you and the recipient have the special key needed to read and unlock them. Not to mention, this happens automatically meaning there’s no need to turn on the settings or set up secret chats. Additionally, one can turn on the two-factor authentication which adds an additional layer of security making it harder for an attacker to gain access. All this can be made redundant if you know how to hack a Whatsapp Account.
Nonetheless, Whatsapp is still vulnerable to attacks from hackers. Since backed up chats are not protected by the end-to-end encryption, an attacker could access old chats if they hack into a user’s cloud storage account.
Since backed up chats are not protected by the end-to-end encryption, an attacker could access old chats if they hack into a user’s cloud storage account.
Methods How to Hack a Whatsapp Account
1. Phishing
This is a fraudulent attempt used by hackers to obtain sensitive information such as login details like usernames and passwords. Whatsapp phishing involves extracting the QR Code from Whatsapp Web then displaying it on a new page. If the victim scans the code using Whatsapp it will grab the credentials from the web client and save them in a file. You can use these credentials to log yourself in as the person who scanned the QR code. The phishing program particularly uses node.js and socket.io for the website and selenium responsible for scripting browsers that communicate with the Whatsapp web client. To begin with, the program starts at Http and a socket.io server. If a new client connects to socket.io, the application will request a selenium instance to start a new browser and connect to web. whatsapp.com. Afterward, it will fetch the QR code data and send it to the client via the web socket connection. The client javascript then shows the QR code to the user. When the QR code gets scanned Whatsapp will authenticate the selenium controlled browser and store some tokens in the local storage and document cookie. Data is extracted then saved into a text file.
whatsapp.com. Afterward, it will fetch the QR code data and send it to the client via the web socket connection. The client javascript then shows the QR code to the user. When the QR code gets scanned Whatsapp will authenticate the selenium controlled browser and store some tokens in the local storage and document cookie. Data is extracted then saved into a text file.
2. Use Keyloggers
Moreover, hackers may also use keylogger applications to hack into a WhatsApp account. A keylogger is a software program that records every keystroke that a targeted user types into their mobile device. It does this by secretly monitoring the victim’s input and keeping a log of all keys that are pressed then saves the data for later use. In this case, when your target user opens WhatsApp in his or her phone, the keylogger collects all the information they type into the device and saves it for you. There are several types of keyloggers available only on the web including mSpy and iKey monitor.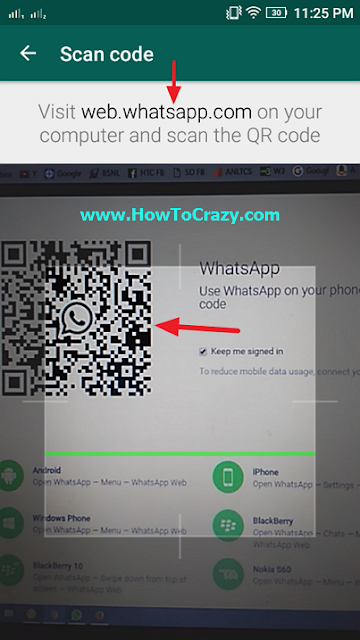
3. Using MAC Spoofing
This technique involves changing the factory assigned Media Access Control address of a specific network interface on a networked device. Besides being completely free, it does not require a lot of technical expertise. The basic requirements for accomplishing are the victims MAC address and the following steps:
· STEP 1: Completely uninstall your personal WhatsApp account from your device. You can still re-install WhatsApp later after you are done with this process.
- STEP 2: Secretly get access to your victim’s phone to find the MAC address. It is essential to note that the address is made of 12 characters but you can easily find it using the following methods depending on the device.
o For Android devices go to Settings > About phone > Status > Wi-Fi MAC address
o For Windows phones go to Settings > About > More info > MAC address
o For iPhone devices go to Settings > General > About > Wi-Fi address
o For BlackBerry go to Options > Device > Device and Status info > WLAN MAC
- STEP 3: Locate your own MAC address using the same procedure indicated above that matches your device then keep it in a secure place for later use.

- STEP 4: Enter the victim’s MAC address into your device. This is procedure is called spoofing which informs WhatsApp that you are trying to log into your account when on the other hand you are gaining access to your targeted victim’s account on your phone.
- STEP 5: Next, download and install specific MAC spoofing apps depending on the type of device that you are using. If you have an iPhone use WifiSpoof or Mac Daddy X, for Android devices use Terminal Emulator or BusyBox. Enter the “IP link show” in the terminal and then find the interface with your MAC address.
- STEP 6: Download and reinstall WhatsApp on your phone again. After you reinstall the app, you will need to configure it using your target victim’s phone number, which will thereby permit you to access his or her messages and other content.
- STEP 7: Once you enter the victim’s phone number, the real owner of the account will receive a confirmation code to verify that this new phone belongs to them.
 Fortunately, you have the phone close to you so you’ll just check the verification code and enter it to confirm. After this, you will have complete access to a target victim’s WhatsApp account. Do not forget to delete the verification code from the target’s phone before giving it back.
Fortunately, you have the phone close to you so you’ll just check the verification code and enter it to confirm. After this, you will have complete access to a target victim’s WhatsApp account. Do not forget to delete the verification code from the target’s phone before giving it back. - STEP 8: Lastly, you will need to reset your MAC address after you’ve gained access to your victim’s phone. Just follow the same process you used initially in the third step to change your MAC address and restore your mobile phone.
4. Mobile Phone Hacking
Mobile phone hacking and monitoring allow you to fully keep track of every activity of the target device. You can easily see the details of every communication that is all calls and text messages (incoming, outgoing, deleted). In addition to this, one may view internet history activities as well as Whatsapp activities. In short, everything will easily be hacked and shared on the app control panel. A few examples of mobile spying apps include: Xyspy, TruthSpy, and Spybubble.
5. SS7 Attack
SS7 which stands for Signaling System 7 is an international telecommunications standard that defines how the public switched telephone network (PSTN) exchanges information over a digital signaling network. Furthermore, it performs number translation, prepaid billing, short message service (SMS), among other mass-market services. Hackers exploit the SS7 vulnerability by tricking the telecom network into believing the attacker’s phone has the same number as the victim’s phone. Once the network has been fooled, the hacker can spy on the legitimate WhatsApp user by creating a new WhatsApp using a secret code. Consequently, the attacker now controls the account, including the ability to send and receive messages. Even more terrifying is the fact that the hacker has the ability to send messages on behalf of the victim, and read confidential messages intended for the victim without ever having to try to break strong end-to-end encryption protocols.
6. Session Hijacking
This is the act of taking control of a user’s valid computer session to gain unauthorized access to information or services after successfully obtaining the victim’s session ID. Session hijacking is highly likely when using the Whatsapp web version. Unlike other messaging websites, WhatsApp does notify users in case there is a second active session. This makes using this method of how to hack a whatsapp account very doable. Regardless, most users do not take note of this, therefore, giving the attacker access to all the information in the attacked WhatsApp account until the victim chooses an option to close the second active session from their computer.
7. Using Social Engineering
Contrary to other hacking techniques, hackers do not break into your device or system using any special kind of malware. Instead, they do it by extracting sensitive information by fooling you in some way.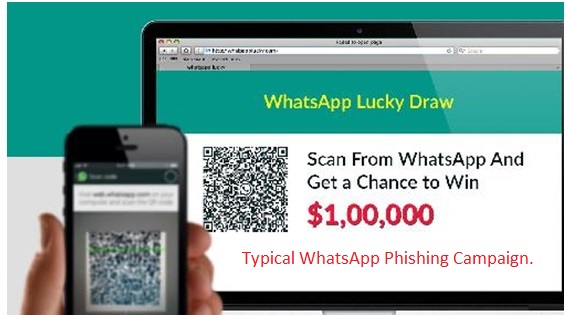 They then use this information against you by hacking into your system and stealing personal and valuable data. Most times they bait users online through promotional advertisements for offering gifts, free music or movie downloads then ask for the individual’s Whatsapp contact.
They then use this information against you by hacking into your system and stealing personal and valuable data. Most times they bait users online through promotional advertisements for offering gifts, free music or movie downloads then ask for the individual’s Whatsapp contact.
8. Use of a Whatsapp Hack Tool
Various hacking tools have been designed to spy on Whatsapp anonymously. A good example is one of our software which is available for sale. It has easy-to-use features that are useful for hacking into any Whatsapp account on another mobile device. It is beneficial on both Android and iPhone devices. The app was created by a group of coding professionals after they successfully mended a loophole detected in the Whatapp security database. The hackers developed and inserted an undetectable ”worm” into the system which allows the hack tool to connect to every account and steal important data like chat logs and calls. Some key features:
· A free two day trials
· Easy to use
· Hack is undetected
· Fast
· GPS location of the device that you’re targeting
· Call control and voice recording
· Direct access to messages, and other media on the device.
· Unlimited professional support
· Works perfectly with both mobile devices and desktop operating systems
· All countries are supported
9. DNS Spoofing
This is a form of computer security hacking in which a user is forced to use a fake website disguised to look like a real one, to divert traffic or steal personal credentials from the users. It can go undetected for a long period. Once a human language is entered on the computer, a DNS Server finds the actual IP address then directs the request from the user’s browser to the actual machine based on the IP address. Ultimately, hackers use DNS Spoofing to hijack the actual Whatsapp website address and redirects it to another IP address. As a result, the victim’s personal information can be compromised.
10. Sidejacking With Firesheep
Firesheep only works when the attacker and victim are on the same connection. It is carried out when an attacker gets a hold of a user’s cookie which is not encrypted hence vulnerable. This gives the hacker access to the user’s website. It is mostly done on open, wireless public networks. It is relatively similar to https hijacking.
This gives the hacker access to the user’s website. It is mostly done on open, wireless public networks. It is relatively similar to https hijacking.
Various ways in which one can avoid being a victim:
· Do not use unsupported versions of Whatsapp for example GBWhatsapp
· Ensure your Whatsapp messages do not back up to Google Drive or iCloud
· Enable the two-factor authentication for extra login security settings like entering a password or answering a security question
· Do not use public and insecure WiFi access points
· Do not share any personal information especially identification details and phone numbers
· Block installation of applications from unknown sources
· It’s essential to protect your Whatsapp with a lock app to safeguard your account from unsolicited users
· In case your phone is lost or stolen, make sure your SIM card is locked and Whatsapp deactivated through your network provider
· Ensure to log out of Whatsapp Web from your browser
· Watch out for scams; Whatsapp does not send emails unless you first contacted them requesting for help
· Avoid suspicious links.
NB: Learning how to hack a whatsapp account is purely for educational purposes.
Like us on Pinterest: https://www.pinterest.co.uk/hannibalhackersUK/
For more information visit us at https://www.hannibalhackers.su.
Contact us at [email protected].
WhatsApp Security Hacks: Are Your 'Private' Messages Really Ever Private?
WhatsApp one of the largest instant messengers and considered by many a social network of its own. So, in continuing our app safety discussion, we’re diving into some of the top security hacks and questions many WhatsApp app users and parents may have.
But first, what’s a security hack? In short, it’s an attempt to exploit the weaknesses in an app, network, or digital service to gain unauthorized access, usually for some illicit purpose. Here are just some of the concerns WhatsApp users may have and some suggestions on boosting security.
WhatsApp Hack FAQ
Are WhatsApp conversations private?
Yes — but there are exceptions. More than any other app, WhatsApp offers greater privacy thanks to end-to-end encryption that scrambles messages to ensure only you and the person you’re communicating with can read your messages or listen to your calls. Here’s the catch: WhatsApp messages (which include videos and photos) are vulnerable before they are encrypted and after they are decrypted if a hacker has managed to drop spyware on the phone. Spyware attacks on WhatsApp have already occurred. Safe Family Tip: No conversation shared between devices is ever 100% private. To increase your WhatsApp security, keep sensitive conversations and content offline, and keep your app updated.
More than any other app, WhatsApp offers greater privacy thanks to end-to-end encryption that scrambles messages to ensure only you and the person you’re communicating with can read your messages or listen to your calls. Here’s the catch: WhatsApp messages (which include videos and photos) are vulnerable before they are encrypted and after they are decrypted if a hacker has managed to drop spyware on the phone. Spyware attacks on WhatsApp have already occurred. Safe Family Tip: No conversation shared between devices is ever 100% private. To increase your WhatsApp security, keep sensitive conversations and content offline, and keep your app updated.
Can anyone read my deleted WhatsApp messages?
A WhatsApp user can access his or her own deleted messages via the chat backup function that automatically backs up all of your messages at 2 a.m. every day. WhatsApp users can delete a message by using the Delete for Everyone button within an hour after sending though it’s not foolproof. Here’s the catch: Anyone who receives the message before it’s deleted can take a screenshot of it. So, there’s no way to ensure regrettable content isn’t captured, archived, or shared. There are also third-party apps that will recall deleted messages shared by others. Another possibility is that a hacker can access old chats stored in an app user’s cloud. Safe Family Tip: Think carefully about sharing messages or content you may regret later.
Here’s the catch: Anyone who receives the message before it’s deleted can take a screenshot of it. So, there’s no way to ensure regrettable content isn’t captured, archived, or shared. There are also third-party apps that will recall deleted messages shared by others. Another possibility is that a hacker can access old chats stored in an app user’s cloud. Safe Family Tip: Think carefully about sharing messages or content you may regret later.
Can WhatsApp messages be deleted permanently?
Even if a WhatsApp user decides to delete a message, it’s no guarantee of privacy since conversations are two-way, and the person on the receiving end may screenshot or save a copy of a chat, video, or photo. On the security side, you may delete a message and see it disappear, but WhatsApp still retains a “forensic trace of the chat” that can be used by hackers for mining data, according to reports. Safe Family Tip: For extra security, turn off backups in WhatsApp’s Settings.
How can I secure my WhatsApp?
It’s crucial when using WhatsApp (or any other app) to be aware of common scams, including malware, catfishing, job and money scams, spyware, and file jacking. To amplify security, turn on Security Notifications in Settings, which will send an alert if, for some reason, your security code changes. Other ways to boost security: Use two-step verification, never share your 6-digit SMS verification code, disable cloud back up, and set your profile to private. Safe Family Tip: Install comprehensive family security software and secure physical access to your phone or laptop with a facial, fingerprint, or a passcode ID. Don’t open (block, report) messages from strangers or spammers. Never share personal information with people you don’t know.
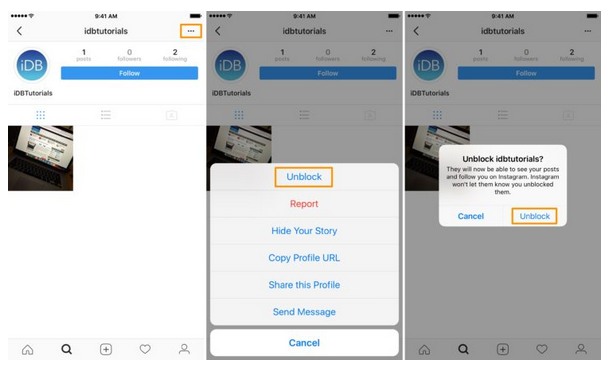
How do I delete my WhatsApp account from another phone?
To delete a WhatsApp account go to > Settings > Account > Delete My Account. Deleting your account erases message history, removes you from groups, and deletes your backup data. According to WhatsApp, for users moving from one type of phone to another, such as from an iPhone to an Android, and keeping the same phone number, your account information stays intact, but you won’t be able to migrate messages across platforms. If you’re not keeping your number, you should delete WhatsApp from your old phone, download WhatsApp to your new phone, and verify your new phone number. Upgrading the same phone type will likely include options to migrate messages. Safe Family Tip: Before you give away or exchange an old phone, wipe it clean of all your data.
Deleting your account erases message history, removes you from groups, and deletes your backup data. According to WhatsApp, for users moving from one type of phone to another, such as from an iPhone to an Android, and keeping the same phone number, your account information stays intact, but you won’t be able to migrate messages across platforms. If you’re not keeping your number, you should delete WhatsApp from your old phone, download WhatsApp to your new phone, and verify your new phone number. Upgrading the same phone type will likely include options to migrate messages. Safe Family Tip: Before you give away or exchange an old phone, wipe it clean of all your data.
How do you know your WhatsApp is scanned?
WhatsApp users can easily sync devices by downloading the WhatsApp web app and activating it (Settings > WhatsApp Web/Desktop). Devices sync by scanning a QR code that appears on your laptop screen. You know your device is scanned when you see the green chat screen appear on your desktop. Safe Family Tip: It’s possible for a person with physical access to your desktop to scan your QR code and to gain account access. If you think someone has access to your account log out of all your active web sessions in WhatsApp on your mobile phone.
How long are WhatsApp messages stored?
According to WhatsApp, once a user’s messages are delivered, they are deleted from WhatsApp servers. This includes chats, photos, videos, voice messages, and files. Messages can still be stored on each individual’s device. Safe Family Tip: The moment you send any content online, it’s out of your control. The person or group on the receiving end can still store it on their device or to their cloud service. Never send risky content.
How secure is WhatsApp?
There’s no doubt, end-to-end encryption makes it much more difficult for hackers to read WhatsApp messages. While WhatsApp is more secure than other messaging apps — but not 100% secure.
Is it true that WhatsApp has been hacked?
Yes. Several times and in various ways. No app, service, or network has proven to be unhackable. Safe Family Tip: Assume that any digital platform is vulnerable. Maximize privacy settings, never share risky content, financial information, or personal data.
Is WhatsApp safe to send pictures?
Encryption ensures that a transmission is secure, but that doesn’t mean WhatsApp content is safe or that human behavior is predictable. People (even trusted friends) can share private content. People can also illegally attempt to gain access to any content you’ve shared. This makes WhatsApp (along with other digital sharing channels) unsafe for exchanging sensitive information or photos. Safe Family Tip: Nothing on the internet is private. Never send or receive pictures that may jeopardize your privacy, reputation, or digital footprint.
WhatsApp isn’t the only popular app with security loopholes hackers exploit. Every app or network connected to the internet is at risk for some type of cyberattack. We hope this post sparks family discussions that help your kids use this and other apps wisely and helps keep your family’s privacy and safety online top of mind.
Try McAfee Mobile Security
Enjoy safer mobile devices with all-in-one protection
How to read someone else's WhatsApp from your phone, knowing the phone number
The reasons for hacking WhatsApp can be both personal and ordinary interest. For example, the most common cause is the jealousy of a wife or husband. Interest also plays an important role. Man is a very inquisitive being, so simple interest is also a private cause. The third reason may be parental control over their child.
- How to access Whatsapp if there is no access to the phone?
- We get access to the Watsap on Android without access
- ACTION ACTION
- We get access to the WATSAP reports on the iPhone, without access
- Method of read any alien Watsap correspondence through a computer
- We get access to the Watsap on Android without access
- Rubatsup.
- Forwarding algorithm:
How to access WhatsApp if there is no access to the phone?
We will talk further about several methods that will help to hack the application without access to the phone. Since it is not always possible for a person to pick up a phone and read SMS on WhatsApp.
Dear readers! Please pay attention! If you have additional questions after reading the article, something is not clear to you, then feel free to write comments in the comments. I will deal with each situation, approach you individually, answer your questions.
Getting access to WhatsApp on Android without access
Everyone knows that the most difficult to bypass and hack applications through Android, so you need to download additional applications. They can be found in the Play Market and installed from the official source.
Convenience lies in the fact that basically the program does all the actions for a person. For those who do not understand the device and the functions of applications, it will be much easier to do everything through special programs.
The program that will help in hacking WhatsApp is called Whatscan for WhatsApp . You can download it from the official source on all Android devices.
Procedure
- Download app
- Scan the code that appears on the screen from a friend's phone.
- After activation, you automatically have access to WhatsApp messages.
Accessing WhatsApp messages on iPhone without access
Unfortunately, such an application, which was mentioned earlier, is not officially available on the iPhone, but there is another "WhatsApp spy" - mySpy.
Application and work with it is exactly the same as with the past. Therefore, there is no need to write. It must be remembered that the iPhone has a strong security system that can block your actions.
But, despite this risk, some use this method and get access to SMS in a few minutes, and sometimes seconds.
A way to read any other person's WhatsApp correspondence through a computer
The easiest way is to hack whatsapp via pc. You must have internet access to complete the steps.
Action sequence:
- Go to web.whatsapp.com
- Through the phone of the person you want to hack, go to create a chat and open the last option of WhatsApp Web
- After just scan the code, after activation you have the option of read other people's WhatsApp messages .
This method involves partial phone access, but since the phone is only needed at the beginning, it belongs to the “no phone access” methods.
Also, this method can help not only in hacking, but also when it is necessary to transfer data from WhatsApp to a computer.
But, this method has several disadvantages, which we will talk about now:
- This method does not work on iPhone.
- A person can find out that someone is using the application and hacking into correspondence.
- The user will be shown online every time they read other people's posts.
- Here are three ways for each phone to help hack the application.
Forwarding WhatsApp correspondence to email
This method is considered more difficult than others, but even this can be learned. The difficulty lies in the fact that you need to know and have e-mail. But the advantage is that this method can be used on both Android and iPhone.
Forward algorithm:
- Go to the WhatsApp messenger in "chats" and select the chat you want to check.
- Shift to the left and select "More"
- Choose to send by E-mail.
- Choose how to read messages with or without media and files.
- Sending.
 And now the messages are sent from one phone to another.
And now the messages are sent from one phone to another. - But the main thing is to have a normal Internet and e-mail.
How to access correspondence without having access to WhatsApp
Hack the application by creating a copy of the account. But the use of such an occasion is responsible for oneself and for others.
We will not describe this method, since it is illegal. But on the Internet you can find a lot of information.
Linking someone else's phone, where there is WhatsApp to your
To bind someone's phone, you need to have two things, this is the friend's phone number and the phone itself to confirm SMS.
Algorithm:
- Downloading the application.
- You need to verify your phone number when you sign in. And log into a friend's account.
- Confirm number.
- Then it is recommended to delete the messages so that the one who was hacked does not think about anything.
- After confirmation, you are logged into your WhatsApp account.
 That's the whole complex method.
That's the whole complex method.
Is it still worth using the services of special hacking services?
There are special services that will help you hack applications, including WhatsApp.
It is not advisable to hire specialists, since you can do everything yourself. We have provided you with three ways that can definitely help you. But on the other hand, it all depends on the specific situation.
There is an article in the criminal code that says that you can not violate personal space and read other people's correspondence. Therefore, such actions may be subject to state sanctions against individuals. And it can also happen that a person will be imprisoned for several years.
Therefore, before hacking WhatsApp or other applications, think carefully. If your “victim” finds out about the break-in, there is a chance that a criminal case may be opened against you upon a police report.
Share with friends:
90,000 people go to a private detective for what / News of the Society of Krasnoyarsk and the Krasnoyarsk Territory / Newslab. Ru The work of a private detective in Russia is shrouded in secrets no less than the everyday life of FSB officers or, for example, those who work in the defense industry. Basically, the townsfolk have developed a stereotypical opinion based on series, films, and sometimes just speculation. Newslab talked to a private detective about who uses his services, is it difficult to do a search, how to take a break from a difficult job, and much more.
Ru The work of a private detective in Russia is shrouded in secrets no less than the everyday life of FSB officers or, for example, those who work in the defense industry. Basically, the townsfolk have developed a stereotypical opinion based on series, films, and sometimes just speculation. Newslab talked to a private detective about who uses his services, is it difficult to do a search, how to take a break from a difficult job, and much more. "Elementary, Watson!" Do modern detectives look like a famous literary character?
Still from the movie "Sherlock Holmes and Dr. Watson" (1979-1986)
How I became a detective
In fact, everything is banal. I worked in the police, in the criminal investigation department, where they solve crimes, search for people, etc., that is, they are at the forefront in the fight against crime. I worked there for 15 years and I got tired of it. Tired of the heavy bureaucratic machine, this constant employment, lack of free time. First, I was called to the business, I left and became a deputy head in a construction company. After working for six months, I realized that this was absolutely not mine. Although the income has become much higher, nevertheless, I realized that I don’t understand this and construction is not my business. In general, six months later, I was about to leave and started looking for a new job.
First, I was called to the business, I left and became a deputy head in a construction company. After working for six months, I realized that this was absolutely not mine. Although the income has become much higher, nevertheless, I realized that I don’t understand this and construction is not my business. In general, six months later, I was about to leave and started looking for a new job.
I did not want to return to the police, my pride did not allow me, although they called me back. And then I began to think what I could do, knowing only how to solve crimes. I did not want to go to the enterprise security service, because it is the same as the police, although the salary is a little higher.
I remember that in Russia there is a law on private detective activity, that such work can be done quite legally, and this distinguishes our state from many CIS countries where such activity is prohibited - for example, in Kazakhstan. We also have a law dated 1991 years old, it has not changed for a long time, but it works and allows you to get a private detective license and provide investigation services.
Obtaining a license was an easy task for me. I had work experience in the authorities, which is practically a prerequisite, I also have a law degree. In addition, one of the conditions is the absence of a criminal record and the absence of any prohibitive points, for example, negative motives for dismissal. And so, from January 1, 2020, I began to engage in detective work.
Spare no money on advertising
Initially, I was afraid that there would be no orders at all. Moreover, many dissuaded me. But mostly retired uncles who had worked in the authorities for many years dissuaded me. They also tried to do detective work, but no one came to them, there were no orders. But here, as in any business, you need to promote your services, you need to advertise and provide them with high quality so that people come back to you. And they said: "Well, we opened, sat, waited, no one came to us, so we closed." People themselves will not come until you show what you are capable of.
At first, I studied the promotion of services, and I took law firms as a basis. I made a page on Instagram, launched a website and started advertising on other sites. From the very beginning, he did not spare money for this, but in fact they are small. Clients poured in almost immediately.
This job does not need employees. I work alone, but I involve other people to carry out some specific activities. It could be a taxi driver who is actually a drama theater actor (acting is good). It could be a plumber whom I ask to come in and get some information.
My work requires some ingenuity, and I involve people I know, whom I know well, and who also want to earn some money. Moreover, people are needed when there is work in other regions or on the territory of other states - this is not a problem for me. I have a lot of established contacts - Russian-speaking people - you can find a detective who will help with the case.
Another Sherlock Holmes and his constant partner, but in a modern interpretation
Still from Sherlock Holmes (2009)
Not all requests are legal and feasible
In fact, I am contacted every day — by 2-3 people. But many of them do not quite understand the work of a detective and, for example, come with a request: "Hello, I want to hack my wife's Whatsapp." And they do not understand that this is not only technically impossible, but also illegal - this is a violation of two articles of the Criminal Code, and not only the detective, but also the customer can be punished.
But many of them do not quite understand the work of a detective and, for example, come with a request: "Hello, I want to hack my wife's Whatsapp." And they do not understand that this is not only technically impossible, but also illegal - this is a violation of two articles of the Criminal Code, and not only the detective, but also the customer can be punished.
The bulk of the work is done by "legs" - personal investigation, communication with people, making inquiries. So there may be several requests per day, but in fact we do not take everything into work. There are small orders - to find the phone number of the right person, there are large orders - for several days or even a week.
The most common request is infidelity, adultery, more than half of such orders. But I think this is not due to the fact that we cheat a lot, but to the fact that people do not understand what detectives do. They think about cheating, remember some series or films and think: “Oh, hiring a private detective, he can help!” But, as a rule, such requests boil down to the fact that the desires of customers are often illegal. By the way, 9 out of 10 infidelity requests are female infidelities.
By the way, 9 out of 10 infidelity requests are female infidelities.
There are very few requests that can be organized legally. Most often, we take on such cases where, for example, a division of property is planned, when, for example, a spouse planned a divorce, but had not yet notified his wife, and at that moment began to get rid of property so as not to divide anything. By the way, these are also interesting tasks.
But my favorite orders are the search for close relatives or those with whom contact has been lost. For example, a person wanted to find a childhood friend - he is not on social networks, he only remembers his name and birthday. It is also interesting to look for biological parents - someone was brought up in an orphanage, in foster families, someone wants to see his mother - he has such an inner desire - we also help with this.
Not so long ago, there was an interesting case - we were approached by a fairly well-known girl in show business with a request to find her birth father. He left his family when she was 5 years old. We literally found my father in two days, it turned out that he lives in some remote village in the Urals. We gave him a video message that she recorded - a very touching video where she is with her son. Uncle, of course, was very happy. We arranged a meeting for them and now they are talking. Such cases are very interesting, and if the story is sincere, it turns out really cool.
He left his family when she was 5 years old. We literally found my father in two days, it turned out that he lives in some remote village in the Urals. We gave him a video message that she recorded - a very touching video where she is with her son. Uncle, of course, was very happy. We arranged a meeting for them and now they are talking. Such cases are very interesting, and if the story is sincere, it turns out really cool.
Finding people is one of the most enjoyable tasks for me, because I know how to do it, and I have been doing it for many years. I have enough skills to find a person using almost improvised means. That is, if a person did not disappear somewhere in the forest without a trace, but left somewhere, moved, he leaves some traces behind him - these are mail, documents, SIM cards. Such a person is very easy to find - of course, at a certain cost.
The crime turned out to be a fantasy
There are many strange requests. One of the most unusual and interesting cases that I took on was last summer. I was contacted by a woman who used to live in Moscow. She made the following request: in 1983-1985. she went to a kindergarten in Moscow, and now she has memories that a boy went to the group with her, who at some point went missing and stopped going to kindergarten. Developing this thought in her head, she came to the conclusion that the boy did not just disappear, but disappeared when her father came to the kindergarten and took away both her and this child. Then she began to talk about the fact that she suspects her own father of a crime - allegedly, having brought someone else's child into the house, he began to mock him - poking with a knife and more.
I was contacted by a woman who used to live in Moscow. She made the following request: in 1983-1985. she went to a kindergarten in Moscow, and now she has memories that a boy went to the group with her, who at some point went missing and stopped going to kindergarten. Developing this thought in her head, she came to the conclusion that the boy did not just disappear, but disappeared when her father came to the kindergarten and took away both her and this child. Then she began to talk about the fact that she suspects her own father of a crime - allegedly, having brought someone else's child into the house, he began to mock him - poking with a knife and more.
Related materials
“Reading King to relax”: one day in the life of a Krasnoyarsk investigator
Cache in the ceiling, black fingers and long interrogations
All this began to appear in her memory, and everything was very plausible. She asked us to verify this information. She had not spoken to her father for a long time. We began to conduct checks, make inquiries, write requests, and raised archives. And after two months of painstaking work, we found out that there was nothing like that. We provided her with all the evidence, and yes, she agreed and began to work on this problem with a psychologist.
She had not spoken to her father for a long time. We began to conduct checks, make inquiries, write requests, and raised archives. And after two months of painstaking work, we found out that there was nothing like that. We provided her with all the evidence, and yes, she agreed and began to work on this problem with a psychologist.
The police don't know who the detectives are at all. Although everything is prescribed by law, the police often do not know who a private detective is and that they even exist, that they have a license. When we conclude an agreement with a customer in a criminal case, we are obliged to notify the investigator that we are getting involved in the work. And every second investigator just rolls his eyes and says: "Who are you anyway?!"
In the code of criminal procedure used by investigators, there is no information about private investigation, and they do not allow to work in full. Therefore, a lot of work and requests are carried out informally. Moreover, a lawyer's request, for example, is mandatory, it must be responded to, and a detective's request is not mandatory.
Moreover, a lawyer's request, for example, is mandatory, it must be responded to, and a detective's request is not mandatory.
Cunning and deceit have to get around these rules, the established contacts also help, we ask the police to help. We are not allowed to introduce ourselves as the police, but we can introduce ourselves, for example, as journalists. In general, a detective and a journalist are very similar professions in terms of obtaining information. In the police, this is called "operational infiltration", that is, you need to infiltrate a person in such a way that he can trust you and tell you.
And our citizens are very gullible, and in half an hour they are already telling you everything. It is enough to sit down with some citizen on the train, get a chicken out of the foil, even without alcohol (and if with intoxicating, then all the more so) and it pours out of it like from a cornucopia, he will simply tell you everything.
Sometimes in a simple conversation you can learn a lot from the people around you.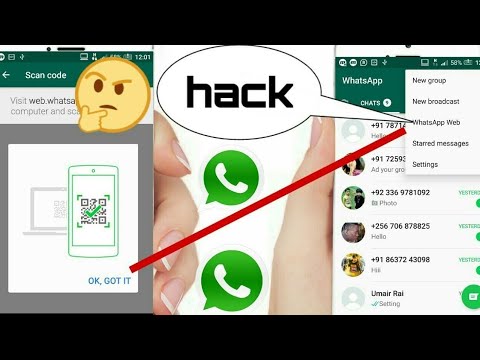 For example, go to the concierge at the entrance and ask to see the recordings from surveillance cameras. You can say: “Hello, I am the owner of the cameras, I need to check them, they should have called you,” as a rule, women or those who sit there willingly tell everything.
For example, go to the concierge at the entrance and ask to see the recordings from surveillance cameras. You can say: “Hello, I am the owner of the cameras, I need to check them, they should have called you,” as a rule, women or those who sit there willingly tell everything.
A real, not a movie detective, often does not look like a hero
A still from the film “Knives Out” (2019)
Nature helps to relax
A change of scenery helps me disconnect from work. Most of the work can be done remotely, which I use. For example, I can go to Gorny Altai, which I love very much and go there several times a year. You can leave for a week and work from there. I can just go somewhere where there is no connection, on a hike, for example, to Belukha, to Shavlinsky Lakes, or to some other Altai places. Here you switch off and think only about which pebble to step on, and not about something else.
I like to have a rest in Siberia. I don’t really like the sea: not so long ago I was in the Dominican Republic, and this vacation is not for me, it seemed boring to me.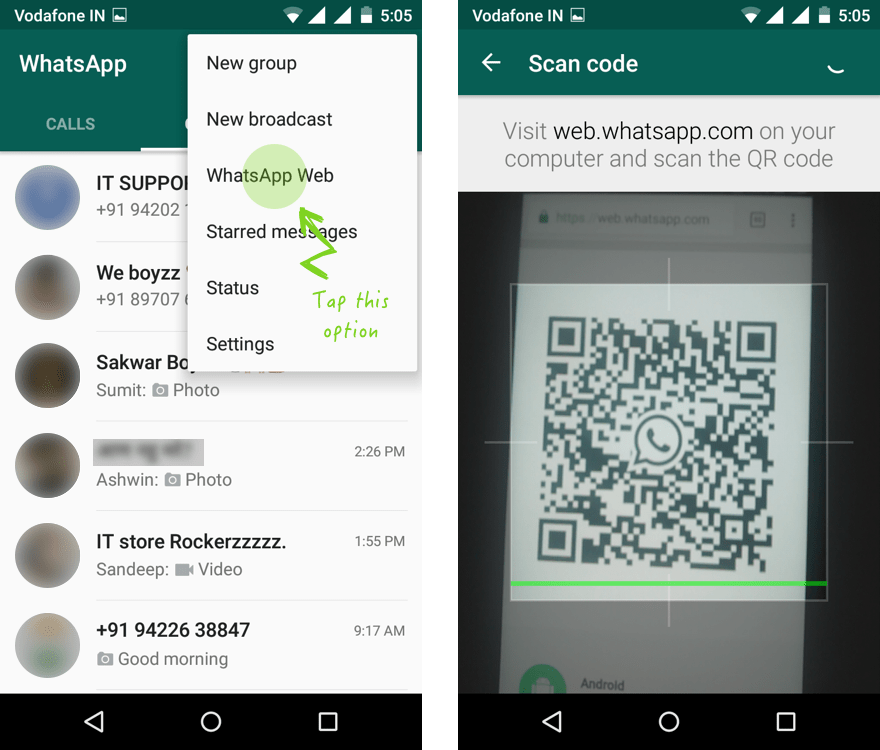 For the first time in my life I went abroad, and on the fifth day I got bored.
For the first time in my life I went abroad, and on the fifth day I got bored.
There are three categories of detectives on the detective market
The first one is licensed detectives, with IP, with open information. There are 700 such people in Russia. There is a second category - they can work with or without a license, they have some experience. But they are often prone to deceit. I have many such colleagues in whom I was disappointed. That is, they take an order, charge a lot of money for it, and then they simply tell the customer lies. The customer will not be able to check. And these "detectives" take an order, for example, to hack a messenger and say: "So, here we were able to open one dialogue of your husband, here they write this and that." Or a person orders surveillance, and they tell him fairy tales - so, he was in that restaurant, went there, but this actually didn’t happen.
And the third category of detectives are ordinary swindlers. They advertise their services mostly on the Internet, they just get money and do nothing.