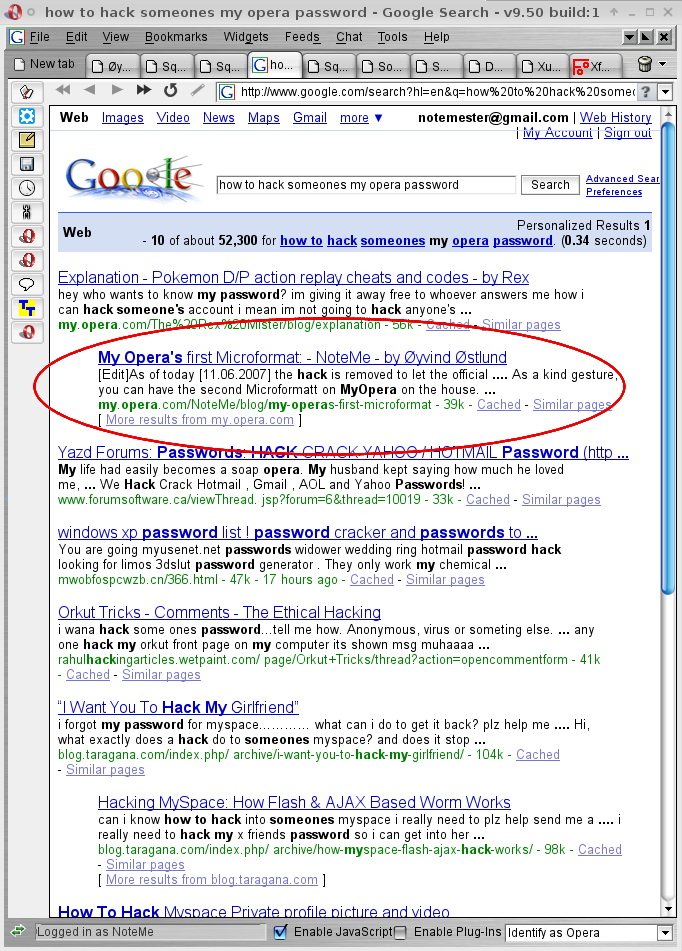
How to easily hack into someones facebook
How to Hack Facebook Account Just by Knowing Phone Number
June 15, 2016Swati Khandelwal
Hacking Facebook account is one of the major queries on the Internet today.
It's hard to find — how to hack Facebook account or facebook messenger, but researchers found a way that can allow someone to hack Facebook account passwords with only the target's phone number and some resources.
Yes, your Facebook profile can be hacked, no matter how strong your password is or how much extra security measures you have taken. No joke!
Hackers with resources to exploit SS7 network can hack your Facebook login and all they need is your phone number.
The weaknesses in the part of global telecom network SS7 that not only let hackers and spy agencies listen to personal phone calls and intercept SMSes on a potentially massive scale but also let them hijack social media accounts to which you have provided your phone number.
SS7 or Signalling System Number 7 is a cell phone signaling protocol that is being used by more than 800 telecommunication operators worldwide to exchange information with one another, cross-carrier billing, enabling roaming, and other features.
However, an issue with the SS7 network is that it trusts text messages sent over it regardless of their origin. So, malicious hackers could trick SS7 into diverting text messages as well as calls to their own devices.
All they need is the target's phone number and some details of the target's device to initiate the silent snooping.
The researchers from Positive Technologies, who recently showed how they could hijack WhatsApp and Telegram accounts, now gave the demonstration of the Facebook hack using similar tricks, Forbes reported.
SS7 has long been known to be vulnerable, despite the most advanced encryption used by cellular networks. The designing flaws in SS7 have been in circulation since 2014 when the team of researchers at German Security Research Labs alerted the world to it.
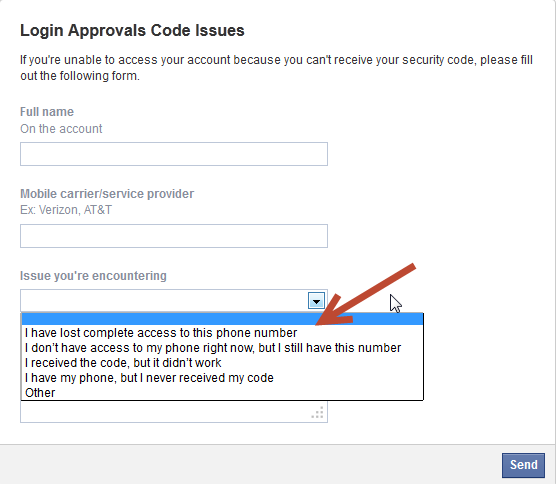
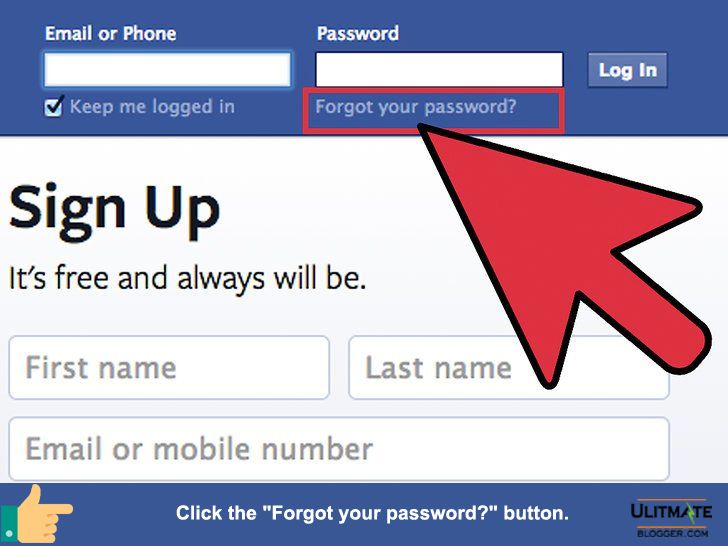
Here's How to Hack Any Facebook Account:
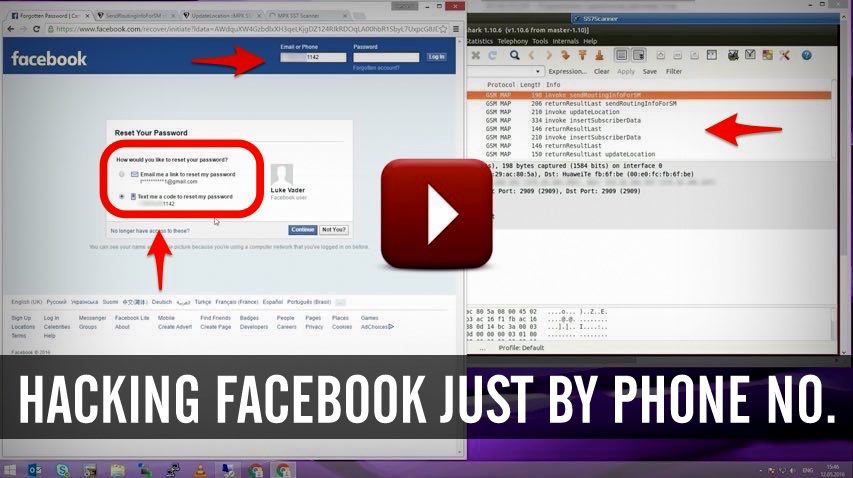
The attacker first needs to click on the "Forgot account?" link on the Facebook.com homepage to reset your password. Now, when asked for a phone number or email address linked to the target account, the hacker needs to provide the legitimate phone number.
Now, when asked for a phone number or email address linked to the target account, the hacker needs to provide the legitimate phone number.
The attacker then diverts the SMS containing a one-time passcode (OTP) to their own computer or phone, and can gain access to the target's Facebook account.
The issue affects all Facebook users who have registered a phone number with Facebook and have authorized Facebook Texts.
Besides Facebook, researchers' work shows that any service, including Gmail and Twitter, that uses SMS to verify its user accounts has left open doors for hackers to target its customers.
Although the network operators are unable to patch the hole sometime soon, there is little the smartphone users can do.
- Do not link your phone number to social media sites, rather rely solely on emails to recover your Facebook or other social media accounts.
- Use two-factor authentication that does not use SMS texts for receiving codes.
- Use communication apps that offer "end-to-end encryption" to encrypt your data before it leaves your smartphone over your phone's standard calling feature.
However, the important thing to note is that the issue has actually nothing to do with Facebook security or other website's security, instead it is the weakness in the telecom network.
"Because this technique [SSL exploitation] requires significant technical and financial investment, it is a very low risk for most people," Facebook spokesperson told The Hacker News.
"As an added precaution, we recommend turning on two-factor authentication, called Login Approvals, in your Facebook security settings. Doing this will disable recovery via SMS on your account so even if someone has your phone number, they'll still need your password to access your account."
Update: If you think this technique is old and can not be used to hack your social media, bank or any online accounts, then you are mistaken. A real-world SS7 attack has been spotted this month when some unknown hackers exploited the design flaws in the Signaling System 7 (SS7) to drain victims' bank accounts.
A real-world SS7 attack has been spotted this month when some unknown hackers exploited the design flaws in the Signaling System 7 (SS7) to drain victims' bank accounts.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
SHARE
Share
Tweet
Share
Share
Share on Facebook Share on Twitter Share on Linkedin Share on Reddit Share on Hacker News Share on Email Share on WhatsApp Share on Facebook Messenger Share on TelegramSHARE
Facebook account hacking, Facebook hacking, gmail hacking, hacking news, How to Hack Facebook, interception, Signaling System 7, sms hacking, SS7, SS7 Protocol, twitter hacking
6 Ways How Someone Can Hack Into Your Facebook Account in 2022
What springs to your mind whenever someone mentions hacking a Facebook account? Do you imagine tech-savvy geeks with a doctorate in software engineering? Or is it some dangerous hooded hacker typing away lines of lethal code on his keyboard and ready to break into anyone’s online world?
In fact, pretty much anyone can hack someones Facebook account by using a few simple methods.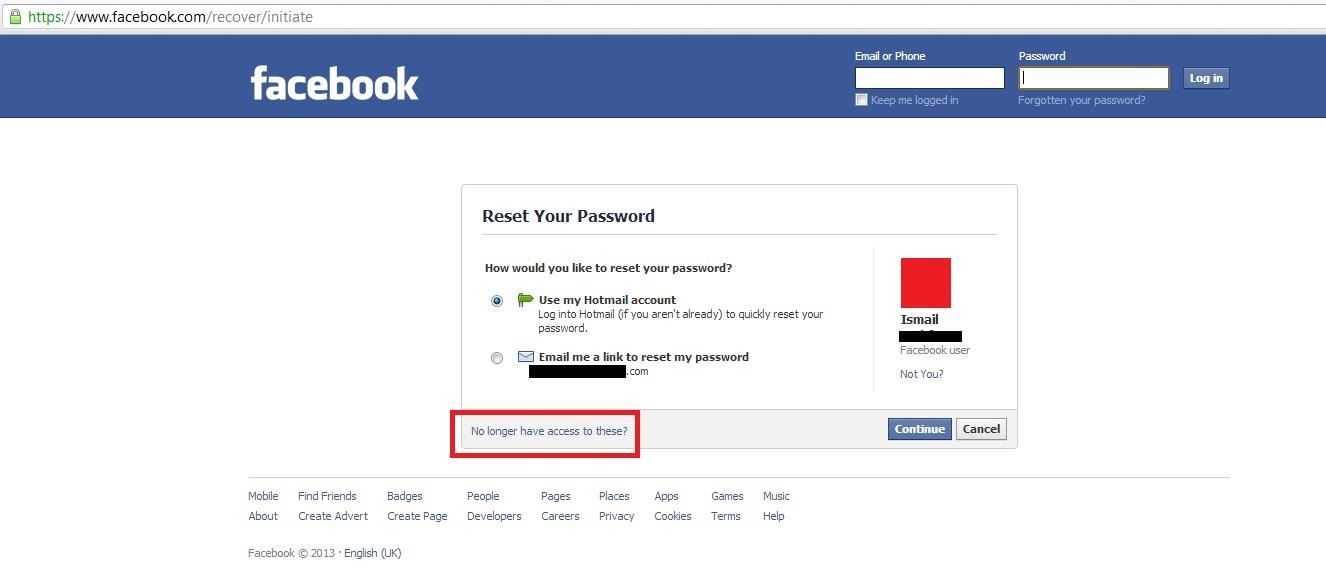 And yet, these methods aren’t for someone who’s itching to practice their hacking skills. Instead, it’s for someone in dire need and with legitimate reasons.
And yet, these methods aren’t for someone who’s itching to practice their hacking skills. Instead, it’s for someone in dire need and with legitimate reasons.
Table Of Contents
How to Hack Facebook Account of Another Person: 6 Methods That You Didn’t Know About
There are countless ways to hack Facebook Messenger conversations. The ones we listed below are the easiest methods to monitor someone’s Facebook activity. Do remember, though, that however, having a good excuse to monitor someone’s social media account without permission is a must.
In the video below we have gathered the best methods for Facebook monitoring. After reviewing it, don’t forget to get back to reading to learn 3 more methods to view your kid’s messages.
1.
 Installing a Monitoring App
Installing a Monitoring AppHave you been looking for ages for a workable solution on how to monitor a Facebook account in just a few clicks without the minesweeper-level strategy? Then this one is for you. One way of getting into their account is to use a superb monitoring tool, such as mSpy.
Here is how you can hack someones Facebook to view data from their FB account with this app:
- Go to mSpy.com and sign up.
- Select and buy a subscription.
- Check your mailbox for the installation instructions from mSpy. Follow them to set up the app.
- Sign in to your mSpy account and link the device you want to force your way into.
- Give the app a few minutes and start monitoring that person’s Facebook.
2. Hacking into Facebook Account Using the Manual Method
An ideal solution for those unwilling to soil their hands and sweat buckets while figuring things out is to hack FB manually, plain and simple. Here is how you can hack someones Facebook and access their account:
- Find out the email address they use to sign up with Facebook.

- Open the login page and click Forgot password. Tap on the popup for more prompts to take further action.
- FB will ask you to provide the recovery email address to send you a link for a password reset. As you probably won’t have access to that email address, you’ll need to click No longer have access to these?.
- Next, you’ll have to give an alternative email address. This email address shouldn’t be tied to the Facebook account you want to monitor.
- FB will ask you a couple of questions to prove that you are the owner of that account. If you know the target user close enough, it will much be easier to guess the correct answers.
- If you fail in the previous stage, you can use your friends to help you reset the password. In this case, you will select three friends and create fake FB accounts in their names. This way the previous obstacle will be easily overcome because Facebook will contact those “friends” for confirmation.
- Once you successfully go through all these stages, you will get an email notification sent to the alternative email address you gave.
 From there, you may reset the password and access the account you want to monitor.
From there, you may reset the password and access the account you want to monitor.
Another fairly straightforward way to hack someones Facebook account is to use a keylogger app. These are used to record keystrokes on another person’s cell phone, helping you to intercept their FB login credentials.
To capture their credentials, you need to install the software directly to the user’s device. After the setup, it’ll start recording and sending you everything that user types on their cell phone.
To use keyloggers effectively, you need to take the following steps:
- Google for a keylogging software and choose the one that suits your needs best and is both reputable and safe.
- Install the software on the device you want to monitor. Activate the app before accessing any keylogging service.
- After installing and verifying the application, sign in to your software’s control panel and go through the list of passwords the app managed to harvest.
 An app that truly lives up to its excellent reputation will capture all the passwords the person used on their devices and might even sho you the screenshots of interactions they had most recently.
An app that truly lives up to its excellent reputation will capture all the passwords the person used on their devices and might even sho you the screenshots of interactions they had most recently.
Although you can find numerous free keyloggers online, we recommend that you avoid using them. Free apps are insecure and can corrupt your or another person’s device. If you want to monitor someone’s Facebook safely, be ready to fork out at least a couple of bucks for a good and reliable app.
4. Matching a Password
This trick depends on the negligence and naivety of FB users who use weak and predictable passwords. And there are many such people. Anyway, this method may not bring the expected results as it’s based solely on luck and someone’s ignorance and negligence.
A lot of people often use dates and names of the highest importance to them. Cracking their password when you know enough information about them will be a piece of cake. This includes things like:
- year of birth
- wedding anniversary
- spouses’ or children’s names
- mobile phone numbers
5.
 Using Cookies to Hack Facebook
Using Cookies to Hack FacebookCookies are another way of hacking someone’s Facebook Messenger without them knowing. Cookies’ purpose is to help websites ‘remember’ the user who visited a particular website. Moreover, they contain some pretty sensitive data since they track whole browsing sessions.
Do you use the same Wi-Fi network as the person you want to monitor? Congratulations, now you can sniff and harvest their data. Sure, you won’t get direct access to the person’s password. But you can cloneit and this way trick FB into believing that the browser has already been authenticated.
So you will log into their account and simply continue where they left off without raising any suspicions. You can use extension apps and add them to your browsers to store cookies in a tab on the browser’s sidebar. Seems like another easy way to hack someones Facebook without putting in too much effort, doesn’t it?
If you know that the person whose account you want to hack is gullible, naive, or inattentive enough, sending them a phishing email might be another option to consider. Phishing means impersonating some organization or person and is a type of online scam that is still quite popular.
Phishing means impersonating some organization or person and is a type of online scam that is still quite popular.
To ‘fish’ their credentials, you’ll need to create a believable enough fake email. It should look like it was sent from Facebook. In this email, you’ll either directly request their password for some made-up reason, or disguise it as a fake notification about friend requests and messages, false claims that that user went against FB’s Community Standards and so on.
Our Final Take
Passwords are the official gatekeepers of any Facebook account. Hacking them is illegal and can lead to some unpleasant consequences. If you need to track someone’s conversations on Facebook to protect them from online predators or want to prevent data from leaking, we recommend using an official monitoring app. It seems obvious that to hack someones Facebook is no mean feat, and you’ll need a truly outstanding software for that to happen.
What is more, with such software as mSpy, you can legally monitor all the information a person gets on their phone, including other messengers, social media apps, calls, and locations. All in all, it’s up to you to decide. Just make sure to analyze the pros and cons of the chosen method and refrain from violating someone’s privacy without a dire need or doing anything illegal.
All in all, it’s up to you to decide. Just make sure to analyze the pros and cons of the chosen method and refrain from violating someone’s privacy without a dire need or doing anything illegal.
Patricia Belton
Patricia Belton was raised in a single-working-mother family, that’s why she’s deeply interested in family issues. She graduated from New York University with a Bachelor’s degree in Classical Literature, married, mother of 2 kids. Mrs. Belton writes for different e-journals, participates in versatile online/offline conferences and forums connected with kids and influence of technology.
Found a way to hack into any Facebook account using a "hole" that is 10 years old
Security Security strategy User Internet Web Services
|
Share
 The flaw, which Facebook closed in early 2020, allowed it to seize control of any account on the social network and its friendly services.
The flaw, which Facebook closed in early 2020, allowed it to seize control of any account on the social network and its friendly services. Dangerous Vulnerability
Security researcher Amol Baikar (Amol Baikar) has identified a dangerous vulnerability in Facebook's OAuth authorization protocol. It allows you to access any social network account, as well as other services that are logged in using Facebook. The specialist spoke about this in his personal blog, emphasizing that the described bug has existed for about 9 years.-10 years.
According to Baikar, the problem lies in the implementation of the "Login with Facebook" function, which uses the OAuth 2.0 authorization protocol to exchange authorization tokens between the social network site and other web resources. Thanks to this feature, Facebook account holders can freely use third-party Internet services that provide such an opportunity without additional registration.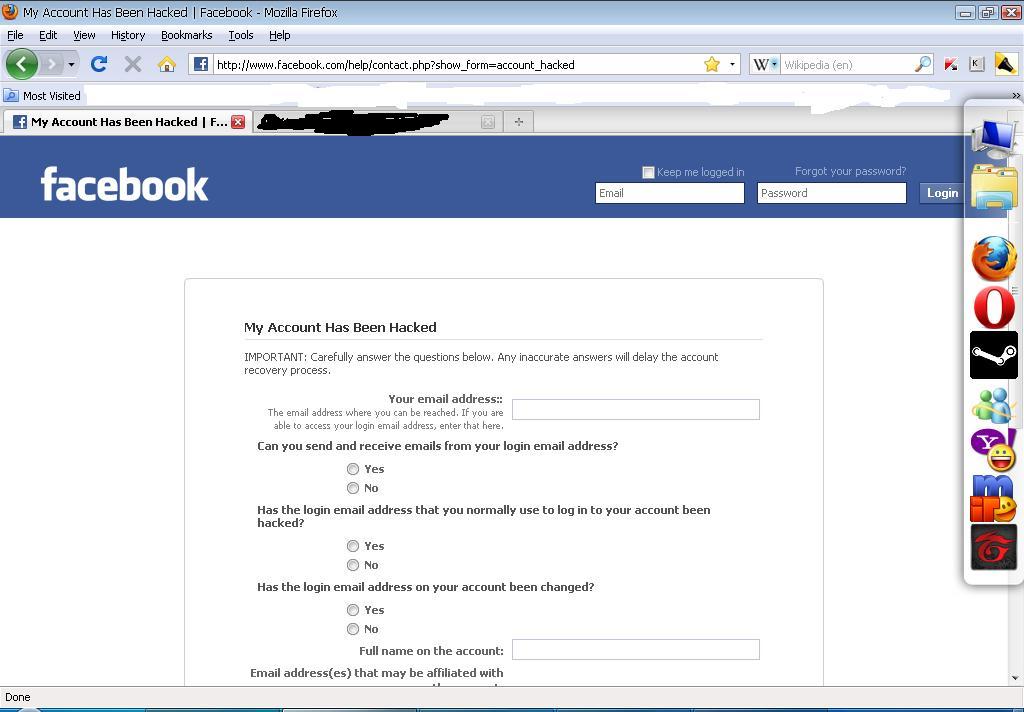
The expert explained that an attacker could deploy a special website to intercept OAuth traffic and steal tokens that grant access to visitors' Facebook accounts. As a result, the “hacker” will be able to send messages, post in the feed, change account information, and perform any other actions on behalf of the victim.
In addition, the cybercriminal gets the opportunity to establish control over accounts on third-party resources, which can be used for authorization using Facebook. Many web services now provide this opportunity, including the social network Instagram, streaming services Netflix and Spotify, and the dating app Tinder.
Company response
Baikar informed Facebook about the discovered vulnerability on December 16, 2019. To his surprise, the company acknowledged the presence of the "hole" on the same day. What's more, she immediately released a fix.
Security researcher Amol Baikar found a way to hack any Facebook account using a decade-old flaw
However, later the researcher found errors in its implementation, about which he notified the company representatives on January 3, 2020.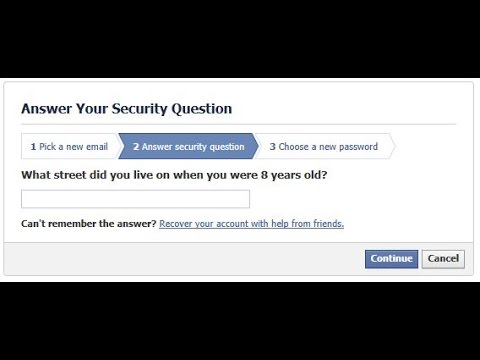 On January 10, Facebook eliminated the shortcomings identified by Baikar.
On January 10, Facebook eliminated the shortcomings identified by Baikar.
On February 20, the expert received a $55,000 reward from Facebook as part of the Bug Bounty program for his work.
Facebook incidents and leaks
Over the past few years, Facebook has repeatedly found itself at the center of various scandals due to a careless attitude to the privacy of social network users, as well as the presence of serious vulnerabilities in other company products.
Andrey Chapchaev, InfoTeKS: The level of cyber threats is growing, it is necessary to accelerate in the pace of development of information security
Safety
For example, in July 2019, a vulnerability was discovered in the mobile version of Instagram (part of the Facebook ecosystem) that allowed an attacker to reset the password for absolutely any account and gain full control over it.
In April 2019, Facebook was convicted that when registering on a social network, a user's password to his email might be requested if the client's email service causes some suspicions in the system. The list of "suspicious" was also the popular Russian service "Yandex.mail".
The list of "suspicious" was also the popular Russian service "Yandex.mail".
In March 2019, it was discovered that tens of thousands of company employees could have access to other people's Facebook and Instagram pages, since the passwords of hundreds of millions of users were stored unencrypted on the company's servers. Moreover, the social network officially recognized the existence of a problem only after a third-party information security specialist with connections within the company spoke about it on the Internet.
In September 2018, Facebook acknowledged the data breach of over 50 million account holders. The cause of the hack was a serious vulnerability in the Facebook code. It was eliminated as soon as possible, and law enforcement agencies were notified about the incident.
Alexey Pavlov, Rostelecom-Solar: Now there is a transformation of the established ideas about information security as a strictly internal function
Safety
In November 2018, it became known that the social network was unable to repel cybercriminals, as a result of which personal information about more than 120 million network users ended up in the hands of hackers. The data was put up for sale at a price of 10 cents per profile.
The data was put up for sale at a price of 10 cents per profile.
Between 2007 and 2014 The social network transmitted information about its users to the British analytical company Cambridge Analytica, as a result of which 87 million people were affected.
- Can Russian BI replace Western platforms? ViRush 2022 speakers are ready to tell you about their experience.
Dmitry Stepanov
4 ways to get someone else's Facebook passwords
Posted by Nelson Aguilar
Despite the fact that over the years there have been repeated security incidents on Facebook, many people continue to use this social network. Moreover, the number of new users is constantly growing, which allows Facebook to set new records. As of December 31, 2017, the monthly audience on Facebook was 2.13 billion users, the average daily audience is about 1.4 billion.
Part of our life is spent on Facebook. We share our birthdays and anniversaries, our vacation plans, and our current location. We share the dates of the birthdays of our children and the dates of the death of our parents. We talk about the most pleasant events and difficult thoughts. In general, we disclose many aspects of our life. There are even entire books written by clinical psychologists that detail just how much of an impact Facebook has on our emotions and relationships.
However, we often forget that we are being watched.
We use Facebook as a means of communicating with friends, but there are people who use this social network for malicious purposes. We disclose information that others can use against us. Attackers know when we are not at home, and how long our absence will last. They know the answers to security questions and, in fact, can steal our personal data using the information that we voluntarily indicate in a public profile.
Figure 1: Login page on Facebook (Source: Digital Trends )
The worst part is that the more technologically advanced our lives become, the more vulnerable we become to intruders.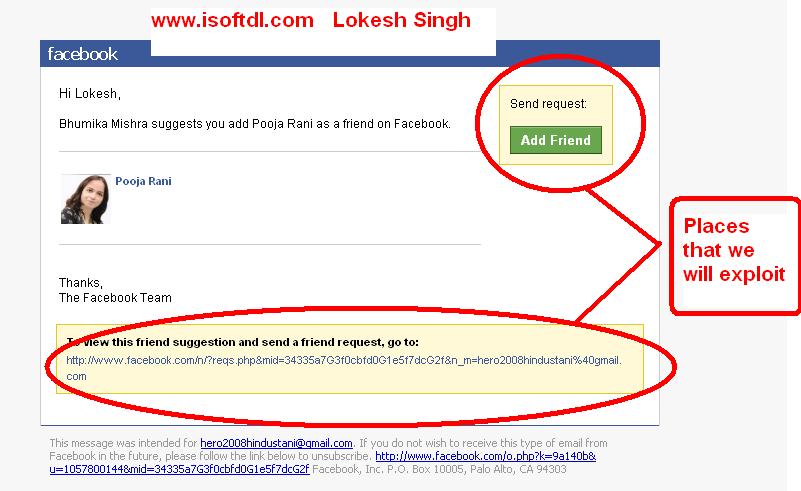 Even if we share incomplete information, in case of urgent need, knowledgeable people can access our email and Facebook account in order to fill information gaps regarding our personal data.
Even if we share incomplete information, in case of urgent need, knowledgeable people can access our email and Facebook account in order to fill information gaps regarding our personal data.
In fact, you don't even need to be a professional hacker to gain access to someone else's Facebook account.
Getting access to your account can be as easy as installing the Firesheep extension. Moreover, on Facebook, you can access someone else's account even without knowing the password. You just need to choose three friends to send the code. Next, you enter the three codes received and get access to your account. It doesn't get easier.
In this article, I'll show you several ways how hackers and ordinary people can access your Facebook account. After describing each method, a method will be given to protect your account from a specific method.
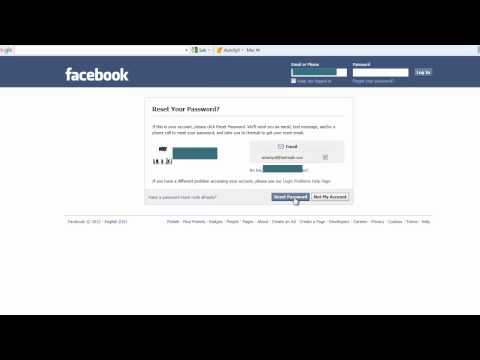
Method 1: Reset password
The easiest way to gain access to someone else's Facebook account is to reset the password. It is easier to implement this method for those people who are on the friends list of the person whose account is planned to be hacked.
It is easier to implement this method for those people who are on the friends list of the person whose account is planned to be hacked.
- The first step is to get the email used during authorization (for example, in the contacts section of the profile). Hackers use utilities like TheHarvester. More information on this topic can be found in this guide.
- Click on the link Forgotten account? and enter the victim's email. After the account appears, click on This is my account .
- You will be asked if you want to reset your password via email. Since we will be accessing by other methods, click on No longer have access to these?
- The question How can we reach you? Enter an email address that you have access to. This address must not be linked to any Facebook account.
- You will be asked to answer a question. If you know the victim well, you can probably answer this question.
 Otherwise, you can try to find the answer. If the correct answer is found, you will be able to change the password. Next, you need to wait 24 hours to log into the victim's account.
Otherwise, you can try to find the answer. If the correct answer is found, you will be able to change the password. Next, you need to wait 24 hours to log into the victim's account. - If you could not find the answer to the question, click on Recover your account with help from friends (recovering access through friends). Next, you will need to select from 3 to 5 friends to whom the code will be sent so that you can restore access to your account.
Figure 2: List of friends through which you can restore access to your account
- Passwords will be sent to the selected friends, which must be entered on the next page. You can either create from 3 to 5 fake accounts and add yourself as a friend to the victim, or choose those friends who agree to share the password sent to you.
Figure 3: Page for entering passwords sent to selected friends
How to protect yourself
- When registering with Facebook, please use a separate and unlit email address.
- The secret question must be such that the answer cannot be guessed based on information from the public profile. No animal names or anniversaries. Should not even be used as the names of elementary school teachers, since this information can be found in the alumni album.
- Select three trusted friends to send the password to. Thus, you can protect yourself from sending your password to random acquaintances who intend to gain access to your account.
Method 2: Use Keylogger
Keylogger Software
Keylogger Software is an application that reads all keystrokes without the user's knowledge. First, this application must be downloaded manually to the victim's computer. The keylogger then starts running in the background and intercepts all keystrokes. You can configure so that all the collected information is sent by e-mail.
To get started, you can read the guide for installing keylogger on the target computer. If this method doesn't work for you, you can look for free keyloggers or try writing your own in C++.
If this method doesn't work for you, you can look for free keyloggers or try writing your own in C++.
Figure 4: Parameters of one of the keyloggers
Hardware keylogger
Hardware keyloggers work in exactly the same way as software keyloggers, except that you need to connect a USB flash drive with software stuffing to the victim's computer , where all intercepted keystrokes will be stored. Subsequently, you only need to insert the USB flash drive into your computer and extract the collected information.
There are several varieties of hardware keyloggers. Models like Keyllama must be connected to the victim's computer and can run on any operating system. To receive the collected information, you must have physical access to the device. Alternative option: Wi-Fi enabled keylogger. The collected information can be sent by e-mail or downloaded via Wi-Fi.
Figure 5: Hardware Keyloggers
How to protect yourself
Use a firewall that will monitor network activity and track suspicious activity, as keyloggers usually send the collected information over the Internet.
- Install a password manager. Password managers will automatically fill out all important forms without using the keyboard, and keyloggers can only intercept keystrokes.
- Install updates in a timely manner. As soon as the developer company learns that vulnerabilities have appeared in the application, work begins on creating patches. Older versions of software can cause additional holes in your system.
- Change passwords. If you still don't feel secure, you can change your passwords every two weeks. At first glance, this approach seems too radical, but on the other hand, passwords stolen by intruders will lose their relevance too quickly.
Method 3: Phishing
Although this scenario is much more difficult to implement than the previous two, phishing remains one of the most popular ways to gain access to someone else's account. The most popular type of phishing involves creating a fake login page. A link to this page is usually sent to the victim's email and is no different from a real authorization form. One of the difficulties is that you need to create an account on a web host and, in fact, the fake page itself.
One of the difficulties is that you need to create an account on a web host and, in fact, the fake page itself.
Figure 6: Fake login page
The easiest way to create such a page is to read the website cloning tutorial. Then you will need to refine the form so that the information entered by the victim is saved somewhere. The implementation of this method is complicated by the fact that, on the one hand, users have become very careful, on the other hand, phishing filters in email services are constantly improving. However, nothing is impossible, especially if you clone Facebook completely.
How to protect yourself
- Do not click on suspicious links in emails. If the email asks you to sign in using a link, be careful. Check the URL first. If you still have doubts, log in directly to the Facebook website.
- Phishing is not necessarily done via email. Links can be distributed through websites, chats, text messages, and so on.
 Even pop-up ads can be malicious. Never click links that look suspicious, and especially those where you are asked to enter any confidential information.
Even pop-up ads can be malicious. Never click links that look suspicious, and especially those where you are asked to enter any confidential information. - Use antivirus and web threat protection applications (Norton, McAfee, etc.).
Method 4: Man-in-the-Middle Attack
If you are close to the target, you can trick the victim into connecting to a fake Wi-Fi network to steal accounts. Utilities like Wi-Fi Pumpkin allow you to create fake Wi-Fi networks based on a wireless network adapter and a Raspberry Pi. After you get close to the target with the configured equipment, and the victim connects to the fake network, you can analyze the traffic or redirect to a fake authorization page. You can even replace individual pages and leave the rest intact.
Figure 7: A small computer based on a clone of a wireless network to intercept traffic (photo by SADMIN/Null Byte) .
- Be especially careful with chains outside public establishments.
 For example, a chain named "Google Starbucks" should be suspect if there is no Starbucks within a few miles. Since the hackers have already collected some data on you, your computer or phone will connect to a fake network, since the name of this network has already been used before.
For example, a chain named "Google Starbucks" should be suspect if there is no Starbucks within a few miles. Since the hackers have already collected some data on you, your computer or phone will connect to a fake network, since the name of this network has already been used before. - If you are having problems connecting to a Wi-Fi network, check the list of neighboring networks to see if there are copies of your network names.
- If the router asks you to enter a password to turn on the Internet to update the firmware, or shows you a page with many grammatical errors, it is very likely that you have connected to a fake hotspot and someone is trying to steal your account.
Extra Hacks
More advanced users can check out two more tutorials: Same Origin Policy Facebook hack and Facebook Password Extractor (the second method is a bit easier).
How to protect yourself
- In the Account Settings, in the Security section, check the Secure Browsing option.
 Firesheep will not be able to intercept cookies if you are using a secure protocol (such as HTTPS).
Firesheep will not be able to intercept cookies if you are using a secure protocol (such as HTTPS). - Always enabled SSL. Use the HTTPS-Everywhere and Force-TLS extensions for Firefox.
- After you finish working with the site, end the authorization session. Firesheep cannot support authorization if you have ended your session.
- Use only trusted Wi-Fi networks. A hacker might be sitting next to you at a Starbucks coffee shop looking through your mail without your knowledge.
- Use a VPN. Since in this case all your traffic will be encrypted, even if an attacker intercepts information using fake Wi-Fi, they will not be able to extract anything useful.
Conclusion
Social networks allow you to keep in touch with old friends and meet new people. You can create events in a few clicks, send greeting cards, confess your love to your parents and other half.
Even with the existing account hacking options we've looked at, it's still possible to use social media and stay protected.