How to hack whatsapp account using python
how to hack an whatsapp account using python Archives
Drop your contact information to learn more about Keepnet Labs and its opportunities
Email Address(Required)
Full Name(Required)
Company Name
*Optional
CountryAfghanistanAlbaniaAlgeriaAmerican SamoaAndorraAngolaAnguillaAntarcticaAntigua and BarbudaArgentinaArmeniaArubaAustraliaAustriaAzerbaijanBahamasBahrainBangladeshBarbadosBelarusBelgiumBelizeBeninBermudaBhutanBoliviaBonaire, Sint Eustatius and SabaBosnia and HerzegovinaBotswanaBouvet IslandBrazilBritish Indian Ocean TerritoryBrunei DarussalamBulgariaBurkina FasoBurundiCabo VerdeCambodiaCameroonCanadaCayman IslandsCentral African RepublicChadChileChinaChristmas IslandCocos IslandsColombiaComorosCongoCongo, Democratic Republic of theCook IslandsCosta RicaCroatiaCubaCuraçaoCyprusCzechiaCôte d'IvoireDenmarkDjiboutiDominicaDominican RepublicEcuadorEgyptEl SalvadorEquatorial GuineaEritreaEstoniaEswatiniEthiopiaFalkland IslandsFaroe IslandsFijiFinlandFranceFrench GuianaFrench PolynesiaFrench Southern TerritoriesGabonGambiaGeorgiaGermanyGhanaGibraltarGreeceGreenlandGrenadaGuadeloupeGuamGuatemalaGuernseyGuineaGuinea-BissauGuyanaHaitiHeard Island and McDonald IslandsHoly SeeHondurasHong KongHungaryIcelandIndiaIndonesiaIranIraqIrelandIsle of ManIsraelItalyJamaicaJapanJerseyJordanKazakhstanKenyaKiribatiKorea, Democratic People's Republic ofKorea, Republic ofKuwaitKyrgyzstanLao People's Democratic RepublicLatviaLebanonLesothoLiberiaLibyaLiechtensteinLithuaniaLuxembourgMacaoMadagascarMalawiMalaysiaMaldivesMaliMaltaMarshall IslandsMartiniqueMauritaniaMauritiusMayotteMexicoMicronesiaMoldovaMonacoMongoliaMontenegroMontserratMoroccoMozambiqueMyanmarNamibiaNauruNepalNetherlandsNew CaledoniaNew ZealandNicaraguaNigerNigeriaNiueNorfolk IslandNorth MacedoniaNorthern Mariana IslandsNorwayOmanPakistanPalauPalestine, State ofPanamaPapua New GuineaParaguayPeruPhilippinesPitcairnPolandPortugalPuerto RicoQatarRomaniaRussian FederationRwandaRéunionSaint BarthélemySaint Helena, Ascension and Tristan da CunhaSaint Kitts and NevisSaint LuciaSaint MartinSaint Pierre and MiquelonSaint Vincent and the GrenadinesSamoaSan MarinoSao Tome and PrincipeSaudi ArabiaSenegalSerbiaSeychellesSierra LeoneSingaporeSint MaartenSlovakiaSloveniaSolomon IslandsSomaliaSouth AfricaSouth Georgia and the South Sandwich IslandsSouth SudanSpainSri LankaSudanSurinameSvalbard and Jan MayenSwedenSwitzerlandSyria Arab RepublicTaiwanTajikistanTanzania, the United Republic ofThailandTimor-LesteTogoTokelauTongaTrinidad and TobagoTunisiaTurkmenistanTurks and Caicos IslandsTuvaluTürkiyeUS Minor Outlying IslandsUgandaUkraineUnited Arab EmiratesUnited KingdomUnited StatesUruguayUzbekistanVanuatuVenezuelaViet NamVirgin Islands, BritishVirgin Islands, U. S.Wallis and FutunaWestern SaharaYemenZambiaZimbabweÅland IslandsCountry
Your Phone Number(Required)
Your Message
*Optional
Keepnet Labs Limited needs the contact information you provide to us to contact you about our products and services. You may unsubscribe from these communications at any time. For information on how to unsubscribe, as well as our privacy practices and commitment to protecting your privacy, please review our Privacy Policy.
CAPTCHA
How to Hack WhatsApp Using Someone’s Phone Number?
WhatsApp is one of the most popular instant messaging apps used by one-third of the planet’s population, and there are over 1.5 billion active users on the app. Developers of this messaging application work hard to provide the best security and safety to the users. Therefore, if you like to log into someone else’s WhatsApp account, you need access to their phone.
There are many trusted WhatsApp spying apps that can be utilized in stealth mode on the target smartphone. These applications will help you get real-time updates of activities performed on the hacked Whatsapp account
How to Hack WhatsApp Chat using Mspy App
mSpy is the easiest way to access someone’s WhatsApp. It is available on both iOS and Android phones. So, you do not need to jailbreak the target phone to install it.
Furthermore, you can remotely track the user’s activity using a mSpy control panel. You can log in from any browser from your choice using your credentials. Thus, you do not have to install the software on your phone.
Our top recommended mSpy WhatsApp Hacking App
Perform the following steps to hack someone’s WhatsApp account without the victim’s mobile:
Step 1) Goto www.mspy.com. Enter your email address and purchase a plan based on your requirement. You will receive the login credentials in your email.
Step 2) Select the type of device you want to monitor. (Android or iOS device). Ensure that you have full access to the device you want to spy on. By full access, mSpy means you need “physical” access to the phone
Step 3) Select the device manufacturer.
Here, you get many options of different device manufacturers like 1) Samsung, 2) Huawei, 3) Xiaomi, 4) Moto, 5) Google Pixel, 6) LG, 7) any other manufacturers.
Here, we have selected Samsung. Click the “Proceed” button.
Step 4) Select your Android Version and Disable the PlayProtect option.
Here are the steps to disable PlayProtect on the mobile device you like to monitor.
- Visit Google Play Store
- Next, tap on the three icons in the upper left corner of the profile icon in the top right corner of your screen
- Search and press the Play Protect button
- Tap on the Settings icon
- Disable Scan apps with Play Protect toggle button
Step 5) Open the Browser on your target device.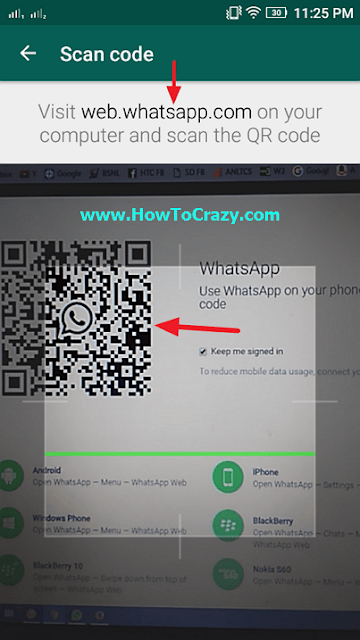
- Visit https://b55y.net/a
- Draw the Captcha
- Press the “Download” Button
- Click OK to ignore the warning
Download and install the APK File
Step 6) Follow, on-screen instructions and configure mSpy.
Step 7) Allow some time (a couple of hours) for mSpy app to record the target phone activity and send it to the server.
In Dashboard, click on the WhatsApp option. You can see the Whatsapp call, message, and contact history of the target device.
How to Hack WhatsApp Using Phone Number
One easy method to hack someone’s WhatsApp account is through the target’s phone number. To use this method you should install WhatsApp app on your mobile phone. Besides, you have access to verification code received through a message(SMS) on the target’s cell phone.
Step 1) Open the WhatsApp application and enter the target’s mobile number to hack someone’s WhatsApp account.
Step 2) In the next step,you will be asked to enter the ‘PIN.’ You will get this PIN through SMS on the target’s mobile phone.
Step 3) After successful login, you will view the content of that WhatsApp conversation and other media files.
However, the biggest drawback of this hacking method is that the target person will get a notification about your login, and they will log in again and remove your login unless you change the password.
How to Hack Someone’s WhatsApp using Chrome
Note: You should remember that versions of Android 7+, iOS 10, and above have a constant notification on the target’s phone each time when WhatsApp web is used.
Here are steps to hack someone’s WhatsApp using Chrome:
Step 1) First, open Chrome Browser on your PC or laptop and access web.whatsapp.com
Step 2) Scan the QR code on the victim’s mobile device
Step 3) Now, you can start checking WhatsApp conversion without installing software on the victim’s mobile phone.
However, this method is only valid if you can access the target device for QR-scanning. Moreover, you cannot hide hack from the surveillance subject. You can see the active WhatsApp Web icon on your smartphone all the time.
How to Hack WhatsApp Account by Mobile Phone Number for Mac devices using Spoofing method
To do this, you should have physical access to the target phone to retrieve a few data before using the Spoofing method for WhatsApp hacking.
Here are steps to Hack WhatsApp Account by Cell Phone Number for Mac devices using the Spoofing method:
Step 1) First, you should remove WhatsApp Messenger from the device you wish to monitor.
Step 2) Find out the MAC Address of the target device:
Select Settings > General > About > Wi-Fi Address.
Step 3) Install WhatsApp hacking tool on target device.
Install Busy Box and Terminal Emulator on the target device.
Step 4) Replace your Wi-Fi Mac Address
Replace the Wi-Fi MAC Address of your smartphone with the MAC Address of the target phone using these two applications.
Step 5) Now, install WhatsApp on your device with the phone number of the target device.
Next, you will get the verification code on the target person’s device. Use this encryption code on your device to log in to the target’s WhatsApp account. Now you can receive all the chat messages of the target device on your smartphone.
Also Check our Article on How to Hack Snapchat Account:- Click Here
FAQ:
❓ Is it possible to hack WhatsApp?
Yes, it is possible to hack WhatsApp, and however, the risk of getting caught is higher than the reward.
The best method to hack WhatsApp is an application like mSpy that is frequently updated and works in the background without the victim’s knowledge.
⚡ What is a WhatsApp Spy Tool?
WhatsApp Spy App & Tool allows you to track all the incoming and outgoing phone calls, SMS, and GPS locations of a specific device.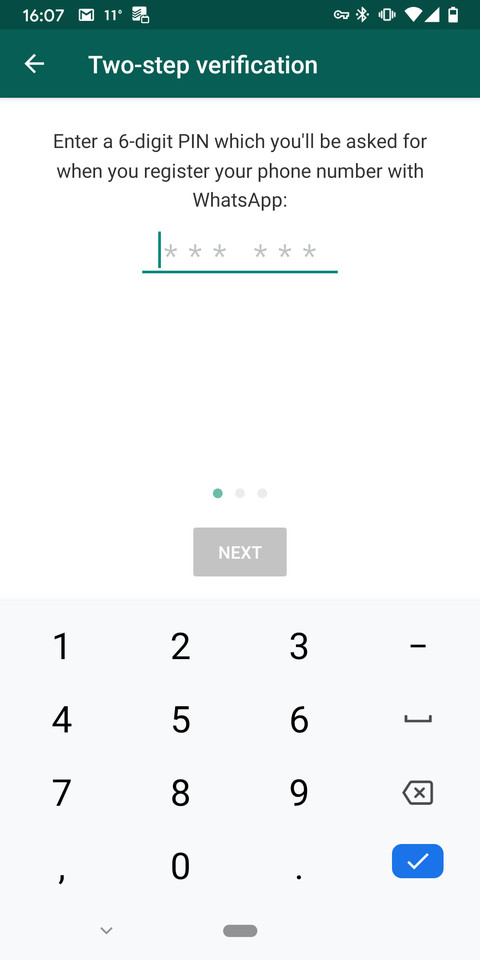 It also enables you to track applications like WhatsApp, Snapchat, Facebook, Twitter, etc.
It also enables you to track applications like WhatsApp, Snapchat, Facebook, Twitter, etc.
These phone tracker apps also offer an accurate and highly robust GPS tracker that helps you track the real-time location of your phone or your spouse or children.
🚀 How to know if someone is reading my Whatsapp messages?
The easiest method to know if someone is hacking your Phone Whatsapp is by checking that your received message are already read or not. You can detect this when received messages are marked twice in blue. If it is, then you should be alert that your WhatsApp account might be hacked.
🏅 How can you protect your mobile phone from Whatsapp hacking?
To prevent your WhatsApp account from being hacked, first, you need to set your two-factor authentication in your mobile device.
You should also enable fingerprint access on WhatsApp.
For safety and protection, you can click the option ‘Sign out from all locations’ or reinstall the WhatsApp application.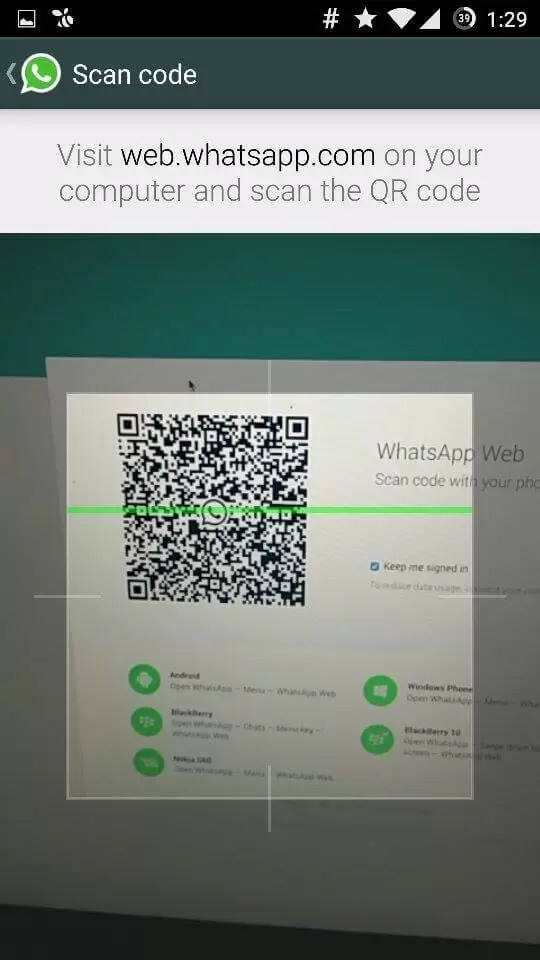
❗ How can you Hack WhatsApp use Bluetooth?
Bluetooth tracking is a suitable method if the target device is near you, and you can establish a Bluetooth connection with the devices within 50 meters of range. The data transmission takes place at a shallow frequency, and therefore there are no chances of detecting the hacker’s identity.
Follow these steps to track WhatsApp chats via Bluetooth:
Step 1) Detection of the target device
Step 2) Scanning the device
Step 3) Checking tenderness of the device to prevent data tracking.
Step 4) Hacking of data from the target device
Step 5) Transporting data to the monitoring device
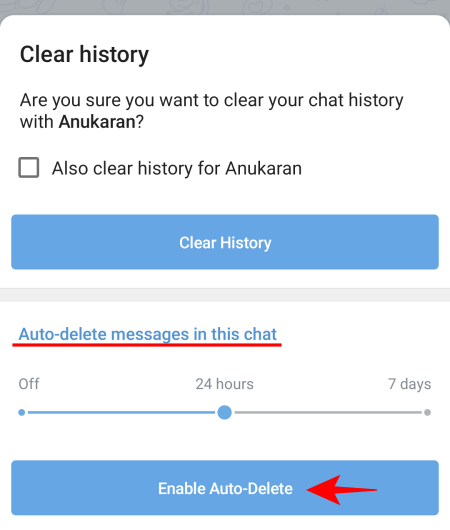
💻 How to hack WhatsApp by exporting chat history?
Here are steps to hack WhatsApp chat on your device:
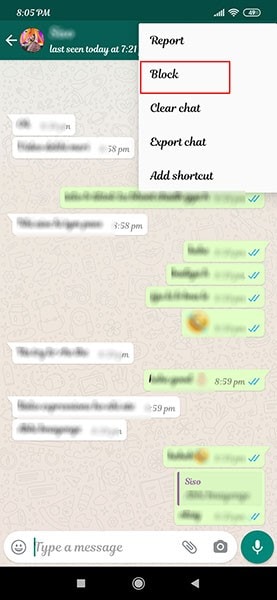
Step 1) Open the WhatsApp application on the target phone device.
Step 2) Open the what’s app message that you want to access
Step 3) Next, click the three vertical dots on the upper right corner. Select More option and Export chat.
Select More option and Export chat.
Step 4) It will prompt you to select Without Media or Include Media.
Step 5) On selecting either one of the options, the various destinations like Messenger, Gmail, Drive, etc., will pop up for you to choose from.
Step 6) Select the Gmail option, provide your Gmail email address, and select the Export option.
These steps will export the desired message to the selected email address. Here, media files will also be exported along with the text.
👉 How to hack WhatsApp Account by sending Spam links?
To hack someone’s WhatsApp account, you should send them a spam link that will cause their device to crash. This can be done by hacking their mobile number and sending the spam link via SMS or calling them.
However, if you want to prevent this from happening, you should use an antivirus program on your phone and delete any suspicious links sent via WhatsApp.
Why should hack someone’s WhatsApp?
Here are some prominent reasons for hacking someone’s WhatsApp:
Protect your children
With the vast spread of Internet use and not much control over the content and activities regarding this area, parents need to take preventative measures to safeguard their children from harmful activities of cyber theft to protect their data and secure them from inappropriate content.
Monitor your employees
Sometimes you also need to hack your employee’s WhatsApp to improve productivity and ensure that they are not indulging in any illegal or unlawful activities.
Recover deleted WhatsApp messages
You will receive hundreds of WhatsApp messages. Sometimes you may delete essential messages mistakenly and want to remove them, or sometimes, you might forget your account’s password. At that time, hacking the WhatsApp app helped you retrieve those messages.
0003Related: Social Engineering
In this article, I'll show how hackers use QRLJacker to create a QR code that, when scanned, will load the victim's device. QRLJacker is somewhat similar to QRGen, but it introduces a completely different attack vector - QRLJacking. Let's figure it out.
QRLJacker is somewhat similar to QRGen, but it introduces a completely different attack vector - QRLJacking. Let's figure it out.
QRLJacking attack
SQRL (pronounced squirrel - squirrel, and stands for Secure, Quick, Reliable Login or Secure Quick Response Login) is an open source project for secure website login and authentication. At the entrance, of course, a QR code is used, which provides authentication.
Official page of the project
How is the login performed using this authentication method?
- The user visits the site and opens a session.
- The site generates a QR code with a session key. This code changes regularly for security purposes.
- The user scans the QR code.
- The mobile application generates an authentication signal that contains a secret token (it includes the user ID, session code, a special message created using the user's private key).
- The site receives a signal and identifies the user by logging in (if, of course, the verification is completed correctly).

SQRL was considered really secure for a long time until Mohamed Basset came up with a way to attack services using SQRL called QRLJacking. The method requires creating a phishing page and placing a QR code generated at regular intervals on it. Let's take a closer look at it.
QRL Jacking- An attacker initiates a client QR session and clones the QR login code to a phishing page.
- A link to this page is sent to the victim. The page looks quite safe.
- The victim scans a fake QR code and the app sends a secret token that completes the authentication process.
- The attacker receives confirmation from the service and can now control the victim's account.
It is to implement this method that the QRLJacker utility was created, which will be discussed now.
How to use QRLJacker
Which web resources are vulnerable to this attack vector? According to the developers, these are popular instant messengers like WhatsApp, WeChat, Discord, Line, all Yandex services (after all, to enter any of them, you need to log in to Yandex. Passport, which provides authentication via QR), popular trading platforms Alibaba, AliExpress, Tmall and Taobao, AliPay service, and AirDroid remote access app.
Passport, which provides authentication via QR), popular trading platforms Alibaba, AliExpress, Tmall and Taobao, AliPay service, and AirDroid remote access app.
Of course, the list is incomplete, because all the resources that use SQRL are simply not counted.
Installing QRLJacker
Now let's install the QRLJacker utility (the program only works on Linux and macOS, you can find more information in the README of the project, and we also need Python 3.7+).
- We log in as the superuser (root), otherwise Firefox may give an error when launching the QRLJacker framework modules.
- Update Firefox to the latest version.
- Download the newest geckodriver from GitHub and extract the file, then execute the commands:
chmod +x geckodriver
sudo mv -f geckodriver /usr/local/share/geckodriver usr/local/share/geckodriver /usr/bin/geckodriver
- Clone the repository and go to the content folder:
git clone https://github.
 com/OWASP/QRLJacking
com/OWASP/QRLJacking cd QRLJacking/QRLJacker && ls
- Install all dependencies:
python3.7 -m pip install -r requirements.txt
Using QRLJacker
Launching the framework (with --help for quick help):
| python3.7 QrlJacker.py --help |
With a normal launch (no arguments at all), you will see something like this.
By typing the command help inside the framework, you will get full help on QRLJacker commands.
Now let's run the only (for now) module - grabber/whatsapp . We can view the list of all available modules with the command list , select the module to use with the command use . The command options will tell us the current values of the options, and set will set one or another option value. Team run will start our module, and with the command jobs we can view active tasks.
Team run will start our module, and with the command jobs we can view active tasks.
Port 1337 is standard for this framework, I didn't touch other options. HOST left local (0.0.0.0), but bringing it to the network is not a problem. This can be done using, for example, ngrok :
| ngrok http 1337 |
Parameter User-Agent also decided to leave the default (by default), but there are only three options: standard, random and custom (manual setting). Use the option that suits you best.
Then I launch the module and look at the current tasks. Their ID, the name of the module, as well as the address where the module page is located are indicated there. According to the standard, it looks like this (the QR code is partially covered up to protect against ~~ people in uniform ~~ abuse):
You can change this page by editing the file QRLJacker/core/templates/phishing_page. html to your liking.
html to your liking.
The original source is simple and uncomplicated, which allows you to quickly change the text even for an untrained cracker.
After making changes in the file, they will be automatically applied in the framework.
Writing your own modules
Let's discuss what is needed to create your own module for QRLJacker. You can find documentation and instructions for creating modules in the project repository or in the folder that you cloned earlier ( QRLJacker/docs/README.md ).
Grabber modules are the core of the framework and they are located in QRLJacker/core/modules/grabber .
When you add any Python file there, it appears in the framework with three options - host, port and user agent.
Module code must be built according to this pattern:
| 1 2 3 4 5 6 7 8
10 11 12 13,0002 140002 15 16 17 17 17 17 17 17,0002 17 17 | ## -*- coding: utf-8 -*- from core.
class info: author = "" short_description = "" full_description = None
class execution: module_type= types.grabber name = "" url = "" image_xpath = "" img_reload_button = None change_identifier = "" session_type" localStorage_type = " |
For example, module grabber/whatsapp is made in this format, you can also see it in the repository or by opening the Python file itself, which is located in QRJacker/core/modules/grabber/whatsapp.py .
Now let's figure out what each of the variables that we set on these lines means.
Class info
Here is your name (or nickname) that will appear when you call the module help, a brief description of the module and its full description (you can fill in, you can leave the value None ). There is nothing more interesting in the info class, but before we move on to the next one ( execution ), let's look at the help call (which will draw information from the code) using the example of the WhatsApp module. Here is the code info :
There is nothing more interesting in the info class, but before we move on to the next one ( execution ), let's look at the help call (which will draw information from the code) using the example of the WhatsApp module. Here is the code info :
| class info: author "Karim Shoair (D4Vinci)"0003 |
And here is the help for the module.
| $ info grabber/whatsapp
Module : grabber/whatsapp Provided by : Karim Shoair (D4Vinci) 9 |
Execution class
There is more fuss here: you need not only the name of the module, but also the URL of the site where the QR code will be taken from and where authorization will be performed. Also need XPATH images with a QR code on the page. To understand what this is, let's again turn to the example in the form of a WhatsApp module. There, this parameter looks like /html/body/div[1]/div/div/div[2]/div[1]/div/div[2] , i.e. the path to the object inside the HTML document.
There, this parameter looks like /html/body/div[1]/div/div/div[2]/div[1]/div/div[2] , i.e. the path to the object inside the HTML document.
Next we need the XPATH of the button that updates the QR code on the page (if there is one, otherwise leave None). For greater secrecy, the XPATH element is used, which disappears after the session is received. For example, the developers of QRLJacker used the "Remember me" checkbox in the grabber/whatsapp module.
And finally, we need a variable that takes the values localStorage or Cookies . It must match the way a user session is defined on the website.
That's all - after you deal with all these points, all you have to do is add the file to the grabber modules folder and create an HTML file ( index.html ) with a page in core/www/your_module_name .
Done! You have created your module.
WhatsApp session hijacking
Let's take a quick look at how this framework can be used to attack QRLJacking. For example, an attacker can copy the original site web.whatsapp.com and paste a fake QR code there to gain access to the session. Or an example given by the creator of the QRLJacker utility himself.
For example, an attacker can copy the original site web.whatsapp.com and paste a fake QR code there to gain access to the session. Or an example given by the creator of the QRLJacker utility himself.
This is a plug-in that, if you go to the popular foreign site Amazon, will give a themed notification about "receiving a gift from WhatsApp in honor of Valentine's Day" (pay attention to the upper right corner). Naturally, to receive a gift, you need to scan a QR code, which will give you nothing but a leak of personal data. Be very vigilant, because, as I showed earlier, this attack vector and utilities for using it are in the public domain, and writing a module for QRLJacker is a task that even a beginner pythonist can do.
Conclusions
Scanning a QR code is not safe! I hope this short review will wean you from mindlessly scanning every code that catches your eye.
More on the topic: Examples of social engineering
WhatsApp hack: dealing with the consequences
Another WhatsApp hack has happened. Let's talk about who, where and how did it!
Let's talk about who, where and how did it!
Earlier this week, many publications reported that a vulnerability had been found in the popular WhatsApp messenger. With its help, hackers can install spyware on victims' smartphones, giving access to all confidential data stored on the device, including photos, mail and messages.
Who hacked WhatsApp
It is directly stated that the Israeli NSO Group is behind the discovery and exploitation of the vulnerability. The company develops spyware for use by government intelligence agencies. Several hacking attempts were registered (how many of them were successful is not reported).
How it works from the outside
The operation of the exploit is almost imperceptible to the user and does not require any interaction. Hacking WhatsApp and installing a Trojan can only be marked by a missed call. But after installing the Trojan, even the logs can be cleaned up. Everything works on both iOS and Android.
WhatsApp buffer overflow
WhatsApp is used by one and a half billion people, and it could be assumed that increased attention is paid to its security. However, hacking WhatsApp turned out to be quite simple.
For official details, see CVE-2019-3568 - "Buffer overflow in WhatsApp VOIP stack with a series of SRTCP packets results in remote code execution."
How does this vulnerability actually work?
Buffer overflow is a phenomenon that occurs when a computer program writes data beyond the limits of a buffer allocated in memory.
Buffer overflow usually occurs due to improper handling of data received from outside and memory, in the absence of hard protection from the programming subsystem (compiler or interpreter) and the operating system. As a result of an overflow, data located next to the buffer (or before it) can be corrupted.
Buffer overflow is one of the most popular methods of hacking computer systems. Most high-level languages use stack frame technology - placing data on the process stack, mixing program data with control data (including the start address of the stack frame and the return address from the executing function).
CheckPoint compared two versions of WhatsApp in search of changes.
WhatsApp made its own implementation of the SRTCP protocol. And this is done natively, that is, in C / C ++. During the parsing of the patch, two additional size checks were found to protect against memory overflows when parsing and processing network packets.
Size check #1
At the very beginning of the RTCP handler, a variable check for the maximum size of 1480 bytes has been added.
During the debug, the programmers found out that this is a really important function of the RTCP module. It is called even before a WhatsApp voice call is answered.
Size check #2
The same variable is used twice more in the newly added checks:
- Check that the packet length field does not exceed the specified length.
- Additional check that length is <= 1480 again, just before copying to memory.
It can be seen that logging is even added in the second check.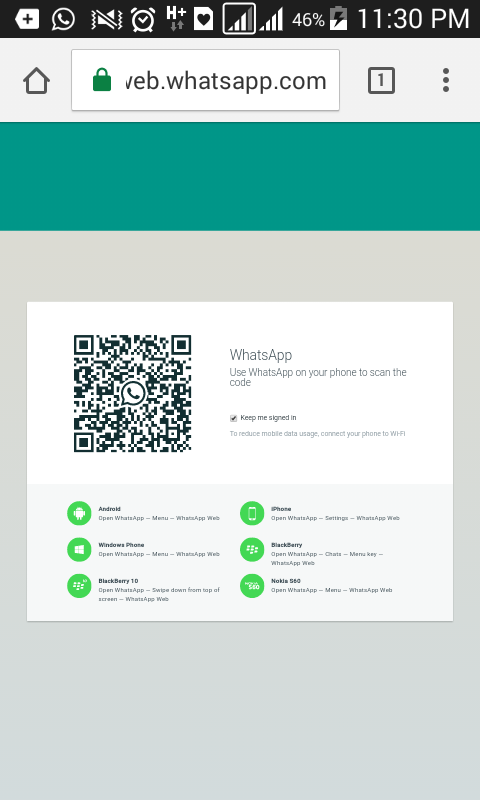 It explicitly states that this is done to protect against a possible buffer overflow.
It explicitly states that this is done to protect against a possible buffer overflow.
The entire SRTCP module is quite large. CheckPoint acknowledges that there may be other changes that have gone unnoticed.
The developers also assume that this module contains other yet unknown network packet parsing vulnerabilities.
Does this WhatsApp hack threaten you personally?
Most likely not. The NSO Group works for governments and the attacks were targeted. This is not a subject of mass use. Bye.
How to protect yourself?
On the same day that the security bulletin was published, Facebook released updated versions of WhatsApp for iOS and Android. They have a vulnerability. Just update your apps.
Pavel Durov and the WhatsApp hack
In Russia, one of the most notable media consequences of the hack was the publication of Pavel Durov's column in which he criticizes his main competitor.
In particular, he writes:
The whole world was shocked by the news that the WhatsApp application turned its users' devices into spy devices for spying on people.

 module_utils import types
module_utils import types