How to hack telegram chats
Telegram App Store Secret-Chat Messages in Plain-Text Database
Spread this blog
EDIT: The following post * was not on a rooted or jailbroken device *. In order to access the plain-text secret-chat database containing the messages, we used our implementation of CVE-2014-3153. The claims that the device is rooted / jailbroken are incorrect and misleading.
I will start by quoting CryptoFail blog
“Telegram is an encrypted instant messaging app for iOS and Android devices. Obviously, I wouldn’t mention it on this blog if its crypto was perfect. In fact, it’s far from perfect. It’s almost horrifying.
I’m not sure if it was in response to some good criticism, but Telegram recently announced a crypto contest. Basically, if you can recover an email address that was encrypted with their secure messaging app, you can win $200,000 USD worth of Bitcoin.
Unfortunately, the contest is useless. Neither users nor Telegram developers will learn anything from the contest results.
But, Telegram will still be able to point to the contest and say, “Look! No one has won the contest, so our software is secure!” Naive users will believe Telegram, and they will feel safe using dangerously broken encryption.”
I decided to take a closer look at the contest. My intention was to see if I could read encrypted messages without being on-the-wire. I conducted a test using Android OS version 4.4.2.
Telegram claims to be a privacy oriented messaging app capable of encrypting personal and business secrets – only they are not. A critical vulnerability discovered by Zimperium Mobile Security Labs exposes their more than 50 million users who believe the app provides the security to chat freely. Let me explain how we stumbled onto this vulnerability.
The old Crypto contests from Telegram reference breaking its protocol while being in the middle of an encrypted conversation. This is not a sound idea for two reasons:
1. In the real world hackers do not play by the rules.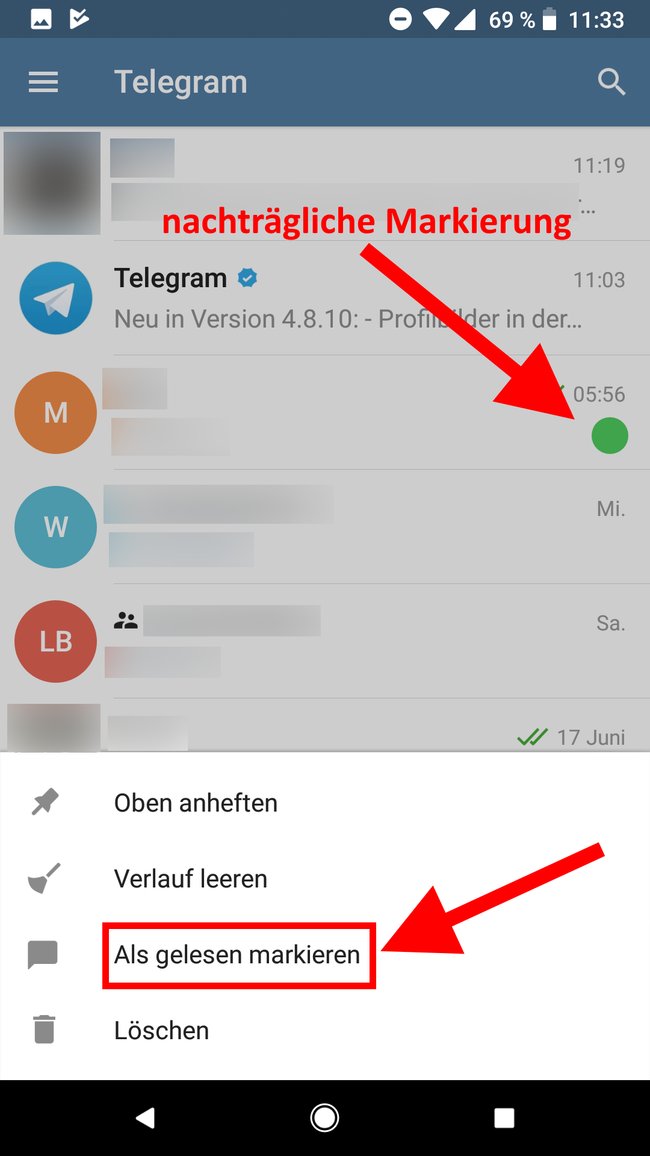
2. This assumes hackers would try to break Telegram’s encryption in the middle, when you can instead find weaknesses in other protocols which provide more benefits (e.g: GoToFail to bypass SSL encryption on iOS).
The New Crypto contests by Telegram says, “…and this time contestants can not only monitor traffic, but also act as the Telegram server and use active attacks, which vastly increases their capabilities.”
As a result, I am not going to break the encryption simply by avoiding it. I am going to bypass the encryption by simulating an active attack on the device.
The best way to do this is by understanding the anatomy of cyberattacks and the architecture of mobile devices. It did not take me long to install Telegram’s software, find both the encrypted and non encrypted texts that I sent, along with a Database containing all of the above.
Telegram’s website says: “A Secret Chat is a one-on-one chat wherein all messages are encrypted with a key held only by the chat’s participants. By definition, it follows that no third parties can access the decrypted content without access to one of the devices.” This raises 2 questions: First, assuming a user has no physical access to the device and the device was hacked remotely – how easy would it be for the attacker to retrieve the end-to-end encryption deployed by Telegram? Second, if and how are the Telegram’s Secret Chats encrypted on the mobile device?
By definition, it follows that no third parties can access the decrypted content without access to one of the devices.” This raises 2 questions: First, assuming a user has no physical access to the device and the device was hacked remotely – how easy would it be for the attacker to retrieve the end-to-end encryption deployed by Telegram? Second, if and how are the Telegram’s Secret Chats encrypted on the mobile device?
It’s easier to find a vulnerability in a phone and hack it remotely via URL/PDF/Man-In-The-Middle and other attack techniques that I have discussed before. Once you hack a mobile phone, you need to elevate your privileges in order to gain control of the device. This can be easily done using a Kernel exploit.
If you are new to mobile security, I’ve included some examples below that demonstrate how an individual can perform an attack on a mobile device remotely. This type of hack would be even easier for nation-state actors with even more resources, time and money at their disposal:
1. Client-side vulnerability: Chrome exploit – Pwn2Own Autumn 2013
Client-side vulnerability: Chrome exploit – Pwn2Own Autumn 2013
2. Kernel exploit – CVE-2014-3153 (a.k.a – TowelRoot)
Let’s take a look at what I did. I started by creating secret messages within the Android version of the Telegram app with the intention of finding it non-encrypted somewhere. I assumed that the Secret-Chat messages were encrypted in memory, or at least in the local database. Is that too much to ask for from a privacy and security oriented text messenger?
If you take a screenshot as the attacker, a notification will be sent to both users – so one can assume that security and privacy must be a top priority for Telegram. However, to believe that an attacker will take a screenshot instead of taking complete control of the device is a bit naive.
I gave Telegram the benefit of the doubt and did not look for the more common mistakes that you can expect to see in non-security oriented programs. I simulated an attack originating from an App / Client Side vulnerability that gains permissions by running a kernel exploit (I used CVE-2014-3153)- as described above. There are cleaner ways to dump the results, but I just wanted to provide a proof of concept (POC). Telegram has a feature called “Secret Chat” with a lock (see above) that feels secure. I dumped the process memory of Telegram and searched for strings that contain the word I sent and received in the picture above.
There are cleaner ways to dump the results, but I just wanted to provide a proof of concept (POC). Telegram has a feature called “Secret Chat” with a lock (see above) that feels secure. I dumped the process memory of Telegram and searched for strings that contain the word I sent and received in the picture above.
As you can see – the words Woof, Text, Shlookido, Cookiedo, Tambalul and NotSoEncryptedInMemory are, well… not encrypted in the process memory. Any attacker that gains access to the device can read the messages without too much effort. The Secure-Chat messages can be read in clear-text in Telegram’s memory. This discovery prompted me to check to see whether there is an easier way to access the content of the messages – and I was successful.
While Telegram’s communication was supposed to be encrypted (it was broken as well…)
To complete my research I accessed the shell I received previously from running CVE-2014-3153 to look at the App’s files at /data/data/org. telegram.messenger/ and I discovered a file called Cache4.db in the app’s “files” folder:
telegram.messenger/ and I discovered a file called Cache4.db in the app’s “files” folder:
I assumed “enc_chats”, “enc_tasks_v2”, enc probably stood for encrypted so I fetched this file and examined it. The file contained our secret messages in plain-text!
One of the most interesting features in the Telegram messaging app is the “Delete” messages function. My next attempt was designed to access and retrieve sensitive information previously deleted by the user. I wanted to retrieve deleted messages directly from the memory or cache4.db files.
1. Memory:
I clicked on options->Set Self Destruct to 5 seconds, and I expected the message to be deleted but nothing happened on either phone. It looked like a bug, not a security related issue.
I deleted the message by clicking on options->delete.
An inspection of the cache4.db file showed no signs of the conversation. (A deleted message might be more interesting to an attacker. ) After examining the cache4.db file I looked at the memory and was able to find the original conversation after I had deleted it from the memory.
) After examining the cache4.db file I looked at the memory and was able to find the original conversation after I had deleted it from the memory.
Disclosure Timeline:
Below is the disclosure timeline that we follow as part of the Zimperium Zero-Day Disclosure Policy. We have made several attempts to contact Telegram’s security team and have yet to receive a response from Telegram for over 30 days. For reference, here is a copy of our policy: 30 days zero-day policy.
1. 17/1/2015 – Vulnerability found
2. 18/1/2015 – Vulnerability responsibly disclosed ZVD-2015-0100, ZVD-2015-0101, ZVD-2015-0102 according to our 30 days zero-day policy – no response from vendor.
3. 23/1/2015 – Asked vendor to comment – no response
4. 3/2/2015 – Asked vendor to comment – no response
5. 6/2/2015 – Asked vendor to comment – no response
6. 23/2/2015 – Vulnerability made public
Recommendation
My conclusion is simple.
While Telegram was founded upon a noble goal of providing privacy to consumers everywhere at no cost, they have fallen short of their objective by focusing purely on data-in-transit versus protecting data-at-rest on the mobile device itself. What is regrettable is that I approached Telegram multiple times and have yet to receive a response. Telegram’s so-called powerful encryption is not protecting users any better than any other page or app that uses SSL. If you are using Telegram because you want to ensure your privacy and the privacy of the messages you are sending, be aware that it will not stop sophisticated hackers from reading your messages. We highly recommended adding additional protection to your mobile device that can detect device-level cyberattacks.
In order to better protect critical communication, I would have expected Telegram (or any messaging software) to encrypt chat strings in memory, as-well as encrypting the conversations in the cache4.db file. Zimperium’s Mobile Threat Defense system detected the entire attack chain that was performed in-order to obtain the content of the secret messages
About Zimperium
Zimperium is the leader in Enterprise Mobile Security. The Zimperium Mobile Threat Defense system delivers enterprise-class protection for Android and iOS devices against the next generation of advanced mobile threats. Developed for mobile devices, Zimperium uses patented, behavior-based analytics that sit on the device to protect mobile devices against host and network-based threats wherever business takes them.
The Zimperium Mobile Threat Defense system delivers enterprise-class protection for Android and iOS devices against the next generation of advanced mobile threats. Developed for mobile devices, Zimperium uses patented, behavior-based analytics that sit on the device to protect mobile devices against host and network-based threats wherever business takes them.
Follow me on twitter (@ihackbanme)
Microsoft says hackers are using Telegram to connect with, hack VIPs at cryptocurrency companies
Emerging technology, Leadership
Menghan XiaoA Bitcoin ATM is seen at the Clark Street subway station on June 13, 2022 in the Brooklyn Heights neighborhood of Brooklyn in New York City. According to a new blog post from Microsoft, a hacking group being tracked under the designation DEV-0139 has been using Telegram groups to facilitate communication between VIP clients and cryptocurrency exchange platforms, drawing their targets from among the members. (Photo by Michael M. Santiago/Getty Images)
(Photo by Michael M. Santiago/Getty Images)
Threat actors have been directly targeting cryptocurrency investment companies using Telegram chat groups.
According to a new blog from Microsoft, a hacking group being tracked under the designation DEV-0139 has been using Telegram groups to facilitate communication between VIP clients and cryptocurrency exchange platforms, drawing their targets from among the members.
“The threat actor posed the target to a different chat group and pretended to ask for feedback on the fee structure used by cryptocurrency exchange platforms,” Microsoft explained. “[They] had a broader knowledge of this specific part of the industry, indicating that they were well prepared and aware of the current challenge the targeted companies may have.”
After building connections and winning the trust of the target, DEV-0139 sent out a malware-laced Excel file that included tables about fee structures among cryptocurrency exchange companies.
According to Microsoft, the group provided likely accurate data in the document to further increase their credibility. But once executed, the malicious file would compromise the victim’s machine, ultimately installing a backdoor to remotely access the system.
But once executed, the malicious file would compromise the victim’s machine, ultimately installing a backdoor to remotely access the system.
Microsoft noted that an investigation showed that there may be other related campaigns being run by the same threat actor using the same techniques.
“Further investigation through our telemetry led to the discovery of another file that uses the same dynamic link library (DLL) proxying technique. But instead of a malicious Excel file, it is delivered in a Microsoft installer (MSI) package,” the post read.
To defend against the attack, Microsoft recommended that organizations use the included indicators of compromise to identify whether the threat actor is in the environment and assess for potential intrusion. Organizations can also change Excel macro security settings and turn on attack surface reduction rules to further manage the risk while educating end users about security risks.
“The cryptocurrency market remains a field of interest for threat actors. Targeted users are identified through trusted channels to increase the chance of success,” Microsoft said. “While the biggest companies can be targeted, smaller companies can also be the targets of interest.”
Targeted users are identified through trusted channels to increase the chance of success,” Microsoft said. “While the biggest companies can be targeted, smaller companies can also be the targets of interest.”
Menghan Xiao
Related
Get daily email updates
SC Media's daily must-read of the most current and pressing daily news
How to hack Telegram? 5 ways to hack Telegram
Is it possible to hack Telegram - answered hundreds of hackers and experienced programmers who took part in the competition from the developers. They identified all the existing vulnerabilities, for which they were awarded hefty cash prizes.
Read more in the article: $300,000 is promised to those who hack Telegram
As the developers say, their creation is absolutely closed from special services, unlike Viber, Skype, and others. You can open the page only by logging in via SMS confirmation, which eliminates the possibility of selection or interception of verification data. And what did you expect? That there will be detailed instructions for dummies here, how to hack a telegram bot or how to hack Telegram itself? - this is impossible even for many experienced programmers, not to mention noobs. Those classic tricks that you may be familiar with on Vkontakte do not work here: phishing, warming, etc.
And what did you expect? That there will be detailed instructions for dummies here, how to hack a telegram bot or how to hack Telegram itself? - this is impossible even for many experienced programmers, not to mention noobs. Those classic tricks that you may be familiar with on Vkontakte do not work here: phishing, warming, etc.
Interception of traffic
The most common article in data acquisition by third parties. As it became clear from the title, the data transmitted from the client to the server is intercepted. Listening to traffic is complicated by encryption, which makes this type of hacking almost impossible, it is almost impossible to decode the bytes.
Intermediary attack
This type involves the intervention of a third party, a device that will replace the embedded data. Each message is closed with an AES key, which cannot be modified from the outside, the DH exchange protocol and the public server key prevent this.
SMS interception
Perhaps this is one of the few ways to hack Telegram. Many advanced programmers will agree that it will be much easier to intercept SMS than to receive and decrypt user chats protected by the MTProto protocol.
Many advanced programmers will agree that it will be much easier to intercept SMS than to receive and decrypt user chats protected by the MTProto protocol.
DDoS
This way you can crash the server part of the application, which happened in July 2015. For several hours, the utility worked with difficulties all over the world. Before hacking Telegram in this way, you will need a lot of money, DDoS is one of the most expensive attacks.
For lovers and others…
Yes! Hacking Telegram or even just fooling a bot is almost impossible from a software point of view, but possible from a human point of view. After all, no one canceled social engineering.
As an idea: Follow your beloved, put the application on your computer, from her phone or on any smartphone, but there is a flaw. Do not mark as read because it will be noticeable. + At any time it will be possible to understand the active sessions and close them.
PS: And it is better to trust or talk - the easiest and right decision. Even if the truth is not so good! Good luck!
Even if the truth is not so good! Good luck!
Protection: Take it right now and check whether you have been hacked and read your correspondence?
- Open your Telegram settings;
- Item "Privacy and Security" or "Confidentiality" - the name of the item depends on the operating system (Android or IOS) and OS version.
- Select "active sessions" or "active sessions". If suddenly, there is an unfamiliar device, complete it.
How to protect yourself and not let someone else's Telegram messages be read? The most detailed instruction!
Found a way to hack any Telegram account. Hundreds have already been hacked
One of the most secure messengers on the market is Telegram, which, after being blocked in Russia in 2017, was unblocked and made public again for everyone. And now, as it became known, a very dangerous critical vulnerability was discovered in this messenger, allowing everyone and everyone to hack into any account as easily and simply as possible, gaining full access to it. In this case, it will be possible to view all sent and received photos, read all correspondence, send any messages, call or perform any other actions, since we are talking about getting 100% control over the entire account as a whole. Such a security hole has been used for more than a month, and hundreds of accounts have been hacked with its help.
In this case, it will be possible to view all sent and received photos, read all correspondence, send any messages, call or perform any other actions, since we are talking about getting 100% control over the entire account as a whole. Such a security hole has been used for more than a month, and hundreds of accounts have been hacked with its help.
As it became known from reliable sources, the Telegram messenger will have a way not just to read someone else's correspondence, but to gain full control over the account and, in fact, steal other people's accounts. All this is due to a vulnerability in the messenger's security system, which allows the launch of third-party code, and its injection into the messenger occurs at the moment the link is clicked. Such a gap exists only in the computer version, that is, in the Telegram assembly for Windows, macOS and Linux, while it is not possible to use it on Android and iOS. The hack link is widely distributed through all sorts of group chats and public channels, promising all those who follow it to provide what they need.
Information about the flaw that allows any Telegram account to be hacked has already been shared with the developers. Representatives of the messenger confirmed the existence of the problem and promised to deal with it as soon as possible. Meanwhile, it is better for owners of any computers based on any OS to refuse to follow links of unknown origin, because otherwise you can lose access to your account. If someone gains such access, he will be able to change his login and password, enable an additional security system and take other steps in connection with which the real owner of the account will lose access to it. These accounts can then be used to post anything in channels and chats, or to scam you.
This vulnerability began to be used for hacking since the end of February 2022, and earlier there were no cases of its use to gain access to the personal data of Telegram users. To become a victim of scammers, you just need to follow the link, after which they will instantly get full access to the account, having the opportunity to use it at their discretion for various purposes.