How to find out someone instagram password
8 Ways to Find Someone's Password on a Computer or Phone
').insertAfter("#intro"),$('
').insertBefore(".youmightalsolike"),$('
').insertBefore("#quiz_container"),$('
'). insertBefore("#newsletter_block_main"),ha(!0),b=document.getElementsByClassName("scrolltomarker"),a=0;a
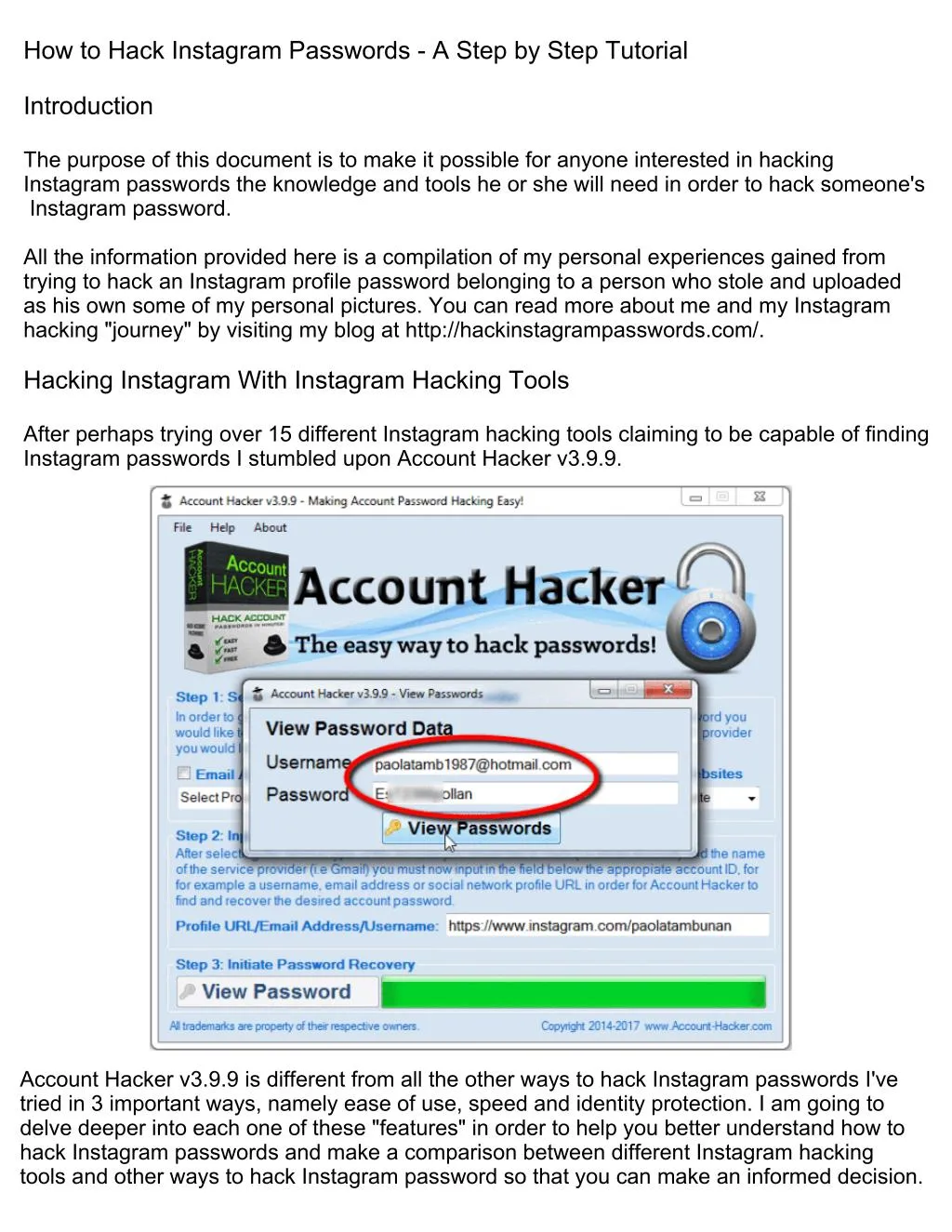
Download Article
Explore this Article
Download Article
If need to access an account and don't know the password, there are many easy things you can try. Whether you want to figure out someone else's password (like an employee or your child) or recover one of your own forgotten passwords, you can use these tools to access accounts quickly. Instead of guessing passwords (which can lock you out of the account), use this wikiHow guide to find the password for your (or somebody else's) social media profiles, streaming services, apps, and more on any computer, phone, or tablet.
Things You Should Know
- Most web browsers on computers, phones, and tablets automatically save logins and passwords so people don't have to remember them.
- If you enter the wrong password too many times when trying to log in, you'll usually be locked out of the account.
- You can use password cracking tools and keyloggers on your own devices, but it's not legal (or ethical) to crack or record other peoples' passwords.
Steps
-
Many web browsers automatically save the passwords we use to access websites. If the password you're looking for was saved by the web browser, you may be able to find it in plain text. In most cases, you'll need to enter the primary password you use to access your PC or Mac to view passwords in the password manager.
- Google Chrome:
- Click the three dots at the top-right and select Settings.
- Click Autofill at the top-left.

- Click Password Manager in the main panel.
- Click the eyeball next to a saved password to view it.
- Safari:
- Click the Safari menu and choose Preferences.[1] X Research source
- Click Passwords
- Select a website and click Edit to view the password.
- Microsoft Edge:
- Click the three dots at the top-right and select Settings.
- Click Passwords in the right panel.
- Click the eyeball next to a saved password.
- Firefox:
- Click the three-line menu at the top-right and select Settings.
- Click Privacy & Security in the left panel.
- Scroll down and click Saved Logins… in the right panel.
- Select a login from the left panel, then click the eyeball on the right to view it.
- Google Chrome:
Advertisement
-
If you (or the person who uses the password) entered the password on a phone or tablet, it may be saved in Keychain or Google Passwords.
 Just like with web browsers on a computer, most phones and tablets automatically save login and passwords so people won't have so many passwords to remember. If you have access to a phone or tablet, you might be able to see all stored passwords in plain text—although, you'll usually need to enter the phone's PIN or biometric to view these passwords.
Just like with web browsers on a computer, most phones and tablets automatically save login and passwords so people won't have so many passwords to remember. If you have access to a phone or tablet, you might be able to see all stored passwords in plain text—although, you'll usually need to enter the phone's PIN or biometric to view these passwords. - iPhone/iPad:
- Try Siri first.[2] X Research source With the screen unlocked, say, "Hey Siri, show me my passwords," or "Siri, what's the password for my Netflix account?"
- Open the Settings app and select Passwords.
- Enter your PIN or biometric.
- Select a website or app to view the password.
- Android:
- Open Chrome and tap the three dots at the top-right.[3] X Research source
- Tap Settings and select Passwords.

- Tap a password, then tap Show password or the eyeball icon.
- iPhone/iPad:
-
Search for stored passwords on the account holder's computer. Some people store their passwords plain text files on their computers, which is definitely not a secure way to store passwords. If you (or the person whose password you're trying to find) have such a file, you can try searching for files that contain the word "password" or the username you're trying to access.
- On Windows:
- First, you'll need to enable a feature that allows you to search for certain text within documents. Press Windows key + S and type index.
- Click Indexing Options.
- Click Advanced and select the File Types tab.
- Select Index Properties and File Contents, click OK, then click Close.
- Now, open File Explorer, click This PC, and type "password" (or the username or site you're trying to access) into the search bar at the top-right.
 All files containing the word "password" anywhere in the text will appear.
All files containing the word "password" anywhere in the text will appear.
- On a Mac:
- Open Finder.
- Press Command + F to open Find.
- Select "Kind" from the first drop-down menu, then select "Text" from the second.
- Type "password" (or the username or site you're trying to access) into the field at the top-right, and all files containing the word you entered will appear.
- On Windows:
Advertisement
-
Some people write down their passwords so they won't forget them. Whether you're looking for somebody else's password or your own, check the area near the computer for sticky notes containing login information, notebooks with passwords lists, or any scraps of paper that might have this information. Some people even buy "password journals," which are entire notebooks geared toward listing your passwords in an easy-to-remember format. While this is not a secure way to store your passwords, it's very common.

-
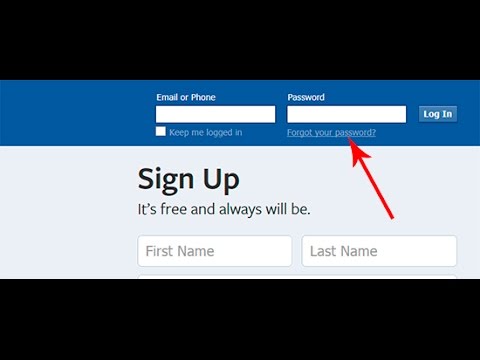
If you're trying to access a website or app, look for a "Forgot Password" link on the login screen. This option is typically somewhere near the username and password fields. Clicking this link will typically give you the option to receive a password reset link via email, text message (SMS), or by answering security questions.
- In most cases, you'll need to have access to the email account or phone number associated with the account. So, it's best to only use this method for your own accounts.
- If security questions are available, you may be able to answer them immediately to reset the password. But in most cases, the answering the security questions will typically send a password reset link to the email address on file to complete the password reset form.
Advertisement
-
If you know the password requirements of the site or service you want to access, you might be able to guess the password.
 This can be a little risky, as too many guesses may lock you out of the account. Before you start guessing, figure out the minimum password requirements for the site or service, such as how many characters are required, and whether there needs to be a mix of upper- and lower-case letters, numbers, and symbols. This can help you narrow down the options.
This can be a little risky, as too many guesses may lock you out of the account. Before you start guessing, figure out the minimum password requirements for the site or service, such as how many characters are required, and whether there needs to be a mix of upper- and lower-case letters, numbers, and symbols. This can help you narrow down the options. - Our handy guide to guessing passwords will be very helpful if you're not sure where to start!
- If you want to access a phone, like an iPhone or Android, the password or PIN will usually be easier to guess as it'll be fewer characters and (almost always) just numbers. People often use digits from their own phone numbers, social security numbers, birthdates, and other significant numbers as their phone PINs.
- People often use names of their pets, partners, or other significant people in their lives in their passwords—you can try these names, along with any numbers you think are important to that person. For example, a pet's name followed by the year of birth.

-
Password cracking tools can crack passwords on Linux, Windows, or macOS. These tools are for advanced users who have access to the hash or shadowed version of the password—you won't be able to use password crackers to try a bunch of logins on a website.[4] X Research source Cracking tools work by brute force (basically, trying all characters from a character set), dictionary attacks (using word lists), or a combination of multiple cracking methods.
- John the Ripper, one of the most famous password cracking tools, comes preinstalled in Kali Linux. If you want to use it on another platform, you can download it from https://www.openwall.com/john.
- Speaking of Kali Linux, Wfuzz is a cracking tool that uses brute force methods to crack web-based passwords. It comes pre-installed on Kali, but you can also download the source code for other flavors of Linux.

- Hashcat, known as "The World's Fastest Password Cracker," is a command-line app that runs on Windows, macOS, and Linux.[5] X Research source
- To crack a Windows user password, you can use Hash Suite, which is a port of John the Ripper.
- Mimikatz is another Windows password-cracking tool that can extract plain text passwords, hashed passwords, PIN codes, and Kerberos tickets from memory.[6] X Research source
Advertisement
-
Keyloggers are programs or devices that capture every keystroke a person types. When installed properly, most users won't know they're being recorded. The thing is, it's not legal to install a keylogger on another person's computer or phone unless you have permission to do so—you should only do this on your own devices, or with permission.
- For example, it's legal for an IT department to install a keylogger on a user's computer to monitor workplace activity if the employee consented during the hiring process.
 [7] X Research source It's also legal to install a keylogger on your own computer, which can be helpful if you're trying to find your child's passwords.[8] X Research source
[7] X Research source It's also legal to install a keylogger on your own computer, which can be helpful if you're trying to find your child's passwords.[8] X Research source - Some keyloggers are hardware based, but those are less common. Legitimate software-based keyloggers are usually marketed to businesses and parents—some popular options are WebWatcher, Kidlogger, Revealer, Spyrix, and StupidKeyLogger.
- Before downloading software to your computer, make sure the website is not a scam.
- For example, it's legal for an IT department to install a keylogger on a user's computer to monitor workplace activity if the employee consented during the hiring process.
Search
Add New Question
-
Question
How can I fully secure my FB account and protect it from hacking?
There is nothing that you can buy to completely protect your Facebook account.
 The only way to minimize the chance of a hacker getting into your Facebook account is to make a long, strong password that you can remember. Make sure that it uses numbers, uppercase and lowercase letters, and even special characters.
The only way to minimize the chance of a hacker getting into your Facebook account is to make a long, strong password that you can remember. Make sure that it uses numbers, uppercase and lowercase letters, and even special characters. -
Question
Would this work for an iPhone?
You could just clean the screen really nicely and then ask them to unlock it. Then look to see where their fingerprints are.
-
Question
What if I don't have a computer and it's a tablet or phone?
Make sure their fingers are smudged, and clean the screen. Ask them to enter their password.
See more answers
Ask a Question
200 characters left
Include your email address to get a message when this question is answered.
Submit
Advertisement
Submit
Thanks for submitting a tip for review!
Advertisement
Advertisement
References
- ↑ https://support.apple.com/en-us/HT211146
- ↑ https://support.apple.com/en-us/HT211146
- ↑ https://support.google.com/chrome/answer/95606?hl=en&co=GENIE.Platform%3DAndroid
- ↑ https://www.openwall.com/john/doc/EXAMPLES.shtml
- ↑ https://hashcat.net/hashcat/
- ↑ https://github.com/gentilkiwi/mimikatz
- ↑ https://home.sophos.com/en-us/security-news/2019/what-is-a-keylogger
- ↑ https://www.malwarebytes.com/keylogger
- ↑ http://www.ncsl.org/issues-research/telecom/computer-hacking-and-unauthorized-access-laws.
 aspx
aspx
About This Article
Article SummaryX
1. Install a keylogger.
2. Search for stored passwords on the computer.
3. Access the password manager.
4. Try password reset links.
Did this summary help you?
In other languages
- Send fan mail to authors
Thanks to all authors for creating a page that has been read 1,788,365 times.
Advertisement
The 8 Most Common Tricks Used to Hack Passwords
By Gavin Phillips
Updated
Share Tweet Share Share Share Email
Want to figure out someone's password? Review your life choices. Learn how to protect your password from hackers instead.
Image Credit: SergeyNivens/DepositphotosWhen you hear "security breach," what springs to mind? A malevolent hacker sitting in front of screens covered in Matrix-style digital text? Or a basement-dwelling teenager who hasn't seen daylight in three weeks? How about a powerful supercomputer attempting to hack the entire world?
Hacking is all about one thing: your password. If someone can guess your password, they don't need fancy hacking techniques and supercomputers. They'll just log in, acting as you. If your password is short and simple, it's game over.
If someone can guess your password, they don't need fancy hacking techniques and supercomputers. They'll just log in, acting as you. If your password is short and simple, it's game over.
There are eight common tactics hackers use to hack your password.
1. Dictionary Hack
First up in the common password hacking tactics guide is the dictionary attack. Why is it called a dictionary attack? Because it automatically tries every word in a defined "dictionary" against the password. The dictionary isn't strictly the one you used in school.
No. This dictionary is actually a small file containing the most commonly used password combinations. That includes 123456, qwerty, password, iloveyou, and the all-time classic, hunter2.
The above table details the most leaked passwords in 2016. The below table details the most leaked passwords in 2020.
Note the similarities between the two—and make sure you don't use these incredibly simple options. And for those wondering why this leaked password list hasn't been updated since 2020, it's simply because the weak, awful passwords remain the same, just in a slightly different order. Long story short, if you don't want someone to figure out your password, never use any of these.
Long story short, if you don't want someone to figure out your password, never use any of these.
- Pros: Fast; will usually unlock some woefully protected accounts.
- Cons: Even slightly stronger passwords will remain secure.
- Stay safe: Use a strong single-use password for each account in conjunction with a password management app. The password manager lets you store your other passwords in a repository. Then you can use a single, ridiculously strong password for every site. Google Chrome does come with an integrated password manager, but standalone password managers are typically considered more secure.
2. Brute Force
Next up is the brute force attack, whereby an attacker tries every possible character combination in an attempt to guess your password. Attempted passwords will match the specifications for the complexity rules, e.g., including one upper-case, one lower-case, decimals of Pi, your pizza order, and so on.
A brute force attack will also try the most commonly used alphanumeric character combinations first, too. These include the previously listed passwords, as well as 1q2w3e4r5t, zxcvbnm, and qwertyuiop. It can take a very long time to figure out a password using this method, but that depends entirely on password complexity.
- Pros: Theoretically, it will crack any password by way of trying every combination.
- Cons: Depending on password length and difficulty, it could take an extremely long time. Throw in a few variables like $, &, {, or ], and figuring out the password becomes extremely difficult.
- Stay safe: Always use a variable combination of characters, and where possible, introduce extra symbols to increase complexity.
3. Phishing
This isn't strictly a "hack," but falling prey to a phishing or spear-phishing attempt will usually end badly. General phishing emails are sent by the billions to all manner of internet users around the globe, and it is definitely one of the most popular ways to find out someone's password.
A phishing email generally works like this:
- Target user receives a spoofed email purporting to be from a major organization or business.
- Spoofed email demands immediate attention, featuring a link to a website.
- This link actually connects to a fake login portal, mocked up to appear exactly the same as the legitimate site.
- The unsuspecting target user enters their login credentials and is either redirected or told to try again.
- User credentials are stolen, sold, or used nefariously (or both).
The daily spam volume sent worldwide remains high, accounting for over half of all emails sent globally. Furthermore, the volume of malicious attachments is high, too, with Kaspersky blocking over 148 million malicious attachments in 2021. Furthermore, Kaspersky's Anti-Phishing system blocked an additional 253 million phishing links. Remember, this is just for Kaspersky, so the real number is much higher.
4 Images
Back in 2017, the biggest phishing lure was a fake invoice. However, in 2020, the COVID-19 pandemic provided a new phishing threat. In April 2020, not long after many countries went into pandemic lockdown, Google announced it was blocking over 18 million COVID-19-themed malicious spam and phishing emails per day. Huge numbers of these emails use official government or health organization branding for legitimacy and catch victims off-guard.
- Pros: The user literally hands over their login information, including passwords—relatively high hit rate, easily tailored to specific services or specific people in a spear-phishing attack.
- Cons: Spam emails are easily filtered, spam domains blacklisted, and major providers like Google constantly update protections.
- Stay safe: Stay skeptical of emails, and increase your spam filter to its highest setting or, better still, use a proactive whitelist.
 Use a link checker to ascertain if an email link is legitimate before clicking.
Use a link checker to ascertain if an email link is legitimate before clicking.
Social engineering is essentially phishing in the real world, away from the screen.
A core part of any security audit is gauging what the entire workforce understands. For instance, a security company will phone the business they are auditing. The "attacker" tells the person on the phone they are the new office tech support team, and they need the latest password for something specific.
An unsuspecting individual may hand over the keys without a pause for thought.
The scary thing is how often this works. Social engineering has existed for centuries. Being duplicitous to gain entry to a secure area is a common method of attack and one that is only guarded against with education. This is because the attack won't always ask directly for a password. It could be a fake plumber or electrician asking for entry to a secure building, and so on. When someone says they were tricked into revealing their password, it is often the result of social engineering.
- Pros: Skilled social engineers can extract high-value information from a range of targets. It can be deployed against almost anyone, anywhere. It's extremely stealthy, and professionals are adept at extracting information that could help guess a password.
- Cons: A social engineering failure can raise suspicions about an impending attack, and uncertainty as to whether the correct information is procured.
- Stay safe: This is a tricky one. A successful social engineering attack will be complete by the time you realize anything is wrong. Education and security awareness is a core mitigation tactic. Avoid posting personal information that could be later used against you.
5. Rainbow Table
A rainbow table is usually an offline password attack. For example, an attacker has acquired a list of user names and passwords, but they're encrypted. The encrypted password is hashed. This means it looks completely different from the original password.
For instance, your password is (hopefully not!) logmein. The known MD5 hash for this password is "8f4047e3233b39e4444e1aef240e80aa."
Gibberish to you and I. But in certain cases, the attacker will run a list of plaintext passwords through a hashing algorithm, comparing the results against an encrypted password file. In other cases, the encryption algorithm is vulnerable, and most passwords are already cracked, like MD5 (hence why we know the specific hash for "logmein."
This is where the rainbow table comes into its own. Instead of having to process hundreds of thousands of potential passwords and matching their resulting hash, a rainbow table is a huge set of precomputed algorithm-specific hash values. Using a rainbow table drastically decreases the time it takes to crack a hashed password—but it isn't perfect. Hackers can purchase prefilled rainbow tables populated with millions of potential combinations.
- Pros: Can figure out complex passwords in a short amount of time; grants the hacker a lot of power over certain security scenarios.
- Cons: Requires a huge amount of space to store the enormous (sometimes terabytes) rainbow table. Also, attackers are limited to the values contained in the table (otherwise, they must add another entire table).
- Stay safe: Another tricky one. Rainbow tables offer a wide range of attacking potential. Avoid any sites that use SHA1 or MD5 as their password hashing algorithm. Avoid any sites that limit you to short passwords or restrict the characters you can use. Always use a complex password.
6. Malware/Keylogger
Another sure way to lose your login credentials is to fall foul of malware. Malware is everywhere, with the potential to do massive damage. If the malware variant features a keylogger, you could find all of your accounts compromised.
Alternatively, the malware could specifically target private data or introduce a remote access Trojan to steal your credentials.
- Pros: Thousands of malware variants, many customizable, with several easy delivery methods.
 A good chance a high number of targets will succumb to at least one variant. It can go undetected, allowing further harvesting of private data and login credentials.
A good chance a high number of targets will succumb to at least one variant. It can go undetected, allowing further harvesting of private data and login credentials. - Cons: Chance that the malware won't work, or is quarantined before accessing data; no guarantee that data is useful.
- Stay safe: Install and regularly update your antivirus and antimalware software. Carefully consider your download sources. Do not click through installation packages containing bundleware and more. Steer clear of nefarious sites (easier said than done). Use script blocking tools to stop malicious scripts.
7. Spidering
Spidering ties into the dictionary attack. If a hacker targets a specific institution or business, they might try a series of passwords relating to the business itself. The hacker could read and collate a series of related terms—or use a search spider to do the work for them.
You might have heard the term "spider" before. These search spiders are extremely similar to those that crawl through the internet, indexing content for search engines. The custom word list is then used against user accounts in the hope of finding a match.
These search spiders are extremely similar to those that crawl through the internet, indexing content for search engines. The custom word list is then used against user accounts in the hope of finding a match.
- Pros: Can potentially unlock accounts for high-ranking individuals within an organization. Relatively easy to put together and adds an extra dimension to a dictionary attack.
- Cons: Could end up fruitless if organizational network security is well configured.
- Stay safe: Again, only use strong, single-use passwords comprised of random strings; nothing linking to your persona, business, organization, and so on.
8. Shoulder Surfing
The final option is one of the most basic. What if someone just looks over your shoulder while you're typing in your password?
Shoulder surfing sounds a little ridiculous, but it does happen. If you're working in a busy downtown café and not paying attention to your surroundings, someone could get close enough to note your password as you type, but it's probably not the easiest way to figure out someones password.
- Pros: Low technology approach to stealing a password.
- Cons: Must identify the target before figuring out the password; could reveal themselves in the process of stealing.
- Stay safe: Remain observant of those around you when typing your password. Cover your keyboard and obscure your keys during input.
So, how do you stop a hacker from stealing your password? The really short answer is that you cannot truly be 100 percent safe. The tools hackers use to steal your data are changing all the time and there are countless videos and tutorials on guessing passwords or learning how to hack a password, or even just how to figure out someone's password.
One thing is for sure: using a strong, unique, single-use password never hurt anyone.
5 Password Tools to Create Strong Passphrases and Update Your Security
Read Next
Share Tweet Share Share Share Email
Related Topics
- Security
About The Author
Gavin Phillips (1100 Articles Published)
Gavin is the Junior Editor for Technology Explained, a regular contributor to the Really Useful Podcast, and a frequent product reviewer. He has a degree in Contemporary Writing pillaged from the hills of Devon, and more than a decade of professional writing experience. He enjoys copious amounts of tea, board games, and football.
He has a degree in Contemporary Writing pillaged from the hills of Devon, and more than a decade of professional writing experience. He enjoys copious amounts of tea, board games, and football.
More From Gavin Phillips
Comment
Subscribe to our newsletter
Join our newsletter for tech tips, reviews, free ebooks, and exclusive deals!
Click here to subscribe
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on.
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password.
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It's possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
Now someone has discovered your oversight and logged into your account.
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
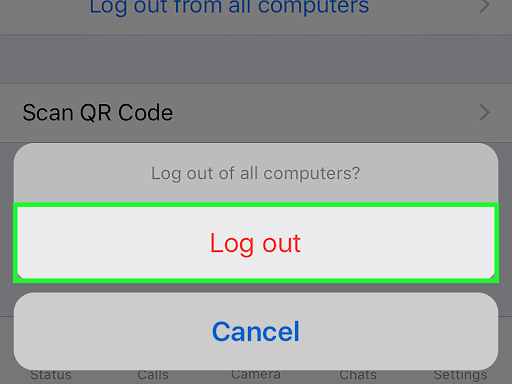
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings. This will reset the access tokens.
- Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them.
 If they managed to do this, change it back to yours.
If they managed to do this, change it back to yours. - Set a new password that is strong and one that you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress.
Tips
Air sellers in online stores
We tell how scammers deceive users of a well-known marketplace using a fake payment page for goods.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site.
 I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site.
Top 5 ways how to hack Instagram from phone 2022
Don't know how to hack password (page, profile) from Instagram? Looking for a reliable Instagram account hack to read correspondence and see photos? Reliable 5 Ways to Hack Insta - It's not as hard as you think!
Instagram hacking is an illegal act that can deprive you of a decent amount of money in the form of a fine and even reward you with a real prison term. Therefore, before doing something in this area, think about it, is it really so important and necessary for you?
Top 5 ways to hack Instagram from a phone 2022
Method 1. Specialized application
We start with the simplest and most realistic (which can be used by everyone without exception) way to hack Instagram - you need to take only 10 (! ) minutes phone and quickly there download free Reptilicus , install and configure.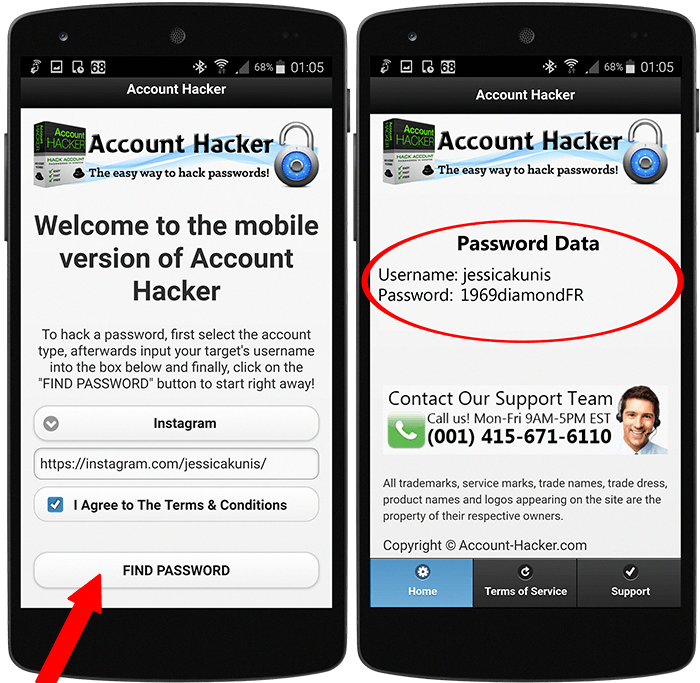 This is easy enough to do. Everything is in Russian. Extremely understandable. If you have any questions, the site has picture guide , instruction video, as well as online consultants.
This is easy enough to do. Everything is in Russian. Extremely understandable. If you have any questions, the site has picture guide , instruction video, as well as online consultants.
After installing the application you will be able to:
- read the correspondence without going to the page;
- see photos without hacking account;
- remotely see the location of a person when he is in the profile;
- see the photos he has saved on his phone;
- see photos that were sent to him, and then he deleted them;
- see what groups are watching and what is liking.
All this will become available when you install the special Reptilicus application on your phone. We offer not hacking an Instagram account, but control - this is the ability to remotely control a person's activities in this social network without penetrating his page and without performing any illegal actions combined with hacking.
In simple words, you won't need to hack your Instagram profile, you just install the program on your phone, and the program itself will send you everything that a person does on his phone, including on his page on Instagram.
Method 2. “Forgot password” function
We continue our review ... this is the most obvious method that (we don’t know for what reason) people don’t see on their own, although it lies on the surface. Yes, imagine, you can crack the Instagram password in order to get into the page using a function that allows you to recover a forgotten password. Here you need to know only the login (nickname) of the person. Just? Yes! Why didn't you think of this before? We do not know! So, you need to take the following steps:
Step 1. If you have your own page, then go to your account - click on the Instagram icon - the home page will open. If not, then just go through the search engine.
Step 2. Press "Menu" - press "Add Account" - the standard menu for logging into your account will open.
Step 3. Enter the username (nickname/login) - click "Forgot Password".
Step 4. Select confirmation via SMS - enter your phone number - wait for SMS with a link to change your password.
Step 5. Open SMS - in the Change Password section, click on change password - change password.
That's it, now you know how to crack an Instagram password! No need to thank.
Method 3. Intercepting keystrokes
You have probably heard that there are programs that can save keystrokes on your phone. And if you are thinking about how to hack an account on Instagram, then this method can allow you to intercept messages typed on your phone when communicating on Instagram.
The Reptilicus program will help you to see literally everything that the person whose correspondence you are so interested in is typing on his phone. You can also install any other keylogger, of which there are quite a lot on the Internet. We are just talking about our program, tested by time and users. You can hack an Instagram page with a simple installation. There are reviews of real users (the forum is over 7 years old).
We are just talking about our program, tested by time and users. You can hack an Instagram page with a simple installation. There are reviews of real users (the forum is over 7 years old).
Method 4. Chat screenshots
Chat screenshots, screenshots or instant screenshots (call it what you want, the meaning of this will not change in any way) is a real opportunity to do without the treacherous hacking of Insta. The screenshots will show all the correspondence, with emoticons, with all the actions that a person performs on his phone.
Screenshots are taken automatically and without root rights, as well as keyboard interception. They will start coming as soon as a person goes to the page on Insta. To do this, you need to check the box in the program settings so that screenshots start working when you enter Instagram.
If you want to receive screenshots around the clock, and not just when you enter Insta, then do not set any restrictions. The settings are very convenient - make sure by looking at the manual.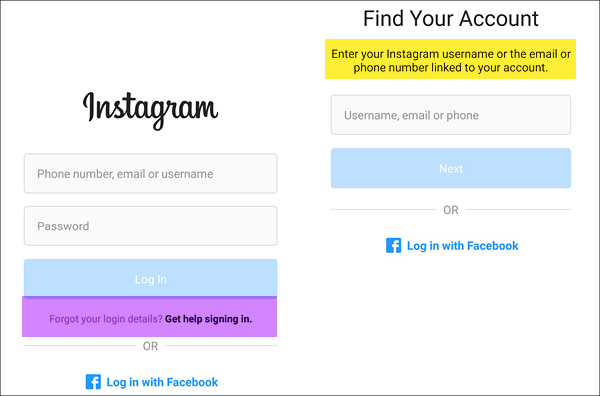 You can do this, but you can do that. Adjust as you need. If you want to receive screenshots every 10 seconds, get it, if you want only correspondence, please, receive only correspondence. Here the choice is entirely yours.
You can do this, but you can do that. Adjust as you need. If you want to receive screenshots every 10 seconds, get it, if you want only correspondence, please, receive only correspondence. Here the choice is entirely yours.
Method 5. Phishing
This method is considered the easiest, but at the same time the most illegal. This is a gross scam. Therefore, we do not advise you to use it. BUT since we provide possible ways, phishing will help you understand how to hack Instagram through a computer.
This method is that you create a phishing (false, fake) page to enter Instagram. At first glance, it will not differ from the standard in any way. Only one letter will be changed there, or some symbol invisible to the naked eye will be added. BUT it will be DIFFERENT. The user enters his username and password there and transfers it to a regular Instagram. Therefore, he will never guess that he was on this fake page. But ... but you will receive his nickname and password.