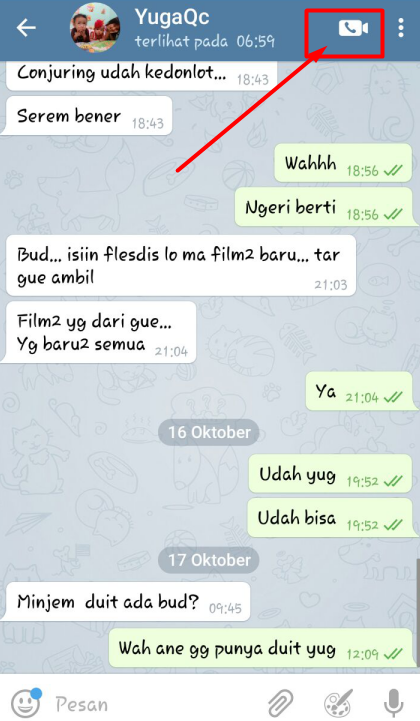
How to make fake video call on telegram
How Are Fake Live Video Calls Made? Here's How to Spot Them
Video calling is ubiquitous. You can video call your friends, family, and colleagues, sharing your face and surroundings simultaneously. Being in the same location all time is boring, right? How about appearing with your regular face? Everyone knows what that looks like.
What if you could make a fake video call that switched out your face, the background, or other important features—would you fake call your family?
Here's how fake video calls work and how you can spot one.
What Is a Fake Video Call?
A fake video call can mean a couple of things.
For instance, you could create a fake video background in an attempt to trick people into believing you're on holiday. You could record a video of yourself staring at your monitor, then play it back during a meeting that you are not required to talk in.
There's the option of mirroring your webcam input to a YouTube video that does not feature you at all but could show an amusing cat video.
A fake video call could also use deepfake technology, using AI-powered video to switch out the faces and voices on display. You can find more information on deepfake tech later in the article.
How to Make a Fake Video Call Using ManyCam
How you approach making a fake video call depends on the platform. On a desktop computer or laptop, you have multiple software options to use a fake video, but your access to certain apps is limited. However, the WhatsApp desktop app now allows voice and video calling, so the following instructions also allow you to make a fake call using WhatsApp.
For those apps that you can use, ManyCam allows you to alter the appearance of your webcam extensively. For instance, you can use more than one webcam with Skype or other voice calling apps or stream a completely different video that appears instead of your webcam.
Here's how you make a fake video call using ManyCam.
1. Configure ManyCam
First, you need to download, install, and configure ManyCam.
Download: ManyCam for Windows | macOS
Once your download completes, install ManyCam.
2. Create a ManyCam Preset & Choose Your Fake Video Source
You can use presets for your fake video call. Open ManyCam, then under Presets, select Preset 1. Underneath the Presets panel are the video source options. Select the video source you want to use, such as a webcam, IP camera, YouTube video, web source URL, and so on.
If you want to use a YouTube video, copy and paste the video URL into ManyCam. Do the same for whichever fake video source you choose.
3. Select ManyCam In Your Voice Calling App
Once you configure the fake video source, you can make your video call. But you must select the ManyCam webcam option in your video call app to display your fake video. The process is slightly different for each video calling app, but you'll find the ManyCam Virtual Webcam option in the camera or webcam options.
How to Select ManyCam In Skype
In the Skype desktop app, head to Settings > Audio & Video. In the Camera options, select the ManyCam Virtual Webcam. When you make your video call, the fake video in ManyCam will play instead of your regular webcam.
How to Select ManyCam In WhatsApp Desktop
After following the above instructions, open your WhatsApp Desktop app and locate the person you want to call. When the call dialog appears, select the three-dot icon, then select ManyCam Virtual Webcam from the dropdown menu. The video call will display the video playing in ManyCam to the person you're calling, and hilarity will ensue. And, that is how you make a fake WhatsApp call with ManyCam.
How to Make a Fake Video Call Using OBS
OBS (Open Broadcaster Software) is a popular cross-platform, open-source video streaming tool. You can use OBS to stream to multiple platforms simultaneously, record media, and much more. In this case, you can use OBS to stream a fake video in place of your webcam.
In this case, you can use OBS to stream a fake video in place of your webcam.
The result is similar to ManyCam. However, as OBS is completely free, you can use the full range of video streaming and broadcasting options. Even though OBS has more tools on offer, the software isn't difficult to use.
Here's how you make a fake video call using OBS.
1. Configure OBS
First, you need to download and install OBS. Although it is a cross-platform tool, the following steps only work with OBS on Windows due to the plugin required to create a virtual webcam.
Download: OBS for Windows (Free)
2. Configure OBS-VirtualCam
OBS-VirtualCam is an open-source plugin for OBS. The plugin creates a virtual webcam option in OBS. Once you install the plugin, you can output media to the virtual webcam, then select the virtual webcam in your video call options.
While the VirtualCam plugin once required you to download and install it manually, as of OBS version 26. 0.0 (launched in August 2020), virtual webcam functionality is now built into OBS directly. You can still install the plugin if you want, but it is no longer the most efficient way of doing things.
0.0 (launched in August 2020), virtual webcam functionality is now built into OBS directly. You can still install the plugin if you want, but it is no longer the most efficient way of doing things.
So, within OBS, head to Tools > VirtualCam and select Start. The virtual webcam option of "OBS-Camera" will now appear in your video calling apps, such as Skype or Facebook Messenger.
3. Select Your Fake Video Source in OBS
OBS has several options you can use for a fake video. You can use OBS to play a local video, display a browser window or online video, create a video stream from a third-party video player (such as VLC), and more.
You can see the range of options along the bottom of the main screen in OBS. Under Source, select the + icon, then choose the video input option for your fake video call.
- If you already have a video you want to use, select Media Source, then browse to the file location on your computer.
- Alternatively, you can play the fake video in a separate media player. Select Window Capture, then select the media player using the Window dropdown menu.
- If you want to use an online video, select Browser, then input the URL of the website you want to display. Next, resize the browser window using Width and Height to fit the video size.
Whichever video configuration you choose, the result will play through the OBS-VirtualCam virtual webcam in your video calling app.
Can You Make Fake Video Calls Using a Smartphone?
Smartphone apps come with a different set of limitations regarding fake video calling.
Fake video apps for smartphones are a dime-a-dozen, but they don't do what you expect. If you search for "fake video calling apps" on Google Play, you'll find thousands of poorly coded apps that let you "chat" with a fake person, rather than stream a fake video through a video calling app.
Spoofing a smartphone camera within an app isn't easy. Smartphone video calling apps (and other apps in general) don't allow such behavior for a simple reason: it presents a security risk. If one app can spoof and mimic the camera for a fun reason, another app will use the same process for nefarious reasons. So while you can make a fake call on WhatsApp Desktop, you cannot do the same using WhatsApp on your smartphone.
What Is a Deepfake?
On the more nefarious side, there are deepfakes. A deepfake video uses AI technology to create an extremely convincing video featuring the likeness of someone else.
Deepfake tech continues to develop, and it is becoming increasingly difficult to spot the difference between a real video and an AI video. For example, check out the example that brought deepfake technology to light, mimicking Barack Obama:
The hands and gestures are Obama's, but the mouth (voiced by comedian Jordan Peele) is out of sync. Whereas, just over one year later, The Dark Knight's Tale features Heath Ledger playing himself as Joker in the Dark Knight, but also in A Knight's Tale.
The Dark Knight's Tale is fake. But it does illustrate the tremendous advances in deepfake technology over the course of a year.
Around the same time, a deepfake featuring Facebook CEO Mark Zuckerberg was also illustrating the technology.
View this post on Instagram
A post shared by Bill Posters (@bill_posters_uk)
Again, it is clearly fake. Zuckerberg sounds completely different from the deepfake.
A deepfake requires masses of computing power (specifically, a powerful GPU), time, and data. For the effort creating a lifelike deepfake requires, you're unlikely to encounter an effective effort as a prank in the near future.
How to Spot a Fake Video Call
Can you spot a fake video call? The answer lies in the quality of the fake video.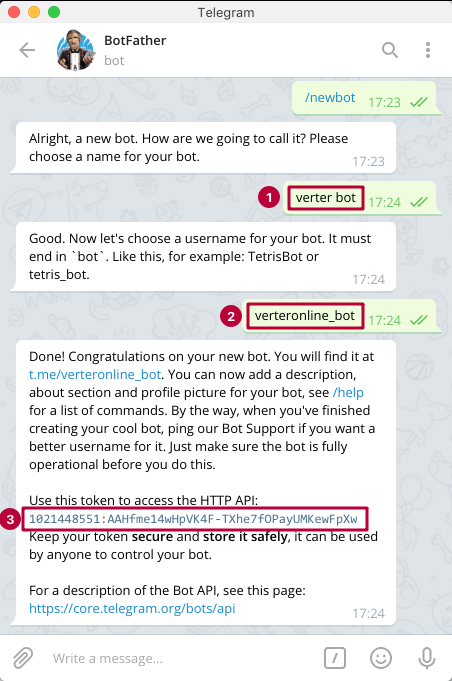
The development of deepfake technology is a prime example. Jordan Peele's deepfake video mimicking Barack Obama was clearly fake. But the quality of public-facing deepfake technology is much better than it was. That's without considering the deepfake technology that powerful organizations or governments will have access to. Regardless, protecting yourself from deepfakes is important.
At other times, you'll know a fake video call is false because of the contact information. Making a truly fake video call on WhatsApp Desktop is incredibly difficult because the contact information is on display during the connection. Similar limitations are present with other video calling apps that link to a phone number, such as making a fake video call with FaceTime.
There are, of course, tricks to skirt these issues—fake accounts, fake phone numbers, false names, pictures, and so on. But for the most part, would someone go to that length to create a fake video call to fool you?
For most people, tech support scams are a more pressing issue. Either that, or the threat of phishing scams relating to the latest news cycle.
Either that, or the threat of phishing scams relating to the latest news cycle.
5 Ways to Spot a Fake Video Call
In short, there are a few tell-tale signs regarding a fake video call:
- Video quality. The quality of the video is usually poor. If the fake video comes from an online source, check for watermarks or other signs the video is stolen.
- Video sizing. Whoever is fake video calling you will resize a video to fit the webcam window or the app they're using. Resizing the video will distort the proportions of the video, so it looks out of shape (think extra long or extra wide face, and so on).
- Contacts. Is the person calling you on your contacts list? If not, does the name mean anything to you? Alternatively, does the contact name appear as the name of an app?
- Content. If the video call comes from someone you know, and their contact information is correct, what is the video content? Is the person allegedly calling you even in the video?
- Loops & Cuts.
 Many fake videos will loop around to the start after a certain amount of time elapses. Alternatively, the video will stop abruptly at the end—but the video call won't finish.
Many fake videos will loop around to the start after a certain amount of time elapses. Alternatively, the video will stop abruptly at the end—but the video call won't finish.
Also, if someone is using a face swapping app with video functionality, the faces are extremely unlikely to align correctly.
Fake Video Calls Be Gone!
Now you know a few of the methods used to make fake video calls and which platforms they work best on, you're better prepared to spot and avoid them. Fake calls using software like ManyCam do work, but unless you're using exceptional hardware, most of the time, a fake video call is easy enough to spot.
Mobile apps like WhatsApp and FaceTime have built-in security mechanisms to prevent fake video calling and other such scams. In reality, it comes down to just taking a moment to double-check the facts on offer, such as the phone number, video quality, and so on.
Telegram Video Call: Everything You Need to Know
Liza Brown
Oct 20, 2022• Proven solutions
Telegram is one of the well-known messaging platforms with a monthly estimate of over 550 million users.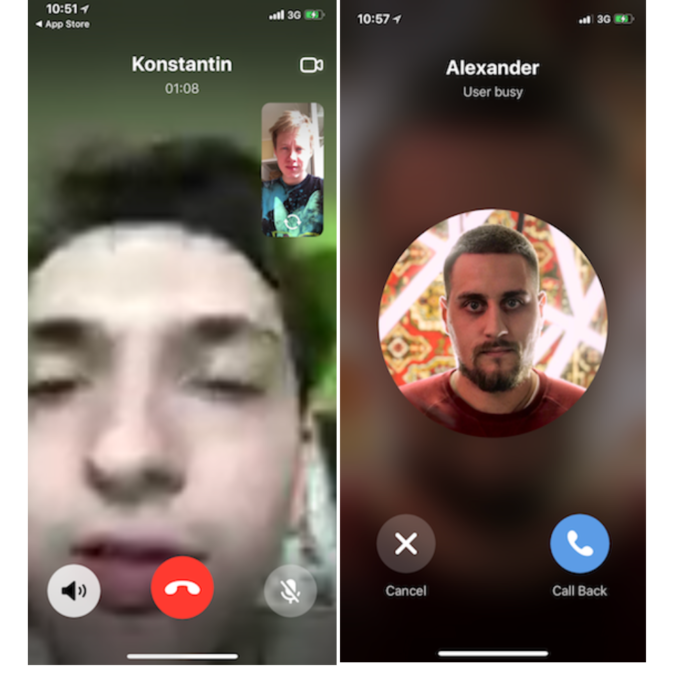 Telegram users usually increase anytime one of its competitors has a problem with their privacy policy. This messaging app allows the same account on multiple devices.
Telegram users usually increase anytime one of its competitors has a problem with their privacy policy. This messaging app allows the same account on multiple devices.
Telegram functions the same way as other messaging apps. It sends messages, allows you to create groups, make telegram video calls and voice to contacts, send files and stickers. Some features make this app stand out from other apps.
Telegram features a privacy policy that makes use of end-to-end encryption that makes hackers or a third party unable to access your conversations. However, telegram uses this encryption for calls only and in its “secret chats” feature, not in regular chats. Meanwhile, other messaging apps like WhatsApp described as a less secure service, use this end-to-end encryption in calls and messages for a long time.
Now, the question is what is a telegram video call limit, and we’ll also see into frequently asked questions (FAQs).
- Part 1: Is Telegram Video Call allowed?
- Part 2: Top 5 Alternative Software/Apps for Perfect Video Calls
- Part 3: FAQs about Telegram Video Call
Part 1: Is Telegram Video Call allowed?
Telegram has improved in its latest updates on having up to 1000 participants in a telegram group call. Its updates cover video calling and sharing.
Its updates cover video calling and sharing.
Telegram group video call allows 30 users to join from their device camera and their screens and viewed by 1000 persons at the same time. Users now have the leverage to hold online events ranging from concerts to lectures and more.
Telegram has promised to keep increasing this limit as time goes on. This new update also includes improving the quality of video calls, sending videos of a high resolution, and allowing users to capture and play videos on full screen. Also, you can now pause a video on an expanded mode, rewind or fast forward a video.
Part 2: Top 5 Alternative Software/Apps for Perfect Video Calls
These are the top 5 alternatives for a perfect video call to cover for telegram desktop video call if not in reach.
1. Skype
Many people worldwide are making use of this app daily to make video calls as it meets their requirements. This app is mainly in use by business organizations for video chatting with a good number of participants.
Pros:
- It enables you to records calls and switches on live subtitles
- You can easily make calls to landlines
- Users have access to smart messaging tools
- Options to share screen are available
- Easily organize interviews
- Make cheap calls and SMS services.
Cons:
- Skype app takes a significant amount of time to manage
- Difficulty in connecting skype to the AV room
- Webcam not suitable for video conferencing
2. Slack
The Slack app aids easy communication between colleagues in a work environment. You can communicate to people around you without taking a break from your system to make someone at intervals.
Pros:
- You can create different groups within your organization.
- Allows for private, public, shared, or multi-workplace communications.
- Easily share anything and add emojis.
Cons:
- Very low storage space
- Automatically deletes convention after 14 days
- Always sends notifications
3. Google Hangouts
One of the best applications offered by Google to its users is Google Hangouts. It can be part of your everyday life when you need an app with an option for video, video calling, and messaging. This outstanding tool comes along with Google and Google+. It also offers other essential features.
Pros:
- No extra cost for the app usage.
- It runs easily on laptops, tabs, mobile devices, and more.
- Easily add and remove contacts.
Cons:
- Very low bandwidth
- Difficulty in sharing and deleting files.
- You can easily connect multiple people to a single interface.
4. Google Duo
This is one of the best video apps that is very reliable, versatile, and easy to use. Google Duo makes communication easy with several features that are beneficial to users.
Pros:
- It works with both iOS and Android devices.
- Video calls are of a good quality
- Availability of the knock-knock feature to check who wants to connect with you.
- Easy connection with contacts
Cons:
- No updates are available.
5.WhatsApp
WhatsApp is one of the trendiest messaging and video calling apps at present. It features texting, calls, sharing of multimedia data.
Pros:
- Easily share contacts
- Supports end-to-end encryption
- Enables auto-update of contacts
- It allows the use of emojis and GIFs
- Easily print chats
Cons:
- You can not make calls in several countries.
- No availability of virtual assistance
Part 3: FAQs about Telegram Video Call
1 - What is the limit of a telegram video call?
This messaging app has a recent update that has introduced many great features for users. The update highlight gives information that the new limit of telegram group video calls is up to 1000 people, referred to as Group Video Calls 2.0. This new feature allows 30 people to broadcast video from both your screen and device camera. The limit is, however, expected to increase as time goes on.
2 - Is telegram really private?
Telegram, though, has a claim of making use of end-to-end encryption for chats. But with the recent incidents, one can say this claim is not for all conversations. This only plays out in the feature called “secret chats.”
3 - Can a third person see a WhatsApp video call?
WhatsApp chats and video calls are very secured. Thus, a third person watching WhatsApp video call during the video is impossible if you allow end-to-end encryption.
So, a third-party getting access to watch WhatsApp video call is an arduous task, and the truth is that hacking into the WhatsApp network is one tough job to take up with their advanced end-to-end encryption.
Conclusion
So, now you can make video calls on telegram efficiently and securely. Besides, try out the alternative apps for video calls in place of telegram video call to experience the difference. Lastly, with the FAQs, you can now know how to use the telegram group video calls.
Liza Brown
Liza Brown is a writer and a lover of all things video.
Follow @Liza Brown
CommentSuccessful!
Thank you for your comment. We will review it within few days.
We explain how the security forces find Telegram users and how to avoid it
Collage: Financial Times
We recently wrote about how to properly clean messengers and protect social networks. Now it's time to tell you how to prevent them from finding you on Telegram.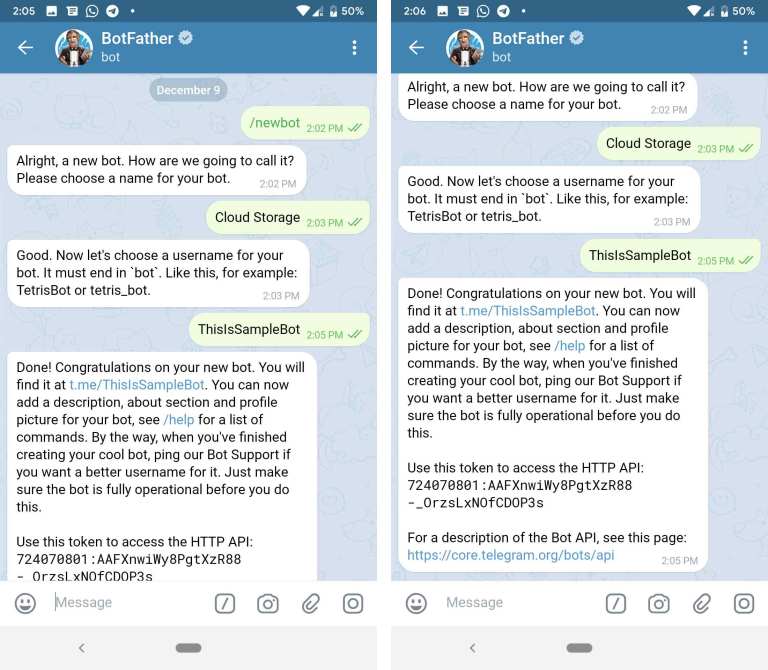
How does Telegram work?
If you register in the messenger using your phone number, an ID is assigned to each account. This makes him related to social networks like Facebook or Vkontakte. nine0003
Whenever you perform an action, you leave some of your data. For example, if you write to a chat, then the security forces receive the date the message was written, ID, name and your username. This data is received by both parties, that is, both you and your interlocutor or all members of the group.
It is important to understand that Telegram allows you to get the ID of any chat participant, any interlocutor and any user of the bot, if it belongs to the security forces or has been hacked. The ID is tied to the account and cannot be changed without changing the account, and it also remains with deleted accounts. nine0003
But how can you find a person using these data? And how to reduce the likelihood of this?
Method #1: using information they already have
Enforcers can check a user ID against an existing one in their database. How it is filled, you will understand later, but it is called "T-Search". If your ID with data about you is already in the database, then finding you is a matter of a couple of minutes.
How it is filled, you will understand later, but it is called "T-Search". If your ID with data about you is already in the database, then finding you is a matter of a couple of minutes.
Method #2: by phone number
Any user who has registered an account with a Belarusian phone number is potentially vulnerable. nine0003
First of all, the giant databases of ID-phone bundles were collected at a time when any user could be found by number. This opportunity came in 2019.
It is not clear how many of those databases, but potentially any user can be found if his account was created before 2020.
As far as we know, data, including photos and phones, of all users was collected back in 2020 itself, when people were not worried about security. If the account has not changed, then it does not matter if you have hidden some parameters - you are already vulnerable. nine0003
Secondly, if you create a new account and a person is in your contacts, then he automatically receives a message of this kind that cannot be turned off:
Theoretically, the security forces can make lists of new registrations for Belarusian numbers. And this is a big danger.
And this is a big danger.
Rule number 1: it is better to register your account on a non-Belarusian number. You can ask for it from friends abroad or buy it cheaply on the virtual number service (preferably also from a non-Belarusian card). This will not allow you to find your account once or twice. nine0003
Rule number 2: immediately after registration, set the maximum privacy of the account. In settings it should look like this:
Rule #3: You should delete and re-create your account on a regular basis - once in a while, say a month or two months. This will complicate the identification and cataloging of Telegram users. If your account is old (that is, it is over a year old or even created before the protests), then you definitely need to change it. nine0003
Rule #4: Be vigilant and constantly think about what you are doing online in general - is it worth the possible responsibility.
Recommendation: you can create at least two accounts - a work account and an "activist" account.
Subscribe to resources not prohibited in Belarus from the desktop, and also communicate with colleagues and friends. From the "activist" do what you see fit, but do not forget about the periodic deletion of the account.
Tip: try using Partisan Telegram (for PC, for Android). It will allow you not to show the "main" account, leaving it when entering a password. Features description here. Recently, a program developed by the CyberGuerillas underwent a code audit at the Rochester Institute of Technology, which confirmed its reliability and safety. nine0003
Method 3: by the history of changing the account name
The easiest way is to check if the person was once called by his own name. And it works even for remote accounts. For the security forces, this is a strong clue.
This is a consequence of the fact that the account ID does not change and if you just save the ID-name-username link, you can track the account history. Also for this, earlier the security forces massively added people to contacts.
Until August 2020, people didn’t worry too much about maintaining anonymity on Telegram, so if the account is old or you have ever been called by your own name, then most likely you can be found. nine0003
The security forces can act like this: find the user they want to "debunk", and then "punch" him through known databases. They have their own database of accounts called "T-Search", they also use paid bots for "breakthrough".
Method number 4: by username
Everything is very simple here - if you use your username on some other site other than Telegram, then you can find it. Even if you did this once, but then “corrected” on the same account.
For this, there is the well-known instrument Maigret, named after Georges Siméon's character Commissioner Jules Maigret. It allows you to search for a username among thousands of resources in all languages of the world.
For the sake of experiment, we looked at the court cases of several political prisoners who were tried in open courts for comments in the telegram.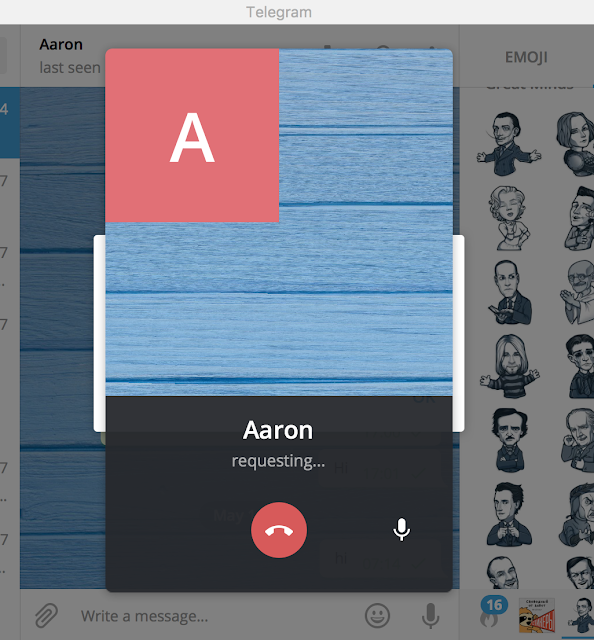 For two out of five randomly selected people, we were able to establish the name and surname of a person by changing the name and surname, and one account has already been deleted.
For two out of five randomly selected people, we were able to establish the name and surname of a person by changing the name and surname, and one account has already been deleted.
In one case, they found a person's linked phone and thus obtained other information. Another username was almost the same as the open instagram, and managed to find his image in a few minutes.
Moreover, we found other social networks and information about a person, having at the beginning, for the sake of the purity of the experiment, neither his name nor his photo, only comments.
In total, the "experiment" took about 30 minutes and we found four out of five commentators. nine0003
Method number 5: by profile picture
If you have your photo or some unique drawing in the telegram, this is also a serious clue for the security forces. Such a picture can be found through a search or various tools if you have it on social networks or you are its author. If this is some place, then it will still give a "tip" to the security forces - at least where you are from, where you traveled, and so on.
Rule #5: Never use your first name or give "leads" to your real identity in your account information. If you have done this before, delete and re-create your account on a non-Belarusian number. nine0003
Method No. 6: according to information from chats
Many people left traces of their activities in 2020. Often these are residential addresses (in yard chats), names, geolocations, even parts of documents or photos of cars. Even the mere belonging to a chatroom of some constituency or house greatly narrows the circle of possible people, not to mention direct pickups.
In closed chats, often people are not "encrypted" at all, and if the security forces got access to it, then a lot of information can be "gotten" from there. nine0003
Rule #6: never give out your real information in chat rooms. To make it harder to identify you, you can, for example, alternate your gender (write about yourself first he, then she) and give random false information.

Rule #7: Don't just chat with your court or county. If you want to be in such a chat, go to 10-15 chats with different localizations at the same time. If you have already "fined" - delete and create an account for a non-Belarusian number.
Method #7: via fake bots
This method was particularly successful during the launch of the Peramoga chat bot by BYPOL. Then the security forces created a network of bots that collected personal data of Belarusians. And for an ignorant person, they looked exactly the same, only Gubopikovsky also collected a telephone, which subsequently made it possible to find a person.
In general, if you start a bot, it gets your ID. And this is already a big risk even if you do not give any information there. nine0003
Rule #8: Be careful what bot you're sending a message to. Do not search for them, but go from the original media pages or channels.
Method #8: through fake links and websites
The security forces have their own services for creating fake links. These methods are "sharpened" to get the user's IP address.
These methods are "sharpened" to get the user's IP address.
The scheme is this: if you control a resource, you can create a link to some material created specifically for some person. If he is the only one who visits the resource, then you already know his IP address. nine0003
This is done through various services. For example, you can create a mirror of a well-known resource or completely invent some other one. It is important that you have control over the statistics and geolocation of those who visit it.
Along with geolocation, you can "pull out" other information in Fingerprint. This is the fingerprint of your browser and, in part, of your system. It allows you to get a lot of information - the browser language, what fonts are installed on your computer, the version of your system, and much more, which will allow you to uniquely identify your device later. nine0003
Rule #9: Don't mindlessly click on links from strangers or public chats. If it's a link to an independent media site or a site you know, it's best to open it on the media site.
If it's a link to something else, then there's an easy way to check if it's true - just type it into any popular search engine and follow it out of it.
Method No. 9: contact books and correspondence
The scheme is very simple - you need to get access to a person's account and download his contact book. Together with other data, this will allow you to find most of his contacts in real life. nine0003
Also, people often call each other by their first names, especially in closed chats and personal correspondence.
Rule #10: Do not add people to contacts under their own names or pseudonyms known to the security forces.
Rule number 11: delete correspondence with all other people once a day. This is easy to do and it will protect you from accidental leaks of unnecessary information.
Rule #12: once a day, also clean the telegram cache and the database cache. You can do this along the path: Settings - Data and storage - Storage usage.
There, select the items "Clear Telegram cache" and "Clear local database". This is important, because a lot of information is stored in the local database - archives of deleted correspondence and cleared chats, some files and metadata, and there is no automatic deletion function. nine0003
Method No. 10: through photo and video
Security forces can find a person with Belarusian citizenship if they have a photo of his face. The main sources are information from correspondence, voice and video messages in dialogues and chats, as well as video calls.
Rule #13: In public chats and correspondence with activists, do not store any photo or video information that would reveal your identity or the identity of other people.
Method #11: via file metadata
All files you create yourself or receive from others contain metadata by default. For photos and videos, the most sensitive is the device from which the photo or video was taken. For documents, the username of the computer on which it was created. Such metadata is created by all computers on all systems.
For documents, the username of the computer on which it was created. Such metadata is created by all computers on all systems.
Telegram saves them only if you send something as a "file", for example, if you want to save the quality of the photo you took. Please be aware of this before submitting sensitive data. nine0003
Rule #14: Before sending files, "clean up" them using various services. This will protect you from "leaking" the metadata.
Method No. 12: through calls and voice messages
If a person is detained, the security forces can "bring" the user to a call with video or at least audio and thus find him.
Audio messages give a lot of information - about what gender a person is, approximate age, timbre and style of speech. If a person is known to the security forces, then this will allow them to be found almost immediately. nine0003
There is also a problem in Telegram that by default calls with contacts are peer-to-peer. This means that two people connect directly and indicate their real IP addresses. P2P calls improve the sound quality a lot, but will allow the security forces to get your real IP when you allow calls, you have internet turned on and a person is in your contacts.
This means that two people connect directly and indicate their real IP addresses. P2P calls improve the sound quality a lot, but will allow the security forces to get your real IP when you allow calls, you have internet turned on and a person is in your contacts.
Rule #15: Don't dump voice messages in public chats.
Rule #16: Do not allow IP calls. You can do this along the path: Settings - Privacy and security - calls - P2P. nine0003
Method #13: through writing style
Many active commentators are recognizable by the way he writes. You do not notice it, but we recognize even our regular commentators from a thousand. The security forces can also analyze this.
Method #14: Fake Files
Almost every type of file has a scheme to obtain an IP address when opening a file. These files are not viruses, so they are not blocked by antivirus programs.
Most of these "tricks" work on Windows, but other systems are also vulnerable. nine0003
nine0003
Rule #17: Don't open files from questionable sources like public chats and private messages from strangers.
Rule #18: Always use a VPN, there are options in Android for this. This feature is also available in many VPN clients on Windows, Linux, Mac and iOS. It's called Kill Switch. This will prevent the device from accessing the internet without a VPN enabled.
Method No. 15: social engineering and the introduction of agents
Social engineering or “attack on a person” is a set of psychological and sociological techniques, methods and technologies that allow you to obtain confidential information. In fact, you need to cunningly deceive a person. It is combined with other methods listed above. nine0003
For example, you can create a fake account that will actively comment on something in the chat. After finding out something about the person you are looking for, for example, that he loves to travel. And then send him a link to some fake text that will allow you to get his IP or understand that he uses a VPN.
Or, further, more, try to strike up a conversation with him and get something about him - gender, age, place of work, circle of curiosities, approximate place of residence. Or, for example, write on behalf of an already detained person in order to find out something. nine0003
This method is different from others, because the task of the enforcers here is to first establish trust. The same with agents - they must pretend that they are supporters of change.
Among the latest such attacks is the creation of the Kosciuszko Battalion. Among the more difficult ones, during the attack on the OGSB groups, the security forces even burned down some kind of tractor in order to infiltrate the ranks of the chat administrators and find the rest of the users. Or the introduction of an agent into the channel of the Black Book of Belarus, which made it possible to detain Roman Protasevich and Sofia Sapieha. nine0003
Rule #19: Be careful. Do not give people from "protest" chats any information about yourself.

Method #16: Torture
This only works if the person is detained and the security forces have not been able to find the exact person behind the username, or they want information about the person's contacts. Now this method is used very widely - they just beat you or humiliate you in different ways until you break.
Most people can't stand the torture and give access to their account. nine0003
Rule #20: Be prepared to be arrested. To do this, clean your devices and take care of your safety regularly, not from time to time.
Method #17: by tracking a specific user
Even if you do everything perfectly, the probability that sooner or later you will “give out” some information about yourself is very high. After all, everyone makes mistakes sooner or later.
And if you are followed personally, then, most likely, sooner or later they will find you. It's just a question of how relevant you are to law enforcement agencies to spend such gigantic resources on you. nine0003
nine0003
Method #18: by removing a person from VPN, proxy or TOP
The next three methods are purely hypothetical. We do not know for sure whether the security forces use them, but they exist and are described in the literature.
The siloviki can use them only if all the other “faster” ones have failed and it is necessary to find some specific person, and not just anyone. Most of the readers are not threatened.
To do this, the security forces need a resource that they can control. Moreover, even real hackers and well-known scammers are being led to this. nine0003
The bottom line is this: when you enter from under some kind of "anonymizer", the site either does not let you in (as the sites of Belarusian government agencies are now), or creates an unbearably long and complicated verification system for you. This forces you to log in under your own IP address, and in Belarusian realities, this means that you are “caught”.
Rule number 21: if a resource requires you to leave the anonymizer, then it is doubtful in any case.
Do not disable anonymization tools, even if you cannot get to some resource. nine0003
Method #19: Timing attack and connection matching
Either the user's activity time or the amount of traffic that the user consumes is tracked. For example, if you have established contact with him, then you can drop him a file of some large size and at the moment fix all the people who have downloaded something of a similar size. So you can narrow the circle of "suspects" hundreds of times.
With activity, the point is to keep a very long record of everyone who was online at one time or another. For example, a person actively writes comments - this is the time of activity at which he joins telegrams. Your task is to record everyone who joined the messenger during this time period. Thus, sooner or later there will be few such people. nine0003
Approximately the same theoretically, you can get the real IP address of a person using a "regular" VPN. You need to get the IP address of the VPN and simply analyze which of the users in Belarus "contacted" with this VPN at the time when the person made an important action for the security forces.
Recommendation: do not go to instant messengers immediately after enabling VPN.
Recommendation: disable automatic file upload in telegram. You can do this along the path: Settings - Data and storage - Media auto download. Auto-download is disabled for all types of connection. In addition, it will help you load telegrams faster, because now images and videos will not be loaded automatically. nine0003
Recommendation:
Method #20: technically difficult methods
They are extremely rare, but they do exist. This, for example, is an attack using sound beacons, deanonymization through Cookies, User Agent and Fingerprint through their long accumulation, through specially created bait files, through the vulnerabilities of the Telegram itself (for example, this one).
If such methods are used against you, then you almost certainly already know about them. Their real use against ordinary Belarusians is unlikely. nine0003
The above rules and methods may not save you if the security forces recorded your data earlier or come to you for another reason.
Initiatives CyberBeaver offers cybersecurity advice to everyone through its secure bot, and their channel contains dozens of instructions on how to protect yourself online. There are also many useful security tips in CyberPartisans.
Read more:
280
67
71
179
99
185
Nashaniva.com
Do you want to share important information anonymously and confidentially? Write to our Telegram
How do telegram calls work and do I need to pay for them?
Now in the Telegram messenger you can not only chat and send voice messages, but also make full-fledged calls. Communication during calls is excellent, the sound quality is much better than during a regular telephone conversation.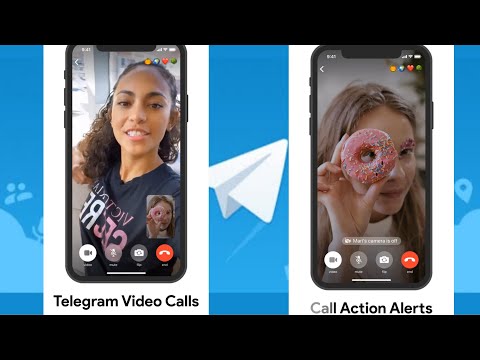 In addition, the developers guarantee users complete security. nine0003
In addition, the developers guarantee users complete security. nine0003
- How do telegram calls work and why are they called secure?
- Paid or not?
- Calls to Telegram on Android
- Calls to Telegram on iOS
- Calls to Telegram Desktop
- Calls to the web version of Telegram
- How to disable calls to Telegram
- Calls to Telegram with number spoofing - how and why?
Many users of the Telegram messenger have probably already noticed the call function. These calls, just like the chats themselves, are end-to-end encrypted. To make sure of this, the application displays the two participants in the call with emoji, and if they match, then the voice call is completely private. nine0003
It is thanks to encryption that the Telegram messenger is so popular. Telegram analogs do not use non-certified encryption tools, so intelligence agencies can gain access to users' correspondence and calls. Telegram developers prioritize security, so your calls and correspondence are securely encrypted from third parties.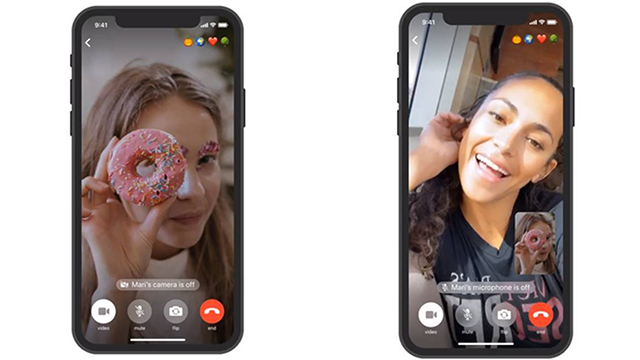
If the user does not want to receive calls from certain people, he can enable the selective blocking function, or disable calls altogether. Calls did not affect the interface of the messenger in any way, it is still just as simple and convenient. In Telegram on iOS, you can make calls in a separate tab, and on Android, this feature can be found in the drop-down menu. nine0003
Recently, it is financially unprofitable to communicate via cellular communication and people are increasingly using Telegram, because you can call in the application for free, except for the cost of the Internet. The function of free calls over the Internet is not new, but Telegram developers still managed to stand out among a large number of competitors.
The fact is that Telegram uses modern compression algorithms and due to this, a minimum of Internet traffic is consumed, while this does not affect the quality of communication. Thanks to such technologies, you can communicate in the messenger by voice using the mobile Internet. That is, it is not necessary to connect to Wi-Fi at all. nine0003
That is, it is not necessary to connect to Wi-Fi at all. nine0003
To make a voice call on Telegram using an Android device, you need to download the application, create an account, find the desired contact and call. To do this, go to the dialog, click on the three dots located at the top right and select the "Call" function.
You can also just go to the profile of the person you need and click on the handset icon located at the top right next to the drop-down menu. After that, the call will start, and when the connection is established, you and the interlocutor will have four emojis in the upper right corner or in the middle. If the symbols for you and the person you called are the same, then the connection is completely private. nine0003
In general, everything here is almost the same as on Android. To call someone on Telegram, you need to do the following:
- Go to chats or contact list.
- Find the desired user.
- Click on the icon with his photo.

- Click on the handset icon.
For convenience, iOS device users can make calls on a separate tab.
Not everyone knows, but the Telegram messenger has a desktop version that can also be used to make voice calls. To do this, you need to download it from the official website and start the installation. When the program is installed, you will need to log into your account. Further, just like in the mobile version of Telegram, you need to enter a dialogue with the desired user and click on the handset icon located in the upper right. nine0003
Unfortunately, calls to Telegram using the web version of the messenger are not available at the moment, but the developers plan to fix this situation in the future.
If you need to make a call to Telegram from a computer, just install the desktop app. It will take no more than seven minutes to install it, and you will be able to fully use all the functionality of the most popular messenger.
If this feature bothers you, you can turn it off completely or block calls to some users. To do this, proceed as follows:
To do this, proceed as follows:
- Open the burger menu at the top left.
- Go to Settings.
- On the page that opens, select "Privacy".
- Next, select the "Calls" item and mark who exactly can call you.
If you do not want to receive calls at all, select "No one", and if you are disturbed by calls from unknown users, select "My contacts". There you can also set up exceptions by adding specific people to whom calls will always be blocked or always allowed, regardless of other settings. nine0003
Number spoofing call is a feature that allows you to make the call anonymous, secure, unlistenable, and untracked. To call with a number substitution in Telegram, you need to use the services of the SafeCalls Telegram bot.
Enter a dialogue with this bot and write the /start command. Next, in the bot menu available from below, select the “Change” command, then click “Caller ID” in the same place and enter the number you want to make a call from.