How to know if someone hacked your instagram
How To Tell If Your Instagram Account Has Been Hacked
Primakov/Shutterstock
By Nor'Adila Hepburn/June 20, 2022 2:11 pm EST
Most Instagram users are not conscious about protecting their information until they fall victim to cybercrime themselves — and by then it is too late. If you are the owner of one or more Instagram accounts, you probably need to be wary as there has been a recent increase in hacking incidents on the platform. It doesn't matter whether you have lots of followers if your account is public or private, any account that is opened can be targeted by hackers.
Out of all the social media apps, Instagram is reported to be the one that is most susceptible to phishing and other online scams (via CodeCondo). Like other apps of its kind, it integrates with other apps and uses cloud storage to save photos and profile information. While this means easy access for users, the company's security measures are no match for sophisticated hackers looking for ways to break into them. Once they are able to hack their way through, the hackers may be able to nab your banking details and other sensitive information.
What are the tell-tale signs?
TY Lim/Shutterstock
The most surefire way to know if you've been hacked is if you are unable to login into your account. In that case, you should take the following steps immediately:
1. Check to see if you received an e-mail from [email protected]
2. When you find the e-mail, look for the "revert this change" button in the message, and select it. Once you click on it you may be able to undo the change (via Instagram).
You can also request a login link, security code, or support from Instagram to resolve your issue. Instagram may ask you to verify your information with a photo, so they know it's actually you.
Another sign that the account is comprised is that your e-mail or registered phone number has been changed. This is often the first thing that will be changed so that you'll stop getting notifications. You can also check the settings page to see if there are unfamiliar devices logging into your account. If you see strange activity such as unknown messages to other people being sent from your account, subscribing to new accounts, or your account is blocked due to spam complaints, odds are strong that a hacker is controlling your account (via RTE and Consumer Reports).
This is often the first thing that will be changed so that you'll stop getting notifications. You can also check the settings page to see if there are unfamiliar devices logging into your account. If you see strange activity such as unknown messages to other people being sent from your account, subscribing to new accounts, or your account is blocked due to spam complaints, odds are strong that a hacker is controlling your account (via RTE and Consumer Reports).
Sometimes, alerts can come from your connections who've picked up that something is wrong and will let you know that they think you've been hacked.
How to protect yourself
Sergei Elagin/Shutterstock
So, how can you prevent your account from being stolen from right under your nose?
Ortal Levitan, a social media expert, says that hackers will usually send DMs to you from accounts that look exactly like official Instagram accounts. "These messages state that their account has been violating Instagram guidelines, or they have done something that goes against what Instagram is OK with. But, the main point of these messages is that the sender wants you to click on a (malicious) link," she says in a recent YouTube video. "A lot of people will click on the link without even thinking. And once you click on that link, they can steal all your login info, and can access your account."
"These messages state that their account has been violating Instagram guidelines, or they have done something that goes against what Instagram is OK with. But, the main point of these messages is that the sender wants you to click on a (malicious) link," she says in a recent YouTube video. "A lot of people will click on the link without even thinking. And once you click on that link, they can steal all your login info, and can access your account."
Her top advice boils down to two rules: Instagram never DMs anyone and if you get a message in your inbox from someone claiming that they are from Instagram, it's a fraud.
Another way you can protect yourself is to use a more difficult password to enter your account. Also, you can set up Two Factor Authentication which requires you to enter an additional log-in code or confirm your login account through a third-party app like Google Authenticator when logging in to any of your accounts (via Instagram).
Recommended
Warning signs your Instagram account has been hacked and what to do about it
Whether you’re a prolific selfie poster, get a kick from hilarious meme accounts, or just like to see what your friends are up to, Instagram can be a whole lot of fun – until your account gets hacked, that is.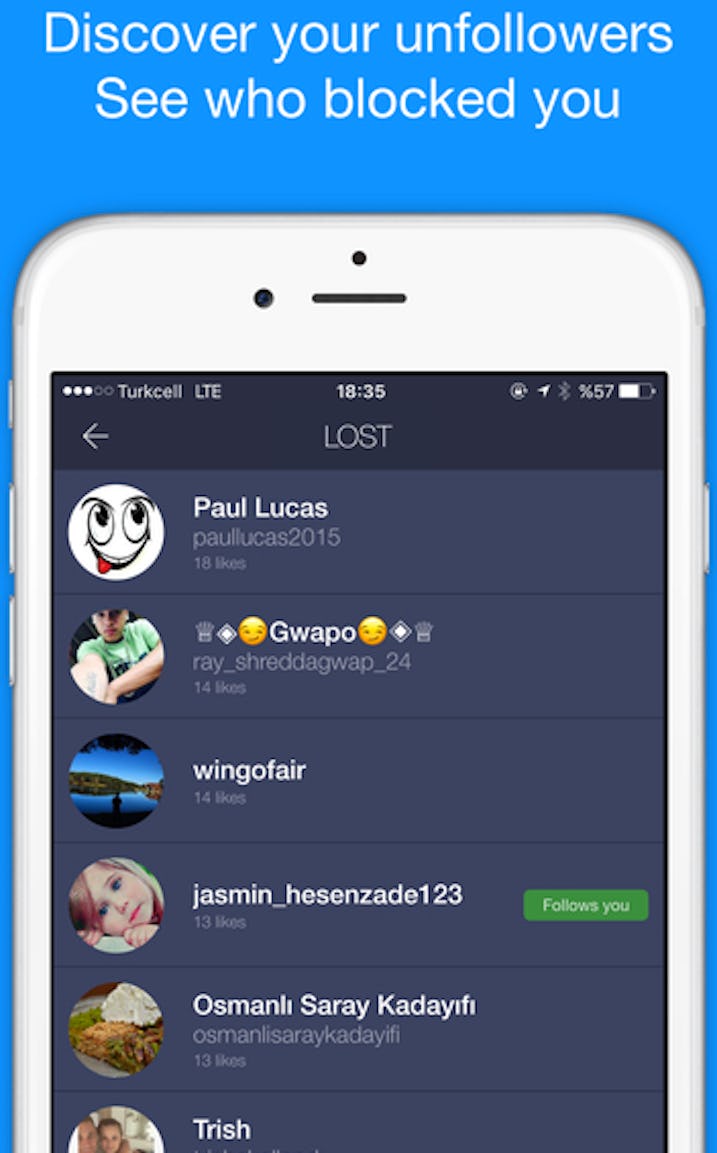
Even if you don’t have millions (or even thousands) of followers, you could still be targeted by cyber criminals – and sometimes it’s not obvious if someone else has gained access to your profile.
We asked digital security experts to explain the red flags to watch out for, and what to do if your Instagram account is hacked.
Woman holding mobile phoneWhy do hackers target Instagram accounts?
“Instagram scams are rampant right now, a result of its growing popularity and influence,” says Tom Gaffney, principal security expert at F-Secure, who believes that fake brand accounts, usually pushing counterfeit goods, may be responsible. “The power of Instagram is in how many followers you have – the more followers these brands can build, the more they can push other nefarious activity.”
Stuart Dobbie, SVP of innovation at Callsign, warns that fraudsters target social media accounts in an attempt to steal confidential information: “Regardless of whether you have a lot of followers, your Instagram profile will have your phone number, email address and other pieces of information private to you. If a fraudster hacks into this, they can access all of it – and they can then use this information elsewhere.”
If a fraudster hacks into this, they can access all of it – and they can then use this information elsewhere.”
In some cases – usually accounts with many followers – the hackers will contact the owner and threaten to delete the account if a ransom (usually Bitcoin) isn’t paid.
App icons on mobile phone screenGaffney adds: “Hackers don’t tend to differentiate on the target as their attacks are automated and at scale, this means they will affect users even with very few followers.”
How can you tell if your account has been hacked?
Unless the hacker gets in contact to demand payment, your account could be compromised without you even knowing it.
“The most obvious sign is if there has been a change to your registered email or phone number,” says Gaffney. “Hackers often will alter this first to avoid you getting any notifications. You can check in your Insta settings if this has been changed.”
Also in the settings page, you can see which devices have logged into your account: “If it’s a device you are unfamiliar with then that is a clear warning sign.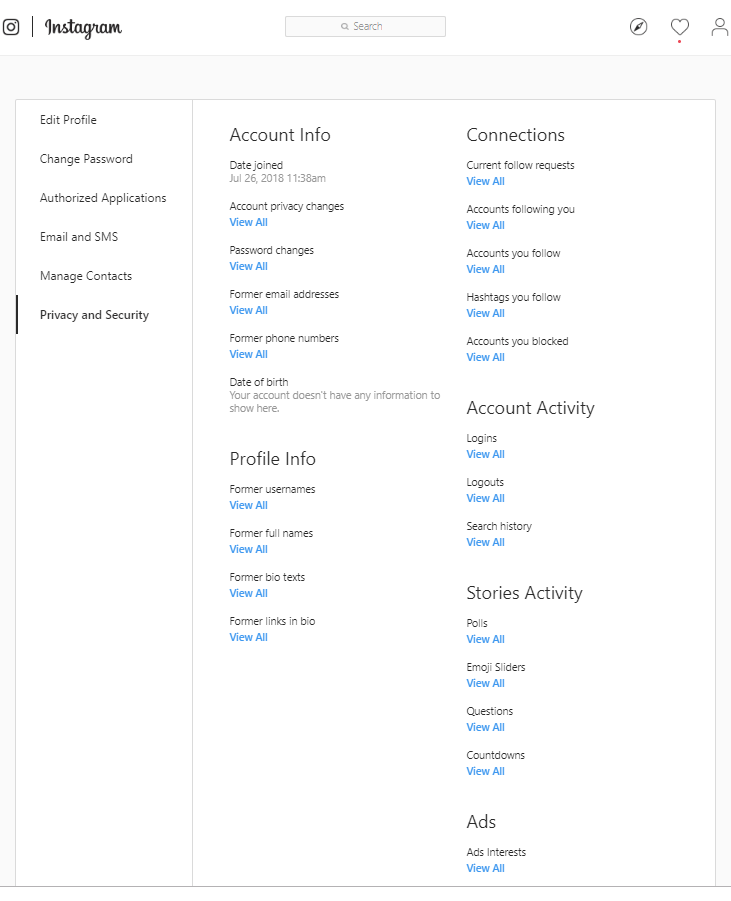 ”
”
David Sygula, senior analyst at CybelAngel, says to watch out for unusual activity linked to your profile. For example: “You get a notification of a suspicious connection, you seem to have sent messages to a lot of people, your account was blocked for spamming or you have subscribed to dozens of accounts without knowing it.”
If you’re lucky, a friend or follower might alert you to a weird message they’ve received.
“Hackers are more likely to use direct messaging as that is less noticeable,” Gaffney explains. “If you see direct messages being sent that were not from you – that’s another red flag.”
What should you do if your account is hacked?
If you notice any suspicious activity and you’ve still got access to your account, log in and change your password immediately, choosing a strong password made up of upper and lower cases letters and special characters.
If you can’t log in, check whether you’ve received an email from [email protected] (beware of similar but fake addresses) saying your email address was changed and choose the ‘Revert this change’ option.
If you still can’t log in, go to the Hacked Accounts page (via help.instagram.com) and follow the instructions to try and recover your account.
In the case of financial scams, Gaffney advises: “Always report hacking to Instagram and never pay the fine. Instagram can help verify your identity and check for account misuse.”
How to understand that you have been hacked and what to do about it
Our accounts in social networks and online services can be compromised, so it is very important to understand the risks and what to do to protect yourself - we have translated an article from Wired dedicated to these issues for you.
The average person is likely to face fewer complex threats than, say, a high-ranking official, activist, or CEO of a company. Public figures may be subject to phishing, which targets sensitive information from corporate networks or steals large sums of money. You, your friends and family are likely to face various other threats, from the revenge of acquaintances, to, more likely, attacks by criminal groups using automated tools for mass collection of credentials.
“We all like to think that we are not subject to social engineering or other types of cyber attacks, but the truth is that even smart, conscientious people fall for online scams that can have devastating financial and social consequences,” says Jake Moore, Eset specialist.
Understanding threats is the key to success. Each person has their own pattern of threats to the things that matter most to them. What's important to you may not be as important to others, but there are shared values in the internet space, whether it's Facebook and Netflix or online banking and shopping. If one of your accounts is compromised, the stolen login or financial details may be used. For example, in a scenario where people order takeaway food through hacked personal accounts in Deliveroo.
While Facebook, Instagram, and other social networks are unlikely to contain your credit card information, there are other risks. Hacked social media accounts can be used to post compromising messages that defame someone, be used to harass or make up your portrait.
If you suspect you've been hacked, here's what to do.
.
Fix unusual behavior
.
The obvious sign that you have been hacked is the changes that have taken place. For example, you can't access your Google account using your regular username and password, or a suspicious purchase has been made on one of your bank accounts. These are pretty clear signs of an account being compromised. It is to be hoped that banks will detect any suspicious payments before things go too far.
But warning signs may appear before an account is hacked. An account that someone is trying to hack can signal unusual login attempts. For example, Facebook and Google will send emails notifying you of attempts to access your account. This usually happens if someone tried to log in and failed, but alerts can also be sent when someone has successfully logged in from an unfamiliar location.
Nearly every day, a company, app, or website suffers a data breach, from Adobe to Dungeons and Dragons. Leaks can include phone numbers, passwords, credit card details, and other information. Companies should report hacks to you quickly, but there are third-party services for this, such as Haveibeenpwned and F-Secure identity checker.
Leaks can include phone numbers, passwords, credit card details, and other information. Companies should report hacks to you quickly, but there are third-party services for this, such as Haveibeenpwned and F-Secure identity checker.
.
Take back control
.
The moment you find out your account has been hacked, the hard work begins. Restoring control of an account can be difficult, depending on who has access to it, and it is likely that it will require the involvement of a large number of people, from administrators to law enforcement.
First of all, you must contact the company that owns your account. Each organization has its own policies, procedures, and instructions for recovering compromised accounts. They can be easily found with an online search. The Facebook account recovery tool is here; Google is here; Netflix is here.
When recovering a compromised account on the Internet, the recovery instructions will depend on how quickly you regain access.
If you are unable to access, you will most likely be asked for additional information (previous passwords, email addresses, security questions, and more). If a person claims to have accessed your account and sent you a message about it, do not click on the links they send, as this may be a lie in order to gain access to more personal information.
Company account recovery is the first step in regaining control. You need to make sure that all the apps and software you use (on your phone and desktop) are up to date. Further actions depend on what was compromised. For example, if you can get back into a hacked email account, it's worth checking your settings to make sure they haven't been changed. Because, let's say, the setting to automatically forward all your emails to another account can be enabled.
You should change the password of the compromised account and any other accounts using the same password and contact anyone who may have been hacked. So, if the messages were sent from your Instagram account or you are forced to create a completely new social media account, it is worth telling friends and family the details of the new page or explain what kind of spam came from you.:strip_icc():format(jpeg)/kly-media-production/medias/1567942/original/069288900_1492327279-Screen_Shot_2017-04-16_at_13.56.53.jpg)
If necessary, you can report a break-in to law enforcement, for example, in case of bullying.
.
Secure everything
The best way to reduce the chance of being hacked is to limit what can be attacked. The better your online hygiene, the less risk you have of being hacked. Although some attacks will always occur, especially from actors with specific targets.
"Information about you is the key to a successful attack, so minimizing your personal data available online will force an attacker to find a less fortunate victim," says Moore.
If your accounts have been compromised once, you are more likely to be targeted again.
You must think about how much information you actively post on the Internet. “I advise making it difficult to access information about yourself,” Eva Galperin, director of cybersecurity at the Electronic Frontier Foundation, said earlier. - When you post photos of yourself on Instagram or post on Facebook or tag a location in a post, people can take that information and publish it without your consent. What people can really say about you is what you have already said about yourself.”
What people can really say about you is what you have already said about yourself.”
There are many things you can do to make your accounts more secure. So, you should use a password manager to create and store unique, strong passwords. You shouldn't use the same password on multiple sites, even if you think the risk of being hacked is low.
If you were hacked into one account, you need to look at the other accounts you use: update passwords and check security settings. When you upgrade your accounts, you should use complex verification questions. Only you should know the answers.
In addition, take a moment to look at the accounts you no longer use. What information is stored there?
Like a password manager, multi-factor authentication (MFA) should be enabled for as many sites and services as possible. This is one of the most effective ways to protect your accounts from hackers. The most common type of MFA is two-factor authentication, which requires something other than a password to log into an account. Most often this is an SMS message, an authenticator application, etc. A list of websites and applications that support 2FA can be found here.
Most often this is an SMS message, an authenticator application, etc. A list of websites and applications that support 2FA can be found here.
For high threat individuals, there are a number of additional steps that can be taken. To increase your privacy and anonymity on the Internet, you can use a VPN, Tor, or Google's advanced security program.
***
Roskomsvoboda also has safety tips — visit the SAFE project page.
Original article
[2022] How to find out who hacked your Instagram?
Before you begin
Instagram is one of the most popular social media platforms among young people, celebrities and famous brands. Due to its growing popularity, the Instagram audience has become an easy target for hackers.
We often see news of celebrity and brand Instagram accounts being hacked. If a user is not serious about the security of their account, it can be easily hacked by hackers in just a couple of minutes.
In this article, we will tell you how to find out who is trying to hack your Instagram account , how to prevent such hacking and what to do if your Instagram account has been hacked.
- 1. 3 ways to find out who hacked your Instagram account
- 2. 4 things to prevent your Instagram account from being hacked
- 3. Tips: How to recover a hacked Instagram account
1. How to find out who hacked my Instagram
If you notice unusual activity on your Instagram account, chances are your account has already been hacked. Here are the steps to take if your Instagram account has been hacked.
Method 1: Detect with anti-spyware software
A hacker gets hold of his victim's Instagram account credentials using spyware. Spyware is installed on the victim's phone in various ways, and they record the credentials when the victim logs into their Instagram account.
ClevGuard Anti-Spyware is a reliable spyware detection application that you can use to scan and detect spyware present on your phone.
Step 1. Click on "Download from Google Play" as shown below to install ClevGuard Anti-Spyware.
Step 2. After installing the application, check the privacy policy and click the "Get Started" button to get started.
Step 3. Click the "Scan" icon to start a detailed scan of your phone. Once the scan is complete, you will see a list of the spy apps present along with their names.
You can also report these apps to ClevGuard if you think an app on your phone is spyware.
Method 2: Report your account to Instagram Support
Once you discover that your Instagram account has been hacked, you must report it to find out who hacked your account.
Step 1. Go to the Instagram help center and click on "Privacy, security and protection".
Step 2. Click on "Username and Password" and go to the "Login" section.
Step 3. Click on "I can't sign in" and go to the "I think my Instagram account has been hacked" section. Here you will find all the possible scenarios and steps you need to take to recover your account, depending on your situation.
Once you have recovered your account, you should contact support and ask them to provide you with the latest login details. Login information must include IP address, login information, time, and device used. You can easily determine the hacker's IP address, as it will be different from yours.
Tracking the IP address on the Internet will help you locate the hacker.
Method 3: Help the police
The best way to find someone who hacked your Instagram account is to contact the nearest police station for help. This is because they have the necessary resources and permissions to pull Instagram details that you would never get from a support team.
Step 1. You must file a complaint about the hacked Instagram account with all possible details.
Step 2: The police station can refer the case to the cybersecurity department. The Cybersecurity Department will initiate an investigation and take appropriate action.
Step 3: The relevant officials will contact the Instagram team to find out the details of your account activity and obtain the hacker's login details.
Step 4. If the IP address is real, it will be easy for them to locate the hacker. However, if the hacker is using a VPN, it will be difficult to trace him. However, most often the hacker is among the followers of the hacked account. Therefore, the relevant officials may conduct additional investigations against suspicious followers of your account in order to identify it, if possible.
2. How to prevent your Instagram account from being hacked?
Now that you know how to find out who hacked your Instagram account , let's move on to preventive measures. Prevention is always better than finding a quick fix. In fact, if you take all preventive steps in advance, it will be very difficult for a hacker to gain access to your Instagram account.
Enable Two-Factor Authentication
Two-Factor Authentication requires the user to enter credentials to log in, as well as a code sent to a phone number.
So if a hacker somehow manages to get your credentials, he won't be able to log in. This is because he will not receive the code sent to your phone number.
This is because he will not receive the code sent to your phone number.
Check your account login activity
You can check your account login activity in the Security section of the app. You will see all the devices on which your account is currently registered.
In addition, you will see the geographical location of the devices. If you suspect something out of the ordinary, you can sign out of all devices. In addition, you must revoke permission to access any suspicious third-party application.
View messages from Instagram
Instagram constantly alerts users via email when it detects unusual activity on an account. If someone tries to reset your password, log into your account from a new device or location, change your password, or even change your email address, you will receive an immediate email notification to your associated address.
In fact, you can undo changes via email if you can take action immediately.
Install ClevGuard Anti-Spyware
Spyware on your phone can record your account credentials when you enter them and pass them on to a hacker. ClevGuard Anti-Spy has a special feature that prevents hackers from installing spyware.
ClevGuard Anti-Spy has a special feature that prevents hackers from installing spyware.
This feature is called "Real-time Protection" and will keep your phone fully protected 24 hours a day, 7 days a week. You will be notified as soon as the spyware detection application detects attempts to download and install spyware.
3. Tips: How to recover a hacked Instagram account
If you are wondering how to recover a hacked Instagram account , then here is the answer. If you haven't changed your password, but you can't sign in with your password, then your account has been hacked.
To confirm, you can check your email where you should find the password change notification.
Below is a list of steps you need to take to recover your Instagram account after being hacked.
Step 1: Check your email account
When a hacker changed your password, Instagram should immediately notify you via your email. So check your inbox and look for the email notification.
In the body of the email, you will find the "Revert this change" option. Click on it and follow the on-screen instructions to see if you can recover your account.
Step 2: Get the login link
If the changes were not reverted, do the following.
1. Go to the login screen.
2. Click on the "Forgot your password?" option.
3. On the next "Find Your Account" screen, enter the username, email address, or phone number associated with your account. Click on the "Next" button.
4. You will be prompted to select an email address or phone number to send the login link to.
You will receive a login link to your email address or phone number. By clicking on the link, you can reset your password and log into your account.
Step 3: Request a security code
If the login link does not work, you need to request a security code.
1. Click on the "I can't access this email or phone number" option.
2.