How to hack someones instagram password for free
The Easiest Way to Hack Your Instagram Password
Skip to main content
The Easiest Way to Hack Your Instagram PasswordMaat Hernandez
Maat Hernandez
Python Engineer at Ricoh USA, Inc.
Published Apr 4, 2023
+ Follow
Hacking Instagram accounts is illegal and unethical. However, there are many tools and methods available online that claim to help users hack into Instagram accounts. In this blog, we will explore the easiest way to hack your Instagram password and discuss why you should never attempt to hack someone else's account.
I. The Risks of Hacking Instagram Passwords
Hacking into someone else's Instagram account is illegal and can result in severe legal consequences, including fines and imprisonment. It is also unethical to invade someone's privacy and access their personal information without their consent. Additionally, attempting to hack someone's account can damage your reputation and relationships.
II. The Easiest Way to Hack Your Own Instagram Password
If you have forgotten your Instagram password and need to regain access to your account, the easiest way to do so is through Instagram's "Forgot Password" feature. This feature allows you to reset your password through your email address or phone number associated with your account. You can also verify your identity by providing additional information, such as a government-issued ID or a photo of yourself holding a piece of paper with a specific code.
III. Why You Should Never Attempt to Hack Someone Else's Instagram Account
Attempting to hack someone else's Instagram account is illegal and unethical. It can cause harm to the account owner and their followers, as well as damage your own reputation and relationships. It is important to respect other people's privacy and not engage in any behavior that could potentially harm them.
It is important to respect other people's privacy and not engage in any behavior that could potentially harm them.
In conclusion, hacking Instagram passwords is illegal and unethical. If you need to regain access to your own account, use Instagram's "Forgot Password" feature and follow their verification process. Never attempt to hack someone else's account, as it can result in legal consequences and cause harm to others.
-
Ethical Hacker
Apr 22, 2023
-
What is iPhone Text Message Hack All About?
Apr 20, 2023
-
How to Reverse Hack a Hacker
Apr 19, 2023
-
Hack Iphone Messages
Apr 19, 2023
-
Know Secrets Another Phone With Phone Hacking Services
Apr 18, 2023
-
How To Remove A WhatsApp Hacker From My iPhone
Apr 18, 2023
-
How to hack a WhatsApp number
Apr 18, 2023
-
Three Things A Facebook Hacker Will Try
Apr 17, 2023
-
How To Find A Good Phone Hacker From Hackerslist
Apr 17, 2023
-
What to Do If Your Facebook Account Is Hacked
Apr 17, 2023
How To hack Someone's Instagram Account
Skip to main content
How To hack Someone's Instagram AccountMaat Hernandez
Maat Hernandez
Python Engineer at Ricoh USA, Inc.
Published Mar 5, 2023
+ Follow
Instagram has become a vital part of our lives, and it is no surprise that people are interested in learning how to hack an Instagram account. While hacking someone's account is illegal and unethical, ethical hacking can be used to enhance security and protect against malicious attacks. Ethical hacking involves identifying vulnerabilities in a system and exploiting them to improve security. In this blog post, we will discuss how to hack someone's Instagram account.
I. What is ethical hacking?
Ethical hacking is a process of identifying security vulnerabilities in a system or network and using them to improve security. It is an authorized and legal way of identifying weaknesses in a system to enhance its security. Ethical hackers are also known as white hat hackers, and they use their skills to help organizations and businesses identify and fix security vulnerabilities. Ethical hacking is crucial in protecting personal and sensitive information from cyber-criminals.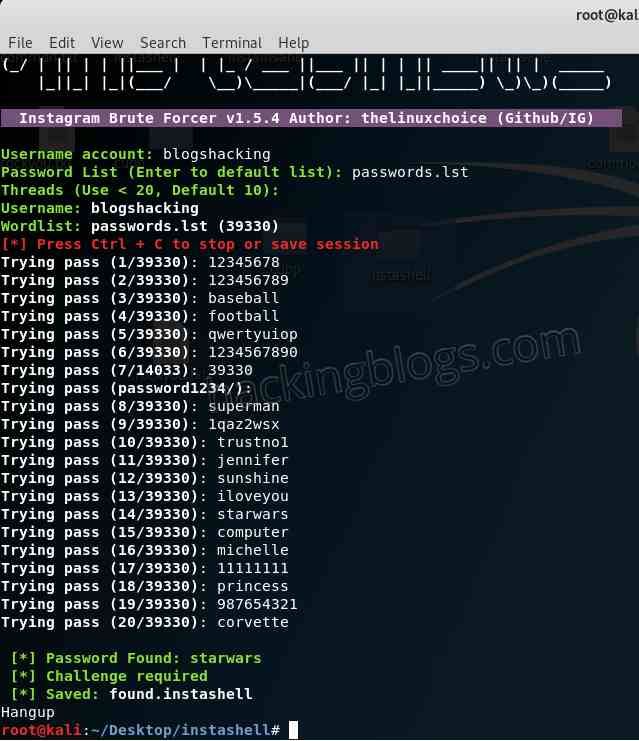
II. How to perform ethical hacking on Instagram accounts
To perform ethical hacking on an Instagram account, you need to identify the vulnerabilities in the system. Some of the common vulnerabilities include weak passwords, unsecured internet connections, and outdated software. Once you have identified the vulnerability, you can exploit it to gain access to the account. However, it is important to obtain permission from the account owner before attempting to hack into their account. This will ensure that your actions are legal and ethical.
III. Tools and techniques used in ethical hacking
There are several tools and techniques used in ethical hacking. One of the most common tools is Metasploit, which is an open-source framework that helps identify and exploit vulnerabilities. Other tools include Nmap, which is a port scanner that identifies open ports and their services, and Wireshark, which is a packet sniffer that captures and analyzes network traffic. Additionally, social engineering techniques such as phishing and pretexting can also be used to exploit human weaknesses and gain access to an account.
IV. Conclusion
In conclusion, ethical hacking is a legal and authorized process of identifying and exploiting vulnerabilities in a system or network. It is an important practice that helps improve security and protect personal and sensitive information. However, it is important to obtain permission from the account owner before attempting to hack into their account. Ethical hacking is not about breaking laws or violating someone's privacy but is instead about enhancing security and preventing malicious attacks. By following ethical practices and using the right tools and techniques, ethical hacking can be an effective way to enhance security and protect sensitive information.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools #bushwhacking #hacking_or_secutiy #porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
Ethical Hacker
Apr 22, 2023
-
What is iPhone Text Message Hack All About?
Apr 20, 2023
-
How to Reverse Hack a Hacker
Apr 19, 2023
-
Hack Iphone Messages
Apr 19, 2023
-
Know Secrets Another Phone With Phone Hacking Services
Apr 18, 2023
-
How To Remove A WhatsApp Hacker From My iPhone
Apr 18, 2023
-
How to hack a WhatsApp number
Apr 18, 2023
-
Three Things A Facebook Hacker Will Try
Apr 17, 2023
-
How To Find A Good Phone Hacker From Hackerslist
Apr 17, 2023
-
What to Do If Your Facebook Account Is Hacked
Apr 17, 2023
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil. " The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
" The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on.
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password.
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It's possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that.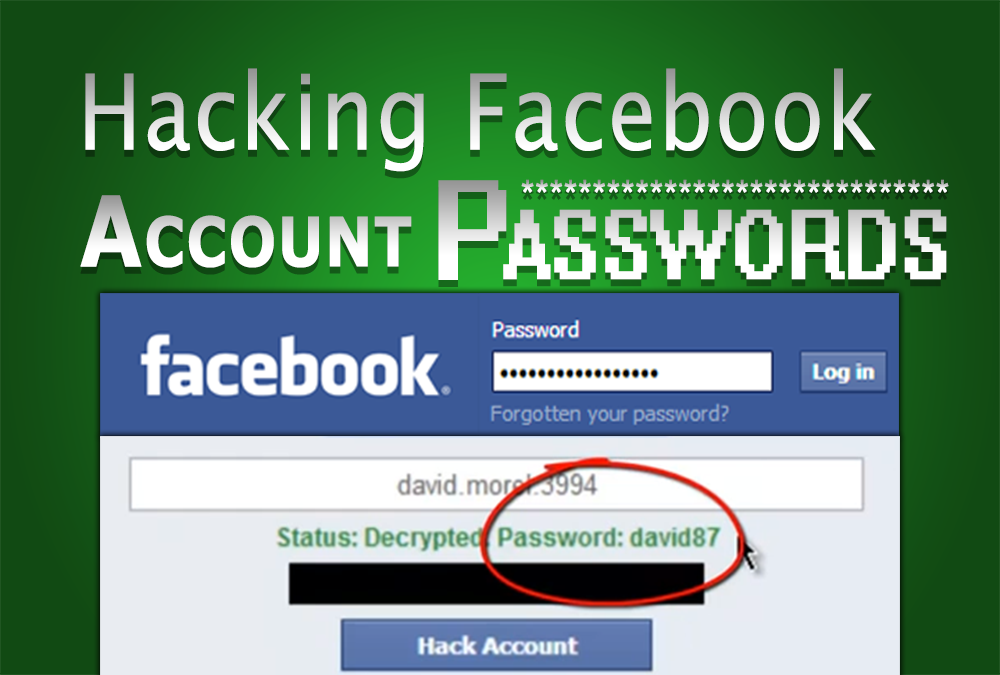 Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually.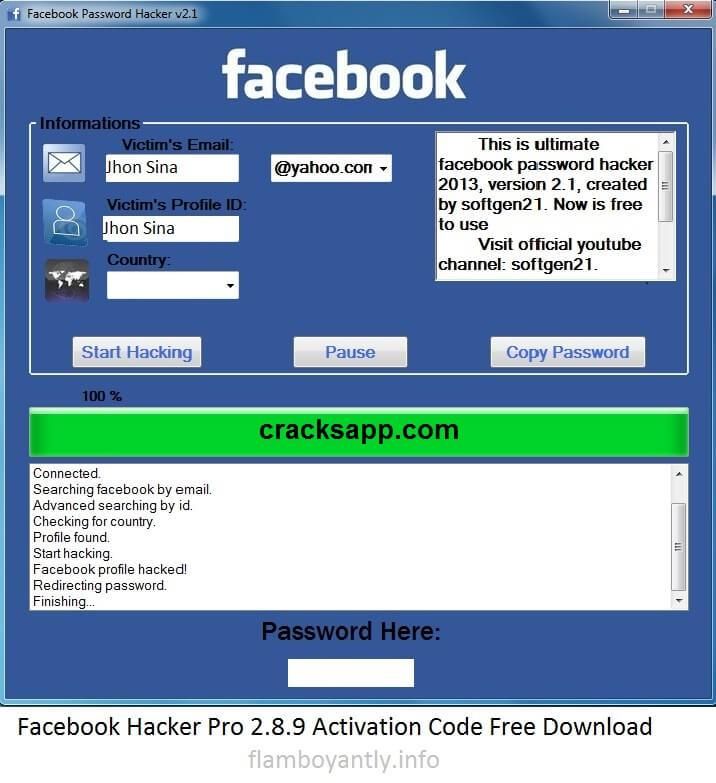 If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings.
 This will reset the access tokens.
This will reset the access tokens. - Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them. If they managed to do this, change it back to yours.
- Set a new password that is strong and one that you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress.
Tips
Five attacks on hardware crypto wallets
Hardware crypto wallets effectively protect cryptocurrencies, but they can also steal your money from them. Let's figure out what risks their owners need to protect themselves from.
Let's figure out what risks their owners need to protect themselves from.
How to protect your smart home
In order for a smart home to bring you more benefit than harm, it must be properly configured and fully protected. Let's analyze the protection of a smart home in detail.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site. I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
Top 5 ways how to hack Instagram from phone 2023
Do not know how to crack the password (page, profile) from Instagram? Looking for a reliable Instagram account hack to read correspondence and see photos? Reliable 5 Ways to Hack Insta - It's not as hard as you think!
Instagram hacking is an illegal act that can deprive you of a decent amount of money in the form of a fine and even reward you with a real prison term.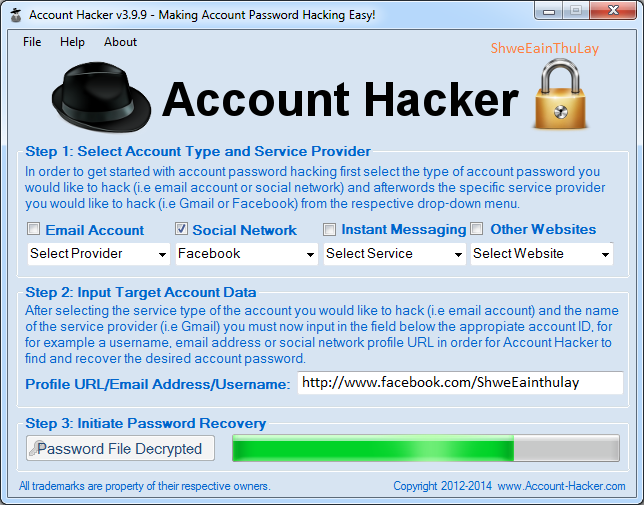 Therefore, before doing something in this area, think about it, is it really so important and necessary for you?
Therefore, before doing something in this area, think about it, is it really so important and necessary for you?
Top 5 ways to hack Instagram from your phone 2023
Method 1. Specialized application
We start with the simplest and most realistic (which can be used by everyone without exception) way to hack Instagram - you need to take only 10 (!) minutes phone and quickly there download free Reptilicus , install and configure. This is easy enough to do. Everything is in Russian. Extremely understandable. If you have any questions, the site has picture guide , instruction video, as well as online consultants.
After installing the application you will be able to:
- read the correspondence without going to the page;
- see photos without hacking account;
- remotely see the location of a person when he is in the profile;
- see the photos he has saved on his phone;
- see photos that were sent to him, and then he deleted them;
- see what groups are watching and what is liking.
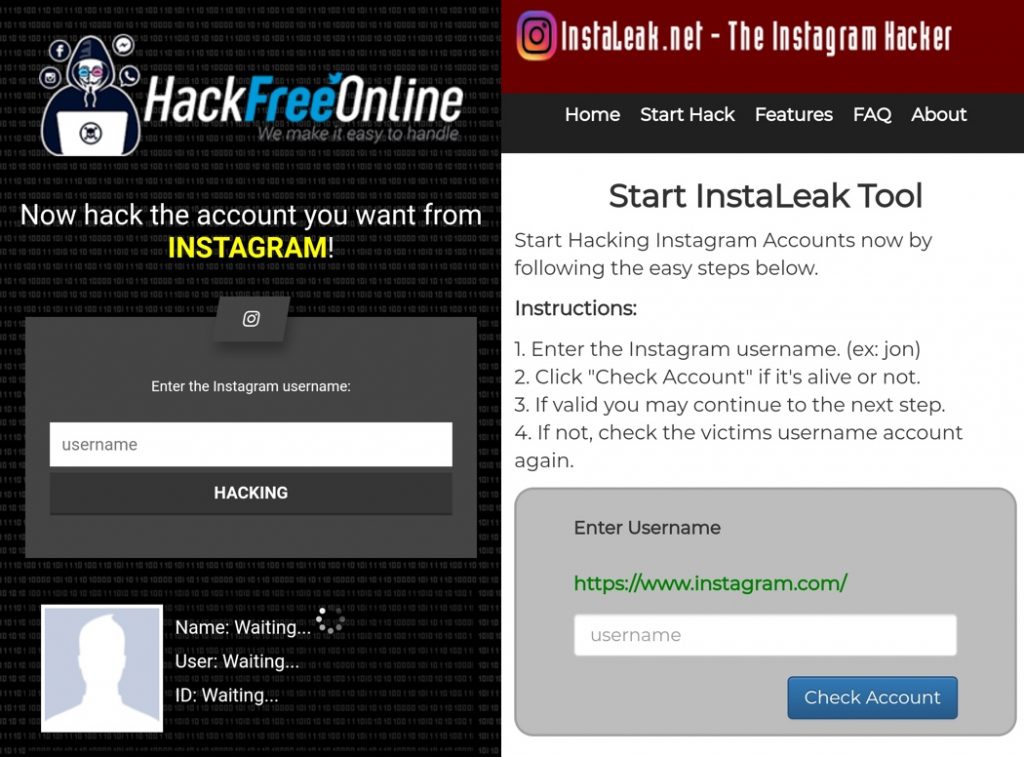
All this will become available when you install the special Reptilicus application on your phone. We offer not hacking an Instagram account, but control - this is the ability to remotely control a person's activities in this social network without penetrating his page and without performing any illegal actions combined with hacking.
In simple words, you won't need to hack your Instagram profile, you just install the program on your phone, and the program itself will send you everything that a person does on his phone, including on his page on Instagram.
Method 2. “Forgot password” function
We continue our review ... this is the most obvious method that (we don’t know for what reason) people don’t see on their own, although it lies on the surface. Yes, imagine, you can crack the Instagram password in order to get into the page using a function that allows you to recover a forgotten password. Here you need to know only the login (nickname) of the person. Just? Yes! Why didn't you think of this before? We do not know! So, you need to take the following steps:
Just? Yes! Why didn't you think of this before? We do not know! So, you need to take the following steps:
Step 1. If you have your own page, then go to your account - click on the Instagram icon - the home page will open. If not, then just go through the search engine.
Step 2. Press "Menu" - press "Add Account" - the standard menu for logging into your account will open.
Step 3. Enter the username (nickname/login) - click "Forgot Password".
Step 4. Select confirmation via SMS - enter your phone number - wait for SMS with a link to change your password.
Step 5. Open SMS - in the Change Password section, click on change password - change password.
That's it, now you know how to crack an Instagram password! No need to thank.
Method 3. Intercepting keystrokes
You have probably heard that there are programs that can save keystrokes on your phone.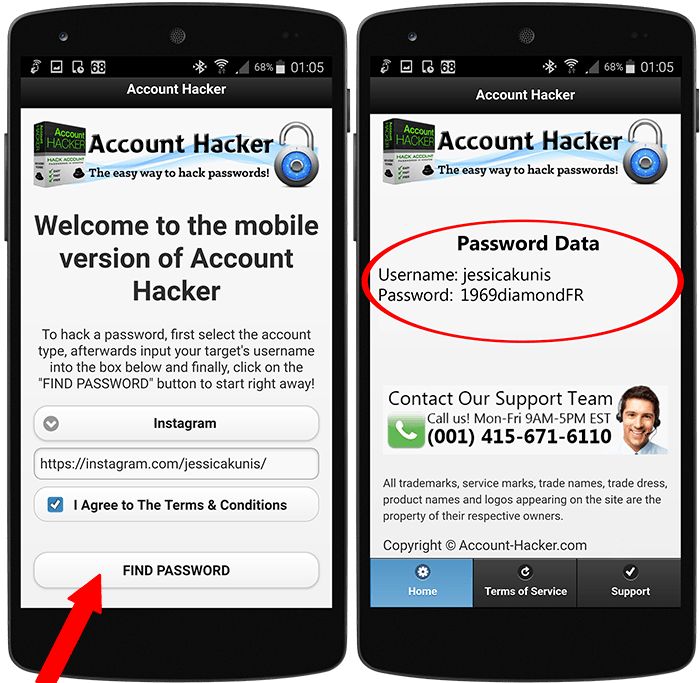 And if you are thinking about how to hack an account on Instagram, then this method can allow you to intercept messages typed on your phone when communicating on Instagram.
And if you are thinking about how to hack an account on Instagram, then this method can allow you to intercept messages typed on your phone when communicating on Instagram.
The Reptilicus program will help you to see literally everything that the person whose correspondence you are so interested in is typing on his phone. You can also install any other keylogger, of which there are quite a lot on the Internet. We are just talking about our program, tested by time and users. You can hack an Instagram page with a simple installation. There are reviews of real users (the forum is over 7 years old).
Method 4. Chat screenshots
Chat screenshots, screenshots or instant screenshots (call it what you want, the meaning of this will not change in any way) is a real opportunity to do without the treacherous hacking of Insta. The screenshots will show all the correspondence, with emoticons, with all the actions that a person performs on his phone.
Screenshots are taken automatically and without root rights, as well as keyboard interception. They will start coming as soon as a person goes to the page on Insta. To do this, you need to check the box in the program settings so that screenshots start working when you enter Instagram.
They will start coming as soon as a person goes to the page on Insta. To do this, you need to check the box in the program settings so that screenshots start working when you enter Instagram.
If you want to receive screenshots around the clock, and not just when you enter Insta, then do not set any restrictions. The settings are very convenient - make sure by looking at the manual. You can do this, but you can do that. Adjust as you need. If you want to receive screenshots every 10 seconds, get it, if you want only correspondence, please, receive only correspondence. Here the choice is entirely yours.
Method 5. Phishing
This method is considered the easiest, but at the same time the most illegal. This is a gross scam. Therefore, we do not advise you to use it. BUT... as we provide possible ways, phishing will help you understand how to hack Instagram through a computer.
This method is that you create a phishing (false, fake) page to enter Instagram. At first glance, it will not differ from the standard in any way. Only one letter will be changed there, or some symbol invisible to the naked eye will be added. BUT it will be DIFFERENT. The user enters his username and password there and transfers it to a regular Instagram. Therefore, he will never guess that he was on this fake page. But ... but you will receive his nickname and password.
At first glance, it will not differ from the standard in any way. Only one letter will be changed there, or some symbol invisible to the naked eye will be added. BUT it will be DIFFERENT. The user enters his username and password there and transfers it to a regular Instagram. Therefore, he will never guess that he was on this fake page. But ... but you will receive his nickname and password.
You can read about how to create a phishing page on the Internet. We do not approve of this method and just brought it as really working and existing for those people who need to know how to hack the Instagram of a friend, girlfriend, wife, husband or their children through their computer.
Conclusion
How to hack someone else's Instagram? There are different ways. We told you about them. Now it's your turn - choose wisely. We certainly advise you to use our service. If difficulties arise, there are always online consultants on the site who will explain in detail and answer all your questions.