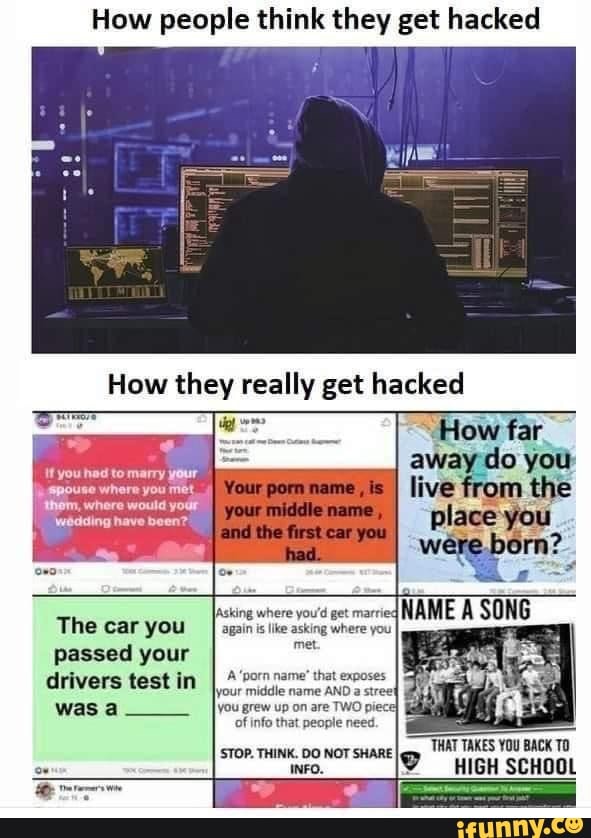
How do people get hacked on instagram
How Your Instagram Account Can Be Hacked and How To Stop It
Instagram is one of the most popular social media apps, so of course, it is a big target for cybercriminals who want to hack into accounts.
So how do people hack your Instagram? What are the consequences of this happening? And what can you do to secure your Instagram account?
Instagram hacking happens in several ways. Many attempts involve social engineering, which manipulates users whose accounts are susceptible to attacks.
These are the most common methods of hacking Instagram profiles.
How Do People Hack Instagram With Malicious Software?
Some hackers infect computers with keylogging software. It records anything someone types, allowing unauthorized parties to capture your Instagram login details that way. Alternatively, malicious software could get on your computer after you click a suspicious link or download a dangerous attachment.
Numerous fraudulent websites use phishing tactics to learn passwords or encourage people to sign up to access accounts.
Determined cybercriminals can target accounts to crack them, but obviously, the software they use is illegal in most countries. In some cases, the software itself is fraudulent too, used to trick people who want to get into someone else's profile into falling victim themselves.
How Do Instagram Accounts Get Hacked Through Third-Party Apps?
Instagram hacks also happen indirectly. Cybercriminals could take over a third-party platform that some people use to access Instagram, compromising all the associated account details in the process.
This is possible through Instagram integrations, as well as linked platforms such as Facebook.
How Do People Get Hacked on Instagram Due to Password Problems?
If you use the same password for another account and it's part of a data leak, cybercriminals could hack into your account using this same password.
Alternatively, if your password is too easy for hackers to guess, your account is at risk.
How Does Instagram Get Hacked Through In-App Scams?
Some hackers trick people into giving up their account details by orchestrating scams. One recent approach making the rounds involves people receiving Instagram messages saying their friends made them gifts. However, the associated link sends people to an external site that steals their passwords.
Cybercriminals also target Instagram and Facebook users with Cash App scams. They promise to send people $850, but experts say falling for this offer could lead to identity theft.
It’s not always skilled hackers breaking into Instagram accounts. How can someone hack your Instagram account if they aren’t a cybersecurity expert? One of the main ways is through purposeful or unintentional device access combined with automatic logins.
Instagram can store information for multiple accounts. However, you can only access them one at a time. Maybe you often let your housemate or a significant other use your phone to access Instagram themselves. If you later have a falling-out, and they know your password, that party could hack your Instagram.
If you later have a falling-out, and they know your password, that party could hack your Instagram.
A similar situation could happen if someone steals your phone, you lose it, or an unauthorized person gets access to your email. These outcomes become problematic if you have the two-factor authentication (2FA) feature activated for Instagram.
Having access to your email or phone could provide a hacker with the 2FA verification code they need to log in to your account without knowing the password. They could then access the account and change the password to something only they know.
The reason for the hack and the methodology used determines what happens after an account hack. In cases where the hacker is someone close to you, you may not notice any changes to your account if the person solely did it to spy on you.
In cases where professional cybercriminals have hacked Instagram profiles, there may be significant changes to the account and its accessibility. These users will likely find themselves locked out of the account. If someone else controls it, they can change the passwords to keep you locked out of the account.
These users will likely find themselves locked out of the account. If someone else controls it, they can change the passwords to keep you locked out of the account.
How Do People’s Instagram Accounts Get Hacked When They Are Influencers?
Cybercriminals often take a particular interest in hacking the accounts of influencers. When people have tens of thousands of followers or more, malicious parties could have a broader reach by compromising those accounts.
Sometimes, internet criminals use special software that launches a brute-force attack against those accounts. Regardless of how the takeover happens, some Instagram influencers reported on BuzzFeed News that contacting the site itself doesn’t often help. Desperation may make them resort to hiring white-hat hackers to resolve the problem.
In some cases, hackers demand a ransom for the account. In other cases, they may change significant details on the account, such as images. Hackers often sell off accounts with many followers or hijack the accounts of specific well-known people for profit.
Instagram’s security features get progressively more advanced in response to hacked user accounts. These changes make it more difficult for hackers to access accounts and easier for affected users to regain access.
If you believe someone has hacked your account, the first step is to report it to Instagram. They will record all the details, examine the case, and assist in getting the service restored as quickly as possible.
The hacker may have also logged you out of your account and changed the password. Select Get Help Logging In (on an Android device) or Forgotten Password? (on an Apple product). You’ll then need to verify your account by entering one of the identity confirmation details, such as a phone number.
If you do not have any of the requested information, choose Need More Help? and follow the on-screen instructions. This is the first step to contacting Instagram’s support team, but you must enter a security code to go further. It goes to your email address or phone number.
It goes to your email address or phone number.
Verifying Your Identity
The methods of confirming your identity vary depending on if the Instagram account in question contains pictures of you. If it does not, Instagram’s support team sends an automated email requesting that you provide the following information.
- The email address or phone number used when creating the account
- The type of device used during the account’s creation (such as an Android phone or an iPad)
If the compromised account has photos of you, Instagram uses a video-selfie method for verification. It requires turning your head in different directions while creating the clip. The Instagram team reviews the video within two business days.
Passing this test results in getting an email from Instagram containing a link to reset your password. Conversely, you may receive an email requiring the submission of another selfie video.
Additionally, Instagram's Recently Deleted folder is a helpful feature that restores deleted posts, stories, and reels. Whenever you remove your Instagram content, they first go and stay in the folder for 30 days before being permanently erased.
Whenever you remove your Instagram content, they first go and stay in the folder for 30 days before being permanently erased.
If you suspect an account hack but can still log in, take the following steps to secure your account:
- Change your password. Passwords should be unique to Instagram and strong to deter hackers from guessing the correct one.
- Enable two-factor authentication. This requires an extra code when you’re attempting to log into your account; cybercriminals would need access to that device or service to sign in too.
- Confirm that your contact details (email address and phone number) linked to your account are correct. If you get an email regarding unknown changes to your Instagram account, verify that it's real by trying to log in on a different window. Otherwise, it could be a phishing scam. Contact Instagram separately, without clicking on any suspicious links.
- Check which linked accounts and third-party apps have access to your Instagram.
 You can do this in the Security section of your Instagram account, which shows your log inactivity. Remove access from suspicious accounts and apps. You can see the geographic locations of where you’re logged in and which devices are being used. If there are any that you do not recognize, you can log out of them.
You can do this in the Security section of your Instagram account, which shows your log inactivity. Remove access from suspicious accounts and apps. You can see the geographic locations of where you’re logged in and which devices are being used. If there are any that you do not recognize, you can log out of them.
There are steps you can take to prevent hackers from gaining access to your account.
These steps are simple to take and are more than worth your while: a hacked account can wreak havoc on your privacy and security. Nip it in the bud by taking simple precautions.
6 Instagram Scams and How to Avoid Them
Social media is a world of endless opportunity, especially Instagram. From connecting with loved ones to building business empires from the safety of your home, your imagination is the limit. Unfortunately, there is also an increasing number of people who are looking to take advantage of it in the wrong ways.
These days, it’s pretty common to come across shady accounts on Instagram offering jobs, followers, supposedly free stuff, and more. Here’s how to spot some of the most common Instagram scams happening today.
Here’s how to spot some of the most common Instagram scams happening today.
1. Companies Offering Cheap Followers
When it comes to Instagram, the number of followers you have matters. In many ways, a larger following can give the illusion of credibility, trust, and influence. In fact, it’s one of the most basic things that companies check when searching for people to choose as influencers.
However, it’s also true that the quality of followers is just as important as the quantity. After Instagram transitioned to an algorithm-based feed instead of chronological order, most followers won’t even see your content if Instagram doesn’t deem it engaging enough.
Unfortunately, there are several companies still seeking to take advantage of users who want the vanity metrics of a large following. Promising cheap followers, these companies will ask you for payment information such as your credit card details and Instagram log in information to proceed. With these, they can gain access to your account and steal your identity.
2. Job Scams
Job applications are the perfect guise for threat actors to get important, Personally Identifiable Information (PII) about you in a quick manner. This is because it’s actually quite common for real recruiters to ask for your CV or resume, which may contain things like your home address, school affiliations, and contact details.
Job scams are some of the best ways to gather information for identity theft. A key way to identify job scams is by checking on official company pages and seeing if the positions listed are the same.
Related: Don't Get Fooled by Employment Scams: How They Work
Aside from this, it's also good to check if there is an official company portal wherein you can send your information. Instead of a personal email address from a recruiter, an official company email or website is a safer way of applying for a new role.
3. Rip-Off Courses
There has been an exponential rise in fake gurus selling courses on things that they have no business talking about. With no credentials to back them up, these courses often target people who are looking to shift careers, break into a new industry, or earn additional money.
With no credentials to back them up, these courses often target people who are looking to shift careers, break into a new industry, or earn additional money.
While not all courses are scams, there's definitely a growing number of courses that just aren't worth your money. Rip-off classes can be identified through checking online forums where people can share their experiences. In addition, doing a quick search of the background of those making the courses on LinkedIn or Google can reveal if they are credible or not.
For example, if a person is selling a course to grow your Instagram following while they have a small following of their own, you can already spot that they're all talk and no walk.
4. Romance Scams
While love scams have been around since the dawn of the internet, Instagram takes romance scams to the next level. Acting like a digital catalog, many scammers use Instagram to attract unsuspecting people who are craving human connection.
Often, romance scam artists also participate in identity theft. Using photos of attractive men or women, these scammers tend to craft a fake, but believable persona and nurture a potential victim with visions of love.
Using photos of attractive men or women, these scammers tend to craft a fake, but believable persona and nurture a potential victim with visions of love.
After a victim is comfortable, scam artists tend to request money. In most cases, they will ask you to send it to accounts that do not require identity verification to withdraw, such as Cash App. First, it is often small, negligible amounts. Then, they will slowly ask for increasingly larger sums of cash.
5. Brand Ambassador Scams
As many people seek to make careers out of social media and so become influencers, brands have taken a nefarious approach to taking advantage of them.
Through selling them the idea of being ambassadors, brands convince aspiring influencers to pay for shipping on supposedly free products. However, the cost of shipping is often absurdly high because it actually factors in the cost of the actual item.
Related: Sophisticated Social Media Scams You Need to Avoid
When checking for legitimate influencer partnerships, one of the key signs is when they do not ask you to pay for anything to receive their product. In addition, real influencer partnerships are also paid, whether up front or through affiliate codes that your followers can issue at checkout.
In addition, real influencer partnerships are also paid, whether up front or through affiliate codes that your followers can issue at checkout.
6. Fake Giveaways
Growing your Instagram following in a sea of competitors can be tough. For this reason, many brands opt to have various campaigns to increase their follower count. One of the common ways that they do this is through giveaways.
Unfortunately, many scammers have also realized how these giveaways can be used to gather information from unsuspecting people. In some cases, scammers attempt to copy the profile of a legitimate brand and host a fake giveaway.
Once they receive enough responses, the scammers then select the "winners" of the scam. On the guise of sending their prize, scammers will then ask for information like your name, contact details, and other information that can be used to steal your identity.
Keep Instagram Safe and Enjoyable
To avoid being scammed on Instagram, you need to be mindful of the people you interact with online, even those who you may know in real life. Sometimes, scammers are closer to us than we think.
Sometimes, scammers are closer to us than we think.
When it comes to avoiding Instagram scams, common sense is not always so common. Before sending any PII, it's best to double-check official channels from companies or individuals. Make sure you gather enough proof before you engage with anyone.
Scammers are working smarter and doing their best to appear legitimate in their attempts to waste your time, steal your money, or take your online identity. However, you don't have to fall for it.
How to protect your Instagram account from hacking
Hello everyone. I am the marketing manager for Picalytics Instagram analytics and I decided to write an article for marketers and business owners, because in my work I encounter banal non-compliance with safety precautions several times a week.
Let's say you spent time and money promoting your account, rebuilt your direct sales process, and got loyal customers. In the morning, you open Instagram to launch a promotion and. .. you can't log in to your account. In this article, you will learn about the “prevention” of hacking and what to do if your account is stolen.
.. you can't log in to your account. In this article, you will learn about the “prevention” of hacking and what to do if your account is stolen.
As usual, your account is hijacked
You can register on Instagram through mail, Facebook or by phone number. With access to your smartphone (and therefore Facebook, mail), it is easy to access all the services associated with them. Therefore, they steal accounts through these "entry points".
First of all, check the relevance and security of the services linked to your account. Then make sure that you have not specified the mail associated with the account in the contact methods.
And one more thing: you don't store accesses in Google Docs or notes on your smartphone, do you?
In addition to mail and phone theft, the most common hacking option is phishing (gaining access) to the account directly:
1. Cloned phishing
This is the usual copying of mail and official letters from Instagram. In this case, the attacker sends a letter that looks as close as possible to a letter from Instagram - both in interface design and in the sender's address.
In this case, the attacker sends a letter that looks as close as possible to a letter from Instagram - both in interface design and in the sender's address.
The screenshots below show examples of emails from Instagram.
The role address can be different - you need to pay attention to the domain name (the part after @).
This is how a letter from scammers looks like.
Cloned phishing is designed for inattentive people and novice account administrators. Therefore, look both ways when you follow unknown links.
Business stories and useful tips
2. Access through third-party applications and services
As a rule, these are photo editors, promotion automation, auto-posting, direct web versions and so on.
Phishing apps are not verified by Google Play and AppStore. Such services, when registering, request access to an account or imitate authorization through Instagram.
Do not be afraid of authorization in third-party services: some options are not possible without access to the account.
Remember: authorization through Instagram takes place in a new tab on the official website of Instagram.
To check the list of applications that have access to your account, go to the application settings and click "Access Management". You have logged in to these applications through Instagram and can revoke access to your account from them.
If you have lost your smartphone or tablet with access to your account, change your password from Instagram and the service linked to it (mail or Facebook) as soon as possible.
In most cases, small Instagram accounts are hacked to be sold to third parties. On average, such "dead souls" cost $0.3-0.5.
In our experience with Instagram tech support, there is no relationship between account size (or ad budget) and response speed.
For example, after a major advertising campaign, we saw a duplicate account using our trademark (and this is a serious violation) and wrote to technical support. There has been no response from Instagram for three weeks. But there are exceptions to the rule.
How to get your account back after being hacked
Try to react quickly. If you still can log in to your account, change the password for the linked services (mail and / or Facebook). Then enable two-factor authentication.
If you can't log in to your account over , try resetting your password via mail, Facebook or phone number. Upon successful login, enable two-factor authentication.
If you do not receive notifications from Instagram when resetting your password and cannot log in via Facebook (if it was connected), then your account was linked to another mail, and also unlinked from Facebook and a phone number (if if they were connected).
In this case, we recommend that you send a request to Instagram support:
- Click "Forgot Password".

- Open the account login page in the Instagram mobile app;
- Enter your nickname, email and phone number associated with your account.
Instagram can substitute the number of the SIM card currently in the phone in the phone number field - this is not always the number associated with the account.
By the way, we never received a magic link via SMS, despite the fact that the accounts were linked to a phone number.
If you did not receive a letter to your address or your nickname was changed, repeat the previous paragraph by entering both nickname and mail.
If you can't find your account using your old nickname anymore, look in your inbox for emails from Instagram. Didn't receive any information about the account change? Ask a friend to find out your current nickname through the history of correspondence in direct or from comments previously left on your behalf.
If you succeeded in logging in, change the password for your account and associated services (mail and/or Facebook). Then enable two-factor authentication.
Then enable two-factor authentication.
What should I do if the login fails?
1. On the password recovery page, click "Need more help?" and enter all the requested information. Check the box next to "My account has been hacked". Send a request and wait for a response to the specified mail.
2. If you do not receive a response within a few days, repeat the request by checking the box next to "I forgot the mail associated with my account."
What to do with a nickname after being hacked
If you managed to regain access to your account, you can change your nickname to any free one. Including your old nickname, if it has been changed.
In some cases, the condition for restoring access to the account by Instagram may be a change of nickname. In this situation, we recommend using a nickname that is as close as possible to the previous one: for example, add a dot or underscore.
If your account has been deleted, you can create a new account with the same email address, but you may not be able to use your old username.
What not to do
- Offer scammers a reward or agree to buy the account back. Most likely, the account will not be returned or you will be asked to pay extra (and pay a little more).
- Show high activity immediately after the restoration of access to the account.
Conclusion
Hacking an account without the help of its owner is a difficult task. Don't let a moment of inattention deprive you of months of work on your account.
How to insure your account:
- Check the security and relevance of Instagram-related services.
- Change the password to a secure one. Use unique alphanumeric combinations with different case. Change your password regularly - at least once every 2-3 months.
- Enable two-factor authentication.
- Do not log in from public Wi-Fi and do not save the password in the browser.
- Do not indicate in the header of the account the mail or phone number by which the account was registered.
- In case of suspicion, immediately change the password for the account and all services associated with it.
Have you heard about account recovery stories with happy endings? Tell us about it in the comments: we will create a chat for support and exchange of experience.
The opinion of the authors of the guest post may not coincide with the position of the editors and specialists of the Netpeak agency.
Artem Borodatyuk about business and how it changes the world
Andrey Chumachenko about marketing, self-management and agency
Follow
Follow
Subscribe to Netpeak founders' Telegram channels
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data breach and wildcard attack
A third-party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on.
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password.
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It is possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
Now someone has discovered your oversight and logged into your account.
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings. This will reset the access tokens.
- Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them.
 If they managed to do this, change it back to yours.
If they managed to do this, change it back to yours. - Set a new password that is strong and one you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress.
Tips
Air sellers in online stores
We tell how scammers deceive users of a well-known marketplace using a fake payment page for goods.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site.

- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site.