How do i hack a whatsapp account
9 Ways Your WhatsApp Messages Can Be Hacked
WhatsApp is a popular and easy to use messaging app. It has some security features, like the use of end-to-end encryption, which tries to keep your messages private. However, as good as these security measures are, WhatsApp still isn't immune to hacks, which can end up compromising the privacy of your messages and contacts.
Don't take our word for it: just go and see how many "How to hack WhatsApp" guides you'll find on the internet if you're persistent enough.
As knowing is half the battle, if we are simply aware of vulnerabilities, we can then take concrete steps to avoid comprising ourselves. To that end, here are a few ways that WhatsApp can be hacked.
1. Remote Code Execution via GIF
In October 2019, security researcher Awakened revealed a vulnerability in WhatsApp that let hackers take control of the app using a GIF image. The hack works by taking advantage of the way WhatsApp processes images when the user opens the Gallery view to send a media file.
When this happens, the app parses the GIF to show a preview of the file. GIF files are special because they have multiple encoded frames. This means that code can be hidden within the image.
If a hacker were to send a malicious GIF to a user, they could compromise the user's entire chat history. The hackers would be able to see who the user had been messaging and what they had been saying. They could also see users' files, photos, and videos sent through WhatsApp.
The vulnerability affected versions of WhatsApp up to 2.19.230 on Android 8.1 and 9. Fortunately, Awakened disclosed the vulnerability responsibly and Facebook, which owns WhatsApp, patched the issue. To keep yourself safe from this problem and similar, you should always keep WhatsApp updated.
2. The Pegasus Voice Call Attack
Another WhatsApp vulnerability discovered in early 2019 was the Pegasus voice call hack.
This scary attack allowed hackers to access a device simply by placing a WhatsApp voice call to their target. Even if the target didn't answer the call, the attack could still be effective. And the target may not even be aware that malware has been installed on their device.
Even if the target didn't answer the call, the attack could still be effective. And the target may not even be aware that malware has been installed on their device.
This worked through a method known as buffer overflow. This is where an attack deliberately puts in so much code into a small buffer that it "overflows" and writes code into a location it shouldn't be able to access. When the hacker can run code in a location that should be secure, they can take malicious steps.
This attack installed an older and well-known piece of spyware called Pegasus. This allowed hackers to collect data on phone calls, messages, photos, and video. It even let them activate devices' cameras and microphones to take recordings.
This vulnerability is applicable on Android, iOS, Windows 10 Mobile, and Tizen devices. It was used by the Israeli firm, NSO Group, for example, which has been accused of spying on Amnesty International staff and other human rights activists. After news of the hack broke, WhatsApp was updated to protect it from this attack.
If you are running WhatsApp version 2.19.134 or earlier on Android or version 2.19.51 or earlier on iOS, then you need to update your app immediately.
Another way you're vulnerable to getting your WhatsApp hacked is through socially engineered attacks, which exploit human psychology to steal information or spread misinformation.
Security firm, Check Point Research, revealed one example of this attack, which they named FakesApp. This allowed people to misuse the quote feature in group chat and to alter the text of another person's reply. Essentially, hackers could plant fake statements that appear to be from other legitimate users.
The researchers could do this by decrypting WhatsApp communications. This allowed them to see data sent between the mobile and the web versions of WhatsApp.
And from here, they could change values in group chats. Then they could impersonate other people, sending messages which appeared to be from them. They could also change the text of replies.
This could be used in worrying ways to spread scams or fake news. Even though the vulnerability was disclosed in 2018, it had still not been patched by the time the researchers spoke at the Black Hat conference in Las Vegas in 2019, according to ZNet. It therefore becomes critical that you learn how to recognize WhatsApp scams and keep reminding yourself of these red flags periodically.
4. Media File Jacking
Media File Jacking affects both WhatsApp and Telegram. This attack takes advantage of the way apps receive media files like photos or videos and write those files to a device's external storage.
The attack starts by installing malware hidden inside an apparently harmless app. This can then monitor incoming files for Telegram or WhatsApp. When a new file comes in, the malware may swap out the real file for a fake one.
Symantec, the company that discovered the issue, suggested it could be used to scam people or to spread fake news.
There is a quick fix for this issue, though. Using WhatsApp, you should look in Settings and go to Chat Settings. Then find the Save to Gallery option and make sure it is set to Off. This will protect you from this vulnerability. However, a true fix for the issue will require app developers to entirely change the way that apps handle media files in the future.
Using WhatsApp, you should look in Settings and go to Chat Settings. Then find the Save to Gallery option and make sure it is set to Off. This will protect you from this vulnerability. However, a true fix for the issue will require app developers to entirely change the way that apps handle media files in the future.
5. Facebook Could Spy on WhatsApp Chats
In an official blog post, WhatsApp asserted that due to its end-to-end encryption, it is impossible for Facebook to read WhatsApp content:
"When you and the people you message are using the latest version of WhatsApp, your messages are encrypted by default, which means you're the only people who can read them. Even as we coordinate more with Facebook in the months ahead, your encrypted messages stay private and no one else can read them. Not WhatsApp, not Facebook, nor anyone else."
However, according to developer Gregorio Zanon, this is not strictly true. The fact that WhatsApp uses end-to-end encryption does not mean all messages are private. On an operating system like iOS 8 and above, apps can access files in a "shared container."
The fact that WhatsApp uses end-to-end encryption does not mean all messages are private. On an operating system like iOS 8 and above, apps can access files in a "shared container."
Both the Facebook and WhatsApp apps use the same shared container on devices. And while chats are encrypted when they are sent, they are not necessarily encrypted on the originating device. This means the Facebook app could potentially copy information from WhatsApp.
There is no evidence that Facebook has used shared containers to view private WhatsApp messages. But the potential is there. Even with end-to-end encryption, your messages may not be private from the all-capturing net of Facebook.
6. Paid Third-Party Apps
You'd be surprised how many paid legal apps have sprung up in the market, which solely exist for hacking into secure systems. It's super easy to carry out covert WhatsApp hacks through this method.
In fact, it isn't unheard of for big corporations to work hand-in-hand with oppressive regimes to target activists and journalists; or by cybercriminals, intent on getting your personal information.
Apps like Spyzie and mSPY can easily hack into your WhatsApp account for stealing your private data. All you need to do is purchase the app, install it, and activate it on the target phone. You can then simply sit back and connect to your app dashboard from the web browser, and snoop in on private WhatsApp data like messages, contacts, status, etc. But obviously, we advise against anyone actually doing this!
7. Fake WhatsApp Clones
Using fake website clones to install malware is an old hacking strategy still implemented by cyber criminals all over the world. These clone sites are known as malicious websites.
The hacking tactic has now also been adopted for breaking into Android systems. To carry out a WhatsApp hack on your account, an attacker will first try to install a clone of WhatsApp, which might look strikingly similar to the original app.
Take the case of the WhatsApp Pink scam, for instance. A clone of the original WhatsApp, it claims to change the standard green WhatsApp background to pink.
Here's how it works: an unsuspecting user receives a link to download the WhatsApp Pink app for changing the background color of their app. And even though it really does change the background color of your app to pink, as soon as you install the app, it will start collecting data not just from your WhatsApp but also from everything else stored on your phone.
8. WhatsApp Web
WhatsApp Web is a neat tool for someone who spends most of their day on a PC. It provides the ease of accessibility to WhatsApp users, so they won't have to pick up their phone again and again for messaging. The big screen and keyboard provides an overall better user experience too.
Here's the caveat though. As handy as the web version is, it can be easily used to hack into your WhatsApp chats. This danger arises when you're using the WhatsApp Web on someone else's computer.
So if the owner of the computer has selected the "keep me signed in" box during login, then your WhatsApp account will stay signed-in even after you've closed the browser.
The computer owner can then access your information without much difficulty.
You can avoid this by making sure that you log out from WhatsApp Web before you leave.
But as they say, prevention is better than cure. The best approach is to avoid using anything other than your personal computer for the web version of WhatsApp altogether.
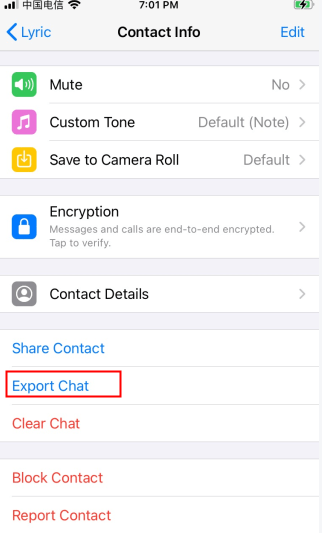
9. Exporting Your Chats
This isn't the traditional method you'd find on the "how to hack someone's WhatsApp" guides. While some of the other methods are really elaborate, and some just capitalize on blank spots in the human psyche, this one simply requires physical access to your smartphone.
And no, the hacker doesn't need a lot of time with your phone, either; just a few seconds is enough. This gives them enough time to export your messages to a location they can later access. It could be anything: an email account, cloud storage, or even a messaging app.
Once a hacker has access to your phone, all they have to do is move to a specific chat, click on the Export chat option and select the location they'd like to move your message history to.
The solution? The ironclad way to protect yourself is to keep your phone away from unfamiliar hands at all times. Furthermore, you have the option to enable fingerprint lock for your WhatsApp. Here's how:
- Head to Accounts > Privacy > Fingerprint lock.
- Toggle the Unlock with fingerprint option on, and set the lock activation to Immediately.
Now, every time your WhatsApp is picked up after inactivity, your fingerprints will be required to launch the app.
Stay Aware of Security Issues in WhatsApp
These are just a few examples of how your WhatsApp can be hacked. While WhatsApp has patched some of these issues since their disclosure, some weak spots persist, so it's important to stay vigilant. To learn more about whether WhatsApp is safe, you need to brush up your knowledge of WhatsApp security threats. Always keep yourself updated!
Hackers steal WhatsApp accounts using call forwarding trick
There’s a trick that allows attackers to hijack a victim’s WhatsApp account and gain access to personal messages and contact list.
The method relies on the mobile carriers’ automated service to forward calls to a different phone number, and WhatsApp’s option to send a one-time password (OTP) verification code via voice call.
The MMI code trick
Rahul Sasi, the founder and CEO of digital risk protection company CloudSEK, posted some details about the method saying that it is used to hack WhatsApp account.
BleepingComputer tested and found that the method works, albeit with some caveats that a sufficiently skilled attacker could overcome.
It takes just a few minutes for the attacker to take over the WhatsApp account of a victim, but they need to know the target’s phone number and be prepared do some social engineering.
Sasi says that an attacker first needs to convince the victim to make a call to a number that starts with a Man Machine Interface (MMI) code that the mobile carrier set up to enable call forwarding.
Depending on the carrier, a different MMI code can forward all calls to a terminal to a different number or just when the line is busy or there is no reception.
These codes start with a star (*) or a hash (#) symbol. They are easily found and from the research we did, all major mobile network operators support them.
“First, you receive a call from the attacker who will convince you to make a call to the following number **67* or *405*. Within a few minutes, your WhatsApp would be logged out, and the attackers would get complete control of your account” - Rahul Sasi
The researcher explains that the 10 digit number belongs to the attacker and the MMI code in front of it tells the mobile carrier to forward all calls to the phone number specified after it when the victim’s line is busy.
Once they tricked the victim into forwarding calls to their number, the attacker starts the the WhatsApp registration process on their device, choosing the option to receive the OTP via voice call.
WhatsApp options for receiving one-time password, source: BleepingComputerAfter they get the OTP code, the attacker can register the victim’s WhatsApp account on their device and enable two-factor authentication (2FA), which prevents legitimate owners from regaining access.
Some caveats
Although the method seems simple, getting it to work requires a little more effort, as BleepingComputer found during testing.
First off, the attacker needs to make sure that they use an MMI code that forwards all calls, regardless of the victim device’s state (unconditionally). For example, if the MMI only forwards calls when a line is busy, call waiting may cause the hijack to fail.
During testing, BleepingComputer noticed that the target device also received text messages informing that WhatsApp is being registered on another device.
Users may miss this warning if the attacker also turns to social engineering and engages the target in a phone call just long enough to receive the WhatsApp OTP code over voice.
BleepingComputer · OTP message from WhatsApp
If call forwarding has already been activated on the victim device, the attacker must use a different phone number than the one used for the redirection - a small inconvenience that might require more social engineering.
The most clear clue of suspicious activity for the target user occurs after the mobile operators turn on call forwarding for their device, since activation comes with a warning overlayed on the screen that doesn't go away until the user confirms it.
Mobile carriers warn users when call forwarding becomes active, source: BleepingComputerEven with this highly visible warning, threat actors still have a good chance of success because most users are not familiar with the MMI codes or the mobile phone settings that disable call forwarding.
Despite these obstacles, malicious actors with good social engineering skills can devise a scenario that allows them to keep the victim busy on the phone until they get the OTP code for registering the victim WhatsApp account on their device.
BleepingComputer has tested this method using mobile services from Verizon and Vodafone and concluded that an attacker with a plausible scenario is likely to hijack WhatsApp accounts.
Sasi's post refers to Airtel and Jio mobile carriers, each with more than 400 million customers as of December 2020, according to public data.
Protecting against this type attack is as easy as turning on two-factor authentication protection in WhatsApp. This feature prevents malicious actors from getting control of the account by requiring a PIN whenever you register a phone with the messaging app.
Any WhatsApp user can have their account taken away. You don't need to be a hacker to do this
software Soft Safety User Internet Internet software Technology
|
Share
There is a flaw in WhatsApp that allows attackers with zero hacking and programming skills to permanently block any user's account. They only need to know their phone number and nothing else, and there is no way to protect themselves from potential blocking. WhatsApp developers are in no hurry to fix the problem.
They only need to know their phone number and nothing else, and there is no way to protect themselves from potential blocking. WhatsApp developers are in no hurry to fix the problem.
New bug in WhatsApp
Each WhatsApp user can lose their profile at any second with a minimal chance of recovery. According to Forbes, it is simply impossible to protect against this, and the attacker will not even need to hack the gadget - he just needs to know the user's phone number, after which he can initiate the procedure for blocking him without the possibility of re-authorization in the system.
The ability to deprive anyone of using WhatsApp is a consequence of a giant vulnerability discovered in the messenger by information security specialists Luis Carpintero and Ernesto Pereña (Ernesto Canales Pereña). They notified the developers of WhatsApp about their discovery, but they have not yet released a patch that fixes the breach, thereby leaving 2 billion users at risk of losing their account.
WhatsApp does nothing to protect users from blocking their profile
WhatsApp is the most popular instant messenger in the world. According to Statista.com, in terms of the number of monthly active users as of January 2021, with its more than 2 billion, it was ahead of Facebook Messenger (1.3 billion) and Chinese WeChat (1.21 billion), along with QQ (617 million). WhatsApp has been owned by Facebook since February 2014.
How vulnerability works
Vulnerability in WhatsApp makes it possible to completely block the victim's account and is carried out in two very simple steps, in each of which the perpetrator does not even need hacking or social engineering skills - he will not contact the profile owner at all.
WhatsApp standard authorization window
At the first stage, an attacker simply needs to install WhatsApp on a smartphone and try to log in using the desired phone number. The messenger will send him an SMS with a confirmation code, and here there is a calculation that the owner of the number will ignore them. After several such attempts, the application on the attacker's device will report too frequent authorization attempts and allow the next one only after 12 hours. At the same time, WhatsApp on the victim’s device will continue to work as before.
After several such attempts, the application on the attacker's device will report too frequent authorization attempts and allow the next one only after 12 hours. At the same time, WhatsApp on the victim’s device will continue to work as before.
Notification that authorization was not possible due to an excessive number of attempts
In the second step, the attacker registers a new email address and writes a letter to WhatsApp technical support saying that his account was lost or stolen. He asks to turn it off and indicates the number of the victim. WhatsApp can send an automatic email asking you to write the number again, and the attacker will do it.
Letter to WhatsApp technical support requesting blocking
Next, WhatsApp, without making sure that the real owner of the account wrote to technical support, initiates the blocking procedure. After about an hour, the messenger will suddenly stop working on the victim's device - she will see a message that her number is no longer registered in the system. “It could be because you registered it on another phone. If you haven't done so, verify your phone number to log into your account again," the notification will say.
“It could be because you registered it on another phone. If you haven't done so, verify your phone number to log into your account again," the notification will say.
WhatsApp response with confirmation of the request
All of this will work even if the user has enabled two-factor authentication. An attempt to request a new code will fail - WhatsApp will allow you to do this only after 12 hours.
Bonus stage and full blocking
If the attacker decides to stop at the second stage, then everything will end up with just the inability of the user to connect to WhatsApp with his number for several hours. After a maximum of 12 hours, the user will be able to regain control over his account and continue working in the messenger exactly until someone wants to repeat the "trick" with the blocking.
But in fact there is an additional, third stage, leading to a complete blocking of the account.
This stage can actually become the second - the attacker does not have to send a letter to WhatsApp support, he can just wait 12 hours, and then again make several attempts to register someone else's number on his phone. After the third 12-hour blocking, WhatsApp will break, and instead of a timer counting down the time until the next authorization attempt, it will show “-1 second”, moreover, constantly. This is a malfunction in the messenger, which cannot be bypassed.
After the third 12-hour blocking, WhatsApp will break, and instead of a timer counting down the time until the next authorization attempt, it will show “-1 second”, moreover, constantly. This is a malfunction in the messenger, which cannot be bypassed.
A stuck timer on the phones of the victim (left) and the attacker
This picture will be observed both on the hacker's device and on the victim's smartphone, and as a result, no one else will be able to log in to the messenger using this phone number. The only thing left is to try to contact WhatsApp technical support and look for ways to solve the problem.
WhatsApp does not solve the problem
A Forbes article shedding light on a new WhatsApp issue was published on April 10, 2021. By April 13, 2021, the developers have not released an update to fix it and have not set a release date for it.
Andrey Rybintsev, Avito: In two years, security on the platform has grown 20 times
Safety
Instead, they are preparing to implement a new privacy policy, according to which the messenger will automatically transfer huge amounts of personal data of users to Facebook for better ad targeting.
This policy was intended to be implemented by WhatsApp on February 8, 2021, but was forced to temporarily abandon this idea due to a flurry of criticism. The new date for its entry into force is May 15, 2021, and all those who are not going to agree with it are in for a very serious punishment.
In February 2021, CNews wrote that those who disagree with the new WhatsApp privacy policy will no longer be able to send and receive text messages. Developers will leave them only voice calls. Moreover, the profiles of those users who stop using WhatsApp and switch to other messengers are guaranteed to be completely deleted.
WhatsApp other issues
WhatsApp is known not only for the fact that it is used by billions of people, but also for the fact that if it appreciates its users, it is far from always. So, for example, in June 2020, it became known that some phone numbers linked to user profiles in WhatsApp had been in the public domain for a long time and even got into Google search results. In total, with the help of Google, it was possible to find up to the number of about 300 thousand users of the messenger, and this problem was of a global nature.
In total, with the help of Google, it was possible to find up to the number of about 300 thousand users of the messenger, and this problem was of a global nature.
WhatsApp is still in first place in terms of the number of users
In November 2019, CNews reported that WhatsApp users were automatically permanently banned for participating in harmless group chats. It turned out to be possible to fall under sanctions for changing the name of the chat to something that would seem to the moderators of the service as something sinister, illegal or malicious.
Which digital products can be purchased with a 50% discount with government support
IT industry support
At the same time, WhatsApp was in no hurry to fix this failure. The employees of the messenger responded to all requests from the victims about the reasons for blocking that the users themselves violated the rules of the service, and the fault in blocking lies solely with them. As a result, people had to either change their phone number to register a new profile, or go to other services - Telegram, Viber, Signal and others.
As a result, people had to either change their phone number to register a new profile, or go to other services - Telegram, Viber, Signal and others.
- Which smartphone display is better: AMOLED or IPS?
Elyas Kasmi
Experts told about the most popular methods of hacking WhatsApp
Cases of hacking WhatsApp accounts on behalf of scammers posing as friends and relatives of the victim have become more frequent on the network - they ingratiate themselves and ask to give them a secret code from an SMS message, warns "Bi- BBC. As information security experts told Gazeta.Ru, such an attack is far from the only way to deceive users of the popular messenger.
Scammers are stealing WhatsApp user accounts by forcing victims to send them the security code they need to access the service, according to BBC .
This scheme works as follows: first, the user receives an SMS message with a six-digit WhatsApp code that he did not request. This should already alert the smartphone owner if he did not try to restore access to his account.
This should already alert the smartphone owner if he did not try to restore access to his account.
The user then receives a message from a number that belongs to a friend or relative. The victim does not know that the sender has already been hacked, so he does not feel a catch. A fake friend asks to share a six-digit number from an SMS, allegedly his account is blocked and in order to regain access he needs a confirmation code, which he asked to be sent to the victim's number.
In fact, the user sends the attacker a code that is needed to access his own WhatsApp account - in fact, he independently and voluntarily parted with it.
Victims of this scam interviewed by the BBC expressed their disappointment at having fallen for such a 'simple' scam.
“I received a message from my friend Michelle who said she couldn't sign in. She said she accidentally entered my phone number to send the verification code, and I took a screenshot of the code and sent it to her. I think I fell for it because everyone knows how hard it can be with technology sometimes, and I really wanted to help. I realized what really happened only a day later, ”said an interlocutor of the agency named Charlie. According to her, after this incident, she stopped using WhatsApp and switched to iMessage.
I think I fell for it because everyone knows how hard it can be with technology sometimes, and I really wanted to help. I realized what really happened only a day later, ”said an interlocutor of the agency named Charlie. According to her, after this incident, she stopped using WhatsApp and switched to iMessage.
Fraud schemes, which are also called scams, in WhatsApp vary greatly from country to country and depend on what is happening in the world, Luis Corrons, Avast cybersecurity evangelist, told Gazeta.ru. As a rule, attackers use current events for their own purposes and develop special schemes for this, for example, dedicated to Black Friday or related to the pandemic.
“In one of the common WhatsApp account cloning scams, the victim is invited to a party, meeting or event.
Hackers send out messages in the victim's native language, and sometimes even mention the name of some person familiar to the victim.
In the message, they write that in order to confirm their presence at the event, it is necessary to write a verification code sent by SMS. In fact, this code is a verification from WhatsApp, necessary for cloning an account, ”Corrons explained.
In fact, this code is a verification from WhatsApp, necessary for cloning an account, ”Corrons explained.
Often, attackers use WhatsApp when they want to transfer communication with the victim from official sites to private chats, for example, from services for placing private ads for sale or joint trips, as well as to hack accounts in various social networks. In these cases, the schemes used are quite standard: they can send a phishing link, try to get a one-time code from SMS, or convince them to perform some other action, Dmitry Galov, cybersecurity expert at Kaspersky Lab, told Gazeta.Ru.
“Information about fake contests or promotions can also be distributed through messengers. For example, after the presentation of the iPhone 12, fraudulent mailings appeared allegedly that you can get a new smartphone for free: just forward this message to 20 contacts or 5 groups, and then follow the link to select the color of the phone and enter your data. Depending on what was asked to enter on the phishing site, the attackers could take possession of personal or financial data or force the victim to transfer money under various pretexts,” the expert noted.
ESET researcher Amer Owaida told Gazeta.Ru that many WhatsApp scams target teenagers, as middle and high school students are willing to share what is happening in life on social networks, and it is not difficult for professional scammers to collect information about the victim, before sending a private message to the messenger.
“The most common scam theme is offering luxury items at low prices. As a rule, “the last pair of limited edition sneakers in your size with a 80% discount” must be purchased in a limited time and transferred money for the purchase or delivery as soon as possible. In this case, the naivete and belief in miracles inherent in teenagers, as well as the desire to stand out among their peers, play into the hands of scammers. Another scam targeting teenagers is the scholarship scam. Attackers select victims among future applicants and send messages on behalf of a university or college promising favorable study conditions. For example, for a scholarship application, the recipient is asked to pay a "registration fee" or "data processing fee".

.png)