How to hack whatsapp using whazzak
9 Ways Your WhatsApp Messages Can Be Hacked
WhatsApp is a popular and easy to use messaging app. It has some security features, like the use of end-to-end encryption, which tries to keep your messages private. However, as good as these security measures are, WhatsApp still isn't immune to hacks, which can end up compromising the privacy of your messages and contacts.
Don't take our word for it: just go and see how many "How to hack WhatsApp" guides you'll find on the internet if you're persistent enough.
As knowing is half the battle, if we are simply aware of vulnerabilities, we can then take concrete steps to avoid comprising ourselves. To that end, here are a few ways that WhatsApp can be hacked.
1. Remote Code Execution via GIF
In October 2019, security researcher Awakened revealed a vulnerability in WhatsApp that let hackers take control of the app using a GIF image. The hack works by taking advantage of the way WhatsApp processes images when the user opens the Gallery view to send a media file.
When this happens, the app parses the GIF to show a preview of the file. GIF files are special because they have multiple encoded frames. This means that code can be hidden within the image.
If a hacker were to send a malicious GIF to a user, they could compromise the user's entire chat history. The hackers would be able to see who the user had been messaging and what they had been saying. They could also see users' files, photos, and videos sent through WhatsApp.
The vulnerability affected versions of WhatsApp up to 2.19.230 on Android 8.1 and 9. Fortunately, Awakened disclosed the vulnerability responsibly and Facebook, which owns WhatsApp, patched the issue. To keep yourself safe from this problem and similar, you should always keep WhatsApp updated.
2. The Pegasus Voice Call Attack
Another WhatsApp vulnerability discovered in early 2019 was the Pegasus voice call hack.
This scary attack allowed hackers to access a device simply by placing a WhatsApp voice call to their target. Even if the target didn't answer the call, the attack could still be effective. And the target may not even be aware that malware has been installed on their device.
Even if the target didn't answer the call, the attack could still be effective. And the target may not even be aware that malware has been installed on their device.
This worked through a method known as buffer overflow. This is where an attack deliberately puts in so much code into a small buffer that it "overflows" and writes code into a location it shouldn't be able to access. When the hacker can run code in a location that should be secure, they can take malicious steps.
This attack installed an older and well-known piece of spyware called Pegasus. This allowed hackers to collect data on phone calls, messages, photos, and video. It even let them activate devices' cameras and microphones to take recordings.
This vulnerability is applicable on Android, iOS, Windows 10 Mobile, and Tizen devices. It was used by the Israeli firm, NSO Group, for example, which has been accused of spying on Amnesty International staff and other human rights activists. After news of the hack broke, WhatsApp was updated to protect it from this attack.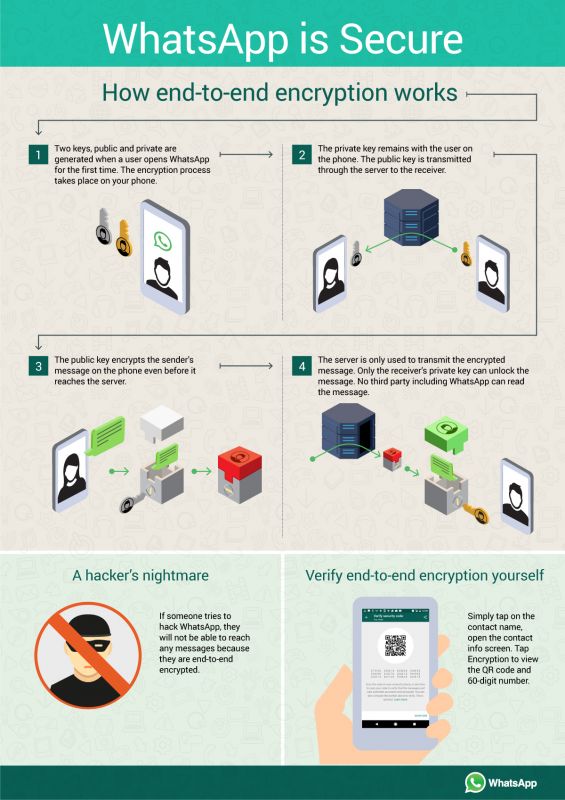
If you are running WhatsApp version 2.19.134 or earlier on Android or version 2.19.51 or earlier on iOS, then you need to update your app immediately.
Another way you're vulnerable to getting your WhatsApp hacked is through socially engineered attacks, which exploit human psychology to steal information or spread misinformation.
Security firm, Check Point Research, revealed one example of this attack, which they named FakesApp. This allowed people to misuse the quote feature in group chat and to alter the text of another person's reply. Essentially, hackers could plant fake statements that appear to be from other legitimate users.
The researchers could do this by decrypting WhatsApp communications. This allowed them to see data sent between the mobile and the web versions of WhatsApp.
And from here, they could change values in group chats. Then they could impersonate other people, sending messages which appeared to be from them. They could also change the text of replies.
This could be used in worrying ways to spread scams or fake news. Even though the vulnerability was disclosed in 2018, it had still not been patched by the time the researchers spoke at the Black Hat conference in Las Vegas in 2019, according to ZNet. It therefore becomes critical that you learn how to recognize WhatsApp scams and keep reminding yourself of these red flags periodically.
4. Media File Jacking
Media File Jacking affects both WhatsApp and Telegram. This attack takes advantage of the way apps receive media files like photos or videos and write those files to a device's external storage.
The attack starts by installing malware hidden inside an apparently harmless app. This can then monitor incoming files for Telegram or WhatsApp. When a new file comes in, the malware may swap out the real file for a fake one.
Symantec, the company that discovered the issue, suggested it could be used to scam people or to spread fake news.
There is a quick fix for this issue, though. Using WhatsApp, you should look in Settings and go to Chat Settings. Then find the Save to Gallery option and make sure it is set to Off. This will protect you from this vulnerability. However, a true fix for the issue will require app developers to entirely change the way that apps handle media files in the future.
Using WhatsApp, you should look in Settings and go to Chat Settings. Then find the Save to Gallery option and make sure it is set to Off. This will protect you from this vulnerability. However, a true fix for the issue will require app developers to entirely change the way that apps handle media files in the future.
5. Facebook Could Spy on WhatsApp Chats
In an official blog post, WhatsApp asserted that due to its end-to-end encryption, it is impossible for Facebook to read WhatsApp content:
"When you and the people you message are using the latest version of WhatsApp, your messages are encrypted by default, which means you're the only people who can read them. Even as we coordinate more with Facebook in the months ahead, your encrypted messages stay private and no one else can read them. Not WhatsApp, not Facebook, nor anyone else."
However, according to developer Gregorio Zanon, this is not strictly true. The fact that WhatsApp uses end-to-end encryption does not mean all messages are private. On an operating system like iOS 8 and above, apps can access files in a "shared container."
The fact that WhatsApp uses end-to-end encryption does not mean all messages are private. On an operating system like iOS 8 and above, apps can access files in a "shared container."
Both the Facebook and WhatsApp apps use the same shared container on devices. And while chats are encrypted when they are sent, they are not necessarily encrypted on the originating device. This means the Facebook app could potentially copy information from WhatsApp.
There is no evidence that Facebook has used shared containers to view private WhatsApp messages. But the potential is there. Even with end-to-end encryption, your messages may not be private from the all-capturing net of Facebook.
6. Paid Third-Party Apps
You'd be surprised how many paid legal apps have sprung up in the market, which solely exist for hacking into secure systems. It's super easy to carry out covert WhatsApp hacks through this method.
In fact, it isn't unheard of for big corporations to work hand-in-hand with oppressive regimes to target activists and journalists; or by cybercriminals, intent on getting your personal information.
Apps like Spyzie and mSPY can easily hack into your WhatsApp account for stealing your private data. All you need to do is purchase the app, install it, and activate it on the target phone. You can then simply sit back and connect to your app dashboard from the web browser, and snoop in on private WhatsApp data like messages, contacts, status, etc. But obviously, we advise against anyone actually doing this!
7. Fake WhatsApp Clones
Using fake website clones to install malware is an old hacking strategy still implemented by cyber criminals all over the world. These clone sites are known as malicious websites.
The hacking tactic has now also been adopted for breaking into Android systems. To carry out a WhatsApp hack on your account, an attacker will first try to install a clone of WhatsApp, which might look strikingly similar to the original app.
Take the case of the WhatsApp Pink scam, for instance. A clone of the original WhatsApp, it claims to change the standard green WhatsApp background to pink.
Here's how it works: an unsuspecting user receives a link to download the WhatsApp Pink app for changing the background color of their app. And even though it really does change the background color of your app to pink, as soon as you install the app, it will start collecting data not just from your WhatsApp but also from everything else stored on your phone.
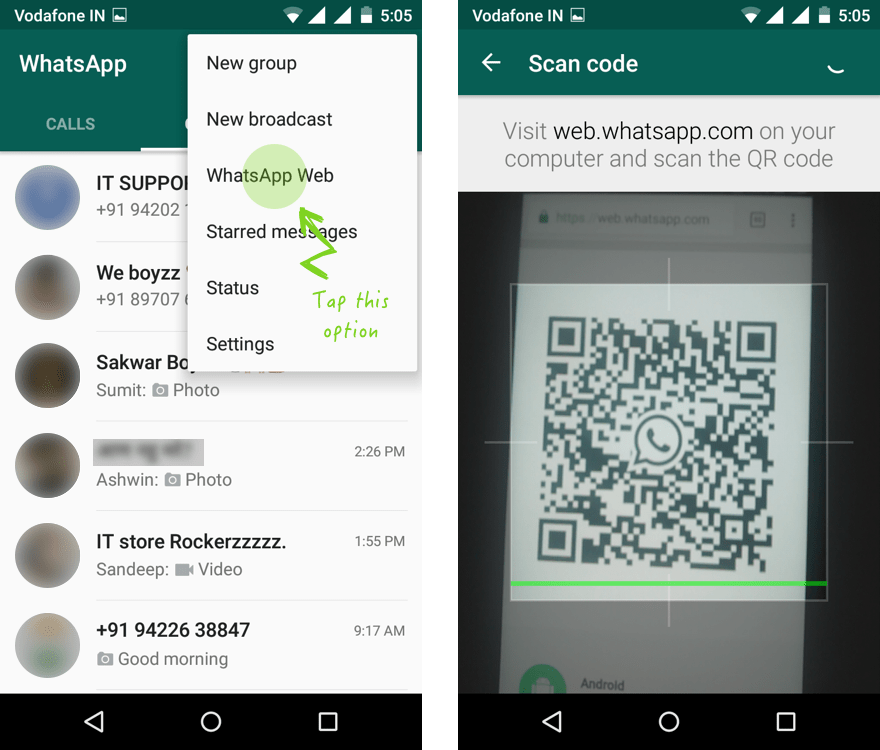
8. WhatsApp Web
WhatsApp Web is a neat tool for someone who spends most of their day on a PC. It provides the ease of accessibility to WhatsApp users, so they won't have to pick up their phone again and again for messaging. The big screen and keyboard provides an overall better user experience too.
Here's the caveat though. As handy as the web version is, it can be easily used to hack into your WhatsApp chats. This danger arises when you're using the WhatsApp Web on someone else's computer.
So if the owner of the computer has selected the "keep me signed in" box during login, then your WhatsApp account will stay signed-in even after you've closed the browser.
The computer owner can then access your information without much difficulty.
You can avoid this by making sure that you log out from WhatsApp Web before you leave.
But as they say, prevention is better than cure. The best approach is to avoid using anything other than your personal computer for the web version of WhatsApp altogether.
9. Exporting Your Chats
This isn't the traditional method you'd find on the "how to hack someone's WhatsApp" guides. While some of the other methods are really elaborate, and some just capitalize on blank spots in the human psyche, this one simply requires physical access to your smartphone.
And no, the hacker doesn't need a lot of time with your phone, either; just a few seconds is enough. This gives them enough time to export your messages to a location they can later access. It could be anything: an email account, cloud storage, or even a messaging app.
Once a hacker has access to your phone, all they have to do is move to a specific chat, click on the Export chat option and select the location they'd like to move your message history to.
The solution? The ironclad way to protect yourself is to keep your phone away from unfamiliar hands at all times. Furthermore, you have the option to enable fingerprint lock for your WhatsApp. Here's how:
- Head to Accounts > Privacy > Fingerprint lock.
- Toggle the Unlock with fingerprint option on, and set the lock activation to Immediately.
Now, every time your WhatsApp is picked up after inactivity, your fingerprints will be required to launch the app.
Stay Aware of Security Issues in WhatsApp
These are just a few examples of how your WhatsApp can be hacked. While WhatsApp has patched some of these issues since their disclosure, some weak spots persist, so it's important to stay vigilant. To learn more about whether WhatsApp is safe, you need to brush up your knowledge of WhatsApp security threats. Always keep yourself updated!
What Is Whazzak? How to use it as a hack tool?
How to use Whazzak WhatsApp?
It should be noted that Whazzak was created in 2017 to easily hack Whazzak accounts. This feature can be used by thousands of people, such as hackers, ordinary people, and parents, to monitor and control the activities of their children. Whazzak WhatsApp is a hacking tool that is being developed ( in Slovak: hackovací nástroj, ktorý sa vyvíja ) today by many hackers and developers in the field of application and network security. With the use of hacking tools, you can easily access all the data in accounts without two-step verification.
This feature can be used by thousands of people, such as hackers, ordinary people, and parents, to monitor and control the activities of their children. Whazzak WhatsApp is a hacking tool that is being developed ( in Slovak: hackovací nástroj, ktorý sa vyvíja ) today by many hackers and developers in the field of application and network security. With the use of hacking tools, you can easily access all the data in accounts without two-step verification.
You may ask, what is the use of Whazzak? We will give you an example below to better understand the use of Whazzak.
Suppose you are in a relationship with a company in another part of the world, such as the United States, and you have contacted that company through WhatsApp. In this case, you want to examine them until you find out more about them. In this case, you can easily use Whazzak to easily access information and data about the calls, messages, contacts, and required items.
How can we hack WhatsApp using Whazzak?
To be able to use Whazzak to hack WhatsApp, it is best to follow these steps:
1- Check the Whazzak website.
2- Then, on the page that shows us, enter the phone number of the desired device. After entering the contact number of the device, it is better to select the content that we want to save.
3- After selecting all the desired information and contents, it is better to click on the hack button.
As you know, there are two types of hacks and hackers: black hat hackers and white hat hackers.
It should be noted that the skills required to do these things are required for both hackers, but the only difference between them is their intention and purpose. Black hat hackers aim to sabotage, and white hat hackers work to increase network security.
In this way, the white hat hacker can try to increase the network's security by identifying the weaknesses and vulnerabilities of the network.
Similarly, a WhatsApp hacker can be a black hat hacker or a white-hat hacker with different goals to increase network security by identifying vulnerabilities, or he can attack and hack the network by identifying vulnerabilities. Slowly
Slowly
Note:
It is better to point out that if you try to hack WhatsApp, there are many crimes you can face. So be aware that this can have consequences and problems for you.
What is the alternative to Whazzak?
As we said, if you use WhatsApp and hack into accounts on social network, you may face some serious problems. For this reason, there are several alternatives to WhatsApp, one of which is Aspire. Aspire is a good alternative to WhatsApp. Aspire can also be used on all platforms and operating systems. You are operating systems and platforms such as Android, iOS, Windows, and Mac.
WhatsApp accounts can be easily hacked using Aspire. In addition, you can fully access the messages in the account and control and manage them remotely.
As you know, WhatsApp is one of the most popular and popular social networks that can be used by many people and users around the world. So far, no filter has been created that can be used to filter and examine messages. But with Aispyer for Android, we can easily control and manage the children and people we want and access and manage all their activities.
But with Aispyer for Android, we can easily control and manage the children and people we want and access and manage all their activities.
This program is very convenient and does not use many resources, which has made this program a popular and popular program. Because this program does not use many resources, the user can hardly notice the hacking and the existence of this program to hack his phone. Aspire for Android can secretly and very powerfully perform the desired operation.
It is better to register at aispyer.com and then start doing the desired hacking and control activities to use this program.
The features of Aispyer for Android are as follows:
- It is very easy to install.
- Does not use many resources.
- Unobtrusively and without the user noticing the program's existence can work and perform the desired operation.
- In addition to the possibility and influence of other activities such as control and management of calls, messages, and even video calls.
- All details such as date, time, number, contact, text message, etc., can be displayed.
- Can check all incoming and outgoing messages.
- All user activities on social networks such as
- All user activities on social networks such as Instagram, WhatsApp, Skype, Snap Chat, etc., can be examined.
Is hacking Whazzak WhatsApp legal or illegal?
We cannot give a clear and direct answer to the question that may arise for you whether hacking WhatsApp is legal or illegal. We cannot say yes. It is legal, and we cannot say no. It is illegal.
In some cases, parents use this application to control and manage their children, which is a legal practice. In other cases, buying people to pry or steal people's data and threatening them is illegal and has problems and crimes.
Note:
You may also be wondering if we can use the hacking process if two-step verification is enabled? The answer to this question is no. If two-step verification is enabled, it is not possible to hack and hack into the user account and check and control their data using Whazzak.
Whazzak Facebook and Whazzak Instagram do not currently exist, and the Whazzak hacking feature is only available for WhatsApp.
How can we clear our WhatsApp chat history?
To clear chat history in WhatsApp, we can easily do this by sending a photo. Of course, it should be noted that this method can be used for people who want to access the message history and delete it without hacking the mobile device. How to do this is to insert a malicious link through an image or even a GIF and infect the phone and account of the person and perform the hacking process.
To do this, hackers first write code related to each other or create a related link for fake and illegal login to WhatsApp.
This link then places the fake login to the account inside the picture or a GIF.
We will send the infected photo and file to the fake login link to the desired person.
If the user and the person in question open the infected photo we sent, a malicious link will be displayed for him that connects him to the web page and causes his mobile device to become infected. In this case, the viruses will be loaded on his phone to access the message history.
In this case, the viruses will be loaded on his phone to access the message history.
How can we prevent our phone from being hacked and WhatsApp account?
To prevent the process of hacking and infiltrating people using some malicious tools and files and viruses, it is better to enable two-step verification for the WhatsApp account in the initial stages. By activating this option, it is impossible to hack the account even using Whazzak.
We can even use QR to access our WhatsApp web and be notified of all the devices and people in our account and cut off access to the account if necessary.
Clicking on Sign out from all places is another way to protect. In addition, if none of these methods work, we can reinstall them.
In this article, we have provided you with methods to hack accounts, and of course, the best methods are to use approved hacking methods. Of course, these methods are paid, but paid versions are much safer and more powerful than free versions.
how to log out of whatsapp on all devices?
By Milena Anderson Reading 5 min. Views 2.8k. Posted by
Short answer
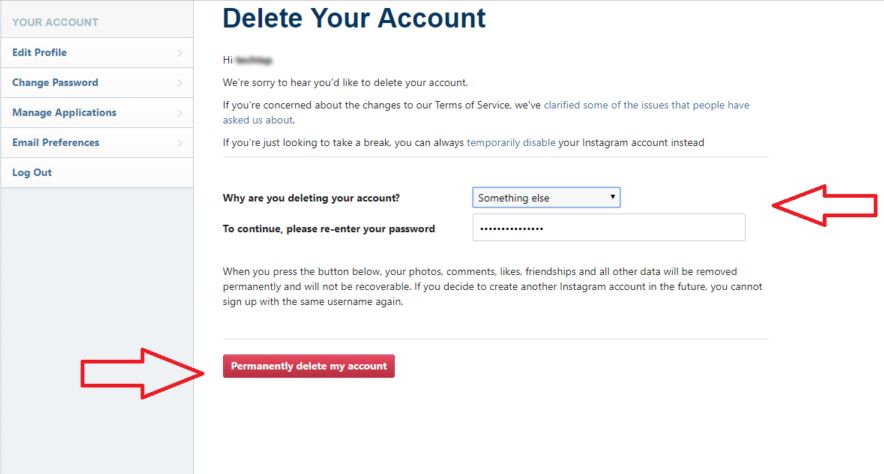
- To sign out of WhatsApp on all devices, you need to delete your account.
- To do this, open WhatsApp and go to Settings > Account > Delete my account.
how to log out of whatsapp on all devices
log out of whatsapp from other devices | how to log out whatsapp on all devices
how to log out whatsapp on other devices?
To sign out of WhatsApp on other devices, open WhatsApp and select Menu > Settings > Account > Sign out.
How do I know which devices my WhatsApp is signed in to?
To view the devices that are signed in to your WhatsApp account, open WhatsApp and select Menu > Settings > Account > tap Change number. You will then see a list of devices that are currently signed in to your account.
How to log out of WhatsApp on all Iphone devices?
To sign out of WhatsApp on all devices, you need to delete your account. To do this, open WhatsApp and go to Settings > Account > Delete my account.
How to exit WhatsApp without deleting it?
Unable to exit WhatsApp without deleting the application.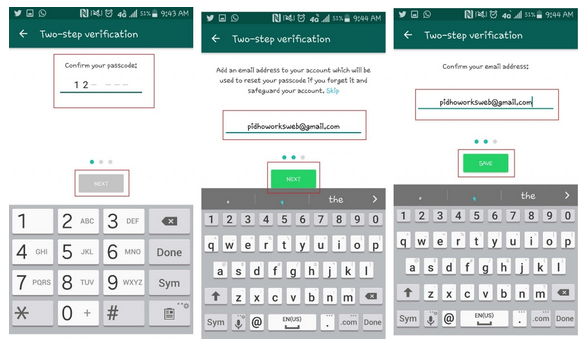 If you want to stop using the app, you will need to remove it from your phone.
If you want to stop using the app, you will need to remove it from your phone.
How do I sign out of WhatsApp on my laptop?
To log out of WhatsApp on a laptop, first open the app. Then click on the three dots in the upper right corner of the screen and select "Logout".
Can I log in to WhatsApp from two phones?
Yes, WhatsApp can be connected to two phones. To do this, open WhatsApp on your primary phone and go to Settings > Account > Dual SIM & Phone Numbers. Click on the phone number you want to use as your primary phone number and then click on the check mark.
How do I know if someone is checking me on WhatsApp?
There is no reliable way to know for sure if someone is checking your WhatsApp messages, but there are a few things you can look out for. If you've noticed that your phone is constantly lit up with new notifications, or that the person you're texting keeps disappearing for an extended period of time, they may be checking your messages without your knowledge..png) You can also try sending them a message and then see if their phone lights up or makes a sound.
You can also try sending them a message and then see if their phone lights up or makes a sound.
What is Whazzak?
Whazzak is a social media platform that allows users to share and discuss content with each other. It is similar to platforms such as Twitter and Facebook but focuses specifically on content sharing. Whazzak is a great way to keep up with the latest news and trends.
How to log out of WhatsApp on Android?
To sign out of WhatsApp on Android, open the app and tap on the three bars in the top left corner. Click "Settings" and then "Account". Click “Logout” and confirm by clicking “Logout”.
Can I turn off WhatsApp?
Yes, you can disable WhatsApp. To do this, open the application and select “Settings” > “Account” > “Privacy”. In the "Last seen" section, set "Everyone" to "Only my contacts" or "No one". You can also disable read receipts and delivery reports.
How do I remove multiple devices from WhatsApp beta?
To remove multiple devices from WhatsApp beta, you need to unregister your phone number from the app. This can be done in the settings menu. Once you unregister your number, you can re-register it on a new device.
How can I use WhatsApp on two devices with the same number?
If you want to use WhatsApp on two devices with the same number, you can either create a new account on the other device or restore the old account on the new device. To create a new account, open WhatsApp on the first device and click "Create a new account". To restore your old account, open WhatsApp on your new device and click "Restore Chat History".
Is it possible to hack WhatsApp on Android?
Yes, WhatsApp can be hacked on Android. However, this is not easy to do and requires some technical knowledge. There are several ways to hack WhatsApp on Android, but the most common is to install a spy app such as mSpy or FlexiSPY. These apps allow you to read messages, track location, and even listen to conversations.
These apps allow you to read messages, track location, and even listen to conversations.
Can you tell if your phone has been hacked?
There are several things you can do to determine if your phone has been hacked. One is to check data usage. If you're suddenly using a lot more data than usual, someone might be spying on your phone. Another thing to check is battery life. If your battery is draining faster than usual, someone may be using your phone's resources to spy on you. Finally, you can check your apps for weird activity.
Can I find out who is following you on WhatsApp?
It is impossible to know exactly who is following you on WhatsApp because the application does not provide such a function. However, there are some things you can do to try and protect yourself from stalking. First, be sure to only share your contact information with people you trust. Second, be careful about the information you post on your profile. Finally, make sure your WhatsApp account is locked with a strong password.
Finally, make sure your WhatsApp account is locked with a strong password.
WhatsApp hack: dealing with the consequences
Another WhatsApp hack has happened. Let's talk about who, where and how did it!
Earlier this week, many publications reported that a vulnerability had been found in the popular WhatsApp messenger. With its help, hackers can install spyware on victims' smartphones, giving access to all confidential data stored on the device, including photos, mail and messages.
Who hacked WhatsApp
It is directly stated that the Israeli NSO Group is behind the discovery and exploitation of the vulnerability. The company develops spyware for use by government intelligence agencies. Several hacking attempts were registered (how many of them were successful is not reported).
How it works from the outside
The operation of the exploit is almost invisible to the user and does not require any interaction. Hacking WhatsApp and installing a Trojan can only be marked by a missed call. But after installing the Trojan, even the logs can be cleaned up. Everything works on both iOS and Android.
Hacking WhatsApp and installing a Trojan can only be marked by a missed call. But after installing the Trojan, even the logs can be cleaned up. Everything works on both iOS and Android.
WhatsApp buffer overflow
WhatsApp is used by one and a half billion people, and it could be assumed that increased attention is paid to its security. However, hacking WhatsApp turned out to be quite simple.
For official details, see CVE-2019-3568 - "Buffer overflow in WhatsApp VOIP stack with a series of SRTCP packets results in remote code execution."
How does this vulnerability actually work?
Buffer overflow is a phenomenon that occurs when a computer program writes data beyond the limits of a buffer allocated in memory.
Buffer overflow usually occurs due to improper handling of data received from outside and memory, in the absence of hard protection from the programming subsystem (compiler or interpreter) and the operating system. As a result of an overflow, data located next to the buffer (or before it) can be corrupted.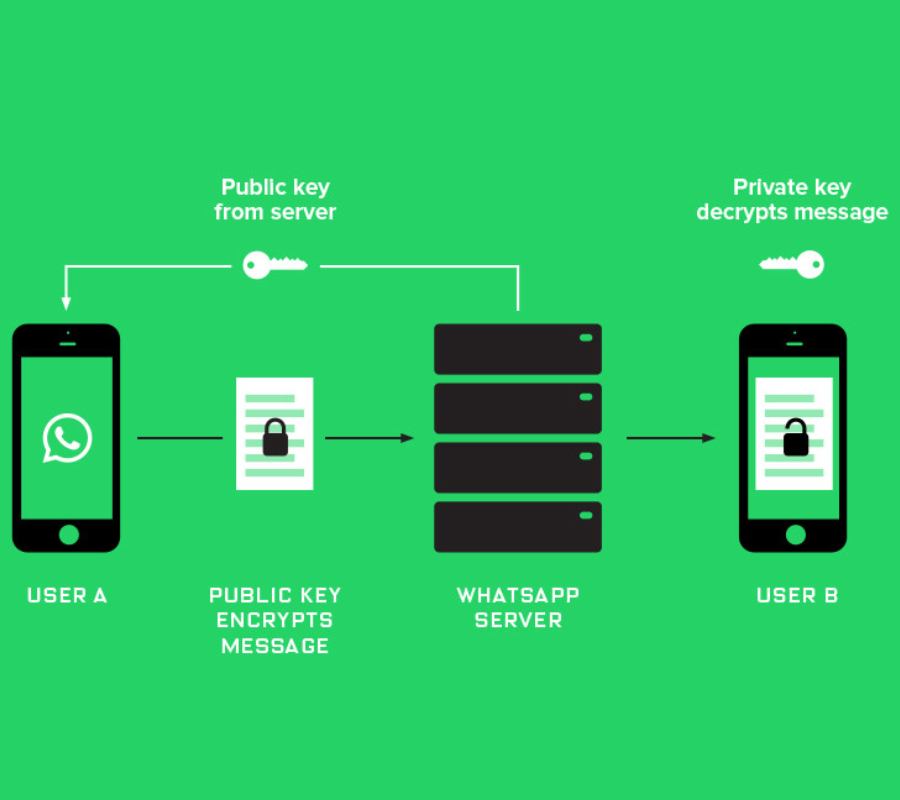
Buffer overflow is one of the most popular methods of hacking computer systems. Most high-level languages use stack frame technology - placing data on the process stack, mixing program data with control data (including the start address of the stack frame and the return address from the executing function).
CheckPoint compared two versions of WhatsApp in search of changes.
WhatsApp made its own implementation of the SRTCP protocol. And this is done natively, that is, in C / C ++. During the parsing of the patch, two additional size checks were found to protect against memory overflows when parsing and processing network packets.
Size check #1
At the very beginning of the RTCP handler, a variable check for the maximum size of 1480 bytes has been added.
During the debug, the programmers found out that this is a really important function of the RTCP module. It is called even before a WhatsApp voice call is answered.
Size check #2
The same variable is used twice more in the newly added checks:
- Check that the packet length field does not exceed the specified length.
- Additional check that length is <= 1480 again, just before copying to memory.
It can be seen that logging is even added in the second check. It explicitly states that this is done to protect against a possible buffer overflow.
The entire SRTCP module is quite large. CheckPoint acknowledges that there may be other changes that have gone unnoticed.
The developers also assume that this module contains other yet unknown network packet parsing vulnerabilities.
Does this WhatsApp hack threaten you personally?
Most likely not. The NSO Group works for governments and the attacks were targeted. This is not a subject of mass use. Bye.
How to protect yourself?
On the same day that the security bulletin was published, Facebook released updated versions of WhatsApp for iOS and Android. They have a vulnerability. Just update your apps.
Pavel Durov and the WhatsApp hack
In Russia, one of the most notable media consequences of the hack was the publication of an column by Pavel Durov, in which he criticizes his main competitor.
In particular, he writes:
The whole world was shocked by the news that the WhatsApp application turned its users' devices into spy devices for spying on people.
However, this news did not surprise me at all. Last year, WhatsApp faced a similar problem that they had to admit publicly: one video call was enough to access absolutely everything on your device.
Once WhatsApp fixes one serious vulnerability in the application, a new one appears in its place. All problems related to the protection of personal data are suspiciously convenient for unauthorized access, and in their appearance and functioning they resemble backdoors.
Unlike Telegram, WhatsApp is not open source, so it is almost impossible to quickly check the code for backdoors. WhatsApp not only does not publish its application code, but does exactly the opposite: it deliberately goes to great lengths to hide its binary code and prevent any attempts to study it.
What a developer should do
Learn about buffer overflows, security issues in general, and safe programming itself, use checks in your applications and programs.