How to hack telegram group
Top 10 Telegram Cybersecurity Groups You Should Join
Social media has long been a great way to keep up to date with breaking news and the latest innovations in special interest areas, and this is especially true in cybersecurity. While you’ll find Twitter a great resource, there are other platforms, from the giants like Facebook, Reddit and LinkedIn to the comparatively niche such as Discord, Slack and Telegram, where you can also find special interest pages, channels, and groups dedicated to the latest in cyber-related events.
Telegram in particular has seen a lot of rapid growth recently in light of media attention focusing on data sharing between rival messaging platform WhatsApp and WhatsApp’s parent company Facebook. If you are one of those that has recently chosen to leap onto Telegram for this or some other reason, or you’re already a Telegram user but haven’t thought about how it can help you keep up with your cybersecurity interests, then this is the post for you.
Below, we highlight ten of the most useful cybersecurity groups we follow on Telegram. Whether you’re interested in penetration testing, red teaming, blue teaming, malware research, reverse engineering, bug hunting, vulnerability research, network security or anything else to do with cyber or enterprise security, if you’ve been wondering what are some good channels to join on Telegram for cybersecurity, these ten groups should help ensure you never miss a thing.
1. Cyber Security News (26k+ members)
Cyber Security News is a feed channel for links to breaking news stories across the internet, everything from TechCrunch and the Washington Post to Portswigger and Security Boulevard. In other words, it’s a one-stop shop for cyber-related news that should be your first port of call along with your morning coffee.
2. Cyber Security Experts (16k+ members)
Cyber Security Experts is a great channel for exchanging information about cyber, IT, and security. This channel was set up for security professionals that want to contribute to the wider security community, get answers to questions directly from security experts and leaders from across the world and help other security experts to enhance their security maturity.
This channel was set up for security professionals that want to contribute to the wider security community, get answers to questions directly from security experts and leaders from across the world and help other security experts to enhance their security maturity.
However, as can be seen from our screen capture above, new users are wont to get into hot water if they don’t read the rules! These are conveniently (and obviously) pinned at the top, and yet some folks still seemingly miss them! If you want to join this group and benefit from getting involved in the chat, remember:
🚨Important rules 🚨
- No illegal stuff (links, offers etc)
- No advertisement (zero tolerance)
- No links to other Telegram channels
- No racism, bad language or destructive behavior
- Be kind and help others. Don’t just consume, and ask if you have a question!
3. Cloud & Cybersecurity (~9k members)
Cloud and Cybersecurity is a unique group that we feel far more people in Infosec would benefit from being a member of. This channel offers career advice, daily quizzes, tips and useful resources that can provide real material benefit and learning no matter what level you’re currently at. If you’re looking to improve on what you know and develop your career (and who isn’t?), then this is a great channel to join.
This channel offers career advice, daily quizzes, tips and useful resources that can provide real material benefit and learning no matter what level you’re currently at. If you’re looking to improve on what you know and develop your career (and who isn’t?), then this is a great channel to join.
4. Cybersecurity & Privacy News (~8k members)
Cybersecurity & Privacy News offers daily news about cyber security and privacy. In this channel, you’ll find everything from alerts on the latest security vulnerabilities to all the latest news you might have missed elsewhere. Chatter is limited, but if you need a notification on what is happening in security vulns, this group is ideal for that.
5. Android Security & Malware (26k+ members)
Android Security & Malware is a channel for all things Android, discussing vulnerabilities, fuzzing techniques, guides and much more. On here you’ll find great questions and answers to real Android security problems, links to open source tools, malware analyses, new CVEs, and a plethora of tips and guides. And if you have something to share, that’s more than welcome, too. If you’re into Android security, this is a community you will definitely want to join.
And if you have something to share, that’s more than welcome, too. If you’re into Android security, this is a community you will definitely want to join.
6. Malware Research (9k+ members)
Malware Research is a channel for all malware practitioners, and you will come across many articles and useful Github repos that you would likely not come across if it wasn’t for being a member of this channel. This is an essential join if you’re a malware analyst, researcher, or reverse engineer.
7. BugCrowd (~6k members)
The BugCrowd channel has almost 3000 bug bounty hackers discussing topics like HackerOne, Intigriti, Cobalt Strike, Yogosha and more. Here you will also learn of new bug bounty programs and platforms. Anyone interested in finding and responsibly disclosing security vulnerabilities will find plenty of value in the discussions in this channel. Expect to learn a lot and don’t be afraid to contribute back to the community when you have something interesting to share.
8. Red Team Alerts (10k+ members)
Red Team Alerts is a dedicated channel for, you guessed it, all things red teaming! From beginners guides and hardware how-tos, this channel will provide help to expand your awareness of what’s going on in, and how to get involved with, the fascinating world of offensive security testing, role playing and attack modelling.
9. APT Intelligence (1k+ members)
APT Intelligence is a recent but growing channel that serves up links and news on topics related to advanced threat actors, tools, techniques and procedures.
Despite the focused name, the nature of APT tradecraft means there’s inevitably wide coverage of many other cybersecurity topics of interest, particularly tools for things like OSINT, pen testing, password cracking and so on. We’ve found a number of interesting tools through this channel recently and it promises to be an extremely useful resource.
10. Reverse Engineering Hangout (~300 members)
Reverse Engineering Hangout is a small but useful place to learn more and share knowledge about reverse engineering. You can also ask questions about assembly, opcodes, x86 and anything else if you need help understanding how a sample works. Ideal for beginners who want to learn, or experts willing to share, you’ll also find plenty of links to free online resources on topics like binary exploitation, reverse engineering and CTF challenges. Unlike some of the other groups in our list, REH doesn’t mind links to other relevant Telegram groups, so you can also use this channel as a jumping board to discover other channels related to RE such as the much larger but single-focus channel for Frida.
You can also ask questions about assembly, opcodes, x86 and anything else if you need help understanding how a sample works. Ideal for beginners who want to learn, or experts willing to share, you’ll also find plenty of links to free online resources on topics like binary exploitation, reverse engineering and CTF challenges. Unlike some of the other groups in our list, REH doesn’t mind links to other relevant Telegram groups, so you can also use this channel as a jumping board to discover other channels related to RE such as the much larger but single-focus channel for Frida.
Are There Other Good Cybersecurity Channels on Telegram?
Of course! There are many, and you can use the search tool in your Telegram client to discover channels by keyword or tag. Note that in our selection, we’ve specifically avoided groups that share prohibited copyright material, that publish stolen credentials or that explore the less seemly side of cybersecurity. Such groups certainly exist and can be useful to researchers with specialist interest.
We’ve also focused on broad-interest groups rather than special interest groups dedicated to particular security tools or security software, but again, these can also be found through a bit of searching. Finally, we limited our choice to English language only (or mainly) channels, but there is a wide variety of other channels on Telegram that cater to other languages, not least of course, Russian!
Exclusive: Hackers accessed Telegram messaging accounts in Iran - researchers
By Joseph Menn, Yeganeh Torbati
7 Min Read
SAN FRANCISCO/WASHINGTON (Reuters) - Iranian hackers have compromised more than a dozen accounts on the Telegram instant messaging service and identified the phone numbers of 15 million Iranian users, the largest known breach of the encrypted communications system, cyber researchers told Reuters.
Amir Rashidi, an Internet security researcher who has worked with Telegram users who were victims of hacking, works at the offices of International Campaign for Human Rights in Iran, in the Brooklyn borough of New York, U. S., July 27, 2016. REUTERS/Brendan McDermid
S., July 27, 2016. REUTERS/Brendan McDermid
The attacks, which took place this year and have not been previously reported, jeopardized the communications of activists, journalists and other people in sensitive positions in Iran, where Telegram is used by some 20 million people, said independent cyber researcher Collin Anderson and Amnesty International technologist Claudio Guarnieri, who have been studying Iranian hacking groups for three years.
MORE REUTERS TOP STORIES:
Didi's China dominance over Uber offers roadmap for ride-hailing rivals
Commentary: The real reason Washington calls Putin a thug
First Republican lawmaker breaks with party, backs Democrat Clinton
Telegram promotes itself as an ultra secure instant messaging system because all data is encrypted from start to finish, known in the industry as end-to-end encryption. A number of other messaging services, including Facebook Inc's FB.O WhatsApp, say they have similar capabilities.
Headquartered in Berlin, Telegram says it has 100 million active subscribers and is widely used in the Middle East, including by the Islamic State militant group, as well as in Central and Southeast Asia, and Latin America.
Telegram’s vulnerability, according to Anderson and Guarnieri, lies in its use of SMS text messages to activate new devices. When users want to log on to Telegram from a new phone, the company sends them authorization codes via SMS, which can be intercepted by the phone company and shared with the hackers, the researchers said.
Armed with the codes, the hackers can add new devices to a person’s Telegram account, enabling them to read chat histories as well as new messages.
“We have over a dozen cases in which Telegram accounts have been compromised, through ways that sound like basically coordination with the cellphone company,” Anderson said in an interview.
Slideshow ( 4 images )Telegram’s reliance on SMS verification makes it vulnerable in any country where cellphone companies are owned or heavily influenced by the government, the researchers said.
A spokesman for Telegram said customers can defend against such attacks by not just relying on SMS verification. Telegram allows - though it does not require - customers to create passwords, which can be reset with so-called “recovery” emails.
“If you have a strong Telegram password and your recovery email is secure, there’s nothing an attacker can do,” said Markus Ra, the spokesman.
Iranian officials were not available to comment. Iran has in the past denied government links to hacking.
ROCKET KITTEN
The Telegram hackers, the researchers said, belonged to a group known as Rocket Kitten, which used Persian-language references in their code and carried out “a common pattern of spearphishing campaigns reflecting the interests and activities of the Iranian security apparatus.”
Anderson and Guarnieri declined to comment on whether the hackers were employed by the Iranian government. Other cyber experts have said Rocket Kitten’s attacks were similar to ones attributed to Iran’s powerful Revolutionary Guards.
The researchers said the Telegram victims included political activists involved in reformist movements and opposition organizations. They declined to name the targets, citing concerns for their safety.
“We see instances in which people ... are targeted prior to their arrest,” Anderson said. “We see a continuous alignment across these actions.”
The researchers said they also found evidence that the hackers took advantage of a programing interface built into Telegram to identify at least 15 million Iranian phone numbers with Telegram accounts registered to them, as well as the associated user IDs. That information could provide a map of the Iranian user base that could be useful for future attacks and investigations, they said.
“A systematic de-anonymization and classification of people who employ encryption tools (of some sort, at least) for an entire nation” has never been exposed before, Guarnieri said.
Ra said Telegram has blocked similar “mapping” attempts in the past and was trying to improve its detection and blocking strategies.
Cyber experts say Iranian hackers have become increasingly sophisticated, able to adapt to evolving social media habits. Rocket Kitten’s targets included members of the Saudi royal family, Israeli nuclear scientists, NATO officials and Iranian dissidents, U.S.-Israeli security firm Check Point said last November.
POPULAR IN THE MIDDLE EAST
Telegram was founded in 2013 by Pavel Durov, known for starting VKontakte, Russia’s version of Facebook, before fleeing the country under pressure from the government.
While Facebook and Twitter are banned in Iran, Telegram is widely used by groups across the political spectrum. They shared content on Telegram “channels” and urged followers to vote ahead of Iran’s parliamentary elections in February 2016.
Last October, Durov wrote in a post on Twitter that Iranian authorities had demanded the company provide them with “spying and censorship tools.” He said Telegram ignored the request and was blocked for two hours on Oct. 20, 2015.
20, 2015.
Ra said the company has not changed its stance on censorship and does not maintain any servers in Iran.
After complaints from Iranian activists, Durov wrote on Twitter in April that people in “troubled countries” should set passwords for added security.
Amir Rashidi, an internet security researcher at the New York-based International Campaign for Human Rights in Iran, has worked with Iranian hacking victims. He said he knew of Telegram users who were spied on even after they had set passwords.
Ra said that in those cases the recovery email had likely been hacked.
Anderson and Guarnieri will present their findings at the Black Hat security conference in Las Vegas on Thursday. Their complete research is set to be published by the Carnegie Endowment for International Peace, a Washington-based think tank, later this year.
Reporting by Joseph Menn in San Francisco and Yeganeh Torbati in Washington; Additional reporting by Michelle Nichols at the United Nations and Parisa Hafezi in Ankara; Editing by Jonathan Weber and Tiffany Wu
what to do if telegrams are hacked
Any telegram account is a great target for hackers. And if it also belongs to the owner of the channel with a large audience, even more so. Today we will tell you how to hack a Telegram account and how you can protect yourself from it.
And if it also belongs to the owner of the channel with a large audience, even more so. Today we will tell you how to hack a Telegram account and how you can protect yourself from it.
Content
- Can Telegram be hacked
- Telegram hacked: the most popular cases
- Telegram hacked: what to do
- How to protect yourself from hacking in Telegram
Is it possible to hack Telegram
The Telegram messenger is considered one of the most reliable in its category. The developers managed to achieve this by using a special telegram protocol - MTProto. According to the creators, it provides the greatest protection of personal data and correspondence in the offer.
To justify the security of the program, the developers even announced a special competition: anyone could try to hack the "cart". The winner would receive a cash prize. So, let's try to figure out how you can hack a group in a telegram, an account, a channel.
Part of the MTProto protocol is in the public domain. The protocol is based on publicly available cryptographic encryption algorithms. Of course, the creators of the messenger have taken measures to protect against various attacks, but they cannot be 100% sure of the security of this system.
The protocol is based on publicly available cryptographic encryption algorithms. Of course, the creators of the messenger have taken measures to protect against various attacks, but they cannot be 100% sure of the security of this system.
That is why it cannot be said that Telegram is guaranteed safe. For example, let's describe one very common way that scammers use to hack telegram accounts. The user receives a message in the messenger from his friend or acquaintance with the text, where he is asked to download something, or promising some kind of win, or an opportunity to earn money if you follow such and such a link. Since he really communicated with this person, he trusts him. But by clicking on this link, a person simply transfers his account to the attackers.
And there are a lot of such cases, so it is important to protect your account from hacking. We have detailed instructions on how to do this below.
Telegram hacking: the most popular cases
Basically, all massive cases of hacking telegram accounts are committed by a group of scammers with the aim of blackmailing and extorting money. The most famous "versions" of such hacks are:
The most famous "versions" of such hacks are:
- Letters of "misfortune". These are the same cases with clicking on links from your contacts, which we described above. Further - hackers gain access to your account and say that they will return it only for a certain amount.
- Extortion through bots. Telegram has a new method of fraud - logins and passwords, personal data of users are collected by local bots, and then people receive emails in which blackmailers promise to reveal personal information about the victim's activities on the network, send it to their friends, relatives, etc.
- Interception of SMS codes. Such a fate may await users who did not enable two-factor authentication. Hackers log into your account with a captured passcode and gain access to all your data.
The telegram code does not come to the phone: causes and their elimination
And there are many similar fraudulent schemes on how to hack Telegram accounts. True, sometimes hacking happens not for selfish purposes. So in March 2022, a massive hacking of telegram channels occurred due to the desire of hackers to place calls on them to participate in illegal actions.
True, sometimes hacking happens not for selfish purposes. So in March 2022, a massive hacking of telegram channels occurred due to the desire of hackers to place calls on them to participate in illegal actions.
Telegram hacked: what to do
If someone tries to log into your telegram account, you will receive a message with a password to enter. If someone has already logged in from a new device, no matter from a computer or smartphone, you will receive an alert indicating the IP address, location, date and time of the new login. If you did not make this login, then your account was hacked, and now it can be used for personal gain. Here are some solutions to fix this issue.
First, let's analyze the situation when you have access to the Telegram application:
- First of all, go to the " Settings " messenger and go to the tab " Devices ".
- Here we see all active sessions.
 Click on the red button " End all other sessions ".
Click on the red button " End all other sessions ".
This allowed us to, so to speak, “throw out” the attacker from our account. But we are not completely protected. Therefore:
- We go into the security settings and enable two-factor authentication.
- This means that a hacker will not be able to enter your account, because to enter you will need not only a passcode generated by the messenger, but also a password that will be set by you.
More about Telegram Passcode
It’s a completely different situation when you don’t have access to your Telegram account (for example, if your phone was stolen), then:
- We call our operator and ask them to block the SIM card. Now, to restore access to the account, we request the restoration of the old number on a new SIM card.
- After that, go to your account and delete the "Active session".
You can also contact telegram support. To do this:
- Follow the link telegram.org
- Describe your problem, indicate your phone number and email so that you can be contacted.
Many people send their personal data, card numbers, passport, etc. via telegram. And they don’t clean up after themselves, but you can create a secret chat and set up auto-delete. And if during a hack, scammers get hold of this information, they can continue to spoil your life. And to avoid this, you need to protect your account. More on that below.
How to protect yourself from hacking in Telegram
To protect your profile from others to the maximum, you need to do the following:
1. We use two-factor authentication.
2. Activate the additional password.
3. From time to time we monitor the activity of other devices: we look at active sessions, follow the notifications from the messenger.
4. Enable automatic deletion of correspondence after a period of inactivity.( more details ..)
Optional: hide profile photo and phone number. The less personal data there is in the public domain, the more protected you are from hacker attacks.
Also, never click on any suspicious links. Even if they are from loved ones.
How is Telegram broken? On SMS interception and mobile network vulnerability
Let Telegram be considered one of the most secure messengers, but its users are periodically hacked. Last Friday, our colleagues from Tut.by reported that unknown people from Ukrainian IP addresses tried to access the Telegram accounts of at least six employees of the organization. Literally an hour before, our conversation with Russian human rights activist and Amnesty International expert Oleg Kozlovsky ended. He told how in 2016 his Telegram account was hacked and unknown people got access to correspondence.
As it turned out, the topic of hacking a secure messenger remains relevant to this day. And this is due not only to hackers, but also to the vulnerability of the technical protocol of mobile networks, which allows you to intercept SMS messages. We will talk about this today. But let's start with history.
And this is due not only to hackers, but also to the vulnerability of the technical protocol of mobile networks, which allows you to intercept SMS messages. We will talk about this today. But let's start with history.
Hacking in the middle of the night
Unidentified persons were able to log into the account of Russian human rights activist Oleg Kozlovsky on one April night in 2016. He found out about it only the next morning, as the operator at night turned off his incoming messages and the Internet for a short time. This is what the hack looked like from the victim's point of view.
- I received a message in Telegram about connecting a new device. Someone connected via Linux supposedly from a server from the USA. Then it turned out that the connection was made through a network of encrypted servers. It was at night when I was sleeping.
I wrote to Telegram technical support. They confirmed that there was such a connection, SMS- message was sent, and a person connected using the code from it.
They confirmed that there was such a connection, SMS- message was sent, and a person connected using the code from it.
Oleg turned to his operator. First, I received details on my number, where I saw connected and disconnected services. And then he called.
- I was told that, at the request of the operator's security service, they turned off a number of services, and then turned them back on. At night, they turned off the delivery of messages, mobile Internet and notifications about disconnecting and connecting services.
Accordingly, no notifications about manipulations came to the phone.
After 15 minutes, someone connects to my account, requests an SMS with a code. It doesn't reach my phone. And somehow this code is intercepted. They enter it, go into my account and, most likely, immediately download all the chats. And after another half an hour or an hour, all MTS services connect back.
When Oleg voiced these facts, the operator did not acknowledge them and declared a mistake. But at the same time, when Kozlovsky's account was hacked, a similar situation occurred with two more activists. One of them is Georgy Alburov, an employee of the Anti-Corruption Foundation.
But at the same time, when Kozlovsky's account was hacked, a similar situation occurred with two more activists. One of them is Georgy Alburov, an employee of the Anti-Corruption Foundation.
- One way or another, but MTS (Russian. - Note Onliner) did not recognize his participation. From my point of view, this meant that some employees were in cahoots with the attackers. Whether it was the secret services, or it was done for money... I don't know.
Oleg did not have two-step authentication enabled, and an additional password was not set, which we will discuss below. This allowed the attackers to gain access to open chats. Perhaps the files that were sent in chats were also downloaded. But, as he himself notes, there was nothing interesting there. Five years have passed, and no one has yet tried to blackmail him, correspondence has not appeared on the Internet.
According to Oleg, he encountered resistance from the Investigative Committee of Russia, where he took the statement about initiating a case on unauthorized access to computer information and a couple of other articles.
It took only a few years for the inspection to begin. Then came the refusal to initiate a criminal case. But this was useful: MTS officially responded to the investigation.
According to the operator's response, he registered an attack from an external network on the SS7 signaling network against the company's subscribers in order to force them to register on a third-party operator's node. 16 subscribers were under attack, 85 unauthorized requests such as Location Update were received.
As a source in the telecom industry explained to us, this wording hides attempts to carry out fictitious registration of subscribers in someone else's switch in one of the networks of MTS roaming partners, simulating the work of a subscriber in roaming so that incoming calls and messages go through this "guest" switch .
The document says that the duty specialist of the MTS Information Security Department decided that night to protect subscribers and turn off SMS, informing them about adding and deleting services, as well as mobile Internet for an hour. According to the same letter, the actions of the employee were recognized as redundant due to his lack of competence. The employee was reprimanded, later he quit of his own free will.
According to the same letter, the actions of the employee were recognized as redundant due to his lack of competence. The employee was reprimanded, later he quit of his own free will.
- This is a really vulnerable channel. Everything that is transmitted via SMS can be read not only by special services, but also by hackers, and not necessarily super cool and incredibly advanced. Both equipment and software systems for such hacking are sold. In addition, mobile operators also have access, for which not all employees are honest.
The SS7 vulnerability
SS7, which was mentioned in that letter from the Russian MTS, is a set of signaling telephone protocols. It was developed half a century ago, and today it is widely used in the provision of most services: when establishing a telephone call, calling from a mobile phone to a fixed number, roaming, sending SMS messages, and so on. The vulnerability of this protocol was periodically discussed by European, Russian and American experts.
The introduction of SS7 in Europe refers to the time when GSM mobile networks were built, in which, when roaming, the "visitor" network switch (MSC / VLR) must access the subscriber's "home" network home network home register (HLR), which stores data about this subscriber. Currently, SS7 constitutes the signaling infrastructure of almost all fixed and mobile operators and is used to transmit connection and routing information.
However, the outdated security concepts at its core make this protocol vulnerable to hackers. For example, there were many articles about vulnerabilities found that can be used to determine the location of a subscriber, listen in on a conversation, or, for example, intercept his SMS message.
German Tobias Engel in 2014 at a hacker conference in Berlin spoke about the SS7 vulnerability and demonstrated how he tracked the movements of several subscribers for two weeks (with their prior consent). They themselves provided him with their phone numbers, and he, by polling the network, was able to build a small map of their movements. So, for example, one of the subscribers lived and worked in Seattle in mid-December, and then went home to the Netherlands for Christmas. Tobias removed the last point from the presentation, as it was too close to the Dutchman's home.
So, for example, one of the subscribers lived and worked in Seattle in mid-December, and then went home to the Netherlands for Christmas. Tobias removed the last point from the presentation, as it was too close to the Dutchman's home.
As the specialist noted at the time, private companies around the world offered tools based on the SS7 vulnerability as Lawful Interception - means for law enforcement and intelligence agencies to intercept within the law.
Practically all intelligence services of all states have a direct connection to the networks of operators and can easily both listen to conversations and read SMS. This is all legal, such equipment is standardized and is called SORM in the post-Soviet space.
But we moved a little to the side.
Previously, it was enough for an attacker to have a computer with special software and be connected to the operator's network in the form of an SS7 signal point.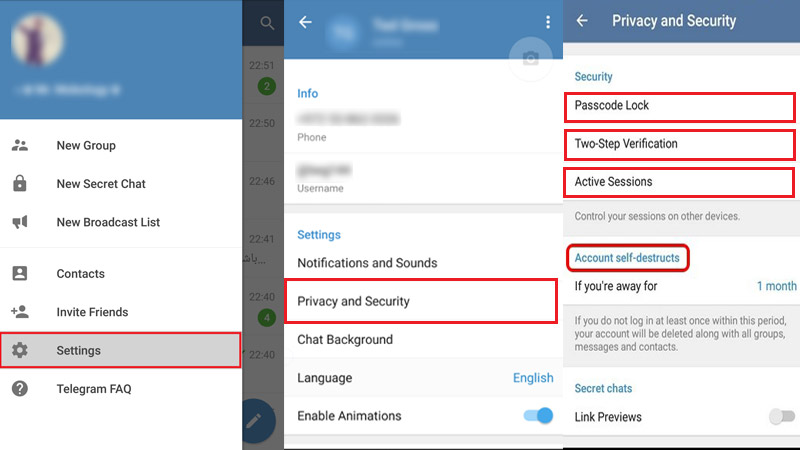 With the proper level of knowledge, it was possible to deceive the network of another operator by passing off a hacker device as a guest MSC / VLR switch.
With the proper level of knowledge, it was possible to deceive the network of another operator by passing off a hacker device as a guest MSC / VLR switch.
How is a cybersecurity attack described? An attacker connects to the SS7 signaling network of a foreign operator and sends the Send Routing Info for SM (SRI4SM) service command to the network channel, specifying the phone number of the attacked subscriber as a parameter. The subscriber's home network sends back the following technical information: IMSI (International Mobile Subscriber Identity) and the MSC address at which it currently provides services to the subscriber. Further, thanks to the received data, the attacker registers the victim's number in the dummy VLR via the Insert Subscriber Data (ISD) message, simulating that the subscriber has arrived on vacation and registered in the new network while roaming. After that, the attacker can receive SMS messages sent to this subscriber.
However, switching equipment providers, banks, telecom operators, messenger owners and other Internet service providers are also aware of this and are on the alert. For example, Internet service providers and banks use two-factor authentication. Mobile telecom operators use protection through SMS Home Routing. This method is used to counter attacks that request the information needed to deliver an incoming SMS message to a subscriber. Previously, in response to it, the subscriber identifier (IMSI) and the address of the node serving it (VLR) were sent. Now, each such request is sent to the SMS Home Routing system, which returns a non-existent subscriber identifier and its own address instead of the real VLR address in which the subscriber is registered. Thus, for requests from other networks, it is possible to completely hide the real identifiers of subscribers and the addresses of the network equipment at which they are registered.
For example, Internet service providers and banks use two-factor authentication. Mobile telecom operators use protection through SMS Home Routing. This method is used to counter attacks that request the information needed to deliver an incoming SMS message to a subscriber. Previously, in response to it, the subscriber identifier (IMSI) and the address of the node serving it (VLR) were sent. Now, each such request is sent to the SMS Home Routing system, which returns a non-existent subscriber identifier and its own address instead of the real VLR address in which the subscriber is registered. Thus, for requests from other networks, it is possible to completely hide the real identifiers of subscribers and the addresses of the network equipment at which they are registered.
In addition, a register of network equipment addresses is maintained, which is specially registered and configured. Therefore, in order to use SS7 at the network level, an attacker must at least be connected directly to the equipment of some telecom operator. But these are risks for such an operator, since its network will simply be blocked upon detection, and this threatens it with a loss of reputation and business. Therefore, in telecommunications networks this is not common. And since all these pseudo-systems of intruders in most cases appear to be foreign operators (they report that you are in international roaming), for your own reinsurance, it is enough for a subscriber in his home network to turn off international roaming on his phone.
But these are risks for such an operator, since its network will simply be blocked upon detection, and this threatens it with a loss of reputation and business. Therefore, in telecommunications networks this is not common. And since all these pseudo-systems of intruders in most cases appear to be foreign operators (they report that you are in international roaming), for your own reinsurance, it is enough for a subscriber in his home network to turn off international roaming on his phone.
Nuts are tightened, but…
Nevertheless, SS7 attacks continue. In December 2019, Group-IB's Cybercrime Investigation Department was contacted by several Russian entrepreneurs. Unknown people got access to their correspondence in Telegram. The victims used smartphones on iOS and Android, were subscribers of various federal operators. The attacks were instantaneous.
First, the user in Telegram from the official account of the messenger received a confirmation code for entering, which he did not request. Then an SMS with an activation code arrived, and almost immediately after it came a message about a successful login from a new device.
Then an SMS with an activation code arrived, and almost immediately after it came a message about a successful login from a new device.
Malefactors got into the account through the mobile Internet from IP-addresses from Samara.
Specialists did not find any spyware on the victims' smartphones. “In all cases, the attackers gained access to the victim’s messenger using SMS codes received when logging into the account from a new device,” is emphasized in the report.
How did the break-in take place? Experts say that when the messenger is activated on a new device, Telegram first sends a code through the official service channel to all other devices, and only then an SMS message is sent upon request. Malefactors ostensibly initiate such request and intercept SMS. With the code from the text message, they successfully log in to the messenger and get access to all files, photos and correspondence.
There are two important points in this story: the interception of SMS (which we talked about above and which they are fighting as best they can) and the lack of two-step authentication for the victims.
Two-step authorization
By default, authentication in Telegram occurs using a verification code. It is one-time and is sent either by SMS or as a message in the messenger if you try to log in from a new device. Telegram sometimes uses the services of mobile operators to send authorization codes. But more than five years ago, the messenger had an additional login step - a password that the user himself sets in the application.
Let's say you use the "cart" on your smartphone all the time, and then decide to enter the messenger through the web interface in your computer browser. You enter your phone number, and through the service channel of the messenger itself, from the official Telegram account, you receive a message with a confirmation code. After entering it in the browser, you have successfully logged in.
But if you have two-step authentication enabled, then after the confirmation code, you must also enter a password that only you know.
Experts advise: 2-Step Verification should be enabled in Telegram's privacy settings. In a recent incident with Tut.by employees, it was noted that it was enabled on one of the accounts. Someone was able to correctly enter the confirmation code, but did not cope with the additional password and did not get access to the account's correspondence.
In a recent incident with Tut.by employees, it was noted that it was enabled on one of the accounts. Someone was able to correctly enter the confirmation code, but did not cope with the additional password and did not get access to the account's correspondence.
- If you take the technical component, Telegram is very secure. They are great. But really, you should understand that you can get physical access to the device. In this case, the technological component of security will not help, - we quote Alexander Sushko, head of Group-IB in Belarus.
Many attackers install malware on devices. This can be a program that a person downloads himself, or infection through a phishing link. Such malware will allow intercepting correspondence, calls, and SMS.
In addition to malware, these can also be vulnerabilities in telecommunications networks. The same SS7, which allows you to intercept SMS. Knowing about this vulnerability, it is important to set up two-factor authentication with an additional password. It's more secure.
It's more secure.
If you have a European or Chinese SIM card linked to your account, it will be more difficult to access your account. But you need trusted people who will give you this access code when you re-authorize.
Two-step verification is enabled in the messenger's privacy settings. On iOS devices, it's called Cloud Password. This password can be linked to an email address, allowing you to retrieve it in case you forget it. But this is optional, the binding can be skipped. Thus, the Telegram password will be stored only in your head. This is probably a more reliable method if attackers are suddenly able to access your mail as well.
Experts from the telecom industry say that hacking through the SS7 protocol, if possible, is very difficult. Nevertheless, incidents with possible interception of SMS and hacking of Telegram occur. Now you know how to protect yourself. In order not to miss our new videos, subscribe to the YouTube channel , then it will be very interesting.