How to hack others facebook account
How to Hack Facebook Account Just by Knowing Phone Number
Jun 15, 2016Swati Khandelwal
Hacking Facebook account is one of the major queries on the Internet today.
It's hard to find — how to hack Facebook account or facebook messenger, but researchers found a way that can allow someone to hack Facebook account passwords with only the target's phone number and some resources.
Yes, your Facebook profile can be hacked, no matter how strong your password is or how much extra security measures you have taken. No joke!
Hackers with resources to exploit SS7 network can hack your Facebook login and all they need is your phone number.
The weaknesses in the part of global telecom network SS7 that not only let hackers and spy agencies listen to personal phone calls and intercept SMSes on a potentially massive scale but also let them hijack social media accounts to which you have provided your phone number.
SS7 or Signalling System Number 7 is a cell phone signaling protocol that is being used by more than 800 telecommunication operators worldwide to exchange information with one another, cross-carrier billing, enabling roaming, and other features.
However, an issue with the SS7 network is that it trusts text messages sent over it regardless of their origin. So, malicious hackers could trick SS7 into diverting text messages as well as calls to their own devices.
All they need is the target's phone number and some details of the target's device to initiate the silent snooping.
The researchers from Positive Technologies, who recently showed how they could hijack WhatsApp and Telegram accounts, now gave the demonstration of the Facebook hack using similar tricks, Forbes reported.
SS7 has long been known to be vulnerable, despite the most advanced encryption used by cellular networks. The designing flaws in SS7 have been in circulation since 2014 when the team of researchers at German Security Research Labs alerted the world to it.
Here's How to Hack Any Facebook Account:
The attacker first needs to click on the "Forgot account?" link on the Facebook.com homepage to reset your password. Now, when asked for a phone number or email address linked to the target account, the hacker needs to provide the legitimate phone number.
Now, when asked for a phone number or email address linked to the target account, the hacker needs to provide the legitimate phone number.
The attacker then diverts the SMS containing a one-time passcode (OTP) to their own computer or phone, and can gain access to the target's Facebook account.
The issue affects all Facebook users who have registered a phone number with Facebook and have authorized Facebook Texts.
Besides Facebook, researchers' work shows that any service, including Gmail and Twitter, that uses SMS to verify its user accounts has left open doors for hackers to target its customers.
Although the network operators are unable to patch the hole sometime soon, there is little the smartphone users can do.
- Do not link your phone number to social media sites, rather rely solely on emails to recover your Facebook or other social media accounts.
- Use two-factor authentication that does not use SMS texts for receiving codes.
- Use communication apps that offer "end-to-end encryption" to encrypt your data before it leaves your smartphone over your phone's standard calling feature.
However, the important thing to note is that the issue has actually nothing to do with Facebook security or other website's security, instead it is the weakness in the telecom network.
"Because this technique [SSL exploitation] requires significant technical and financial investment, it is a very low risk for most people," Facebook spokesperson told The Hacker News.
"As an added precaution, we recommend turning on two-factor authentication, called Login Approvals, in your Facebook security settings. Doing this will disable recovery via SMS on your account so even if someone has your phone number, they'll still need your password to access your account."
Update: If you think this technique is old and can not be used to hack your social media, bank or any online accounts, then you are mistaken. A real-world SS7 attack has been spotted this month when some unknown hackers exploited the design flaws in the Signaling System 7 (SS7) to drain victims' bank accounts.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
SHARE
Tweet
Share
Share
Share
Share on Facebook Share on Twitter Share on Linkedin Share on Reddit Share on Hacker News Share on Email Share on WhatsApp Share on Facebook Messenger Share on TelegramSHARE
Facebook account hacking, Facebook hacking, gmail hacking, hacking news, How to Hack Facebook, interception, Signaling System 7, sms hacking, SS7, SS7 Protocol, twitter hacking
How to Hack Facebook Accounts: 5 Common Vulnerabilities
Facebook is a free and popular social networking site that makes it easy for users to connect and share posts with their friends and family members. Since Facebook is a popular social media platform, there is an increased interest from cybercriminals to hack Facebook accounts.
This article will talk about the five common vulnerabilities and what you can do to prevent cybercriminals from hacking your Facebook accounts.
Facebook Hacks and Vulnerabilities:
- Weak Passwords
- Phishing Emails
- Man in The Middle (MITM)
- Remote Keyloggers
- Denial of Service (DoS)
1. Weak Passwords
Hackers can easily hack Facebook accounts by guessing or performing a brute force attack if the password is easy and commonly used such as a nickname, phone number, partner’s name, pet name, just to name a few. Once the hacker has obtained your password, they have the ability to do whatever they want with your account.
How to Protect Against Weak Passwords
Users should implement a strong password that combines numbers, symbols, space bars, and lower and uppercase letters. It is important that the password they create for their Facebook account is unique and not the same password that is used for their other social media or email accounts.
This would reduce the risk of your account from being compromised. A usual site to verify that your accounts are safe is HaveIBeenPwned. Here you can see if your credentials have been leaked to the public.
2. Phishing Emails
“Facebook will never ask you for your password in an email or send you a password as an attachment”
Phishing emails are an easy way for attackers to hack Facebook accounts. An attacker can create fake emails to make it look like they were sent from Facebook. These are some examples of what the emails may look like:
- Notifications about friend requests, messages, events, photos and videos
- False claims that you went against their Community Standards
- Warnings that something will happen to your account if you don’t update it or take a certain action
- Claims or offers that sound too good to be true (such as winning a Facebook lottery)
How to Protect Against Phishing Attacks
Users should be educated and informed on the characteristics of phishing emails in order to keep an eye out for them. Here is what you can do:
Here is what you can do:
- Do not click on any links or open any attachments from a suspicious email
- Do not respond to the suspicious emails especially ones that ask for your password, social security number, or credit card information
- Do no enter personal information from a pop-up screen (note: legit companies would never ask for personal information via a pop-up screen)
- Keep an eye out for misspellings in the contents of the email
3. Man In The Middle (MITM)
A man in the middle attack may occur when a user unknowingly connects to a fake WiFi connection. This is another technique hackers can use to hack Facebook accounts. Most of the time you may not be able to tell which WiFi is real or not because it is public and is normal to bring you to a login page where you are asked to enter in your email and a password before granted internet access. Again, without you knowing, the attacker has recorded this information and can test out these login credentials on other social media platforms.
How to Protect Against Man In The Middle Attacks
You should never connect your mobile device or laptop to a public WiFi network because they are not secure and are an easy way for hackers to obtain information. If you want to connect to public WiFi then I would recommend using a VPN with it to make sure that your connection is safe.
4. Remote Keyloggers
A hacker first needs to access your mobile device or laptop to install a piece of software to record whatever you type on your device. Once installed, anything that is typed (password, login credentials, bank information, etc.) will be recorded and can be viewed by the hacker. This is a hidden technique for an attacker to hack Facebook accounts. For example, if an attacker has somehow hacked into your laptop and installed a keylogger software, then anything you type will be recorded for the attacker. Not only would your Facebook credentials be recorded but also your bank credentials, email accounts, and whatever other accounts you have.
How to Protect Against Remote Keyloggers
- Do not use third party keyboard applications
- Do not open any attachments or click on links in the email message as the keylogger may be embedded in the attachment
- Install anti-spyware applications to help detect, disable, quarantine software-based keyboard loggers (Norton)
5. Denial of Service (DoS)
A denial of service attack “is a malicious attempt to affect the availability of a targeted system, such as a website or application, to legitimate end users” (AWS). Attackers will typically generate a large volume of packets or requests to overwhelm Facebook. When this type of attack occurs, users will have issues accessing Facebook and won’t be able to log in.
How to Protect Against Denial of Service Attacks
- Monitor the network so that you are aware of what normal incoming traffic looks like
- Implement web application firewall
- Understand common signs of a denial of service attacks so that you can mitigate the attack as early as possible
Final Thoughts on Facebook Hacks and How to Prevent Them
These are the five common vulnerabilities that hackers use to hack Facebook and how to protect against each vulnerability. There are definitely many more ways and even new methods that are not publicly known yet to hack Facebook accounts.
There are definitely many more ways and even new methods that are not publicly known yet to hack Facebook accounts.
Hackers are always one step ahead in finding new techniques where prevention might not be possible at first. Therefore, users and organizations (as the last vulnerability is targeted towards organizations) should make sure that they do everything they can to ensure that their account and site are secure.
Check out our podcast on big tech companies.
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act. nine0003
So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act. nine0003
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on. nine0003
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.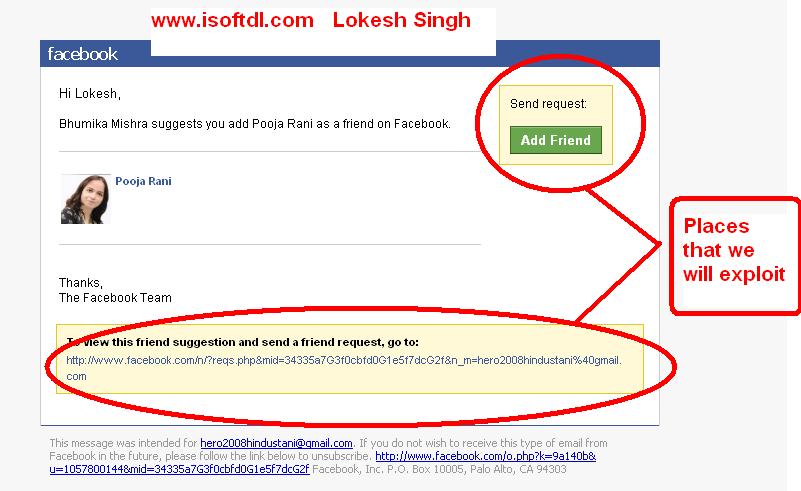
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password. nine0003
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It's possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account. nine0003
Now someone has discovered your oversight and logged into your account. nine0003
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there. nine0003
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing. nine0003
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings. This will reset the access tokens.
- Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them.
 If they managed to do this, change it back to yours. nine0052
If they managed to do this, change it back to yours. nine0052 - Set a new password that is strong and one that you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress. nine0052
Tips
Christmas and security
Many famous break-ins began during the Christmas holidays. A few simple tips will reduce your risk of becoming the next victim.
Is it safe to use Avast in 2023?
Avast solutions have a good reputation, but several incidents cast doubt on their reliability. We tell you whether you can trust Avast products.
We tell you whether you can trust Avast products.
Football cyberthreats
How to watch the World Cup and not become a victim of fraud.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site. I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons. nine0052
Found a way to hack into any Facebook account using a "hole" that is 10 years old
Security Security strategy User Internet Web Services
|
Share nine0003
 The flaw, which Facebook closed in early 2020, allowed it to seize control of any account on the social network and its friendly services.
The flaw, which Facebook closed in early 2020, allowed it to seize control of any account on the social network and its friendly services. Dangerous vulnerability
Security researcher Amol Baikar (Amol Baikar) has identified a dangerous vulnerability in Facebook's OAuth authorization protocol. It allows you to access any social network account, as well as other services that are logged in using Facebook. The specialist spoke about this in his personal blog, emphasizing that the described bug has existed for about 9 years.-10 years.
According to Baikar, the problem lies in the implementation of the "Login with Facebook" function, which uses the OAuth 2.0 authorization protocol to exchange authorization tokens between the social network site and other web resources. Thanks to this feature, Facebook account holders can freely use third-party Internet services that provide such an opportunity without additional registration.
The expert explained that an attacker could deploy a special website to intercept OAuth traffic and steal tokens that provide access to visitors' Facebook accounts. As a result, the "hacker" will be able to send messages, post in the feed, change account information, and perform any other actions on behalf of the victim. nine0003
In addition, the cybercriminal gets the opportunity to establish control over accounts on third-party resources, which can be used for authorization using Facebook. Many web services now provide this opportunity, including the social network Instagram, streaming services Netflix and Spotify, and the dating app Tinder.
Company response
Baikar informed Facebook about the discovered vulnerability on December 16, 2019. To his surprise, the company acknowledged the presence of the "hole" on the same day. What's more, she immediately released a fix. nine0003
Security researcher Amol Baikar found a way to hack any Facebook account using a decade-old flaw
However, later the researcher found errors in its implementation, about which he notified the company representatives on January 3, 2020. On January 10, Facebook eliminated the shortcomings identified by Baikar.
On January 10, Facebook eliminated the shortcomings identified by Baikar.
On February 20, the expert received a $55,000 reward from Facebook as part of the Bug Bounty program for his work.
Facebook incidents and leaks
Over the past few years, Facebook has repeatedly found itself at the center of various scandals due to a careless attitude to the privacy of social network users, as well as the presence of serious vulnerabilities in other company products.
Hit or miss: how communication with employees saves business in the face of a shortage of personnel
Digitalization
For example, in July 2019, a vulnerability was discovered in the mobile version of Instagram (part of the Facebook ecosystem) that allowed an attacker to reset the password for absolutely any account and gain full control over it. nine0003
In April 2019, Facebook was convicted that when registering on a social network, a user's password to his email address could be requested if the client's email service causes some suspicions in the system. The list of "suspicious" was also the popular Russian service "Yandex.mail".
In March 2019, it was discovered that tens of thousands of company employees could have access to other people's Facebook and Instagram pages, since the passwords of hundreds of millions of users were stored on the company's servers in clear text. Moreover, the social network officially recognized the existence of a problem only after a third-party information security specialist with connections within the company spoke about it on the Internet. nine0003
In September 2018, Facebook acknowledged the data breach of over 50 million account holders. The cause of the hack was a serious vulnerability in the Facebook code. It was eliminated as soon as possible, and law enforcement agencies were notified about the incident.
Nikita Vinogradov, FC Otkritie Bank: “Those who have long dealt with the issue of corporate technological sovereignty coped with the difficulties”
Security
In November 2018, it became known that the social network was unable to repel cybercriminals, as a result of which personal information about more than 120 million network users ended up in the hands of hackers.