How to hack into a whatsapp group
NSO Group WhatsApp hack victims speak out, from India to Rwanda
Around the world, governments are using surveillance tools they have purchased from Israeli spyware firm NSO Group — the infamous creator of Pegasus — to monitor and crack down on human rights defenders. Access Now and our partners have repeatedly called on NSO Group and its investors to stop providing its products to countries who use them as tools of oppression, but the company has failed to take any meaningful steps to address these harms.
Since 2016 — when UAE human rights activist Ahmed Mansoor first uncovered NSO’s Pegasus on his iPhone — it has been detected in at least 46 countries around the world. Reports from Access Now, Citizen Lab, and others all show that an alarming number of people targeted using Pegasus have been journalists, lawyers, and activists, whose only crime was speaking out against and reporting on the injustices in their home countries. Citizen Lab has identified more than 100 such victims in a hack targeting WhatsApp users. The platform has since sued NSO Group in U.S. court, claiming NSO illegally used WhatsApp’s servers to hack into the phones of 1,400 of its users. The legal battle, which started in October 2019, is now under review in the 9th Circuit Court of Appeals over the issue of jurisdiction.
Despite all the evidence, NSO has continuously denied knowing about these abuses and has insisted their priority is to fight crime and prevent terrorism. Instead of taking meaningful action, NSO has instead tried to improve its image by creating sham human rights policies and advisory boards, and by developing a COVID-19 tracking app.
Five individuals who suffered from the WhatsApp hack have stepped forward to tell their stories — sharing the important work they are doing to protect human rights in their communities, how their governments used NSO Group’s products to surveil them, and consequences they have faced as a result.
Read their personal narratives below. Help ensure these brave human rights defenders’ stories are heard and that NSO Group is brought to justice for its failure to protect dissenting voices from its harmful tools.
- Lawyer
- Journalist
- Opposition Leader
- Activist
- Community Organizer
| Bela Bhatia is an Indian human rights lawyer, activist, independent researcher, and writer. |
My name is Bela Bhatia. I live in Jagdalpur in Bastar district of Chhattisgarh state of India. I work here as a human rights lawyer and activist, independent researcher, and writer. Before shifting to live in Bastar in January 2015, I was an honorary professor at the Tata Institute of Social Sciences, Mumbai. My association with Bastar goes back to 2006. Bastar has been a site of a “war” between the Indian government and the Communist Party of India (Maoist) since 2005. Since then there have been scores of human rights violations involving the indigenous Adivasi residents of the villages of the war zone. I have been amongst other members of civil society who have documented, spoken out, and written against these excesses as well as represented victims in courts.
I believe I was targeted because the state and federal governments of India do not want individuals to witness or speak out against the impunity of the police and paramilitary while they carry out their plans to quell the Maoist movement with brutal force and illegal means. Besides issues related to the Maoist movement, there are other issues pertaining to governance and the democratic rights of citizens, especially Adivasis in this area — that comes under the Fifth Schedule of the Indian Constitution that allows them special protection — that are being trampled upon, for example, furthering the mining industry in the interests of private corporations without due process. The government is keen to discourage even nonviolent mobilization for upholding such democratic rights.
There has been continuous surveillance and harassment of independent observers and actors, whether local or visitors, in this area for many years, including local youth, especially educated youth, who have been harassed and arbitrarily arrested, social workers, journalists, lawyers, and academics who have been threatened, driven away, or framed under false charges.
Like others, I was also subjected to such surveillance, harassment, threats, and labelling — as a “Naxalite agent” and “urban Naxalite” — as well as attacks in diverse ways by police, paramilitary, and vigilante organizations during 2016-17. For example, an anonymous leaflet with my photo, labelling me as a Naxalite agent (an implicit incitement to violence), was circulated in the area by members of a hostile rally organized by a vigilante group in the village that I used to live in, in March 2016; my phone was snatched by a masked man when I was trying to report on a rally organized by police and vigilante groups in Jagdalpur, in September 2016; my effigy was burnt along with that of other activists by police in several district headquarters, in October 2016; and goons of a vigilante group attempted to threaten me in the night and attacked my house, a rented accommodation in a village, the following morning with the idea to evict me, in January 2017. Besides, I have been aware that my phone was most probably tapped and that my movements were often tracked.
Therefore, when I learnt from John Scott-Railton, a senior researcher at Citizen Lab, at the University of Toronto, that my phone had been hacked using spyware called Pegasus that was sold exclusively to governments by the Israeli cyber-warfare company NSO Group, I was not surprised. I saw that as a continuation of the older surveillance in a more sophisticated form.
The impact of these surveillance activities, culminating in the Pegasus operation, is that I am forced to work in an environment of suspicion and live a restricted life. Building trust among community members for any joint activity has become all the more difficult. Besides, I have not been able to live where I would have liked to, a village close to the town I live in now, where I was attacked in January 2017. I have also not been able to work in other capacities that I would have liked to; for example, I would have liked to have had some association with the university here, but university officials have also become wary of me.
Being targeted with international spyware has amplified all the earlier rumors and their possible consequences. The Pegasus operation has taken surveillance to a new level and made me even more controversial and vulnerable than I used to be. I also have to live with the constant apprehension of possible arrest based on false charges, as has already happened to several other activists in the country in recent times.
| Aboubakr Jamaï is a Moroccan journalist and a winner of the Committee to Protect Journalists’ International Press Freedom Award. |
For more than 10 years, I have been a journalist in Morocco. I founded and led two weekly magazines. Our work won international awards, chief among them the Committee to Protect Journalists’ International Press Freedom Award. After multiple bans, and trumped-up defamation cases resulting in huge fines, I was forced out of the country in 2007. In 2010, the publications went bankrupt after a state-led advertisement boycott. After leaving Morocco, I started a new career working as a consultant and teacher.
After leaving Morocco, I started a new career working as a consultant and teacher.
On two occasions in the last two years, confidential work I did for my client was leaked to the media close to the Moroccan regime. In the articles on my work, content stolen from my phone was used to smear professional acquaintances. While in Morocco, I always acted with the assumption that my phones were tapped by the state. Outside of Morocco, I hoped I could work and make a living without the Moroccan state snooping on me and jeopardizing my work relationship with my professional partners. Thanks to Citizen Lab investigations, I learned that my phone was infected with Pegasus spyware. My clients too knew about it and have not resorted to my services since then.
As a professor, I am in charge of the international relations departments of a France-based study abroad program. Most of our students are U.S. citizens. Part of my duties is to organize and lead travelling seminars in Morocco. Since the spying revelations, I worry about taking our students to Morocco.
Being spied on by an authoritarian state does not only spoil your professional relationships, it reduces your social circle too. You put at risk your relatives and friends by the mere fact of freely talking to them on the phone. They consequently tend to reduce their interactions with you. Most of my family lives in Morocco. Although I go back occasionally to my home country and see my relatives, most of my interactions with them are through the phone. Knowing that our conversations are snooped on is emotionally distressing for them and for me.
| Placide Kayumba is a Rwandan activist and a member of the opposition in exile. |
I’m quite sure I was targeted because I have been criticizing the government of Rwanda. This government is a dictatorship. You know exactly how the government of Rwanda works. When I was a student [in Belgium], we started a nonprofit organization (Jambo- asbl) that began to publish another narrative about Rwanda, the government, the regime. I was the first president of this organization. We started a website with information, I wrote some articles (Jambo News), and organized some conferences, demonstrations, to raise awareness in Rwanda and the “Great Lakes” region in general.
I was the first president of this organization. We started a website with information, I wrote some articles (Jambo News), and organized some conferences, demonstrations, to raise awareness in Rwanda and the “Great Lakes” region in general.
I was targeted by the government officials in 2015 or 2016. I also joined an opposition party with Victoire Ingabire. In 2018, I went on the board of the political party [the United Democratic Forces/ Forces Democratiques Unifiées – Inkingi, also known as FDU-Inkingi] and I continued to raise awareness and struggle for change from dictatorship to democracy.
During those years, some people were killed in Rwanda, including colleagues in the party. Anselme Mutuyimana was arrested in the north in Rwanda; some people found his body. The Vice President of the party, Boniface Twagirimana, was disappeared [from his prison cell] in October 2018. We still don’t know where he is but presume he’s dead. Eugene Ndereyimana is another member of the party who disappeared.
I have been criticizing [these disappearances] and am trying to get some support from human rights groups, like Amnesty and the UN human rights agency. We need help to find out what happened to those people, an independent investigation. The government won’t investigate this.
I was considered an enemy of the state. I’m not surprised that I was targeted by spyware [so that the government can] see who I was in touch with in Rwanda. Maybe those people who were killed were targeted because they were people in their party [the FDU]. I exchanged some messages [with them], nothing that could be considered criminal, and discussed with them what they can do to mobilize many people to get toward democracy, more liberty, and freedom of expression.
People’s houses were destroyed because they have no official land titles. To find a way to get the land, [they were] thrown on the streets, became homeless, [and given] no financial funds from the government. I was working on this with people in Rwanda. I was targeted because I was a human rights activist and they didn’t like it. They don’t like people who fight them. [Not] fight them, but try to get more freedom from them. I want them to be more open to other visions, other political actors.
I was targeted because I was a human rights activist and they didn’t like it. They don’t like people who fight them. [Not] fight them, but try to get more freedom from them. I want them to be more open to other visions, other political actors.
[I found out I was targeted after] I read an article in the Financial Times, and Rwanda was mentioned as a country that used this spyware. I could guess I was surely targeted. There’s a history of attacks on social networks from officials.
The confirmation that I was targeted came from WhatsApp, when WhatsApp started to work with Citizen Lab. Citizen Lab contacted me with some questions, to see if my phone had some abnormalities. They explained that there had been an attempt to attack my phone/device. Then they informed me that WhatsApp would send a message to inform all people who had been targeted. A few days later I received a message from WhatsApp. I don’t know if they [the government] took something from my phone. That’s the big question.
What’s harmful is that they know about your family, where your children go to school. When you exchange messages, you don’t know whether someone else could have [access to] them, [someone] that has criminal plans against you.
There are many impacts [that the targeting had on me]. My friends now don’t contact me easily. They think my phone is under surveillance. My social life was impacted.
My security – I cannot move freely where I want because they can locate where I am. These are the things you think about when these things happen to you. There are some places where I cannot go easily. Mainly Africa, as they can kill people easily in some countries in Africa. For my security, I cannot move except in some countries where I feel safe (U.S. and in Europe). Even in Belgium, we know there are some cells that are in Belgium.
Financially – it’s difficult to say. I have to adapt the way I communicate when I contact some people. I have to be sure it’s safe. I have to find ways to communicate outside usual channels. It can cost some money. I have to move to see people face-to-face to make sure I’m not being listened to. It’s another way of living.
It can cost some money. I have to move to see people face-to-face to make sure I’m not being listened to. It’s another way of living.
Professionally – if somebody can pay so much to control/monitor your communication, he’s ready to do much more. In time, they [the government] could put some information in my devices (my professional devices), and through that they can steal everything in my phone, they can record messages from themselves in my phone. I fear that.
When I learned that they had targeted my phone, I had no idea this could happen. Especially using WhatsApp, which everyone says is so secure.
Something in my mind changed the way I see technology. I don’t trust it anymore. For me everything can be targeted, and they can spy however they want.
For me, any application can have some vulnerability. In my mind, my assumption is that every channel of communication can be spied on. The only way to be sure [to be free of communications surveillance] is to go see someone in person without your phones in a place where there is no possibility [of being spied on].
[On achieving justice in] Rwanda – if I were to go to Rwanda, they will be happy to put me in jail or kill me. Because they kill people like Anselme Mutuyimana [who] had no place on the board in our party [he was an assistant to Victoire Ingabire]. I was the third Vice President [of the FDU]. If they could kill him like that, you can imagine what they would do if they found me. There’s no justice in Rwanda for anything. Even people who are now homeless because they [the government] decided to give their homes to rich friends. There’s no justice in Rwanda. It’s not safe for me there.
[On achieving justice in] Belgium – [I] could go for justice in Belgium. It’s more trustworthy. But for me, I’m very small. I’d be against a huge organization like NSO Group, which has many resources. It would be a waste of time for me and loss of money for me to go for justice in Belgium. For what result? Even if NSO Group is condemned here in Belgium, this won’t prevent Rwanda from trying to find another way to threaten or kill people like me.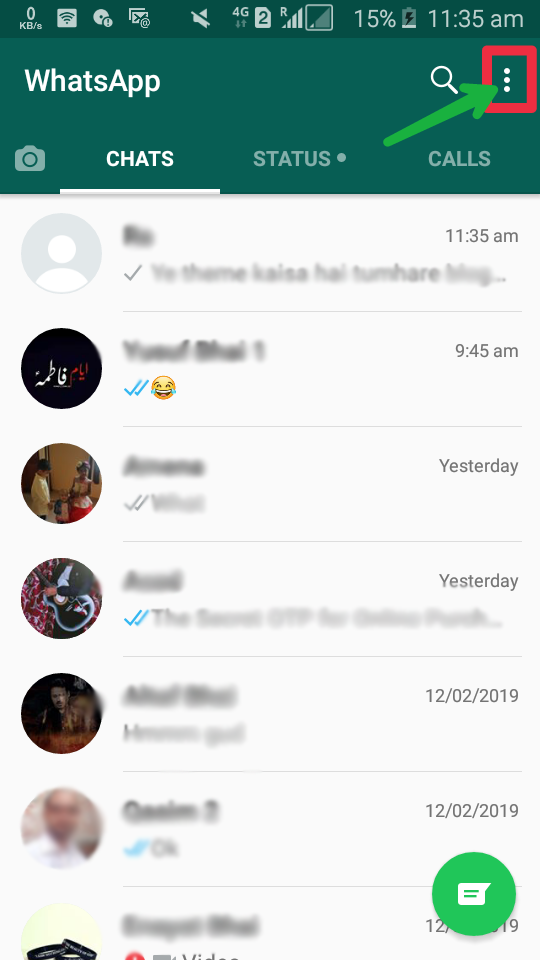 The result is not worth it to me.
The result is not worth it to me.
The real way to change things for me is to change the government in Rwanda. As long as RPF has resources from many countries in the E.U., U.S., U.K., or Congo, as long as they have enough resources to kill people wherever they want (Kenya, South Africa, Australia), [I won’t be safe]. Filing a case for justice here in Belgium, will cost so much for me. For them it’s just details.
Some years ago, we filed a case in the Arusha court [the African Court on Human and Peoples’ Rights (AfCHPR)], [in which] Rwanda was condemned in the case of Victoire Ingabire [Ingabire Victoire Umuhoza v. The Republic of Rwanda, App. No. 003/2014]. Her case in Rwanda was not just; she was jailed for eight years for nothing. Until now, Rwanda hasn’t done anything about that. Even the result in justice [is] not a solution for us. The solution is to get democracy and freedom in Rwanda; it’s the only way to stop the killing and looting, the only solution.
What I expect from the case in the U. S. — if it’s possible to get NSO Group to pay for what those governments did to activists, it would send a message to all companies that help dictatorships in criminal processes. I hope that the U.S. will consider that companies that spy on people should have no support. The U.S. government is one of the [biggest] contributors [of aid] to Rwanda.
S. — if it’s possible to get NSO Group to pay for what those governments did to activists, it would send a message to all companies that help dictatorships in criminal processes. I hope that the U.S. will consider that companies that spy on people should have no support. The U.S. government is one of the [biggest] contributors [of aid] to Rwanda.
| Fouad Abdelmoumni is a Moroccan human rights and democracy activist, who works with Human Rights Watch and Transparency International Morocco. |
I feel invaded, harassed, and severely violated. I am Fouad Abdelmoumni, a 62-year-old Moroccan man. I was subjected to torture, imprisonment, and several years of enforced disappearance, outside any proper legal framework, when I was just 20 years old. Yet I am experiencing as much more violent the current violation of my privacy, the distribution of information or intimate and sexual videos where I appear to be with another person, and the harassment and the threats against my loved ones.
I am a human rights and democracy activist (one of my roles is as a board advisor for Human Rights Watch – MENA), as well as a campaigner for Transparency International (a movement that fights corruption, for which I chaired the Moroccan Chapter a few years ago). I have no partisan political affiliation, although I regularly speak out against authoritarianism, corruption, and predation in my country and elsewhere.
I became one of the targets of Morocco’s repressive system a few years ago, but until now I had only ever been attacked in insidious ways. The pro-regime press, which specializes in slandering opponents and critical voices, regularly targets me, peppering its floods of lies with the odd fact taken from reality, which could only be obtained by powerful organizations that are able to access my private spaces, documents, and communications. In October 2019, I was contacted by the Citizen Lab, which, as part of a project commissioned by WhatsApp, had identified my telephone number among those hacked using spyware that makes it possible to access all the content and functions of my communication tools. In light of that, I posted the following statement on my Facebook page: “States, including the Moroccan State, behave like Mafias, but that can’t protect their oppression and corruption forever.” The following month, my sister received a call, purportedly from the police, informing her that I had been imprisoned, which was completely untrue. Together with seven other victims of the spying, I lodged an investigation request with the National Control Commission for the Protection of Personal Data (CNDP). The CNDP did nothing, arguing that it does not have jurisdiction over those types of matters (according to its president, who agreed to meet me but never provided the written response to our complaint that he promised). Then, in January 2020, one of the sites that does dirty work within the system of political repression, posted a video insulting and threatening me, as well as invading my private life. On February 13, 2020, six videos of several minutes each, showing my partner and I — or people who closely resemble us — in explicit sexual situations, were sent to dozens of people.
In light of that, I posted the following statement on my Facebook page: “States, including the Moroccan State, behave like Mafias, but that can’t protect their oppression and corruption forever.” The following month, my sister received a call, purportedly from the police, informing her that I had been imprisoned, which was completely untrue. Together with seven other victims of the spying, I lodged an investigation request with the National Control Commission for the Protection of Personal Data (CNDP). The CNDP did nothing, arguing that it does not have jurisdiction over those types of matters (according to its president, who agreed to meet me but never provided the written response to our complaint that he promised). Then, in January 2020, one of the sites that does dirty work within the system of political repression, posted a video insulting and threatening me, as well as invading my private life. On February 13, 2020, six videos of several minutes each, showing my partner and I — or people who closely resemble us — in explicit sexual situations, were sent to dozens of people. In parallel, I have been subjected to severe harassment by services of the administration, including exorbitant tax audits and cancellation of decisions awarding investment grants for a value of more than USD 30,000. Then, in October 2020, further attacks in the gutter press pried into not only my private life, but also that of other people whose only crime was to be friends of mine, going as far as publishing confidential information about the family status of an 11-year-old child, even revealing his identity.
In parallel, I have been subjected to severe harassment by services of the administration, including exorbitant tax audits and cancellation of decisions awarding investment grants for a value of more than USD 30,000. Then, in October 2020, further attacks in the gutter press pried into not only my private life, but also that of other people whose only crime was to be friends of mine, going as far as publishing confidential information about the family status of an 11-year-old child, even revealing his identity.
I am someone who refuses to act in the shadows and I aim to never say anything in confidence that I wouldn’t be prepared to defend in front of any audience. But that certainly doesn’t mean that I accept others interfering in my private life or having my privacy or that of the people with whom I keep company exposed to voyeurism. It should be underlined that I live in Morocco, a country where, by law, prison sentences can be handed down for extramarital sex and where society is very intolerant about sexual freedom, particularly for women.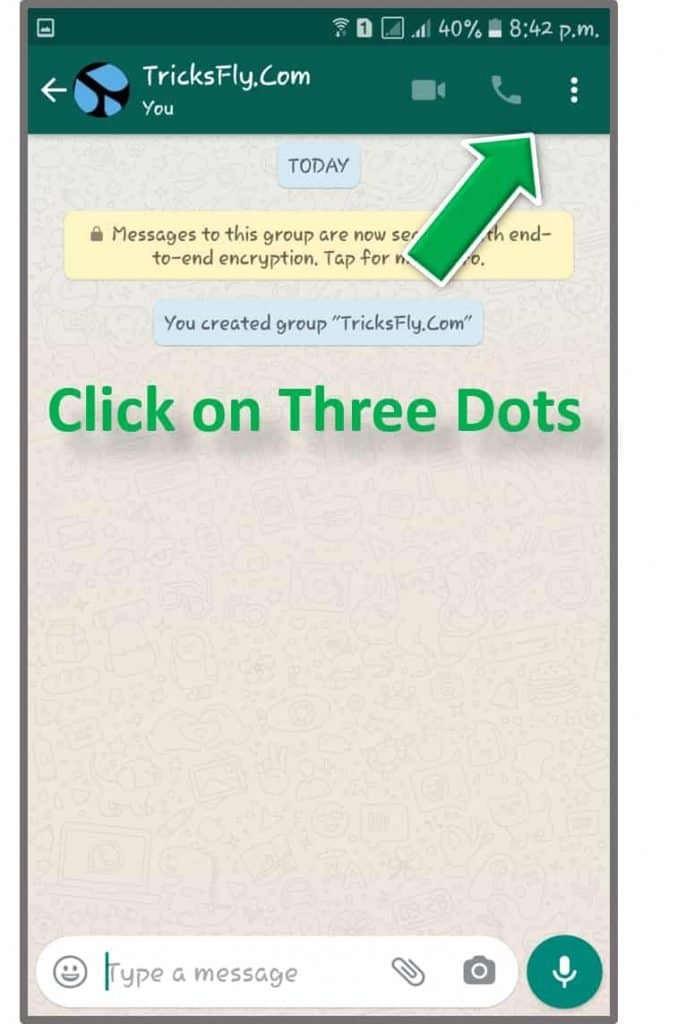
The details that I am recounting here are not linked only to the hacking of my phone, although that is a key aspect of the system of espionage and Mafia-style harassment to which myself and others are being subjected. I have always accepted the risk that microphones and cameras could be installed in places where I might think I am in private. But until a year ago, I still believed that the Moroccan regime was not so crooked that it would use those recordings to blackmail its opponents and terrorize critical voices. I certainly didn’t think that it would expose itself so directly, knowing that no one will believe that the meddling, recordings, campaigns of denigration, and harassment in various forms are not deliberate, well-orchestrated, and determined action at very high levels of the Moroccan State. Today, certain actions reveal just how awful those behaviors are and make it possible to publicly condemn the perpetrators. I hope that credible judicial systems will take up this task, for my dignity and that of the other people who have been attacked as collateral victims, so that elites in Morocco and around the world are no longer in terror of having their private lives and sex lives divulged.
PS: In 1984, toward the end of my second year of “incommunicado” disappearance, totally isolated from the world, handcuffed and blindfolded for days and months on end, a subcommittee of the United States Senate received the Ambassador of Morocco in preparation for King Hassan II’s visit to the U.S. Amnesty had submitted my case to some of the senators who asked what had happened to me. The ambassador replied that it was all a fabrication and invited any of the senators to accompany him to Morocco, saying that he would take them to my house to have tea together. He immediately informed the Moroccan Ministry of Foreign Affairs about the exchange, which referred the matter to the Ministry of Justice. The Attorney General of the King contacted the heads of the police, who told him that they were very happy that my case was finally being recalled, as they had absolutely nothing against me and had just been waiting for the green light from the palace to release me. As my father was a senior official in the Ministry of Justice, his colleagues hurried to give him the good news. A few days later, the official, written response from the police was received by the Ministry of Justice: “We have had no information about Mr. Fouad Abdelmoumni for years and do not know where he is…”
A few days later, the official, written response from the police was received by the Ministry of Justice: “We have had no information about Mr. Fouad Abdelmoumni for years and do not know where he is…”
| Father Pierre Marie-Chanel Affognon is a Togolese Catholic priest and the founder of a movement to promote constitutional, institutional, and electoral reform in Togo. |
[I found out I was targeted because] WhatsApp brought it to my attention; Citizen Lab in Canada contacted me following the WhatsApp message and confirmed it, and the facts strictly about my private life as well as other people’s [lives] have been mentioned in truncated form.
It is difficult to describe [the impact the targeting had on me] and painful to relate repeatedly. In any case, it is exactly like being undressed by someone in public, stripped naked, and you are powerless before an invisible hand and a terrifying faceless force.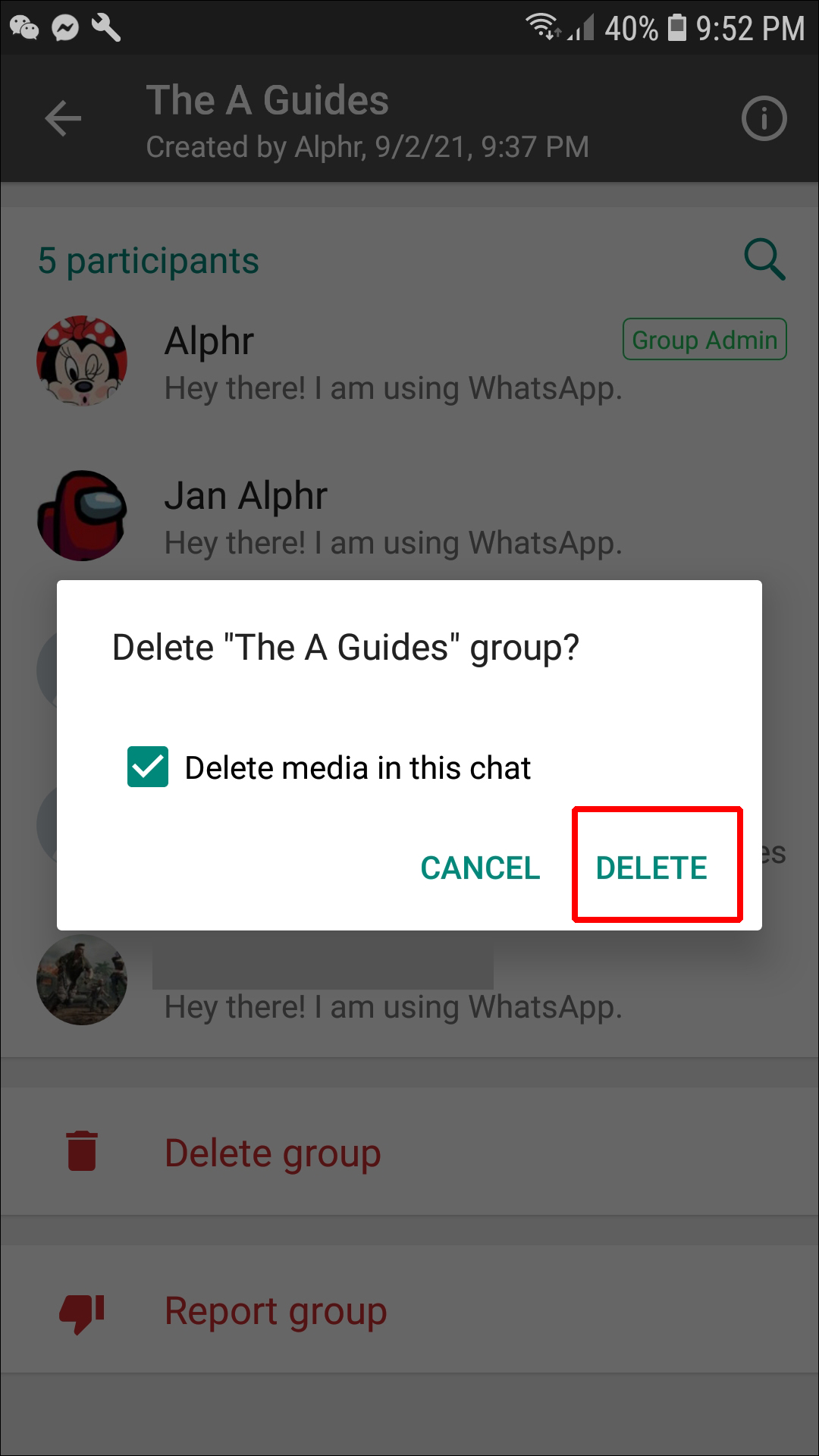 It is also an enormous shock when one considers the public money spent acquiring the Israeli software whilst in my country, Togo, there is destitution everywhere.
It is also an enormous shock when one considers the public money spent acquiring the Israeli software whilst in my country, Togo, there is destitution everywhere.
It is impossible to get justice in Togo. Togo has a regime which on the face of it is democratic. There is no justice possible in this matter because the judges are afraid to state what the law is. But I, I rely on God and on the organizations defending human rights in my country and internationally to put an end to these grave deviations which destroy democracy and the rule of law.
We thank Human Rights Watch, Internet Freedom Foundation, Committee to Protect Journalists, and others who helped bring to light these stories, but most importantly, the courageous survivors of the NSO hacking themselves.
Researchers found a way into WhatsApp group chats — but Facebook says it’s not a problem
Skip to main content
The VergeThe Verge logo.The Verge homepage
The VergeThe Verge logo.
- Tech/
- Security/
/
Anyone with control of WhatsApp servers can infiltrate group chats
By Shannon Liao / @Shannon_Liao
|
Share this story
Photo by Jaap Arriens/NurPhoto via Getty Images
German cryptographers have found a way to infiltrate WhatsApp’s group chats despite its end-to-end encryption.
Researchers announced they had discovered flaws in WhatsApp’s security at the Real World Crypto security conference in Switzerland, Wired reports. Anyone who controls the app’s servers could insert new people into private group chats without needing admin permission.
Once a new person is in, the phone of each member of that group chat automatically shares secret keys with that person, giving them full access to all future messages, but not past ones. It would appear as if the new member had the permission of the admin to join.
It would appear as if the new member had the permission of the admin to join.
“The confidentiality of the group is broken as soon as the uninvited member can obtain all the new messages and read them,” Paul Rösler, one of the researchers told Wired. The researchers recommend in their paper that summarizes their findings that users who rely on absolute privacy should stick to Signal or individual private messaging.
On the surface level, WhatsApp, which is owned by Facebook, looks to have a pretty big security flaw. But how easy can it be to gain access to the WhatsApp servers? The WhatsApp servers can only be controlled by staff, governments who legally demand access, and high-level hackers.
Facebook’s Chief Security Officer Alex Stamos responded to the report on Twitter, saying, “Read the Wired article today about WhatsApp – scary headline! But there is no [sic] a secret way into WhatsApp groups chats.”
Stamos objected to the report, stating that there are multiple ways to check and verify the members of a group chat. He argued that since all members of a group chat can see who joins a chat, they’ll be notified of any eavesdroppers. It’s also worth asking what a redesigned, secure WhatsApp would look like without this flaw. According to Stamos, if the app were to be redesigned, that would diminish how easy it is to use.
He argued that since all members of a group chat can see who joins a chat, they’ll be notified of any eavesdroppers. It’s also worth asking what a redesigned, secure WhatsApp would look like without this flaw. According to Stamos, if the app were to be redesigned, that would diminish how easy it is to use.
Moxie Marlinspike, a security researcher who developed Signal, which licenses its protocol to WhatsApp, said that the current app design is reasonable, and that the report only sends a message to others not to “build security into your products, because that makes you a target for researchers, even if you make the right decisions.”
Most Popular
Today I learned the Xbox can run Nintendo GameCube and Wii games
Amazon launches a $5 monthly subscription for unlimited prescription medications
We are now 90 seconds to our doom
Sony and Honda’s EV goes where the Apple Car never did
Rick and Morty will continue, but without Justin Roiland
More from Tech
BP makes an order for EV charging stations from US-based Tritium
Netflix’s paid password sharing to roll out ‘more broadly’ in the coming months
Samsung Display shows off a new folding phone hinge that can rotate 360 degrees
Twitter officially bans third-party clients with new developer rules
7 Ways to Hack WhatsApp Chats and How to Avoid Them
Do you think Encrypting WhatsApp Chats is Enough to Keep Your Chats Safe? Think again!
What's going on This is a popular messaging application that has become an integral part of our life as a communication channel. But hacking whatsapp conversations on your own is probably everyone's worst nightmare and you can avoid it by knowing the methods that can be used to hack whatsapp chats and taking precautions. nine0003
But hacking whatsapp conversations on your own is probably everyone's worst nightmare and you can avoid it by knowing the methods that can be used to hack whatsapp chats and taking precautions. nine0003
Top 7 Methods Used to Hack WhatsApp Chats
1. Exploiting weaknesses
2. whatsapp web
How to prevent whatsapp exploit online?
3. Export chat history to email.
4. Access to chat backups.
5. Search for media files
How to prevent interception of media files in WhatsApp?
6. Method of plagiarism.
7. Use of third party spyware. nine0003
Prevent whatsapp messages being hacked
Top 7 Methods Used to Hack WhatsApp Chats
1. Exploiting Weaknesses
From time to time, new security holes appear that can be abused to hack WhatsApp chats. Some of the common WhatsApp vulnerabilities that have caused chaos in the past year are attacks. Pegasus vocals و Remote code execution via GIF .
Pegasus vocals و Remote code execution via GIF .
The Pegasus Voice Call attack allowed hackers to gain access to a device by simply making a WhatsApp voice call to their target. Even if the target does not answer the call, the attack may continue and the target may not realize that they have malware installed on their device. nine0003
While another vulnerability included malicious GIFs that, when viewed by the victim, allowed attackers to capture their WhatsApp chat history.
Although these vulnerabilities have been fixed, there is always the possibility of a new one, and as long as these unknown vulnerabilities remain in nature. Thus, there is always a security risk.
Tip: Always keep your WhatsApp up to date as the development team continues to release new patches to fix these vulnerabilities. And if you haven't updated WhatsApp for a long time, I recommend you do it right now! nine0003
2.
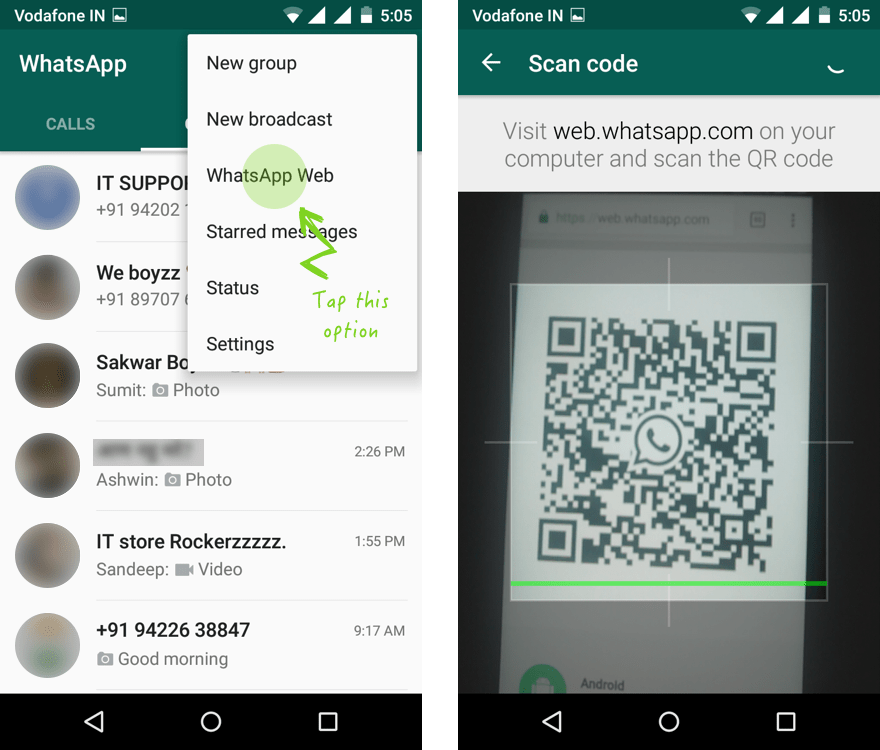
 WhatsApp Web
WhatsApp Web WhatsApp Web This is a feature that allows you to access the messaging application on a desktop browser. You can send and receive texts, images, videos and files through it. Your conversations as well as media files remain fully synchronized between your mobile device and desktop computer. This means that any action you perform on one of the devices is reflected on the other device. nine0003
However, this feature also poses a security risk. Although you need to authorize WhatsApp Web on PC by scanning the QR code on the WhatsApp mobile app, once you authorize your desktop device, it continues to provide access to WhatsApp chat via PC.
So if you allow someone else to access this computer with authorized access to your WhatsApp Web account, that person can unblock https://web.whatsapp.com in the browser and all your conversations will be visible to that person. nine0003
From there, the person can either export chats or take screenshots of them, hacking into your WhatsApp chat and violating your privacy.
How to prevent WhatsApp exploit on the network?
Here are a few things you can do to keep your WhatsApp Web chats secure:
- Never activate WhatsApp Web on a computer that others have access to. If you have to do this in a necessary situation, remember to log out of your account. To log out of your WhatsApp account, simply click on the vertical button with three dots and select "Log out" as shown in the image below. nine0074
- In addition, you can choose not to click on the "Keep me logged in" option that appears when you are about to sign in to WhatsApp on the web. This way, WhatsApp will automatically log you out every time you end your session.
- When the WhatsApp web app is active on your device, your mobile app will always notify you in the notification bar of your smartphone. So if you see this message below, quickly log out from all devices by opening the WhatsApp app on your phone > More options > WhatsApp Web > Log out from all devices > Sign out.
 nine0074
nine0074
3. Export chat history to email.
This method is similar to the previous one and requires physical access to your device in order to hack WhatsApp chats. This method takes less than a minute and all you need is to secretly access your device by tricking you or taking advantage of the fact that your device was left unlocked.
To export WhatsApp chats, you just need to open WhatsApp, click on more options (in the upper right corner) and select the option to export the chat and send all chats to an email address where you can access it later. nine0003
Tip: Always keep your device secure with a PIN or fingerprint so no one snoops on your conversations. If you need to give your device to someone, be sure to use WhatsApp's App Locker to keep it safe.
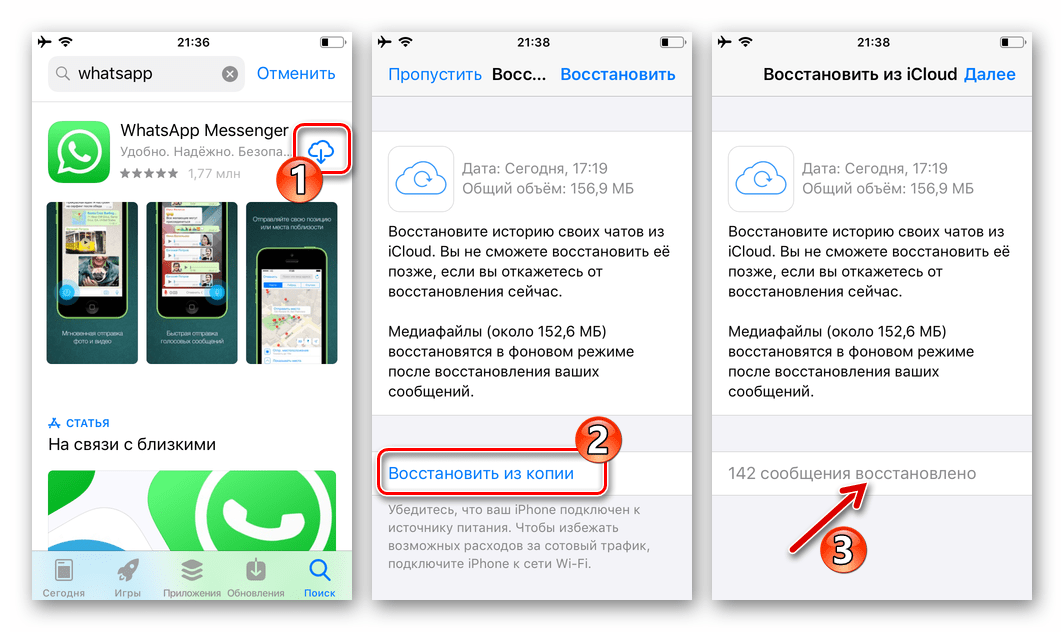
4. Access to chat backups.
Note that WhatsApp only provides end-to-end encryption on its platform. This means that the moment you leave WhatsApp conversations, you lose the encryption.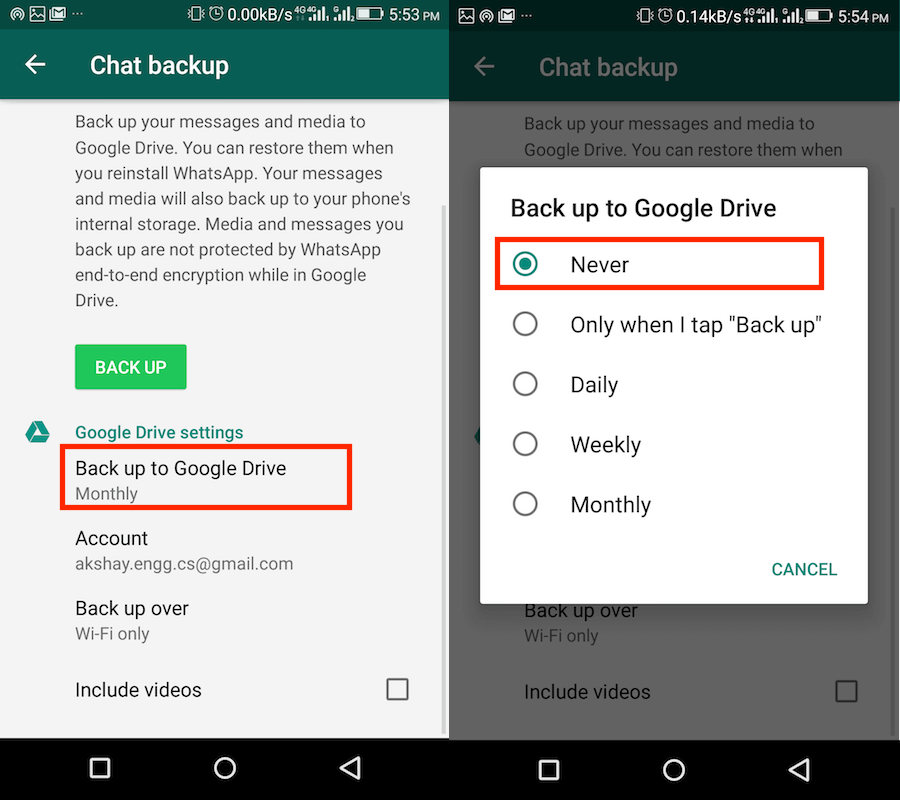 nine0003
nine0003
If you have enabled the ability to back up chats and save a copy of the conversation to Google Drive or iCloud, remember that these messages are not encrypted and can be easily accessed by other users if they manage to hack into or access your Gmail or iCloud. Account.
Tip: Personally, I wouldn't recommend storing chat backups in the cloud just because of the security risks. Even if you have to do this because you need to save important conversations, I suggest that you be more careful about keeping your cloud account secure by using strong passwords and not sharing them with anyone. nine0003
5. Search for media files
WhatsApp keeps your messages encrypted during transmission, but once the media file reaches your phone, this cannot be guaranteed. Media Hacking is a vulnerability in which an attacker exploits WhatsApp's way of obtaining media files such as photos or videos and writing those files to the device's external storage.
Media hacking can be done by installing malicious malware hidden inside an apparently harmless application. This malware can track incoming WhatsApp files. So when a new file arrives, the malware can replace the real file with a fake one, and it can be used to trick people or just snoop on their conversations. nine0003
How can I prevent WhatsApp from intercepting media files?
To prevent your WhatsApp media from being hacked, go to Settings > Chat Settings > option Save to Gallery and turn off launch it .
This will prevent your WhatsApp chats from being hacked.
6. Plagiarism method.
Using the spoofing method, WhatsApp chats can be hacked without physical access to the device, making them dangerous and difficult to prevent. While this is a difficult task, it is not entirely impossible. nine0003
In this method, the attacker must find the MAC address for the target smartphone. They can then use Busy Box and a terminal emulator on their smartphones to change the Wi-Fi MAC address on their device to that of the target device.
They can then use Busy Box and a terminal emulator on their smartphones to change the Wi-Fi MAC address on their device to that of the target device.
After that, they install WhatsApp and enter the phone number of the target device. They then receive a verification code on the target device to sign in. Once they receive the verification code, they use it to log into the target's WhatsApp account and remove the verification code so that the victim cannot find it. nine0003
However, one of the red flags could be that WhatsApp on the victim's device will be logged out when the hacker logs in. But, unfortunately, the damage may already have been done by then.
7. Use of third party spyware.
There are a number of cellular monitoring applications available, such as EvaSpy or Spyzie, which are specifically designed to monitor WhatsApp chats and other messaging applications. For this method to work, someone needs to install this app on your phone, gaining physical access to it and granting access to track your conversations. nine0003
nine0003
Some of these spy apps offer additional features such as live listening, screen recording, keyboard recording, camera control, screenshots, and chat recording.
You can go up and select spyware that hacks into WhatsApp chats remotely. Some of the well known names are POCWAPP and WSP 3.0 - WhatsApp Scan Pro. Now these apps are paid and available on the DarkNet, so they are not used often, but that doesn't change the fact that tools are available that can violate your privacy. nine0003
Tip: To avoid becoming a victim of spyware, do not install apps from unverified sources and be careful about the type of apps you have installed on your phone. If you see any application that you didn't install yourself or notice any suspicious behavior in it, I recommend that you uninstall it immediately.
Prevent WhatsApp Messages from being Hacked
These were some of the ways to hack your WhatsApp chats. I hope this also helps you avoid falling victim to any of these methods. nine0003
nine0003
In the meantime, if you have anything else to add or any other question, feel free to contact us via comments and email.
7 Ways to Hack Whatsapp Chats and How to Avoid Them
Do you think encrypting WhatsApp chats is enough to keep your chats secure? Think again!
What's going on This is a popular messaging application that has become an integral part of our life as a communication channel. But hacking whatsapp conversations on your own is probably everyone's worst nightmare and you can avoid it by knowing the methods that can be used to hack whatsapp chats and taking precautions. nine0003
Top 7 Methods Used to Hack WhatsApp Chats
1. Exploiting weaknesses
2. whatsapp web
How to prevent whatsapp exploit online?
3. Export chat history to email.
4. Access to chat backups.
5. Search for media files
How to prevent interception of media files in WhatsApp?
6. Method of plagiarism.
Method of plagiarism.
7. Use of third party spyware. nine0003
Prevent whatsapp messages being hacked
Top 7 Methods Used to Hack WhatsApp Chats
1. Exploiting Weaknesses
From time to time, new security holes appear that can be abused to hack WhatsApp chats. Some of the common WhatsApp vulnerabilities that have caused chaos in the past year are attacks. Pegasus vocals و Remote code execution via GIF .
The Pegasus Voice Call attack allowed hackers to gain access to a device by simply making a WhatsApp voice call to their target. Even if the target does not answer the call, the attack may continue and the target may not realize that they have malware installed on their device. nine0003
While another vulnerability included malicious GIFs that, when viewed by the victim, allowed attackers to capture their WhatsApp chat history.
Although these vulnerabilities have been fixed, there is always the possibility of a new one, and as long as these unknown vulnerabilities remain in nature. Thus, there is always a security risk.
Thus, there is always a security risk.
Tip: Always keep your WhatsApp up to date as the development team continues to release new patches to fix these vulnerabilities. And if you haven't updated WhatsApp for a long time, I recommend you do it right now! nine0003
2. WhatsApp Web
WhatsApp Web This is a feature that allows you to access the messaging application on a desktop browser. You can send and receive texts, images, videos and files through it. Your conversations as well as media files remain fully synchronized between your mobile device and desktop computer. This means that any action you perform on one of the devices is reflected on the other device. nine0003
However, this feature also poses a security risk. Although you need to authorize WhatsApp Web on PC by scanning the QR code on the WhatsApp mobile app, once you authorize your desktop device, it continues to provide access to WhatsApp chat via PC.
So if you allow someone else to access this computer with authorized access to your WhatsApp Web account, that person can unblock https://web. whatsapp.com in the browser and all your conversations will be visible to that person. nine0003
whatsapp.com in the browser and all your conversations will be visible to that person. nine0003
From there, the person can either export chats or take screenshots of them, hacking into your WhatsApp chat and violating your privacy.
How to prevent WhatsApp exploit on the network?
Here are a few things you can do to keep your WhatsApp Web chats secure:
- Never activate WhatsApp Web on a computer that others have access to. If you have to do this in a necessary situation, remember to log out of your account. To log out of your WhatsApp account, simply click on the vertical button with three dots and select "Log out" as shown in the image below. nine0074
- In addition, you can choose not to click on the "Keep me logged in" option that appears when you are about to sign in to WhatsApp on the web. This way, WhatsApp will automatically log you out every time you end your session.
- When the WhatsApp web app is active on your device, your mobile app will always notify you in the notification bar of your smartphone.
 So if you see this message below, quickly log out from all devices by opening the WhatsApp app on your phone > More options > WhatsApp Web > Log out from all devices > Sign out. nine0074
So if you see this message below, quickly log out from all devices by opening the WhatsApp app on your phone > More options > WhatsApp Web > Log out from all devices > Sign out. nine0074
3. Export chat history to email.
This method is similar to the previous one and requires physical access to your device in order to hack WhatsApp chats. This method takes less than a minute and all you need is to secretly access your device by tricking you or taking advantage of the fact that your device was left unlocked.
To export WhatsApp chats, you just need to open WhatsApp, click on more options (in the upper right corner) and select the option to export the chat and send all chats to an email address where you can access it later. nine0003
Tip: Always keep your device secure with a PIN or fingerprint so no one snoops on your conversations. If you need to give your device to someone, be sure to use WhatsApp's App Locker to keep it safe.
4.
 Access to chat backups.
Access to chat backups. Note that WhatsApp only provides end-to-end encryption on its platform. This means that the moment you leave WhatsApp conversations, you lose the encryption. nine0003
If you have enabled the ability to back up chats and save a copy of the conversation to Google Drive or iCloud, remember that these messages are not encrypted and can be easily accessed by other users if they manage to hack into or access your Gmail or iCloud. Account.
Tip: Personally, I wouldn't recommend storing chat backups in the cloud just because of the security risks. Even if you have to do this because you need to save important conversations, I suggest that you be more careful about keeping your cloud account secure by using strong passwords and not sharing them with anyone. nine0003
5. Search for media files
WhatsApp keeps your messages encrypted during transmission, but once the media file reaches your phone, this cannot be guaranteed.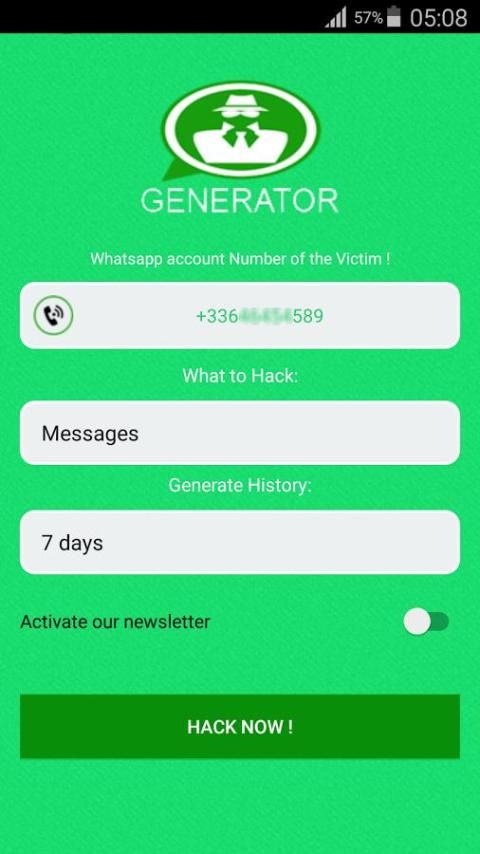 Media Hacking is a vulnerability in which an attacker exploits WhatsApp's way of obtaining media files such as photos or videos and writing those files to the device's external storage.
Media Hacking is a vulnerability in which an attacker exploits WhatsApp's way of obtaining media files such as photos or videos and writing those files to the device's external storage.
Media hacking can be done by installing malicious malware hidden inside an apparently harmless application. This malware can track incoming WhatsApp files. So when a new file arrives, the malware can replace the real file with a fake one, and it can be used to trick people or just snoop on their conversations. nine0003
How can I prevent WhatsApp from intercepting media files?
To prevent your WhatsApp media from being hacked, go to Settings > Chat Settings > option Save to Gallery and turn off launch it .
This will prevent your WhatsApp chats from being hacked.
6. Plagiarism method.
Using the spoofing method, WhatsApp chats can be hacked without physical access to the device, making them dangerous and difficult to prevent. While this is a difficult task, it is not entirely impossible. nine0003
While this is a difficult task, it is not entirely impossible. nine0003
In this method, the attacker must find the MAC address for the target smartphone. They can then use Busy Box and a terminal emulator on their smartphones to change the Wi-Fi MAC address on their device to that of the target device.
After that, they install WhatsApp and enter the phone number of the target device. They then receive a verification code on the target device to sign in. Once they receive the verification code, they use it to log into the target's WhatsApp account and remove the verification code so that the victim cannot find it. nine0003
However, one of the red flags could be that WhatsApp on the victim's device will be logged out when the hacker logs in. But, unfortunately, the damage may already have been done by then.
7. Use of third party spyware.
There are a number of Cell Monitoring Applications For example, EvaSpy or Spyzie are available, specially designed to monitor WhatsApp chats and other messaging applications. For this method to work, someone needs to install this app on your phone, gaining physical access to it and granting access to track your conversations. nine0003
For this method to work, someone needs to install this app on your phone, gaining physical access to it and granting access to track your conversations. nine0003
Some of these spy apps offer additional features such as live listening, screen recording, keyboard recording, camera control, screenshots, and chat recording.
You can go up and select spyware that hacks into WhatsApp chats remotely. Some of the well known names are POCWAPP and WSP 3.0 - WhatsApp Scan Pro. Now these apps are paid and available on the DarkNet, so they are not used often, but that doesn't change the fact that tools are available that can violate your privacy. nine0003
Tip: To avoid becoming a victim of spyware, do not install apps from unverified sources and be careful about the type of apps you have installed on your phone. If you see any application that you didn't install yourself or notice any suspicious behavior in it, I recommend that you uninstall it immediately.
Prevent WhatsApp Messages from being Hacked
These were some of the ways to hack your WhatsApp chats.