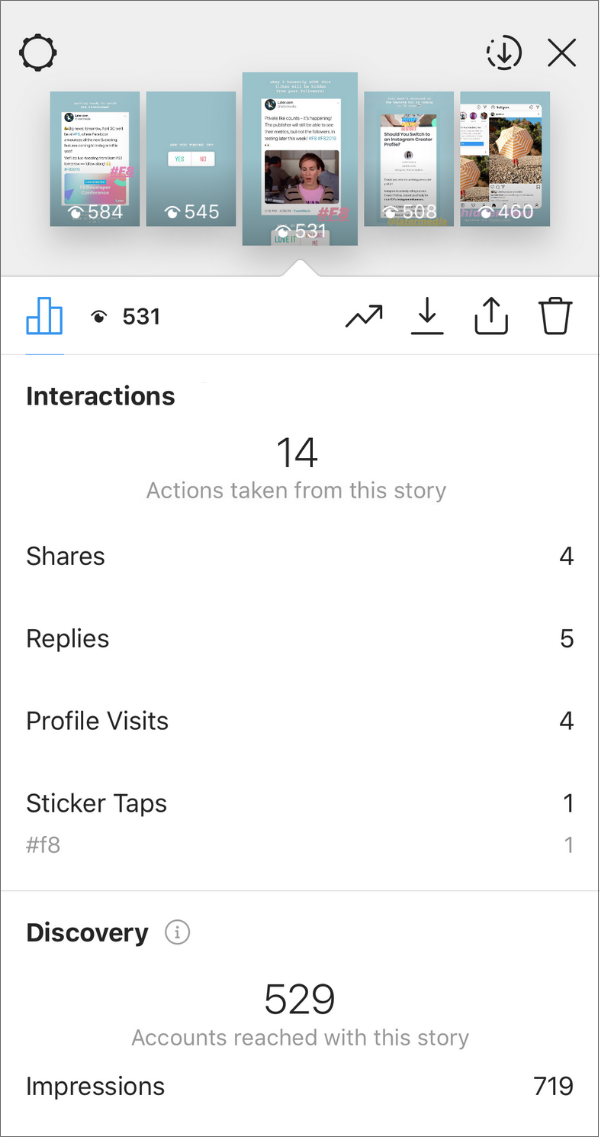
How to hack instagram using rainbow tables
How to Create & Use Them to Crack Passwords « Null Byte :: WonderHowTo
- By Alex Long
More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.
Passwords are normally stored in one-way hashes. When a password is created, the user types the password in what is called "plain text", since it is in a plain, unhashed form. However, after a password is made, the computer stores a one-way hash of the password that obfuscates it. Hashes are made to be one-way, which means algorithmic reversal is impossible. This means we have to crack those hashes!
Normally, when you crack a password hash, your computer computes a word, generates the hash, then compares to see if there is a match. If there is, the password is correct; if not, it will keep guessing. Rainbow tables work on the principle of a time-memory trade-off. This means that hashes are pre-generated by a computer and stored in a large rainbow table file with all of the hashes and words that correspond to them. This method works especially well for people with slow processors, since you don't have to compute much. Rainbow cracking can greatly reduce the amount of time it takes to crack a password hash, plus you can keep the tables, so you only have to generate them once!
Requirements
- Windows, Mac OSX, or Linux OS
- Admin, or root access
Step 1 Download & Install RainbowCrack
Text in bold means it is a terminal command (NT, OSX, or *nix). However, for this step, all commands in bold are for Linux only. The other operating systems use a GUI.
However, for this step, all commands in bold are for Linux only. The other operating systems use a GUI.
RainbowCrack is the tool that we are going to be using to generate and use rainbow tables.
- Download RainbowCrack.
- Extract the archive (Windows and Mac users extract via GUI).
tar zxvf <rainbowcrack> - Change to the new directory that has been made from extracting RainbowCrack.
cd <new dir> - Configure the installation.
./configure - Now, compile the source code for installation.
make && sudo make install
Step 2 Generate a Rainbow Table and Crack with It
Now, lets generate a table that consists of all the alpha-lowercase and numeral characters. We want these to use the MD5 hash algorithm and be between 4-6 characters. All OS users must open a terminal, or a command prompt and be located in the RainbowCrack working directory.
- In your working directory, issue the following command to start table generation.
rtgen md5 loweralpha-numeric 1 7 0 3800 33554432 0 - Sort the tables so the processor can access them quicker. The table files will be in the current directory. Run the following command on each of the files in the directory ending in *.rt.
rtsort <*.rt file>
This will take about 6 hours to generate on a single core processor. After you generate the table, let's practice using it on a word.
- Let's hash the word "burger" with the MD5 algorithm and then use our tables to crack it. Notice the b is in lowercase. Here is our result: 6e69685d22c94ffd42ccd7e70e246bd9
- Crack the hash with the following command, along with the path to your file.
rcrack <path-to-rainbow-table.rt> -h 6e69685d22c94ffd42ccd7e70e246bd9
It will return your hash. You'll see it is a lot faster than if you were try to bruteforce the six character hash.
You'll see it is a lot faster than if you were try to bruteforce the six character hash.
If you have any questions or want to talk, stop by our IRC channel or start topics in the forums.
Want to start making money as a white hat hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals.
Buy Now (90% off) >
Other worthwhile deals to check out:
- 97% off The Ultimate 2021 White Hat Hacker Certification Bundle
- 99% off The 2021 All-in-One Data Scientist Mega Bundle
- 98% off The 2021 Premium Learn To Code Certification Bundle
- 62% off MindMaster Mind Mapping Software: Perpetual License
21 Comments
- Hot
- Latest
Password hacking and how to prevent against it
Caleb McKee on January 12, 2021
The name "rainbow table" may conjure up images of colorful furniture and dinner placements, but in actuality, it's a technology hackers use to try and commandeer information from your online accounts.
Most websites advance their security to prevent this, but even trusted technology enterprises like Github have been subject to such attacks. Instances like the 2016 attack on the shopping site Taobao left over 20 million users, 1 out of every 20 of their annual shoppers, vulnerable. This article will shed light on exactly how hackers exploit weaknesses—particularly in passwords—and what you can do to keep your accounts as safe as possible.
How hackers get your passwords
Tools for password cracking and recovery like Hashcat are available on the internet for cybersecurity professionals to perform penetration testing on systems to ensure their security. The unfortunate consequence is that tools like this can also find their way into the hands of cyber criminals as well.
To make websites as secure as possible, passwords aren't stored on a database themselves. Instead, when you create an account password, the website processes your password through a hashing algorithm. This algorithm uses the string of characters you chose as your password to store a longer, more secure string that is much more difficult to obtain.
This algorithm uses the string of characters you chose as your password to store a longer, more secure string that is much more difficult to obtain.
This means hackers don't obtain your password when they crack the website's database. The good news is that hashing is a one-way process, so your password can't be reverse-engineered from a discovered hash. The bad news? Hackers don't need your password once they find the hash; the hash is all they need to gain access.
What is a rainbow table?
Rainbow tables are large collections of data that store various common or weak passwords and the hashes that are created from those passwords. During a network attack, the rainbow table compares its hashes to the hashes in the database to crack the code and gain access to information. Hackers can then utilize this information to exploit a vulnerable network.
How to defend against rainbow table attacks
The measures you can take to keep your accounts safe from rainbow table attacks are extremely simple:
- Use long, mixed-case, elaborate passwords
- Don't use the same password for more than one account
- Enable 2 factor authentication on every possible account
Longer, more complex passwords mean more possibilities for a hacker to deal with.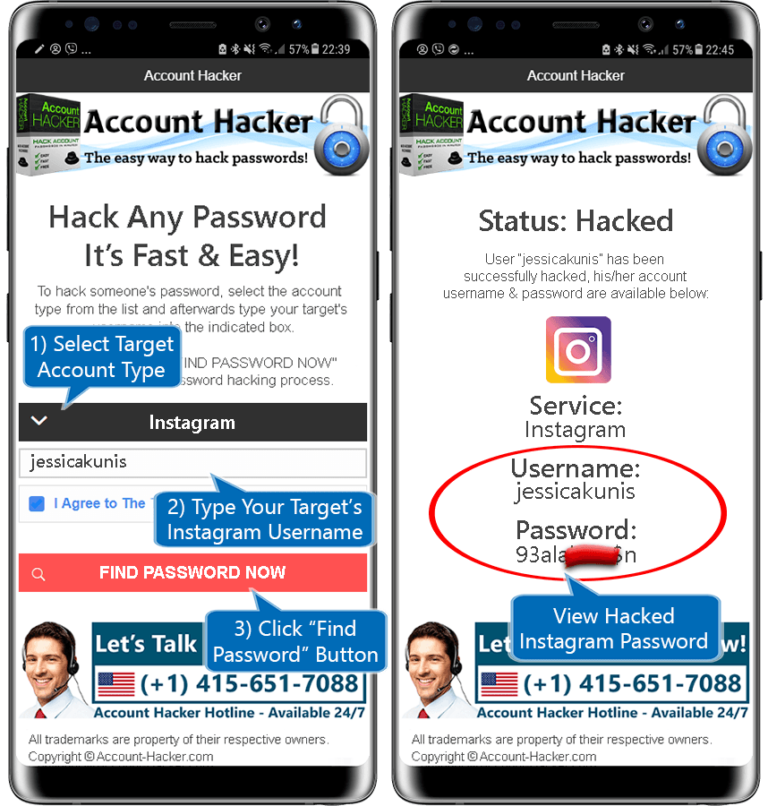 More possibilities equate to larger rainbow tables, which may demand more time than a hacker is willing to dedicate. You can even test the strength of your password to understand how much time it would take a hacker to crack your code.
More possibilities equate to larger rainbow tables, which may demand more time than a hacker is willing to dedicate. You can even test the strength of your password to understand how much time it would take a hacker to crack your code.
Make sure to not use the same password for everything. If you do, hackers could use the single hash they find to access every account you have. It would be like using the same key for every lock you own. If you want to make this easier, you can use password management software that keeps a list of complex passwords that can only be unlocked by a master password of your choice.
Additionally, 2 factor authentication may be a slight annoyance every time you log in from a new device, but it's masterful at keeping your accounts protected. As long as you have this setting enabled, you'll be notified anytime someone tries to access your account.
If you're curious about cybersecurity yourself, you can also check out the Kali Linux operating system designed for being a monitored space to play with penetration testing tools.
Author Bio: As an English graduate, technology enthusiast, and Asian food connoisseur, Caleb is happy to talk tech with anyone. You can find more of his writings on caleb-writes.com.
Interested in learning more about Minim?
Topics: Cybersecurity · home network security monitoring · smart home cybersecurity · smart home security system
Rainbow tables and RainbowCrack for cracking hashes on Kali
We have already shown how to decrypt a hash without much calculation. In today's article, I'll show you how to crack a hash on Kali Linux using rainbow tables and the RainbowCrack tool.
More on the topic: Stealing an NTLM hash using a PDF file
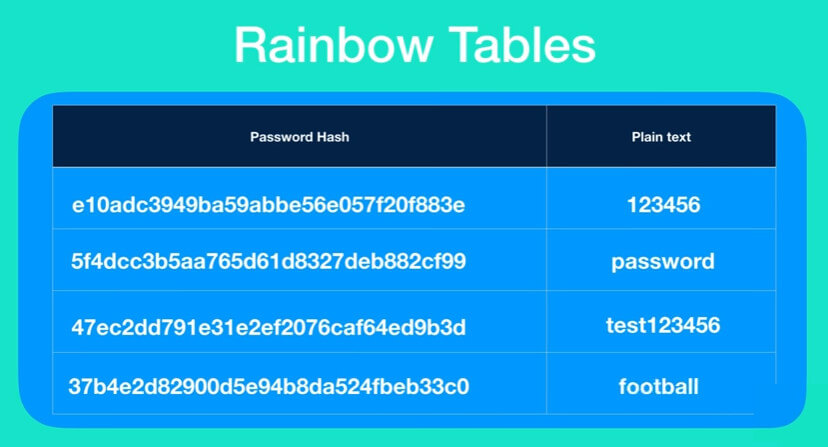
What is a rainbow table and password hash
There are a lot of theories regarding rainbow tables and hashes, so I will try to explain in simple terms. nine0003
nine0003
Passwords for Wi-Fi sites or networks are not stored in clear text. Stored passwords are hashed with various hashing methods such as LM, NTLM, MD5, SHA1, etc. The hash function converts passwords into a random set of numbers and characters.
Before a rainbow table attack, a hacker must first obtain a hash of the password. For example, it can find a vulnerability in Active Directory or obtain a password hash of users of a site with an insufficiently secure password database.
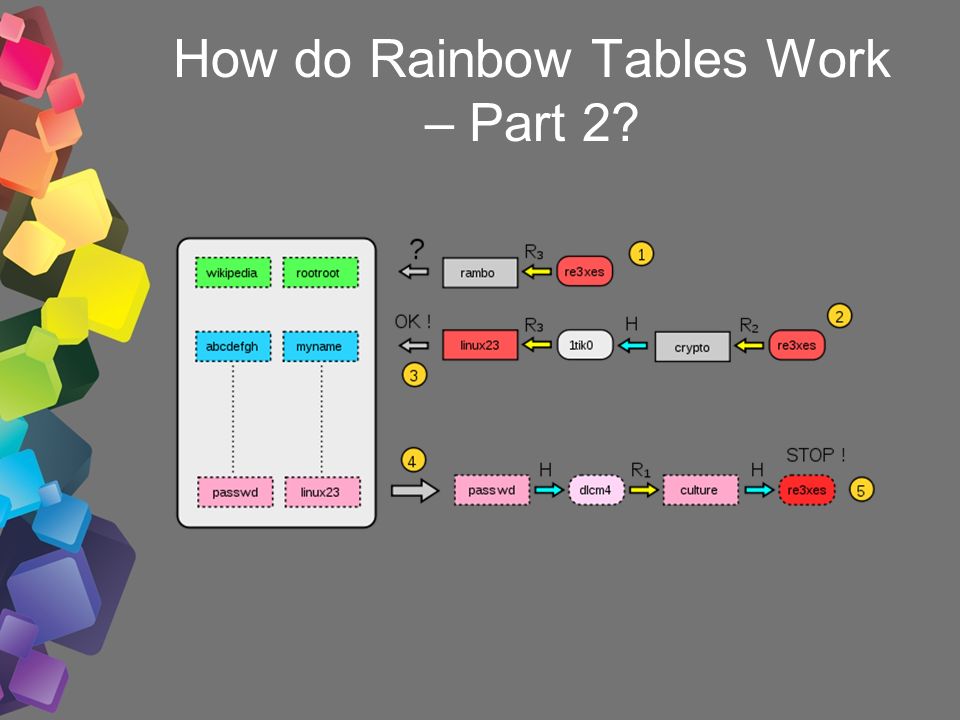
A hacker steals user password hashes and uses a rainbow table to try to crack the hash and get the passwords.
Rainbow tables are pre-calculated hashes that are used to quickly crack hashes, i.e. recovering passwords from the received hash. Rainbow tables are databases in which a calculated hash corresponds to a password.
Brute force vs rainbow table
As you know, a brute force attack uses a list of passwords. Brute passwords require a lot of time and computing resources of a computer, in particular a video card. But, unlike rainbow tables, it doesn't use much memory. nine0003
But, unlike rainbow tables, it doesn't use much memory. nine0003
Rainbow table works differently, requires less time but more memory. In general, hash cracking with rainbow tables is much faster than a brute force attack.
There are several types of rainbow tables depending on the type of hashes, characters, and password length. For example, a rainbow table is for SHA1 and using all lowercase letters (a,b,c…z), with a password length of 1 to 7, will be different from a rainbow table for SHA1, a lowercase password with a length of 1 to 9.
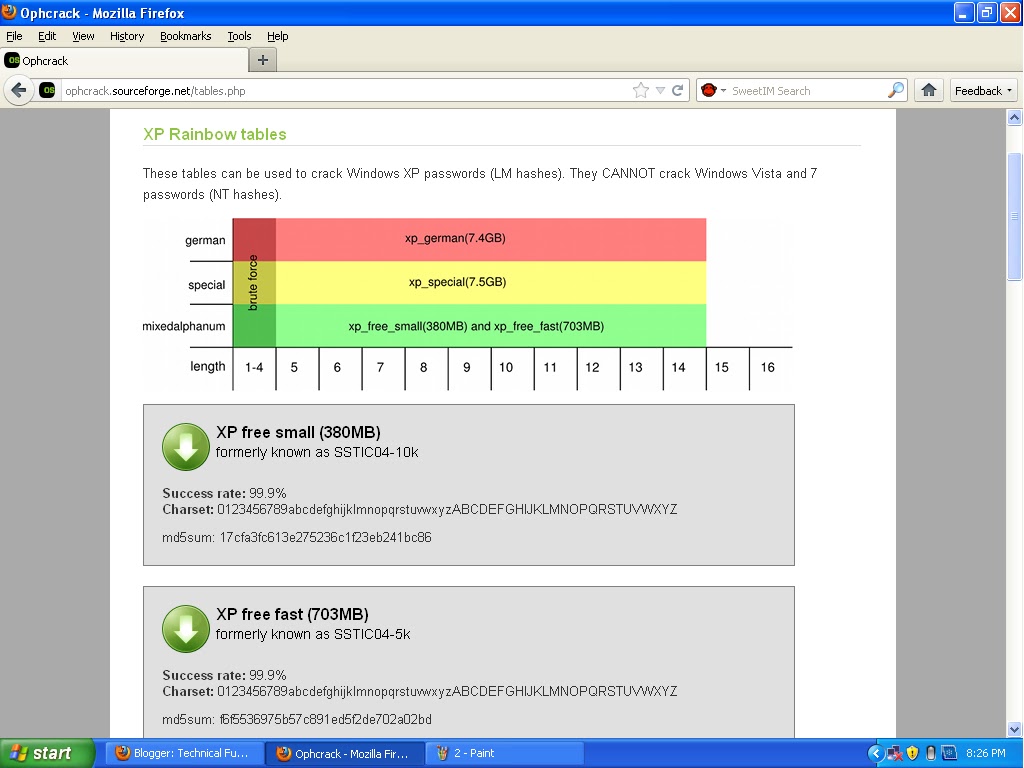
You can download rainbow tables (free and paid) on this site.
Rainbow tables are divided by hash algorithm (LM, NTLM, MD5, SHA1), encoding (numeric, lowercase, etc.), and password length.
You can download rainbow tables or create your own, meeting certain requirements and tailored to a specific hash.
It should be noted here that rainbow tables weigh a lot (from 20 GB to more than TB).
Creating a rainbow table with RainbowCrack
To create a rainbow table, you can use the RainbowCrack tool preinstalled on Kali Linux.
Creating a rainbow table takes a lot of time and space, but once the table is created, it can be used to quickly crack the hash.
Let's try to create a rainbow table to crack a 4-character MD5 password using only lowercase letters. To do this, open the Kali Linux terminal and run the command rtgen.
But first, let's open the help and take a look at the parameters:
| rtgen-h |
The above screenshot shows examples of using rtgen .
To generate a rainbow table for a 4-character MD5 hash using only lowercase letters, use the command:
| sudo rtgen md5 loweralpha 1 4 0 1000 1000 0 |
Where:
- rtgen md5 creates a rainbow table for the MD5 hash. nine0080
- loweralpha only uses lowercase letters.
- 1 is the minimum password length, and 4 - maximum.
- table index, chain length and chain number are set to 1000.
Upon execution, a rainbow table will be created. You can see the character set in use and other information.
The rainbow table will be in the directory:
| /usr/share/rainbowcrack | nine0056
Cracking hashes with the RainbowCrack rainbow table
We have an MD5 hash, password length is 4 characters in lower case.
| d6ca3fd0c3a3b462ff2b83436dda495e |
To crack the MD5 hash of a four-character password, we will use the rainbow table we created earlier, but before that, we need to sort the rainbow table with the following command:
| sudo rtsort . |
After executing the command, the rainbow table will be sorted.
Now using RainbowCrack to crack the password hash:
| rcrack. |
Where:
- rcrack calls RainbowCrack to crack the hash.
- -h indicates cracking the password hash.
- d6ca3fd0c3a3b462ff2b83436dda495e is the md5 hash.
Password cracked instantly.
You can also use a list of hashes from a text file.
To crack all hashes from a text file, use the directive -l:
| rcrack. -l /home/kali/Desktop/hash.txt |
As you can see, RainbowCrack cracked the hashes in a few seconds.
Now, create your own MD5 rainbow table, with a password length of 6 characters, consisting of lowercase letters and crack the hash. nine0003
Did it work? Congratulations! You have learned how to create and use rainbow tables to crack hashes using RainbowCrack on Kali Linux.
RECOMMENDED:
- Installing and using Shodan in the Kali Linux terminal
- Using Mimikatz on Kali Linux to Extract Windows Hashes
Top 5 ways to hack Instagram from phone 2022
Don't know how to hack password (page, profile) from Instagram? Looking for a reliable Instagram account hack to read correspondence and see photos? Reliable 5 Ways to Hack Insta - It's not as hard as you think! nine0003
Instagram hacking is an illegal act that can deprive you of a decent amount of money in the form of a fine and even reward you with a real prison term.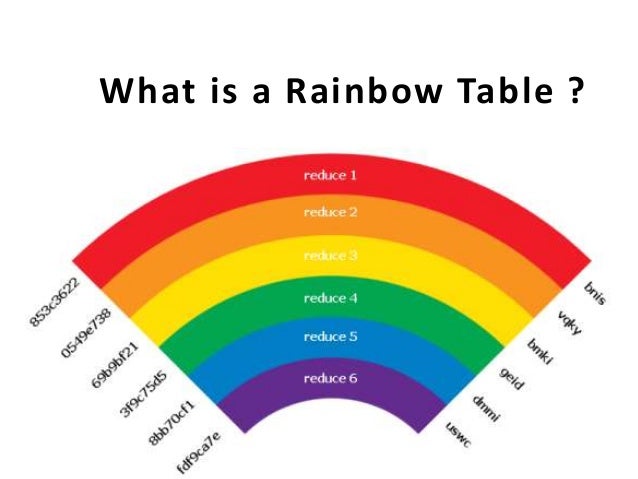 Therefore, before doing something in this area, think about it, is it really so important and necessary for you?
Therefore, before doing something in this area, think about it, is it really so important and necessary for you?
Top 5 ways to hack Instagram from your phone 2022
Method 1. Specialized application
We start with the simplest and most realistic (which can be used by everyone without exception) way to hack Instagram - you need to take only 10 (! ) phone minutes and quickly there free download Reptilicus , install and configure. This is easy enough to do. Everything is in Russian. Extremely understandable. If you have any questions, the site has manual in pictures , video instructions, as well as online consultants.
After installing the application you will be able to:
- read the correspondence without going to the page;
- see photos without hacking account;
- remotely see the location of a person when he is in the profile; nine0080
- to see the photos he has saved on his phone;
- see photos that were sent to him and then deleted;
- see what groups are watching and what is liking.
All this will become available when you install the special Reptilicus application on your phone. We offer not hacking an Instagram account, but control - this is the ability to remotely control a person's activities in this social network without penetrating his page and without performing any illegal actions combined with hacking. nine0003
In simple words, you won't need to hack your Instagram profile, you just install the program on your phone, and the program itself will send you everything that a person does on his phone, including on his page on Instagram.
Method 2. “Forgot password” function
We continue our review ... this is the most obvious method that (we don’t know for what reason) people don’t see on their own, although it lies on the surface. Yes, imagine, you can crack the Instagram password in order to get into the page using a function that allows you to recover a forgotten password. Here you need to know only the login (nickname) of the person. Just? Yes! Why didn't you think of this before? We do not know! So, you need to take the following steps:
Just? Yes! Why didn't you think of this before? We do not know! So, you need to take the following steps:
Step 1. If you have your own page, then go to your account - click on the Instagram icon - the home page will open. If not, then just go through the search engine.
Step 2. Press "Menu" - press "Add Account" - the standard menu for logging into your account will open.
Step 3. Enter the username (nickname/login) - click "Forgot Password".
Step 4. Select confirmation via SMS - enter your phone number - wait for SMS with a link to change your password. nine0003
Step 5. Open SMS - in the Change Password section, click on change password - change password.
That's it, now you know how to crack your Instagram password! You don't need to thank.
Method 3. Capturing keystrokes
You have probably heard that there are programs that can save keystrokes on your phone. And if you are thinking about how to hack an account on Instagram, then this method can allow you to intercept messages typed on your phone when communicating on Instagram. nine0003
And if you are thinking about how to hack an account on Instagram, then this method can allow you to intercept messages typed on your phone when communicating on Instagram. nine0003
The Reptilicus program will help you to see literally everything that the person whose correspondence you are so interested in is typing on his phone. You can also install any other keylogger, of which there are quite a lot on the Internet. We are just talking about our program, tested by time and users. You can hack an Instagram page with a simple installation. There are reviews of real users (the forum is over 7 years old).
Method 4. Chat screenshots
Chat screenshots, screenshots or instant screenshots (call it what you want, the meaning of this will not change in any way) is a real opportunity to do without the treacherous hacking of Insta. The screenshots will show all the correspondence, with emoticons, with all the actions that a person performs on his phone. nine0003
Screenshots are taken automatically and without root rights, as well as keyboard interception.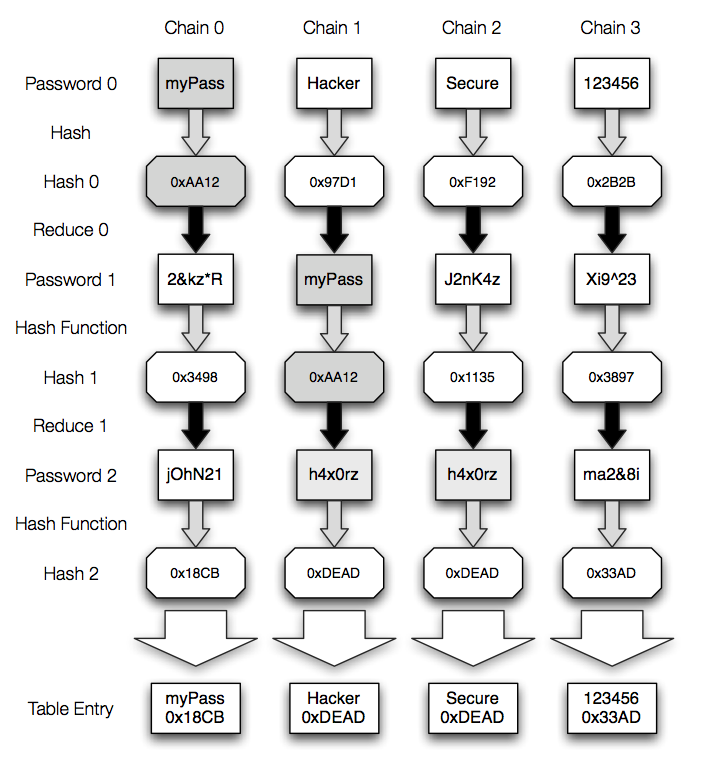 They will start coming as soon as a person goes to the page on Insta. To do this, you need to check the box in the program settings so that screenshots start working when you enter Instagram.
They will start coming as soon as a person goes to the page on Insta. To do this, you need to check the box in the program settings so that screenshots start working when you enter Instagram.
If you want to receive screenshots around the clock, and not just when you enter Insta, then do not set any restrictions. The settings are very convenient - make sure by looking at the manual. You can do this, but you can do that. Adjust as you need. If you want to receive screenshots every 10 seconds, get it, if you want only correspondence, please, receive only correspondence. Here the choice is entirely yours. nine0003
Method 5. Phishing
This method is considered the easiest, but at the same time the most illegal. This is a gross scam. Therefore, we do not advise you to use it. BUT since we provide possible ways, phishing will help you understand how to hack Instagram through a computer.
This method is that you create a phishing (false, fake) page to enter Instagram.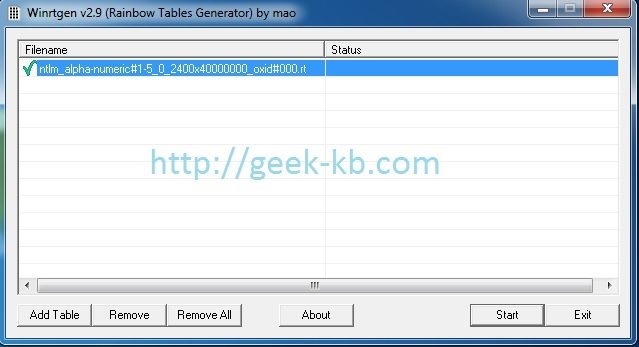 At first glance, it will not differ from the standard in any way. Only one letter will be changed there, or some symbol invisible to the naked eye will be added. BUT it will be DIFFERENT. The user enters his username and password there and transfers it to a regular Instagram. Therefore, he will never guess that he was on this fake page. But ... but you will receive his nickname and password. nine0003
At first glance, it will not differ from the standard in any way. Only one letter will be changed there, or some symbol invisible to the naked eye will be added. BUT it will be DIFFERENT. The user enters his username and password there and transfers it to a regular Instagram. Therefore, he will never guess that he was on this fake page. But ... but you will receive his nickname and password. nine0003
You can read about how to create a phishing page on the Internet. We do not approve of this method and just brought it as really working and existing for those people who need to know how to hack the Instagram of a friend, girlfriend, wife, husband or their children through their computer.
Conclusion
How to hack someone else's Instagram? There are different ways. We told you about them. Now it's your turn - choose wisely. We certainly advise you to use our service. If difficulties arise, there are always online consultants on the site who will explain in detail and answer all your questions.

 -h d6ca3fd0c3a3b462ff2b83436dda495e
-h d6ca3fd0c3a3b462ff2b83436dda495e