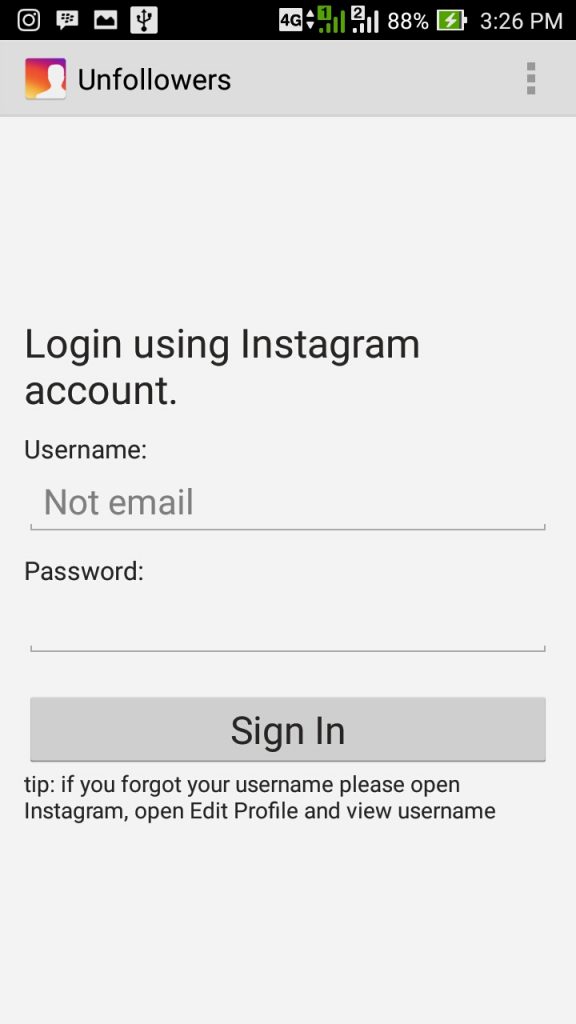
How to get peoples instagram passwords
How Instagram accounts get hacked: 6 tactics used by hackers
How many Instagram accounts get hacked a year?
According to Notch's data, an Instagram creator account gets hacked every 10 minutes on average - meaning over 50,000 creator accounts get hacked every year. The hacking figure for all accounts, not just creator accounts, is much higher.
Every year, cybercriminals generate over $3 billion in revenue from social media attacks alone and hacking constitutes a large portion of these malicious incidents.
To help influencers and business owners protect their Instagram accounts, below we breakdown 6 tactics hackers use to extract personal information and bypass 2-factor authentication.
{{learn-more}}
How do Instagram accounts get hacked?
How do hackers hack Instagram accounts? There are default security features on Instagram, like 2-factor authentication, so how can hackers overcome these?
The general answer to that question is, in most cases, some form of social engineering.
In this context, social engineering refers to the act of manipulating and deceiving Instagram users into willingly providing confidential information.
1. False copyright infringement messages
The tactic
Instagram clearly states that you can only share original content that doesn’t violate copyright infringement laws. That said, it’s possible for you to commit a copyright violation unintentionally, in which case Instagram would take action and reach out to correct the problem.
This has led to many cybercriminals actually impersonating Instagram representatives pretending to address copyright infringement issues. In these cases, a hacker sends a link to your email or through a private message on Instagram and asks you to log in in order to address the issue. This is a real-life example of a message that was used to hack @wandertears:
You can learn more about this case by checking out this article.
The link leads to a fake page that, even though it mimics Instagram’s login page, is actually designed to collect your username and password details. The only difference between the real page and the fake is a small variation in the URL, which is hard to detect.
The only difference between the real page and the fake is a small variation in the URL, which is hard to detect.
To avoid raising suspicion, cybercriminals usually redirect you to one of Instagram’s legitimate FAQ pages that discusses the topic of copyright infringement.
The solution
There’s a couple different methods you can use to verify the messages you receive from Instagram. First, urgent Instagram notifications are usually delivered directly through the account interface or via email. If you receive a DM about your account, it won’t be legitimate - even if it’s from a profile that has the name “Instagram” in the username.
Second, Instagram now allows you to see a record of all security and login emails through your account. If you receive a suspicious email directly to your inbox, you should check this part of your Instagram account before opening the message.
From your profile, go to Security>Emails from Instagram. If you don’t see a record of the email, you should delete it right away.
{{subscribe}}
2. Deceitful verified badge offers
The tactic
You’re probably familiar with verified badges, the blue pins at the top of Instagram profiles that have been authenticated by the social network. While valuable, this account feature is also at the center of another social engineering that hackers use to break into Instagram.
In this scenario, hackers send a private message or email that offers a chance to add a verified badge, linking to a deceitful website that collects your login information. They may request that you don’t change your profile data, like username or password, until the change has taken effect in order to gain enough time to break into your account.
Here’s an example of a verification badge scam email sent to the owners of pillow business, Cuddle Buddy.
The solution
There are a few tell-tell discrepancies here to help you avoid falling for such a scam. For starters, grammar mistakes like excessive capitalization should serve as a warning. Not only this, but the profile the message is being sent from does not belong to an official account nor does it have a verified account. It has the word “Instagram” in the name, but it doesn’t give any indication of being official. Finally, note how the “contact us” text on the blue button is not centered properly, so it’s not consistent with other Instagram content.
Not only this, but the profile the message is being sent from does not belong to an official account nor does it have a verified account. It has the word “Instagram” in the name, but it doesn’t give any indication of being official. Finally, note how the “contact us” text on the blue button is not centered properly, so it’s not consistent with other Instagram content.
To get a blue verification badge right now you need to apply through your profile, and the form you have to fill in should look a little something like this:
3. Illegitimate suspicious activity alerts
The tactic
Hackers that employ social engineering attacks leverage every piece of information they have at their disposal. For example, they sometimes design suspicious activity alerts that look like a legitimate notification from Instagram, but actually contain malicious links.
The solution
According to the Meta-owned social platform, emails from Instagram only come from “@mail.instagram. com” or “@facebookmail.com” addresses. Here’s an example of what a legitimate security email from Instagram looks like:
com” or “@facebookmail.com” addresses. Here’s an example of what a legitimate security email from Instagram looks like:
This security message is for a new login from a device that the user didn’t commonly sign in through. Note how the email address is from a trusted source and how all of the design elements are aligned properly.
Even if the emails you receive look legitimate, we advise that you go to your Instagram account and verify that the security email was sent through there.
4. Fraudulent giveaways and brand sponsorships
The tactic
Fraudulent giveaways are especially troublesome because they exist in an ecosystem that is packed with legitimate promotional freebies. This form of social engineering can take two different shapes.
In its most traditional version, this type of hack operates like a false verified badge attack. The difference is that the hacker impersonates a big brand, exciting start-up, or similar renowned company that’s offering a big giveaway to specific social media influencers.
Some scammers even have legitimate-looking accounts that have been active for a while and have thousands of followers. The first message usually includes at least one spoofed link leading to a false Instagram login that’s designed to extract the username and password submitted.
A more complex form of fraudulent giveaways and sponsorships can occur when hackers have collected information about you, but still need a few more details to successfully breach your account. Instead of sending you a link to a spoofed login page, hackers may ask you to fill in a survey that asks for personal information, like your date of birth, mother’s maiden name, and other answers to common security questions.
Below is a real example of the phishing email that led to @FlipFlopWanderers getting hacked. Read their full story here.
The solution
Never rush or feel pressured into clicking links. Take time to investigate if the email looks legitimate: for instance, check for spelling mistakes and hover over the hyperlink to see if the URL leads to a familiar or safe website. To be extra safe, you could even Google the company supposedly sending the email, and contact them to check if they really did send you an email.
To be extra safe, you could even Google the company supposedly sending the email, and contact them to check if they really did send you an email.
5. Counterfeit social media tools
The tactic
Managing a social media profile can take a huge amount of time, especially if you have a large base of followers. There are many tools that can simplify the process, but you also have to evaluate each platform to make sure it comes from a legitimate developer.
Just as with malicious web extensions, hackers can create counterfeit tools that are supposed to improve functionality, but actually pose a security threat.
These tools usually look and feel legitimate, but bring you very little in terms of functionality and practical value. This type of scheme is not as common because it requires a significant amount of resources, but it’s still used by cybercriminals looking for bigger, more valuable targets.
When this type of attack is successful, target users integrate the counterfeit tool into their social media accounts. This fake tool can be used to set up man-in-the-middle attacks, intercept all data, and extract login details, among other data.
This fake tool can be used to set up man-in-the-middle attacks, intercept all data, and extract login details, among other data.
The solution
It’s normal to watch your budget, especially in the early stages of your Instagram account. But, working with lesser-known, low-cost tools increases the chances of being targeted by scammers. To avoid this, you should opt for established tools that come from renowned providers or platforms that have been recommended by trusted peers.
6. Reverse proxy attacks
The tactic
All of the social engineering hacking techniques we’ve covered so far require hackers to manually create fake apps and website pages in order to collect details from their targets. With reverse proxy attacks, hackers don’t need to create a spoof website or app - instead they can automate the theft of credentials.
A reverse proxy attack is a type of man-in-the-middle approach - hackers direct victims to a domain that sits in between the user and the legitimate website. The URL will be very similar to the legitimate page, and the overall appearance in the malicious domain mirrors the legitimate page.
The URL will be very similar to the legitimate page, and the overall appearance in the malicious domain mirrors the legitimate page.
When applied to the Instagram context, you could receive a convincing email from a hacker that directs you to Instagram’s login page. What you don’t realize is that you’ve been sent to do this via a proxy server - so when you enter your credentials and log into Instagram, your information - including 2FA - is being intercepted in real time.
The solution
Be extremely cautious when clicking on links from your email inbox - always verify an email claiming to be from Instagram by checking your Instagram account. From your profile, go to Security>Emails - if the email doesn’t appear there, it’s likely a scam.
What Do Hackers Do After Hacking Your Account?
Now that we’ve answered the question “how do hackers steal Instagram accounts?” let's go over the reasons why these criminals may want to target your profile.
Like other types of criminals, hackers and other malicious actors flock to the most popular platforms because these present the biggest financial opportunities. Today, you can generate a significant amount of revenue from a large base of followers and hackers are eager to benefit from this.
Today, you can generate a significant amount of revenue from a large base of followers and hackers are eager to benefit from this.
Some of the common things a hacker may do once your account is breached include:
- Demand a ransom
- Scam your friends, family members, and customers. Investment, Bitcoin, and Romance scams are some of the most common.
- Sell your account on the dark web
- Use your account to run a fraudulent operation
- Make various types of illegal requests, like requesting lewd photos
What To Do If Your Instagram Is Hacked
Getting hacked on Instagram is a nightmare, especially if you're a business owner relying on your account to market your services and drive sales. Keep reading for a summary of what you can do if you've just been hacked. For more information, watch the video explainer below.
- Reach out to your social media insurance provider, who'll help you recover your account ASAP while paying you for each day you're locked out.
- Check your email for a message from [email protected] and select “revert this change”. If this doesn't work, continue to step 3.
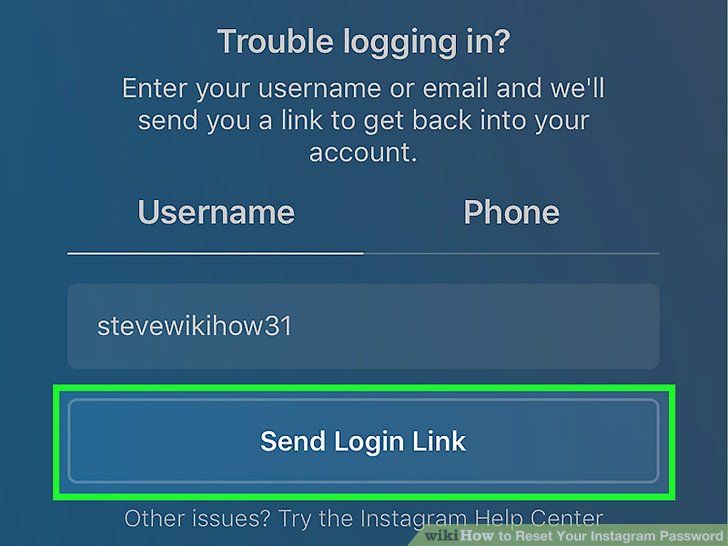
- Click “Forgot password” on the login screen and request a login link. If this doesn't work, continue to step 4.
- Send a video selfie to Instagram: This method has helped a lot of people retrieve their accounts. An important detail here is that if your account doesn’t contain photos of your face, this verification process won’t work.
- Create a Business Account on Facebook, go to "Help", and select "My ad account was hacked". From there, you have a better chance of reaching a human customer support representative. We show how to do this in the video.
Looking for the Best Way to Protect Your Account?
Hackers use a wide range of approaches and develop new techniques regularly to hack Instagram accounts and bypass Instagram’s default security measures. The number of social media scam victims in the US skyrocketed from 46,000 to 95,000 in 2021, and that number shows no signs of slowing down in the future.
The number of social media scam victims in the US skyrocketed from 46,000 to 95,000 in 2021, and that number shows no signs of slowing down in the future.
Learning about the different techniques that hackers use and implementing security best practices as a counter are the first steps to keeping your Instagram account safe. Unfortunately, however, there is no way to guarantee your account against hacks - even users with multi factor authentication set up are falling victim. That's why we launched Notch - to finally give creators peace of mind.
{{learn-more}}
How to Avoid Getting Your Instagram Account Hacked (And What to Do if it Happens)
Getting your Instagram account hacked is a serious situation—there’s no guarantee that you can recover a hacked Instagram account. And even if you eventually regain control, the account recovery process is time-consuming and frustrating.
If you use Instagram to promote your business, sell products, and connect with your fans, that could mean going days without access to a crucial social media channel. And since many hackers use the Instagram account to scam other Instagram users, you risk losing the trust of your audience.
And since many hackers use the Instagram account to scam other Instagram users, you risk losing the trust of your audience.
It’s crucial to proactively protect your account and know how to take action quickly if hackers slip past your defenses.
💡
Schedule your Instagram posts, carousels, stories, and reels with Buffer
Visually plan your content calendar and make your profile a "must-follow" with Buffer's suite of Instagram scheduling and analytics tools.
Start with a strong password
Your childhood pet’s name paired with an ! and your area code might meet Instagram’s password requirements, but it’s far from a strong password. If your password is easy to remember, it’s probably easy to hack.
Consider using password manager tools such as 1Password and LastPass that auto-generate random, complex passwords and store them in a virtual vault which is protected by encryption and multiple layers of authentication. All that is a techy way to say that your passwords are locked behind (virtual) doors that would make a heist-movie hacker sweat. Password managers are a win-win—you get secure passwords without having to memorize a long stream of gibberish for every app or site you use.
Password managers are a win-win—you get secure passwords without having to memorize a long stream of gibberish for every app or site you use.
Use two-factor authentication
Two-factor authentication puts another barrier between hackers and your Instagram account. If anyone gets your password and attempts to log in from an unrecognized device or location, they’ll be asked to verify their identity with an authentication code.
To set up two-factor authentication, open your Instagram profile on mobile or desktop and go to Settings, Security, then Two-Factor Authentication. From there, you can choose either text messages or an authentication app.
Instagram recommends authentication apps such as Google Authenticator or Auth0 because they are designed specifically for this purpose, so they are more secure than text messages. Think of it this way—how many devices have access to your text messages? If you’re an iCloud user, for example, your text messages might pop up on your iPad or laptop as well.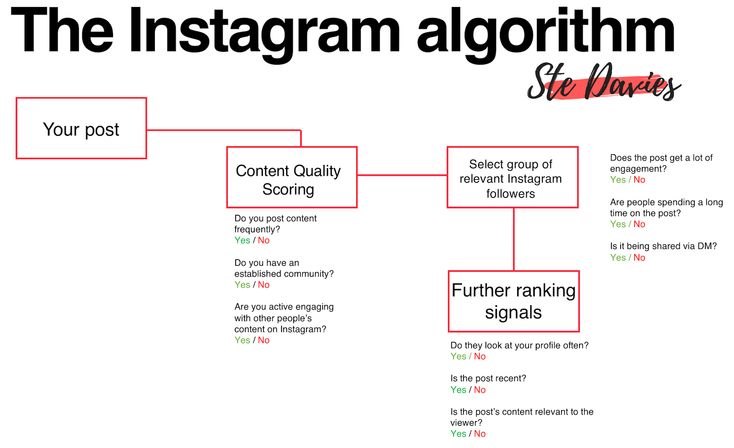
Once you choose an authentication method, the app will also provide several backup codes in case you lose access to your authentication method. Screenshot your backup codes and store them in a secure location such as password-protected cloud storage like Google Drive or Dropbox.
Monitor third-party apps
Third-party access isn’t necessarily a bad thing, but it’s important to keep an eye on which apps are connected to your Instagram account. To check if any third-party apps have access to your Instagram, go to your Instagram Settings, then Security, then Apps and Websites.
If you use a third-party tool for Instagram analytics or to schedule Instagram posts, this is where you’ll see those connections. When deciding whether or not to keep a connection, ask yourself—is this tool secure on its own, and does this connection help keep my Instagram account secure? For example, a Buffer connection allows you to grant access to analytics and scheduling to multiple people without ever having to share your Instagram password. Plus, Buffer supports two-factor authentication, so your Buffer account is also secure.
Plus, Buffer supports two-factor authentication, so your Buffer account is also secure.
Watch out for apps and websites that don’t need regular access to your account. It’s easy to use Instagram to log in to another app or make a purchase and then forget you granted access. Make sure you regularly check to avoid racking up suspicious third-party apps and, when in doubt, revoke access.
Keep in mind that some third-party tools are inherently risky. For example, apps with mass automation such as following/unfollowing accounts are both a security and terms of service risk—Instagram will flag accounts that use mass automation and potentially shut them down.
Learn how to spot phishing messages
Phishing—fraudulent communication designed to trick people into giving up sensitive information—is one of the most common ways of getting an Instagram account hacked.
Phishers slide into your DMs with official-sounding messages. Scammers often pose as an Instagram support account or Instagram copyright help center and try to convince you there is an urgent need to share personal information. Never reply to these messages or click on any links. The Instagram Creators account shared a warning about these types of DMs:
Never reply to these messages or click on any links. The Instagram Creators account shared a warning about these types of DMs:
View this post on Instagram
A post shared by Instagram’s @Creators (@creators)
Emails from Instagram, built directly into the app, is only one official way for Instagram to contact you. You can view your emails by going to Settings, then Security, then Emails from Instagram, or check your inbox for emails from [email protected].
How to recover a hacked Instagram account
If you suspect your Instagram account has been hacked, there are several steps to follow to regain control of your account.
Hackers usually change your password right away, but sometimes you’ll get lucky and still be able to access your account through a saved login. If that’s the case, immediately change your password, and enable all the security precautions we discussed in the previous section.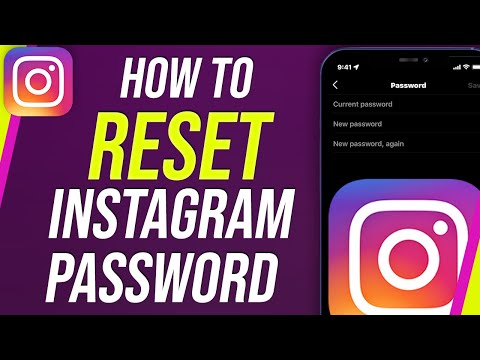
If you can’t log in, check your inbox for an email from [email protected]. Instagram may reach out to you if they detect suspicious activity. When caught early, changes can be reversed.
You can also request a login link from Instagram by selecting “get helping logging in” on an Android or “forgot password” on an iPhone. If the login link doesn’t work, you’ll need to request a security code. After that, Instagram will ask you to verify your identity by submitting a photo of yourself holding a paper with the security code written on it.
Sounds pretty complicated, right? Unfortunately, the process is both complex and time-consuming. Instagram also doesn’t guarantee account recovery, which is why we highly recommend being proactive about your Instagram account security.
Instagram management requires good security measures
Don’t put all your hard work at risk with weak passwords or lax security. Set up your security measures early so you can concentrate on creating and sharing great content for your audience.
You and your team can manage your Instagram posts, Stories, and analytics directly in Buffer without putting your Instagram account at risk. Get started today with a 14-day trial.
Brought to you by
Did you find this article helpful? You might also like our all-you-need social media toolkit.
Get started for free now
Instagram: privacy and security settings
Social network accounts, especially popular ones, are a tasty morsel for attackers. And it is easiest to hack what is poorly protected. Therefore, we regularly remind you that it is worth taking care of the security of your accounts, as far as social networks allow it.
- Set up privacy and security for your Instagram account
- The most important security settings on Instagram
- How to change your Instagram password
- How to set up two-factor authentication on Instagram
- How to check in the app if you received a real email from Instagram
- Where to find the list of apps connected to Instagram
- The most important privacy settings on Instagram
- How to close your Instagram account and edit your followers list
- How to control who sees your Instagram stories
- How to get rid of spam comments on Instagram
- How to get rid of spam in direct and adding to the left groups on Instagram
- How to hide your online status on Instagram
- How to block or restrict a user from your Instagram
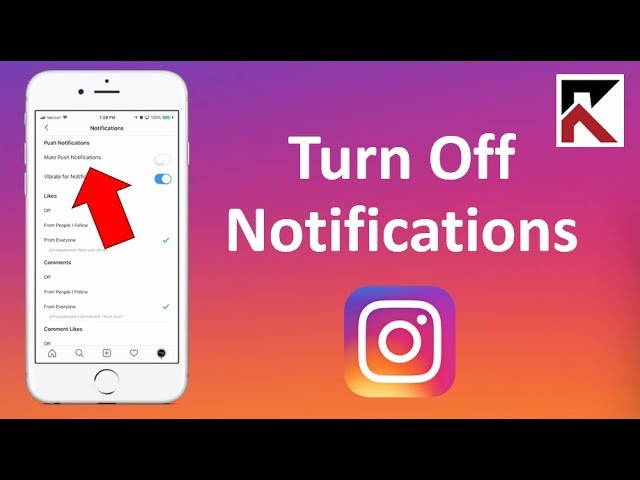
- How to remove unnecessary push notifications in the Instagram app
- The most important security settings on Instagram
- Do not forget to set up security in other social networks
Unfortunately, security and privacy settings are often difficult to understand.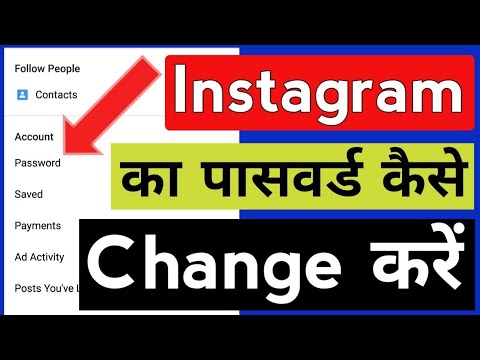 Moreover, developers change them from time to time. For example, Instagram settings have recently been updated. We tell you what is useful in them and where to look for this useful.
Moreover, developers change them from time to time. For example, Instagram settings have recently been updated. We tell you what is useful in them and where to look for this useful.
Setting up account security on Instagram
New Instagram settings allow you to even more securely protect against unauthorized account login and identity theft.
To find your security settings:
- Open your profile.
- Click on the three bars in the upper right corner of the screen.
- Select Settings .
- Go to section Security .
Where to find the security settings in the Instagram app
The password is the head of everything
The first rule of security for any account is to set a good, long, unique password. Attackers will not be able to quickly pick it up and will not find it in the databases that they managed to steal from other sites, which means they will not be able to hack into your account.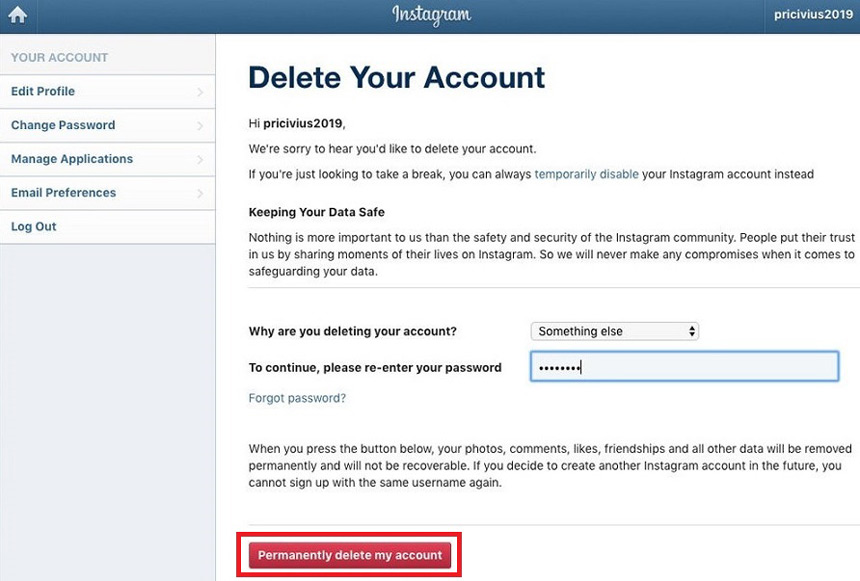 At least, if you do not give out your password yourself or it does not leak from the social network itself.
At least, if you do not give out your password yourself or it does not leak from the social network itself.
How to set up two-factor authentication on Instagram
Turn on two-factor authentication to ensure that your password is leaked. Every time someone tries to log in on a new device on your behalf, the social network will request a one-time code from SMS or from a special application. Thus, you will always be aware of login attempts, and it will be impossible to hack your account without knowing the code.
To enable two-factor authentication:
- Select Two-factor authentication .
- Press Start .
- Choose how you want to receive codes: via SMS or two-factor authentication app .
How to set up two-factor authentication in the Instagram app
An added bonus - after enabling this feature, the social network will give you backup codes . They will help you log into your profile if you don’t have a phone at hand that should receive SMS or on which an application for generating one-time codes is installed (yes, you can do this too - see this post for more details). Write down the backup codes and keep in a safe place.
They will help you log into your profile if you don’t have a phone at hand that should receive SMS or on which an application for generating one-time codes is installed (yes, you can do this too - see this post for more details). Write down the backup codes and keep in a safe place.
How to check in the app if you received a real email from Instagram
Instagram developers figured out how to protect their users from phishing via email. Now in the application settings you can see what letters the social network has sent you over the past two weeks. If you received a letter supposedly from Instagram, but it is not in the application, you can safely send it to spam.
To see which social media notifications are real:
- Select Emails from Instagram .
- Look for the letter you are interested in under the Security tab if it concerns login attempts, suspicious activity from your account, and so on. If it's about something else, check if it's on the tab Other .

How to check in the app if you received a real email from Instagram
Where to find a list of apps connected to Instagram
Another source of danger is third-party sites and apps. They are connected to expand the capabilities of the social network, for example, add photo filters or convenient marketing tools. However, if such an application is hacked or its authors are dishonest, your account can be used for criminal purposes. You can view the list of connected applications and sites and remove everything superfluous in the same section Security , in block Applications and websites .
Where can I find the list of apps connected to Instagram
Setting up Instagram privacy?
Instagram allows you not only to keep your profile safe, but also to restrict access to your photos, videos, stories and other data. You can hide personal content from prying eyes, save yourself and friends from offensive comments, and prevent subscribers from sharing your stories and posts with others. For this:
For this:
- Open your profile.
- Click on the three bars in the upper right corner of the screen.
- Select Settings .
- Go to section Privacy .
Where to find the privacy settings in the Instagram app
How to close your Instagram account
If Instagram is not a promotion site for you, but a place to share pictures and videos with friends, you can make your account private:
- Open Account privacy .
- Enable Closed account .
How to close your Instagram account
Now only followers you have approved will see your posts and stories. True, there are some nuances. Firstly, everyone who managed to subscribe to you before is automatically considered approved by the social network. If you do not agree with it, then you need to do this:
- Section Privacy select Accounts you follow .

- On the Followers tab, find and remove those you don't want to show your posts and stories to.
How to edit your Instagram followers list
Secondly, if you repost an Instagram photo to another social network, it will be seen by everyone who can see your posts on that social network. So if you do this often, don't forget to set up privacy on other social networks as well.
How to control who sees your Instagram stories
If you are an insta-blogger and it is not convenient for you to close your account, you can control access to specific content. For example, Instagram allows you to hide stories from individual users, publish some of them only to your list of close friends, and limit or even turn off the ability to respond to them. All this is done in section Privacy in block History . There you can also prevent readers from sharing your stories in messages and showing your posts in their stories.
How to control who sees your Instagram stories
To protect yourself and your followers from abuse and spam, you can automatically hide inappropriate comments using Instagram filters or your own.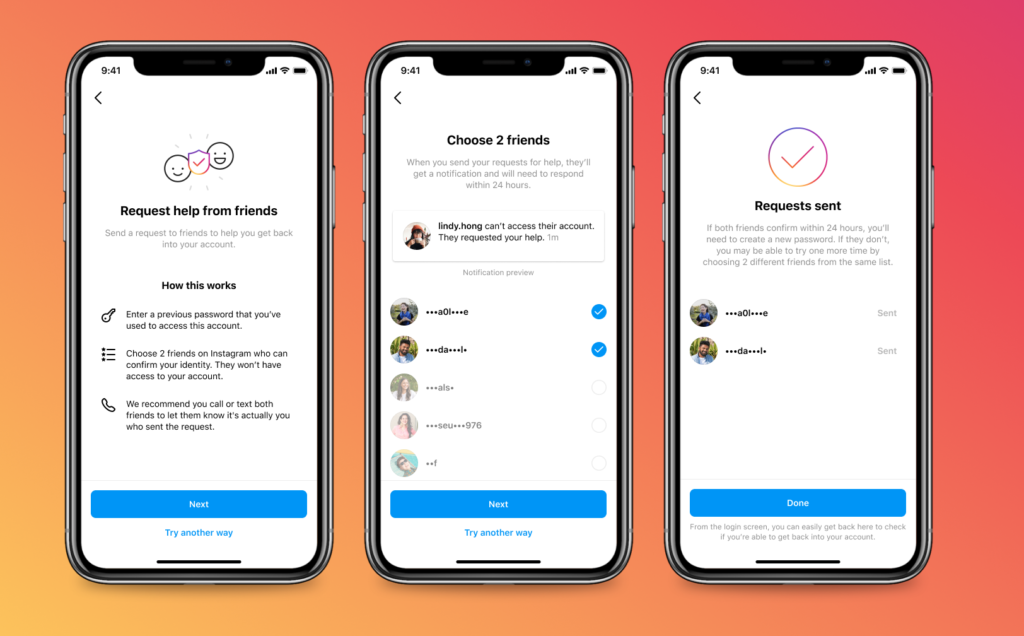 You can configure this in section Privacy , in block Comments . There you can also prevent especially gifted spammers from commenting on your photos and videos.
You can configure this in section Privacy , in block Comments . There you can also prevent especially gifted spammers from commenting on your photos and videos.
How to get rid of spam comments on Instagram
How to get rid of direct spam on Instagram
The social network allows you to prevent outsiders from writing you private messages and adding you to groups. If you are annoyed by spam in direct or you think that messages are your private space, open in section Privacy block Messages and select Only people you follow for both items.
How to get rid of spam in direct and adding to the left groups on Instagram
How to hide your online status on Instagram
If you don't want your readers to know when you're online, you can hide your online status from them. To do this, select in section Privacy item Network status and deactivate the switch. True, after that you will also not be able to see information about the activity of other users.
True, after that you will also not be able to see information about the activity of other users.
How to hide your online status on Instagram
How to hide from specific users on Instagram
Finally, spammers and other annoying readers can be blocked or restricted from accessing your account. To do this, click on the objectionable profile three dots in the upper right corner and select Block or Restrict access .
How to block or restrict someone from accessing your Instagram
Restricted account holders will still be able to view your photos and videos and even leave comments on them, but only you and the author will see these comments.
You can also put the user in silent mode if you are tired of his stories and posts in the feed. This can also be done in his profile:
- Click the button Subscriptions .
- Select Switch to silent mode .
- Enable mute mode for Stories , Posts or both.
Setting the Instagram user to silent mode
Your friend will not know anything about it, and you can take a break from the flurry of his photos and look at them only when you are in the mood - his profile will remain visible to you.
How to remove unnecessary push notifications in the Instagram app
Instagram, like any social network, by default sends more notifications than you need. To avoid annoying pop-up notifications that one of your friends has posted a photo for the first time in a long time, you can turn them off. To do this:
- Open your profile.
- Click on the three bars in the upper right corner of the screen.
- Select Settings .
- Go to section Notices .
- Go through the list of push notifications and turn them off for any events you don't want to know about right away. If you don't want to be notified at all, for example when you're playing or watching a series, select Pause all and set how long Instagram will remain silent.

How to remove unnecessary push notifications in the Instagram app
Now you know how to protect your Instagram account and can customize it the way you want. It's time to remember about your accounts in other social networks. Here's what the security and privacy settings look like on Vkontakte, Facebook, Odnoklassniki, and Twitter.
What to do if someone tries to access your Facebook or Instagram
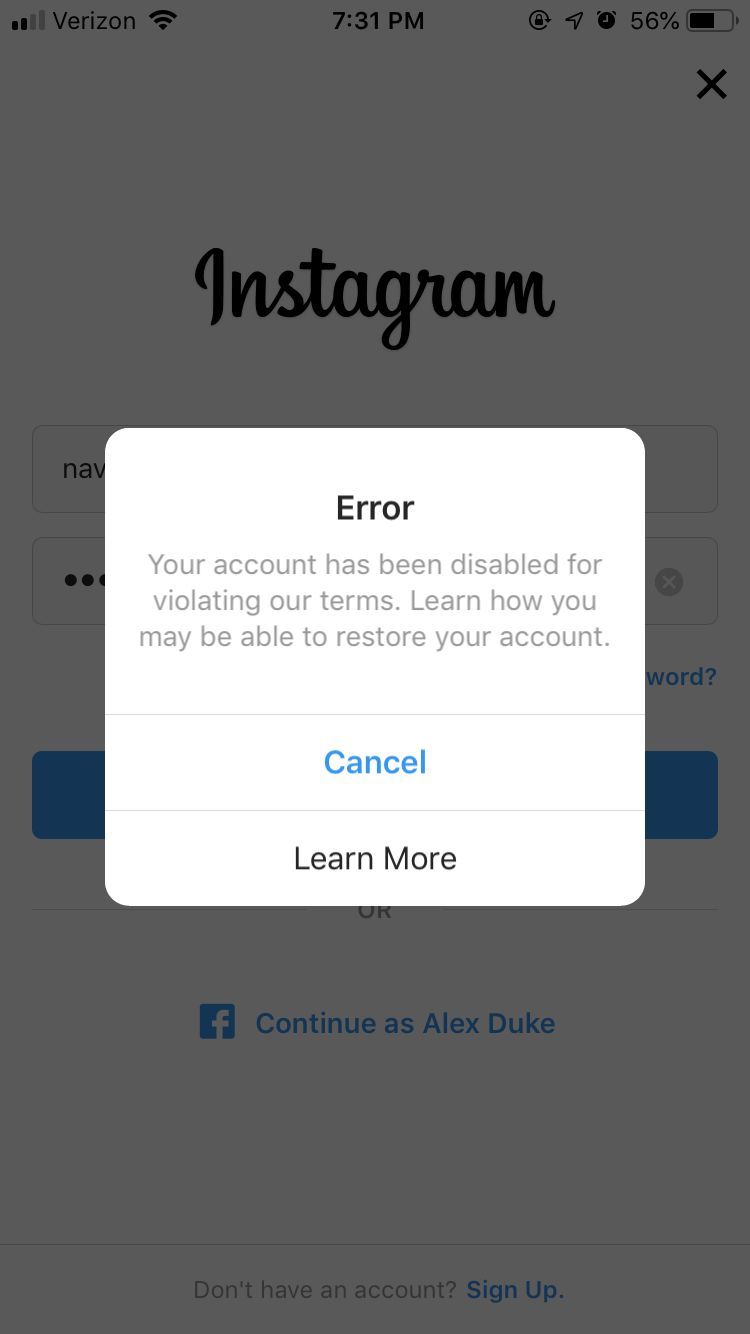
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act.
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on.
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password.
If an attacker steals the current token, he will be able to log into the account without a username and password.
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It is possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account.
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there.
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing.
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done by pressing one button in the Security and login section in the settings. This will reset the access tokens.
- Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them. If they managed to do this, change it back to yours.
- Set a new password that is strong and one that you don't use anywhere else.