How to hack telegram messages
Telegram App Store Secret-Chat Messages in Plain-Text Database
Spread this blog
EDIT: The following post * was not on a rooted or jailbroken device *. In order to access the plain-text secret-chat database containing the messages, we used our implementation of CVE-2014-3153. The claims that the device is rooted / jailbroken are incorrect and misleading.
I will start by quoting CryptoFail blog
“Telegram is an encrypted instant messaging app for iOS and Android devices. Obviously, I wouldn’t mention it on this blog if its crypto was perfect. In fact, it’s far from perfect. It’s almost horrifying.
I’m not sure if it was in response to some good criticism, but Telegram recently announced a crypto contest. Basically, if you can recover an email address that was encrypted with their secure messaging app, you can win $200,000 USD worth of Bitcoin.
Unfortunately, the contest is useless. Neither users nor Telegram developers will learn anything from the contest results.
But, Telegram will still be able to point to the contest and say, “Look! No one has won the contest, so our software is secure!” Naive users will believe Telegram, and they will feel safe using dangerously broken encryption.”
I decided to take a closer look at the contest. My intention was to see if I could read encrypted messages without being on-the-wire. I conducted a test using Android OS version 4.4.2.
Telegram claims to be a privacy oriented messaging app capable of encrypting personal and business secrets – only they are not. A critical vulnerability discovered by Zimperium Mobile Security Labs exposes their more than 50 million users who believe the app provides the security to chat freely. Let me explain how we stumbled onto this vulnerability.
The old Crypto contests from Telegram reference breaking its protocol while being in the middle of an encrypted conversation. This is not a sound idea for two reasons:
1. In the real world hackers do not play by the rules.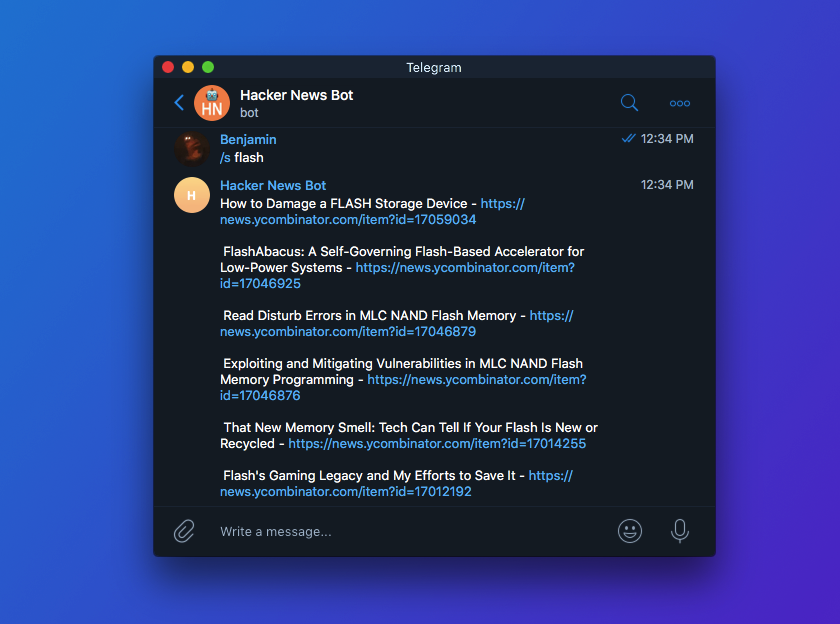
2. This assumes hackers would try to break Telegram’s encryption in the middle, when you can instead find weaknesses in other protocols which provide more benefits (e.g: GoToFail to bypass SSL encryption on iOS).
The New Crypto contests by Telegram says, “…and this time contestants can not only monitor traffic, but also act as the Telegram server and use active attacks, which vastly increases their capabilities.”
As a result, I am not going to break the encryption simply by avoiding it. I am going to bypass the encryption by simulating an active attack on the device.
The best way to do this is by understanding the anatomy of cyberattacks and the architecture of mobile devices. It did not take me long to install Telegram’s software, find both the encrypted and non encrypted texts that I sent, along with a Database containing all of the above.
Telegram’s website says: “A Secret Chat is a one-on-one chat wherein all messages are encrypted with a key held only by the chat’s participants.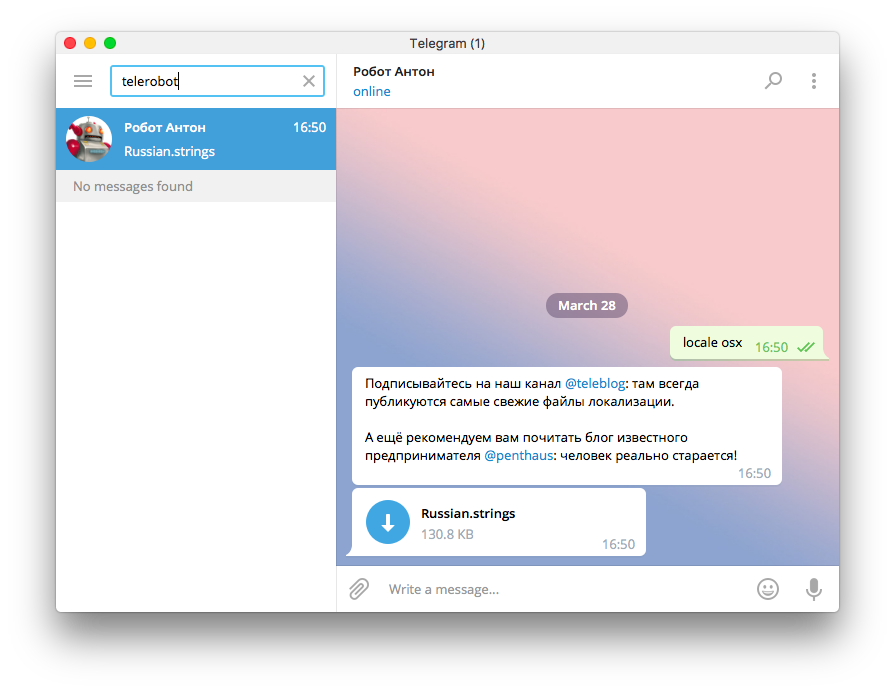 By definition, it follows that no third parties can access the decrypted content without access to one of the devices.” This raises 2 questions: First, assuming a user has no physical access to the device and the device was hacked remotely – how easy would it be for the attacker to retrieve the end-to-end encryption deployed by Telegram? Second, if and how are the Telegram’s Secret Chats encrypted on the mobile device?
By definition, it follows that no third parties can access the decrypted content without access to one of the devices.” This raises 2 questions: First, assuming a user has no physical access to the device and the device was hacked remotely – how easy would it be for the attacker to retrieve the end-to-end encryption deployed by Telegram? Second, if and how are the Telegram’s Secret Chats encrypted on the mobile device?
It’s easier to find a vulnerability in a phone and hack it remotely via URL/PDF/Man-In-The-Middle and other attack techniques that I have discussed before. Once you hack a mobile phone, you need to elevate your privileges in order to gain control of the device. This can be easily done using a Kernel exploit.
If you are new to mobile security, I’ve included some examples below that demonstrate how an individual can perform an attack on a mobile device remotely. This type of hack would be even easier for nation-state actors with even more resources, time and money at their disposal:
1. Client-side vulnerability: Chrome exploit – Pwn2Own Autumn 2013
Client-side vulnerability: Chrome exploit – Pwn2Own Autumn 2013
2. Kernel exploit – CVE-2014-3153 (a.k.a – TowelRoot)
Let’s take a look at what I did. I started by creating secret messages within the Android version of the Telegram app with the intention of finding it non-encrypted somewhere. I assumed that the Secret-Chat messages were encrypted in memory, or at least in the local database. Is that too much to ask for from a privacy and security oriented text messenger?
If you take a screenshot as the attacker, a notification will be sent to both users – so one can assume that security and privacy must be a top priority for Telegram. However, to believe that an attacker will take a screenshot instead of taking complete control of the device is a bit naive.
I gave Telegram the benefit of the doubt and did not look for the more common mistakes that you can expect to see in non-security oriented programs. I simulated an attack originating from an App / Client Side vulnerability that gains permissions by running a kernel exploit (I used CVE-2014-3153)- as described above. There are cleaner ways to dump the results, but I just wanted to provide a proof of concept (POC). Telegram has a feature called “Secret Chat” with a lock (see above) that feels secure. I dumped the process memory of Telegram and searched for strings that contain the word I sent and received in the picture above.
There are cleaner ways to dump the results, but I just wanted to provide a proof of concept (POC). Telegram has a feature called “Secret Chat” with a lock (see above) that feels secure. I dumped the process memory of Telegram and searched for strings that contain the word I sent and received in the picture above.
As you can see – the words Woof, Text, Shlookido, Cookiedo, Tambalul and NotSoEncryptedInMemory are, well… not encrypted in the process memory. Any attacker that gains access to the device can read the messages without too much effort. The Secure-Chat messages can be read in clear-text in Telegram’s memory. This discovery prompted me to check to see whether there is an easier way to access the content of the messages – and I was successful.
While Telegram’s communication was supposed to be encrypted (it was broken as well…)
To complete my research I accessed the shell I received previously from running CVE-2014-3153 to look at the App’s files at /data/data/org.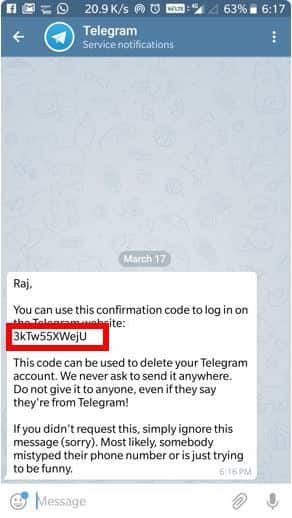 telegram.messenger/ and I discovered a file called Cache4.db in the app’s “files” folder:
telegram.messenger/ and I discovered a file called Cache4.db in the app’s “files” folder:
I assumed “enc_chats”, “enc_tasks_v2”, enc probably stood for encrypted so I fetched this file and examined it. The file contained our secret messages in plain-text!
One of the most interesting features in the Telegram messaging app is the “Delete” messages function. My next attempt was designed to access and retrieve sensitive information previously deleted by the user. I wanted to retrieve deleted messages directly from the memory or cache4.db files.
1. Memory:
I clicked on options->Set Self Destruct to 5 seconds, and I expected the message to be deleted but nothing happened on either phone. It looked like a bug, not a security related issue.
I deleted the message by clicking on options->delete.
An inspection of the cache4.db file showed no signs of the conversation. (A deleted message might be more interesting to an attacker. ) After examining the cache4.db file I looked at the memory and was able to find the original conversation after I had deleted it from the memory.
) After examining the cache4.db file I looked at the memory and was able to find the original conversation after I had deleted it from the memory.
Disclosure Timeline:
Below is the disclosure timeline that we follow as part of the Zimperium Zero-Day Disclosure Policy. We have made several attempts to contact Telegram’s security team and have yet to receive a response from Telegram for over 30 days. For reference, here is a copy of our policy: 30 days zero-day policy.
1. 17/1/2015 – Vulnerability found
2. 18/1/2015 – Vulnerability responsibly disclosed ZVD-2015-0100, ZVD-2015-0101, ZVD-2015-0102 according to our 30 days zero-day policy – no response from vendor.
3. 23/1/2015 – Asked vendor to comment – no response
4. 3/2/2015 – Asked vendor to comment – no response
5. 6/2/2015 – Asked vendor to comment – no response
6. 23/2/2015 – Vulnerability made public
Recommendation
My conclusion is simple.
While Telegram was founded upon a noble goal of providing privacy to consumers everywhere at no cost, they have fallen short of their objective by focusing purely on data-in-transit versus protecting data-at-rest on the mobile device itself. What is regrettable is that I approached Telegram multiple times and have yet to receive a response. Telegram’s so-called powerful encryption is not protecting users any better than any other page or app that uses SSL. If you are using Telegram because you want to ensure your privacy and the privacy of the messages you are sending, be aware that it will not stop sophisticated hackers from reading your messages. We highly recommended adding additional protection to your mobile device that can detect device-level cyberattacks.
In order to better protect critical communication, I would have expected Telegram (or any messaging software) to encrypt chat strings in memory, as-well as encrypting the conversations in the cache4.db file. Zimperium’s Mobile Threat Defense system detected the entire attack chain that was performed in-order to obtain the content of the secret messages
About Zimperium
Zimperium is the leader in Enterprise Mobile Security. The Zimperium Mobile Threat Defense system delivers enterprise-class protection for Android and iOS devices against the next generation of advanced mobile threats. Developed for mobile devices, Zimperium uses patented, behavior-based analytics that sit on the device to protect mobile devices against host and network-based threats wherever business takes them.
The Zimperium Mobile Threat Defense system delivers enterprise-class protection for Android and iOS devices against the next generation of advanced mobile threats. Developed for mobile devices, Zimperium uses patented, behavior-based analytics that sit on the device to protect mobile devices against host and network-based threats wherever business takes them.
Follow me on twitter (@ihackbanme)
Exclusive: Hackers accessed Telegram messaging accounts in Iran - researchers
By Joseph Menn, Yeganeh Torbati
7 Min Read
SAN FRANCISCO/WASHINGTON (Reuters) - Iranian hackers have compromised more than a dozen accounts on the Telegram instant messaging service and identified the phone numbers of 15 million Iranian users, the largest known breach of the encrypted communications system, cyber researchers told Reuters.
Amir Rashidi, an Internet security researcher who has worked with Telegram users who were victims of hacking, works at the offices of International Campaign for Human Rights in Iran, in the Brooklyn borough of New York, U. S., July 27, 2016. REUTERS/Brendan McDermid
S., July 27, 2016. REUTERS/Brendan McDermid
The attacks, which took place this year and have not been previously reported, jeopardized the communications of activists, journalists and other people in sensitive positions in Iran, where Telegram is used by some 20 million people, said independent cyber researcher Collin Anderson and Amnesty International technologist Claudio Guarnieri, who have been studying Iranian hacking groups for three years.
MORE REUTERS TOP STORIES:
Didi's China dominance over Uber offers roadmap for ride-hailing rivals
Commentary: The real reason Washington calls Putin a thug
First Republican lawmaker breaks with party, backs Democrat Clinton
Telegram promotes itself as an ultra secure instant messaging system because all data is encrypted from start to finish, known in the industry as end-to-end encryption. A number of other messaging services, including Facebook Inc's FB.O WhatsApp, say they have similar capabilities.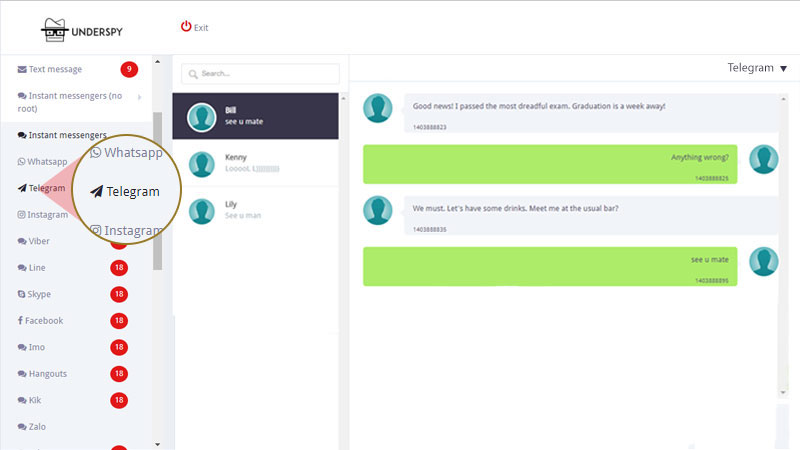
Headquartered in Berlin, Telegram says it has 100 million active subscribers and is widely used in the Middle East, including by the Islamic State militant group, as well as in Central and Southeast Asia, and Latin America.
Telegram’s vulnerability, according to Anderson and Guarnieri, lies in its use of SMS text messages to activate new devices. When users want to log on to Telegram from a new phone, the company sends them authorization codes via SMS, which can be intercepted by the phone company and shared with the hackers, the researchers said.
Armed with the codes, the hackers can add new devices to a person’s Telegram account, enabling them to read chat histories as well as new messages.
“We have over a dozen cases in which Telegram accounts have been compromised, through ways that sound like basically coordination with the cellphone company,” Anderson said in an interview.
Slideshow ( 4 images )Telegram’s reliance on SMS verification makes it vulnerable in any country where cellphone companies are owned or heavily influenced by the government, the researchers said.
A spokesman for Telegram said customers can defend against such attacks by not just relying on SMS verification. Telegram allows - though it does not require - customers to create passwords, which can be reset with so-called “recovery” emails.
“If you have a strong Telegram password and your recovery email is secure, there’s nothing an attacker can do,” said Markus Ra, the spokesman.
Iranian officials were not available to comment. Iran has in the past denied government links to hacking.
ROCKET KITTEN
The Telegram hackers, the researchers said, belonged to a group known as Rocket Kitten, which used Persian-language references in their code and carried out “a common pattern of spearphishing campaigns reflecting the interests and activities of the Iranian security apparatus.”
Anderson and Guarnieri declined to comment on whether the hackers were employed by the Iranian government. Other cyber experts have said Rocket Kitten’s attacks were similar to ones attributed to Iran’s powerful Revolutionary Guards.
The researchers said the Telegram victims included political activists involved in reformist movements and opposition organizations. They declined to name the targets, citing concerns for their safety.
“We see instances in which people ... are targeted prior to their arrest,” Anderson said. “We see a continuous alignment across these actions.”
The researchers said they also found evidence that the hackers took advantage of a programing interface built into Telegram to identify at least 15 million Iranian phone numbers with Telegram accounts registered to them, as well as the associated user IDs. That information could provide a map of the Iranian user base that could be useful for future attacks and investigations, they said.
“A systematic de-anonymization and classification of people who employ encryption tools (of some sort, at least) for an entire nation” has never been exposed before, Guarnieri said.
Ra said Telegram has blocked similar “mapping” attempts in the past and was trying to improve its detection and blocking strategies.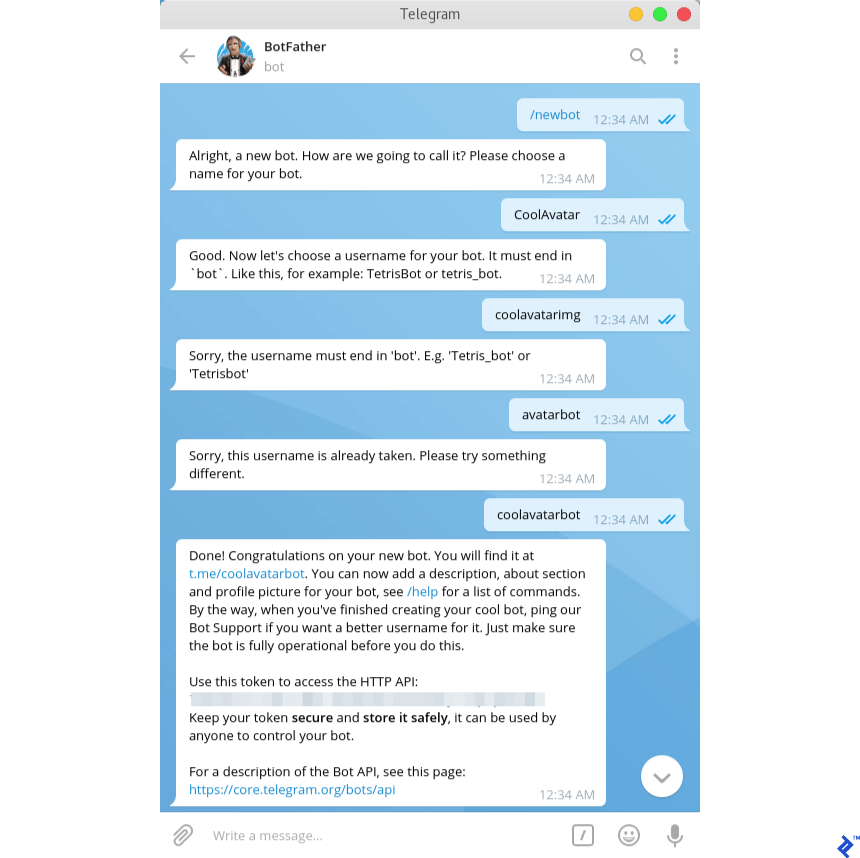
Cyber experts say Iranian hackers have become increasingly sophisticated, able to adapt to evolving social media habits. Rocket Kitten’s targets included members of the Saudi royal family, Israeli nuclear scientists, NATO officials and Iranian dissidents, U.S.-Israeli security firm Check Point said last November.
POPULAR IN THE MIDDLE EAST
Telegram was founded in 2013 by Pavel Durov, known for starting VKontakte, Russia’s version of Facebook, before fleeing the country under pressure from the government.
While Facebook and Twitter are banned in Iran, Telegram is widely used by groups across the political spectrum. They shared content on Telegram “channels” and urged followers to vote ahead of Iran’s parliamentary elections in February 2016.
Last October, Durov wrote in a post on Twitter that Iranian authorities had demanded the company provide them with “spying and censorship tools.” He said Telegram ignored the request and was blocked for two hours on Oct. 20, 2015.
20, 2015.
Ra said the company has not changed its stance on censorship and does not maintain any servers in Iran.
After complaints from Iranian activists, Durov wrote on Twitter in April that people in “troubled countries” should set passwords for added security.
Amir Rashidi, an internet security researcher at the New York-based International Campaign for Human Rights in Iran, has worked with Iranian hacking victims. He said he knew of Telegram users who were spied on even after they had set passwords.
Ra said that in those cases the recovery email had likely been hacked.
Anderson and Guarnieri will present their findings at the Black Hat security conference in Las Vegas on Thursday. Their complete research is set to be published by the Carnegie Endowment for International Peace, a Washington-based think tank, later this year.
Reporting by Joseph Menn in San Francisco and Yeganeh Torbati in Washington; Additional reporting by Michelle Nichols at the United Nations and Parisa Hafezi in Ankara; Editing by Jonathan Weber and Tiffany Wu
how to hack telegrams read correspondence, messages
How to read someone else's Telegram chat? We will tell you in the article several ways how to read other people's messages in Telegram.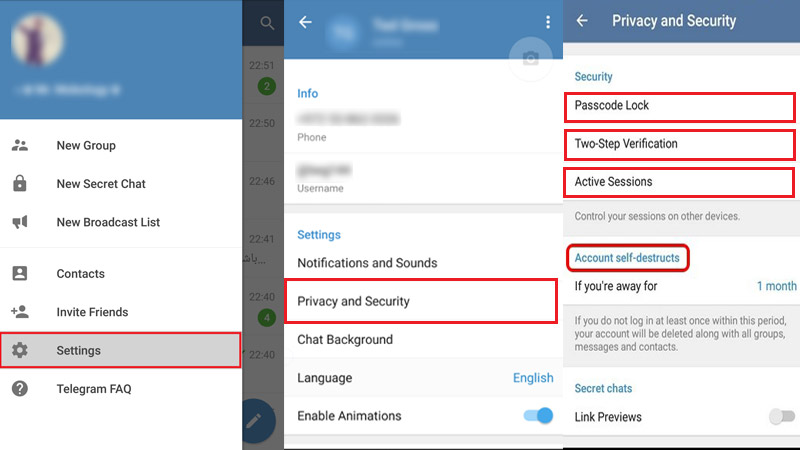 So, let's begin!
So, let's begin!
Telegram is one of the most secure instant messengers that exist today. The service cares about the privacy and confidentiality of its users, so the issue of hacking the application in order to read other people's messages in Telegram remains open. To protect the program from hacking, developers implement various encryption and encoding methods. According to them, it is impossible to read the cipher, and those who still manage to gain access to someone else's account and Telegram messages are entitled to a reward of $ 200,000. nine0003
Let's see if this is possible.
How to hack Telegram
How to read other people's messages in Telegram? Here are a few ways an attacker can do this:
- Gaining access to the user's phone. In this case, you can log into someone else's account and get access to messages in a matter of minutes, which cannot be said about this method, when a person finds out the phone number associated with the profile - he will have to guess the password received via SMS messages, which is quite time consuming process; nine0016
- Hacking a gadget running Telegram.
 This method of accessing messages was discovered recently by a hacker. He claimed that the phone's memory contained unencrypted messages that could be read by scanning the device's database;
This method of accessing messages was discovered recently by a hacker. He claimed that the phone's memory contained unencrypted messages that could be read by scanning the device's database; - Detection of weak parts of the code. There is an opinion that a certain part of the code is still not brought to a high level of security, and the exchange of codes and ciphers can contribute to the emergence of “holes” in data protection. If a hacker finds these gaps, which is very difficult, he will be able to hack the profile and get access to the Telegram user's private messages; nine0016
- Code change at the beginning of communication. To perform this action, you need to study the company's server. Since this action is almost impossible, neither the program nor the Telegram user himself will detect the hacking in the future. The difficulty lies in the fact that you need to know both the initial code and the changed one;
- Account attack by special services. This option implies not so much hacking the application itself, but obtaining data from the entire device.
 Those users who install the Telegram messenger on another computer without completing active sessions on the previous device are especially at risk; nine0016
Those users who install the Telegram messenger on another computer without completing active sessions on the previous device are especially at risk; nine0016 - Hacking due to errors that occurred during the creation of the Telegram application. To do this, you need to constantly check the compliance of the program code and its protocol.
It makes no sense to say that the implementation of each of these methods requires great knowledge in the field of IT technologies and programming, it is almost impossible to perform these actions.
People who practically managed to hack someone else's Telegram got a lot of money, and the problems they found were fixed. nine0003
Ways to protect your Telegram account
In order to avoid hacking your Telegram profile by intruders, you must do the following:
- Always keep an electronic device with you, regularly check its presence;
Do not give your phone to strangers, even if you trust them. It takes a few minutes to hack an account if the attacker has access to the device;
It takes a few minutes to hack an account if the attacker has access to the device; - Use different passwords and patterns on your smartphone's lock screen; nine0016
- Set up a double password in the Telegram settings;
- Regularly check active sessions and end extraneous sessions;
- Install the latest versions of the Telegram application;
- Think of a complex, long password that is impossible to pick up.
These actions significantly reduce the risk of hacking your Telegram account, so it is not recommended to neglect them. Despite all the vulnerabilities, Telegram is still one of the most reliable applications. nine0003
How to delete a contact in Telegram - details and nuances
Telegram notifications do not come
The expert told how they can read your correspondence in Telegram :00+03:00
2021
https://1prime.ru/telecommunications_and_technologies/20210520/833703094.html
The expert told how they can read your correspondence in Telegram
Technology
News
en-RU
https://1prime.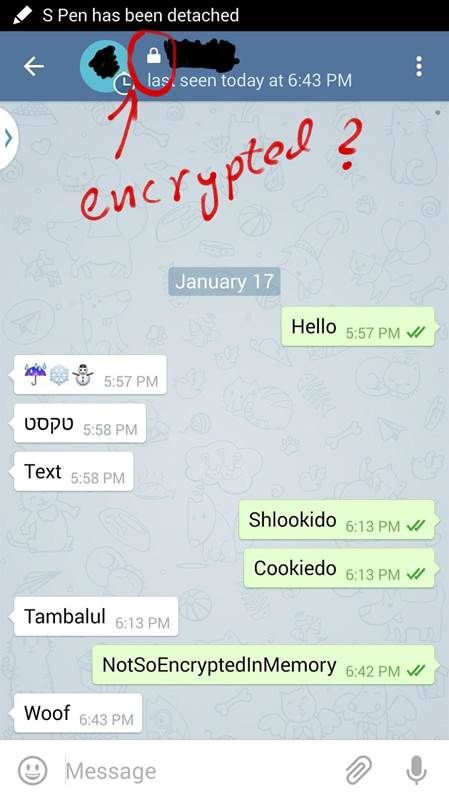 ru/docs/terms/terms_of_use.html
ru/docs/terms/terms_of_use.html
https://russiatoday.rf
Soulmate, colleague-opponent at work or any other a person who has access to your phone can theoretically and practically gain access to chats and an account... ru/images/83314/55/833145538.jpg
1920
1440
True
https://1prime.ru/images/83314/55/833145538.jpg
https://1prime.ru/images/83314/55/8331455557.jpg 9000 1920 1920 1920
1080
True
https://1prime.ru/images/83314/55/833145537.jpg
https://1prime.ru/images/83314/83314525.jpg
00 1920 9000 920
true
https://1prime.ru/telecommunications_and_technologies/20210428/833559569.html
Economic Information Agency Prime
1
5
4.7
9000
7 495 645-37-00
Federal State Unitary Enterprise “Russia Today”
https: // Russian-Russian day.
Economic Information Agency Prime
1
5
4.7
9000
7 495 645-37-00
FSUE MIA Today
HTTPS: // Russian SAVADARDS/
Agency economic information PRIME
1
5
4. 7
7
96
7 495 645-37-00
Federal State Unitary Enterprise “Russia Today”
HTTPS: // Russian SAYASYA.RF/AVARDS/
Agency of Economic Information Prime
1 1 1
5
4.7
9000
7 495 645-37-00
FSUE MIA Russia Today
https: // Russianase-earnads.rf/Awards/
Prime Information Economic Information Prime
1
5 nine0003
4.7
96
7 495 645-37-00
Federal State Unitary Enterprise MIA Rossiya Segodnya
A significant other, a colleague-opponent at work or any other person who has access to your phone can theoretically and practically gain access to chats and a Telegram account. To do this, it is enough to peep the verification code in time, Olga Sokolova, partner of the Digital Guru social media analytics agency, told the Prime agency. nine0204 Russians are warned about the risks of fraud in Telegram
You can check if someone used your Telegram account in the security section.