How to hack into someones instagram reddit
how to hack someones instagram reddit?
Answer
- One way is to try to guess the person’s password,
- or to use a program that can hack into the account. However,
- these methods are often not successful and can be risky.
- A more reliable way to access someone’s Instagram account is to ask them for their login information.
Use Someones Instagram WITHOUT Knowing The Login! (TRY THIS)
How to Hack Instagram Account! Is it Possible? MUST WATCH 😲
How do Instagram accounts get hacked?
There are many ways that an Instagram account can be hacked. One way is if the user’s password is easily guessed. Another way is if the user’s account is compromised by malware.
Can someone hack my Instagram password?
Yes, someone could hack your Instagram password. However, there are ways to help protect your account, such as using a strong password and enabling two-factor authentication.
Can someone hack your Instagram through a link?
Yes, it’s possible for someone to hack your Instagram account through a link. They could do this by stealing your login information or by installing malware on your device that gives them access to your account. To protect yourself, always be careful about the links you click on, and make sure to use strong passwords for your accounts.
Can a hacker hack a deleted Instagram account?
Yes, a hacker can hack a deleted Instagram account. If the account was not deleted using the Instagram app or website, the account may still be accessible to the hacker. The hacker could also use spyware or another method to access the account information.
The hacker could also use spyware or another method to access the account information.
What’s Instagram’s phone number?
Instagram’s phone number is not listed publicly.
Can I get hacked by opening a message?
Yes, you can get hacked by opening a message. However, the likelihood of this happening is relatively low, as most malicious messages are designed to exploit vulnerabilities in software programs or operating systems. If you are careful about what messages you open and where you click, you can reduce your risk of being hacked.
Can someone hack my Instagram with my phone number?
There is no one-size-fits-all answer to this question, as the risk of someone hacking your Instagram account depends on a variety of factors, such as the strength of your password and how much information someone has about you. However, in general, it is safer to use a unique password for each account you create, and to avoid sharing too much personal information online.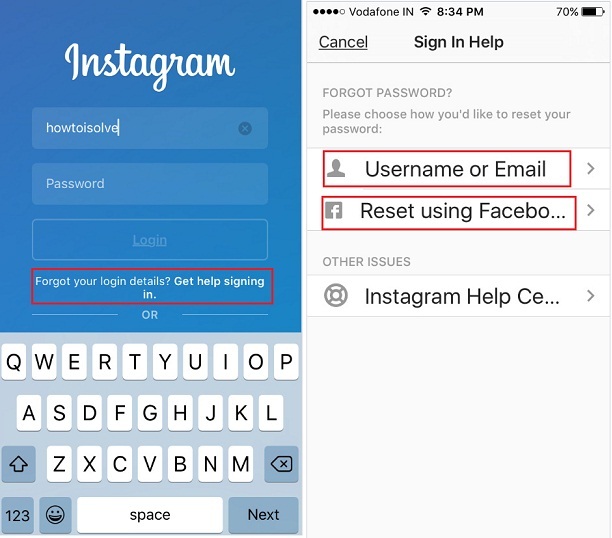
Can you get a virus on Instagram?
Yes, you can get a virus on Instagram. Malicious links and files can be sent through direct messages or comments, and can infect your device if you click on them. Be careful what links you click on, and only download files from trusted sources.
Can Instagram be hacked even with two-factor authentication?
Yes, Instagram can be hacked even with two-factor authentication. However, two-factor authentication makes it much more difficult for someone to hack your account.
How do you get 2 step verification on Instagram?
To get two-step verification on Instagram, you first need to have a verified account. Once you have a verified account, go to your settings and scroll down to “Two-Step Verification.” Tap “Turn On” and follow the instructions.
Is my IG account banned?
There’s no easy answer to this question. It depends on the reason your account was banned in the first place. If you were using fake or spammy followers, or violating Instagram’s terms of service, then it’s likely that your account has been banned. However, if you were simply using unpopular or controversial content, then it’s possible that your account was temporarily suspended and is now back online.
It depends on the reason your account was banned in the first place. If you were using fake or spammy followers, or violating Instagram’s terms of service, then it’s likely that your account has been banned. However, if you were simply using unpopular or controversial content, then it’s possible that your account was temporarily suspended and is now back online.
Can you clone an Instagram account?
Yes, you can clone an Instagram account. This is done by creating a new account and then importing the images and followers from the original account.
Can 2 step verification be hacked?
Yes, it’s possible for someone to hack into your account if they have your login information and 2-step verification code. However, if you have a strong password and enable two-step verification, it will make it much more difficult for someone to gain access to your account.
Can I find out who tried to log into my Instagram?
Yes, you can find out who tried to log into your Instagram account. To do this, open the Instagram app and go to your profile. Tap on the three lines in the top left corner of the screen and select “Settings.” Scroll down and tap on “Security.” Under “Logging In,” you will see a list of devices that have been used to log into your account. If you see a device that you don’t recognize, tap on it and then select “Remove.
To do this, open the Instagram app and go to your profile. Tap on the three lines in the top left corner of the screen and select “Settings.” Scroll down and tap on “Security.” Under “Logging In,” you will see a list of devices that have been used to log into your account. If you see a device that you don’t recognize, tap on it and then select “Remove.
What is my Instagram key?
Your Instagram key is the unique code that allows you to log in to your account. You can find this code on the settings page of your account.
How any Instagram account could be hacked in less than 10 minutes
SBN News Security Bloggers Network
by Graham Cluley on July 15, 2019
A security researcher has been awarded $30,000 after discovering a serious vulnerability that could potentially have put any Instagram account at risk of being hacked.
Sponsorships Available
Following a recent increase in rewards offered for the discovery of critical account takeover vulnerabilities in Facebook and Instagram, Indian security researcher Laxman Muthiyah chose to take a close look at the photo-sharing service.
As he describes in a blog post, Muthiyah explored whether there might be a vulnerability in how Instagram handled password reset requests for users who have forgotten their login credentials.
Mutiyah found that when users asked for a password reset via Instagram’s web interface, the site would email a reset link to the user’s email account.
After a few minutes of testing Mutiyah couldn’t find any bugs, and so turned his attention instead to how smartphone users recover access to their Instagram accounts.
What Mutiyah found was that Instagram offered the option for users locked out of their accounts to request that a six-digit secret security code be sent to their mobile phone number or email account. If that passcode is entered, a user can regain access to their Instagram account.
In theory, if a hacker could enter the six-digit security code they would be able to break into the Instagram account (and reset the password locking out the legitimate owner. )
)
Now, that passcode could potentially be stolen if a hacker had somehow managed to gain access to their target’s email account, or had hijacked control of their victim’s mobile phone number via a SIM swap scam. But Mutiyah wondered if there might be another way to break into accounts if neither of those options were available.
Mutiyah realised that all a hacker would need to do was enter the correct six digit code – a code that could be any combination between 000000 and 999999 – within the ten minute window Instagram would accept the code before expiring it.
Up to one million numbers to be entered within ten minutes, in order to change an Instagram account’s password.
Of course, the likes of Facebook and Instagram aren’t going to simply sit quietly as an automated script tries a brute force attack to guess the correct security code. Instead they have rate-limiting in place to detect when multiple attempts have been made to get past the security check and slow down subsequent attempts – meaning the ten minute window of opportunity expires.
In Mutiyah’s tests he discovered that when he cycled through 1000 attempts to guess an Instagram account’s security codes, 250 of them went through and the subsequent 750 requests were rate limited.
However, after a few days of testing the researcher was able to discover that Instagram’s rate limiting mechanism could be bypassed by rotating IP addresses (in other words, not using the same computer to brute force the recovery code) and sending concurrently from different IP addresses:
“Sending concurrent requests using multiple IPs allowed me to send a large number of requests without getting limited. The number of requests we can send is dependent on concurrency of reqs and the number of IPs we use. Also, I realized that the code expires in 10 minutes, it makes the attack even harder, therefore we need 1000s of IPs to perform the attack.”
Mutiyah says that he used 1000 different machines and IPs to achieve easy concurrency, and sent 200,000 requests in his tests. He shared a YouTube video with Facebook and Instagram’s security team to demonstrate the attack in action:
He shared a YouTube video with Facebook and Instagram’s security team to demonstrate the attack in action:
Of course, 200,000 requests isn’t quite the million requests that would be necessary to guarantee the correct recovery passcode would be entered to allow an Instagram account to be hijacked.
Mutiyah’s investigation concludes that in a real attack, 5000 IP addresses would be needed to hack an Instagram account. Although that sounds like a large number, it can actually be easily achieved at a low price (Mutiyah says there would be approximately US $150 cost if a cloud provider like Google or Amazon was used).
All Instagram users should be grateful that Laxman Muthiyah chose to responsibly disclose the security vulnerability to Instagram’s security team rather than monetise his discovery by selling it to online criminals.
It’s easy to imagine that a technique like this would be very attractive to many hackers interested in compromising Instagram accounts, and they might be prepared to pay much more than the $30,000 Muthiyah received in the form of a bug bounty.
All internet users are reminded to better secure their online accounts with strong, unique passwords and to enable two-factor authentication wherever possible.
*** This is a Security Bloggers Network syndicated blog from HOTforSecurity authored by Graham Cluley. Read the original post at: https://hotforsecurity.bitdefender.com/blog/how-any-instagram-account-could-be-hacked-in-less-than-10-minutes-21409.html
Graham Cluley critical vulnerability, Industry News, instagram vulnerability, SIM swap
- ← GUEST ESSAY: 6 unexpected ways that a cyber attack can negatively impact your business
- Cybersecurity analyst salary →
Step 1 of 6
16%
Where is your sensitive (protected/regulated/proprietary) data located? (Select all that apply)On-prem
IaaS (AWS, Azure, GCP, etc. )
)
SaaS (Microsoft 365, Salesforce, Workday, etc.)
Corporate-owned devices (mobile, laptops, etc.)
Employee-owned devices (mobile, laptops, etc.)
How to hack an Instagram account: proven methods
To hack an Instagram account, you must use spyware (pre-installed on your computer or phone), guess the password ou use brute force programs to directly access the selected you profile.
It is important to note that hacking is a crime so you must be very careful with the methods you use as you may get into legal trouble which can be severely punished in many countries around the world. nine0009
There are many reasons why you want to hack Instagram account , either to enter personal information, to control the content that your children see through this social network, to recover a lost account, among other things.
With this in mind, in this article you will see methods that can be used to achieve this goal effectively and quickly. Also, some processes will be rejected so as not to waste time.
Also, some processes will be rejected so as not to waste time.
Via download software
Forest « Keyloggers are access keys to a particular account. They were created for to track activities on a specific device and save it in a document record or send it directly to the program administrator. Next, you will see how to hack an Instagram account using keyloggers.
FlexiSPY
FlexiSPY is another program that is great for spying or hacking your Instagram account. Its keylogging feature is is one of the most attractive features of which improves its service and offers advanced features that you can use in other applications. It can be installed on computers, Android and iOS mobile phones.
In addition to full phone recording, will give you access to device location tracking, phone call recording, Internet usage management and more. Like other apps, you will need to install FlexiSPY on the device you want to hack . To access your web portal
To access your web portal
You can try the FlexiSPY program from the link
mSpy
This program is available on for Android and iOS phones and is among the favorite spy or Instagram account hacks. In fact, you can have access to all mobile phone activities, be it browsing history, messaging, photo gallery and more. nine0009 However, if you want utiliser spy to hack instagram then you must unsubscribe which varies between 15 or 20 euros in the year . Similarly, you will need to have access to the phone number of the account you want to hack and allow it to be downloaded to the device. Once installed, it will not be easy to detect with the naked eye. You will even have to factory reset your phone to erase mSpy. to get this program. nine0009 You can try the mSpy program from the link Spyzie is the most complete program to hack Instagram and other social networks like Facebook, Snapchat, WhatsApp and others. After installation Spyzie will remain completely hidden . You will have a record of all activities performed on this phone, whether browsing, sharing content on networks, call log, etc. Instagram Spyzie
 It works for both Android devices and iOS phones and the like. mSpy, you must have direct access to the mobile phone that you want to hack to properly configure and install the program.
It works for both Android devices and iOS phones and the like. mSpy, you must have direct access to the mobile phone that you want to hack to properly configure and install the program. Access password recovery
After resetting your password, you will be able to access your Instagram account without any inconvenience. However, as mentioned earlier, this method is not practical. It is important that you have an email password associated with your Instagram profile. . Otherwise, this option will not work.
Through InstaRipper
With this software you will be able to crack a password by force, that is, using thousands of possible password combinations in the shortest possible time. From InstaRipper you will be able to access account and more you will pourrez change your IP address after 3 failed attempts so you won't get banned and tracked.
However, the counterproductive part of this tool is that it you have to be very nimble and fast because if a person turned on the login notification, he will quickly change the access password.
Trying to guess password
This is a somewhat unorthodox method that you can always try. This consists of guessing the account password by knowing certain personal details of the person . Previously, this method would have been one of the first to be used because passwords were simpler. Now, this is a little tricky due to the great creativity that users have in assigning their keys.
Even if you don't have enough information about the person whose Instagram account you want to hack, it's not recommended to use this process. As a result, Instagram automatically locks the account after repeated unsuccessful attempts enter the password. Basically, it sends a direct email notification so that you can unblock it without any problems.
Using apps
It should be noted that this is not a free app or website that can hack 's Instagram account. In fact, the following list will mention some of the suspicious or scam apps that trick users into offering hacking services, but in reality they are not:
- Xploitz - It's ne fact that is promoting other apps that claim to do hack work, but this is more of a reality check.
- InstaRipper: This is a app that can be downloaded on Android, iOS, Windows or macOS systems. However, since this is not from an official store, you can use at your own risk and take responsibility for .
- Instagram: once you have login that person's username, it tells you that the account has been successfully hacked and that you need to upload a file containing data for that profile. It is not right. Account file not loaded .
- Ighak and InstaHak : Works the same as "InstaLeak". You must write the username you want to hack, but you must also add an email address. Once the page claims the account has been hacked, it asks to install two programs and run them for 30 seconds.
Please note must underline that it is not possible to hack Instagram account or other social network in using phone number or IMEI code of phone . If any web page or application asks you for this information, it will most certainly be done with malicious intent.
How to avoid being hacked
Faced with possible cyberattacks from certain hackers, we need to fortify ourselves and know avoid account being hacked, be it on Instagram, Facebook, Snapchat and other social networks. This will leave a list with a number of tips and tricks that you need to follow to achieve your goal:
This will leave a list with a number of tips and tricks that you need to follow to achieve your goal:
- Strengthen the security of your password . The longer it is and the more characters it contains, the more difficult it will be to access your profile.
- Customize your privacy: It's harder to log into a profile if it's private. So go to your Instagram account settings and enable private mode by following this path: Profile > Three horizontal lines > Settings > Privacy > Personal account ".
- Constantly check for connection activity: if you have opened Instagram on other devices, go to " Settings > Security > Login Activity And close the sessions you don't recognize.
- Enable 2-Step Verification: In the same section " Security ", you will find the option " 2-Step Verification ". That is, you can download the application for to receive security codes every time you log in or the code is sent to the security number you register.
- Lock phone: Strengthen the security of your apps by blocking the sharing of your appareil . Add unlock pattern, PIN or fingerprint . This ensures that no one will download or install programs without your consent. nine0144
As you can see, the procedure for to hack Instagram account can be somewhat complicated or easy to perform depending on the tool you use for this purpose.
Remember to use any of these methods to the best of your ability with awareness, caution and responsibility, because hacking is not a legal activity in many countries around the world .
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act. nine0009
So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act. nine0009
What could have happened
First, let's figure out how a stranger could get access to your account at all. There are several options here.
Data breach and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on. nine0009
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password. nine0009
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It is possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account. nine0009
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there. nine0009
And what about?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing. nine0009
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done by pressing a single button in the Security and login section in the settings. This will reset the access tokens.
- Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them.
If they managed to do this, change it back to yours. nine0144
- Set a new password that is strong and one you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress. nine0144
Tips
Christmas and security
Many famous break-ins began during the Christmas holidays. A few simple tips will reduce your risk of becoming the next victim.
Is it safe to use Avast in 2023?
Avast solutions have a good reputation, but several incidents cast doubt on their reliability.