How to hack facebook account by phishing
How Do Hackers Take Over a Facebook Account? | Small Business
By Clare Edwards
Your Facebook account is a useful commodity for online criminals. Not only can they potentially access your personal information -- your full name, location, details about your life -- but your Facebook friends' as well. Your account can also be used to spread spam and malware to other users, compromising their security. To gain access they may use malicious software, rogue applications and social engineering. Protect your account by following sensible guidelines.
Login Information
-
If someone obtains your login information, he can access your account anytime he wants. Choose strong passwords -- at least eight characters, containing letters and numbers. Single words, even long words, are too easy to guess. Don't leave your Facebook account logged in on a shared computer or public terminal. Anyone could commandeer your account. Don't leave your Facebook password lying around or give it to anyone else.
-
If the email you use with your Facebook gets hacked, you may lose control of your Facebook account too. Your email login information is valuable and you should look after it. Follow the same guidelines as for your Facebook password: pick a strong password, don't leave your email account logged in where someone else could access it and don't give away your password.
Malware
-
Malware -- malicious software -- is another tool that a hacker can use to take over your Facebook account. Keyloggers are programs that record everything you type into your computer. The person controlling the keylogger then has access to your login information. Other forms of spyware can steal information from your computer that may give someone else access to your Facebook account.
Rogue Applications And Infected Links
-
You can use applications, also known as apps, to give your Facebook new features, play games or answer quizzes.
 Unfortunately, not all apps are what they pretend to be. Rogue apps ask for posting access to your Facebook account. If you give them access, they can post spam to your account or your friends' walls and send messages via Facebook's private message system or instant messenger. Some rogue apps and links can even infect your computer with malware; an example is the Koobface worm that places malware on your system and hijacks your account to post spam. Be very careful what links you click on Facebook and don't give too much access to any application.
Unfortunately, not all apps are what they pretend to be. Rogue apps ask for posting access to your Facebook account. If you give them access, they can post spam to your account or your friends' walls and send messages via Facebook's private message system or instant messenger. Some rogue apps and links can even infect your computer with malware; an example is the Koobface worm that places malware on your system and hijacks your account to post spam. Be very careful what links you click on Facebook and don't give too much access to any application.
Social Engineering
-
Instead of high-tech attacks, social engineering relies on confidence tricks to steal your data. In the case of Facebook, this is generally done by "phishing." You receive an email that looks as if it came from Facebook. It seems real but this email comes from a scammer. It will often have an urgent tone, for example telling you that your account will be shut down if you don't respond with your password or log in via a link in the email.
 If you do either of these, your login information will be stolen. Avoid phishing mails by setting your spam filter to block junk mail. Always log into Facebook via your bookmarks or by typing Facebook.com into your browser -- that way you know you are on the real Facebook site, not a counterfeit operated by phishers.
If you do either of these, your login information will be stolen. Avoid phishing mails by setting your spam filter to block junk mail. Always log into Facebook via your bookmarks or by typing Facebook.com into your browser -- that way you know you are on the real Facebook site, not a counterfeit operated by phishers.
References
- PCMag.com; How Did My Facebook Get Hacked?; Neil J. Rubenking; March 2011
- Securelist; Keyloggers: How They Work and How to Detect Them"; Nikolay Grebennikov; March 2007
- Naked Security; Photo Tagged as a Facebook Bunnygirl? Beware Viral Scam; Graham Cluley; April 2011
Writer Bio
Clare Edwards has been providing Internet content since 1998. She has written and translated for a variety of markets: everything from technical articles to short fiction and essays on alternative spirituality. She holds a certificate of higher education in electronics and audio arts from Middlesex University.
How to Hack Facebook Accounts: 5 Common Vulnerabilities
Facebook is a free and popular social networking site that makes it easy for users to connect and share posts with their friends and family members.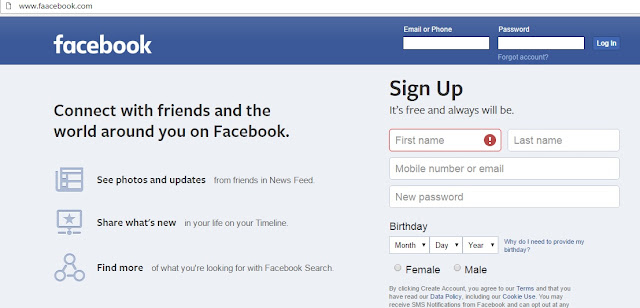 Since Facebook is a popular social media platform, there is an increased interest from cybercriminals to hack Facebook accounts.
Since Facebook is a popular social media platform, there is an increased interest from cybercriminals to hack Facebook accounts.
This article will talk about the five common vulnerabilities and what you can do to prevent cybercriminals from hacking your Facebook accounts.
Facebook Hacks and Vulnerabilities:
- Weak Passwords
- Phishing Emails
- Man in The Middle (MITM)
- Remote Keyloggers
- Denial of Service (DoS)
1. Weak Passwords
Hackers can easily hack Facebook accounts by guessing or performing a brute force attack if the password is easy and commonly used such as a nickname, phone number, partner’s name, pet name, just to name a few. Once the hacker has obtained your password, they have the ability to do whatever they want with your account.
How to Protect Against Weak Passwords
Users should implement a strong password that combines numbers, symbols, space bars, and lower and uppercase letters.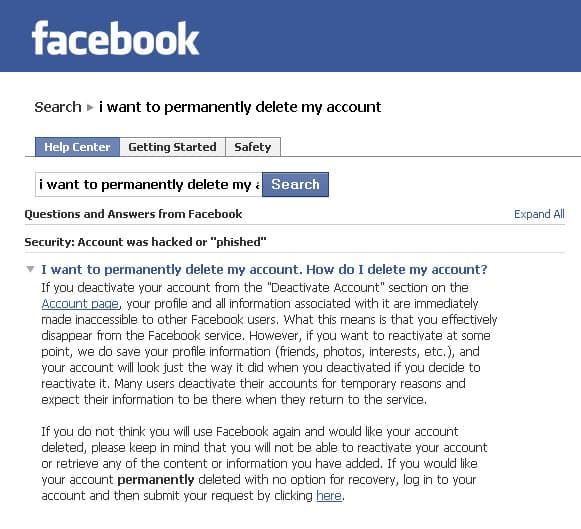 It is important that the password they create for their Facebook account is unique and not the same password that is used for their other social media or email accounts.
It is important that the password they create for their Facebook account is unique and not the same password that is used for their other social media or email accounts.
This would reduce the risk of your account from being compromised. A usual site to verify that your accounts are safe is HaveIBeenPwned. Here you can see if your credentials have been leaked to the public.
2. Phishing Emails
“Facebook will never ask you for your password in an email or send you a password as an attachment”
Phishing emails are an easy way for attackers to hack Facebook accounts. An attacker can create fake emails to make it look like they were sent from Facebook. These are some examples of what the emails may look like:
- Notifications about friend requests, messages, events, photos and videos
- False claims that you went against their Community Standards
- Warnings that something will happen to your account if you don’t update it or take a certain action
- Claims or offers that sound too good to be true (such as winning a Facebook lottery)
How to Protect Against Phishing Attacks
Users should be educated and informed on the characteristics of phishing emails in order to keep an eye out for them.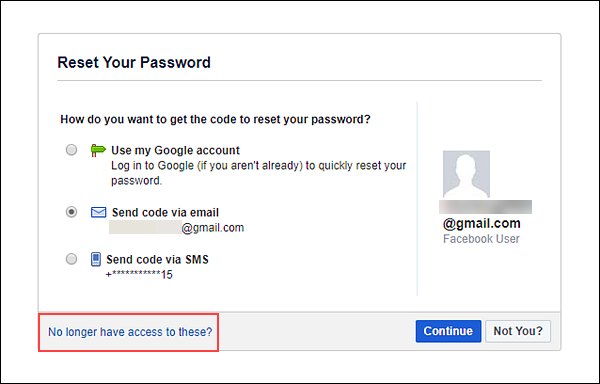 Here is what you can do:
Here is what you can do:
- Do not click on any links or open any attachments from a suspicious email
- Do not respond to the suspicious emails especially ones that ask for your password, social security number, or credit card information
- Do no enter personal information from a pop-up screen (note: legit companies would never ask for personal information via a pop-up screen)
- Keep an eye out for misspellings in the contents of the email
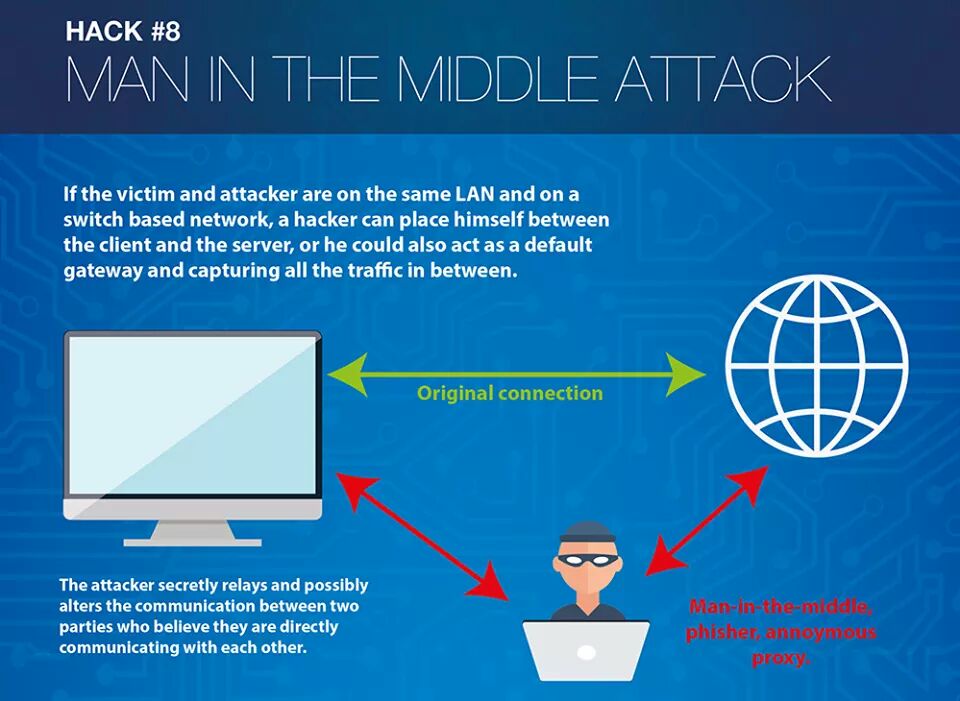
3. Man In The Middle (MITM)
A man in the middle attack may occur when a user unknowingly connects to a fake WiFi connection. This is another technique hackers can use to hack Facebook accounts. Most of the time you may not be able to tell which WiFi is real or not because it is public and is normal to bring you to a login page where you are asked to enter in your email and a password before granted internet access. Again, without you knowing, the attacker has recorded this information and can test out these login credentials on other social media platforms.
How to Protect Against Man In The Middle Attacks
You should never connect your mobile device or laptop to a public WiFi network because they are not secure and are an easy way for hackers to obtain information. If you want to connect to public WiFi then I would recommend using a VPN with it to make sure that your connection is safe.
4. Remote Keyloggers
A hacker first needs to access your mobile device or laptop to install a piece of software to record whatever you type on your device. Once installed, anything that is typed (password, login credentials, bank information, etc.) will be recorded and can be viewed by the hacker. This is a hidden technique for an attacker to hack Facebook accounts. For example, if an attacker has somehow hacked into your laptop and installed a keylogger software, then anything you type will be recorded for the attacker. Not only would your Facebook credentials be recorded but also your bank credentials, email accounts, and whatever other accounts you have.
How to Protect Against Remote Keyloggers
- Do not use third party keyboard applications
- Do not open any attachments or click on links in the email message as the keylogger may be embedded in the attachment
- Install anti-spyware applications to help detect, disable, quarantine software-based keyboard loggers (Norton)
5. Denial of Service (DoS)
A denial of service attack “is a malicious attempt to affect the availability of a targeted system, such as a website or application, to legitimate end users” (AWS). Attackers will typically generate a large volume of packets or requests to overwhelm Facebook. When this type of attack occurs, users will have issues accessing Facebook and won’t be able to log in.
How to Protect Against Denial of Service Attacks
- Monitor the network so that you are aware of what normal incoming traffic looks like
- Implement web application firewall
- Understand common signs of a denial of service attacks so that you can mitigate the attack as early as possible
Final Thoughts on Facebook Hacks and How to Prevent Them
These are the five common vulnerabilities that hackers use to hack Facebook and how to protect against each vulnerability. There are definitely many more ways and even new methods that are not publicly known yet to hack Facebook accounts.
There are definitely many more ways and even new methods that are not publicly known yet to hack Facebook accounts.
Hackers are always one step ahead in finding new techniques where prevention might not be possible at first. Therefore, users and organizations (as the last vulnerability is targeted towards organizations) should make sure that they do everything they can to ensure that their account and site are secure.
Check out our podcast on big tech companies.
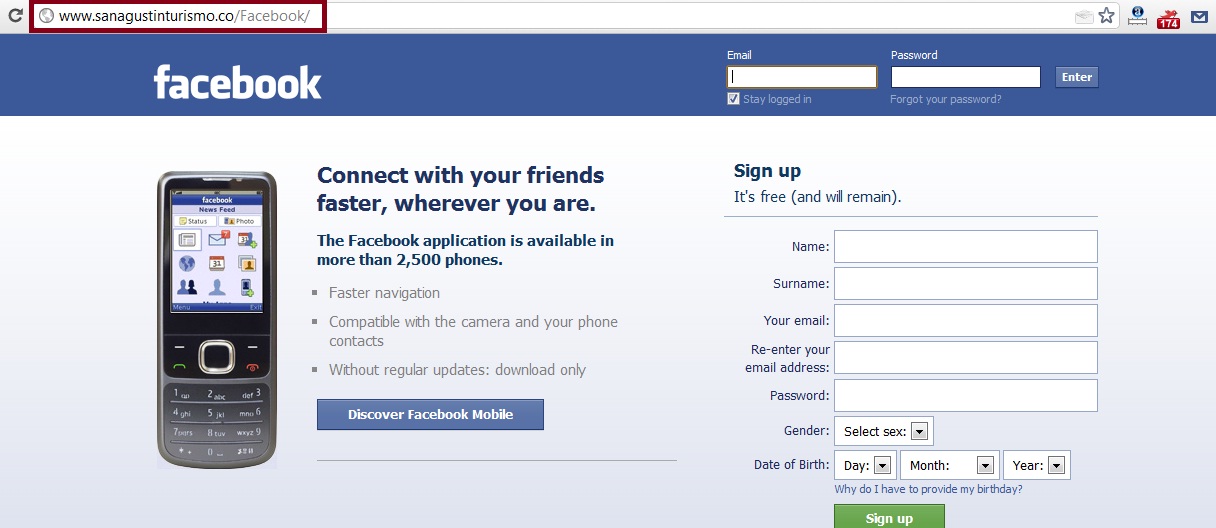
How to hack Facebook account and protect it
How to hack Facebook account? Is there an online tool or software to crack Facebook passwords? Today it is one of the most popular queries on the Internet. We'll cover how hackers can easily hijack someone's social media account in minutes, and how you can prevent it. After all, you will not be vulnerable to hacking if you understand how this mechanism works.
There is no specific hack tool that will allow you to do the former, but there are many websites on the web that claim otherwise. You will be asked to fill out a lot of forms, and in the end you will not receive anything, so do not waste your precious time on this. Some of the methods below apply not only to Facebook, but also to Google, Twitter, Yahoo, etc.
1. Phishing
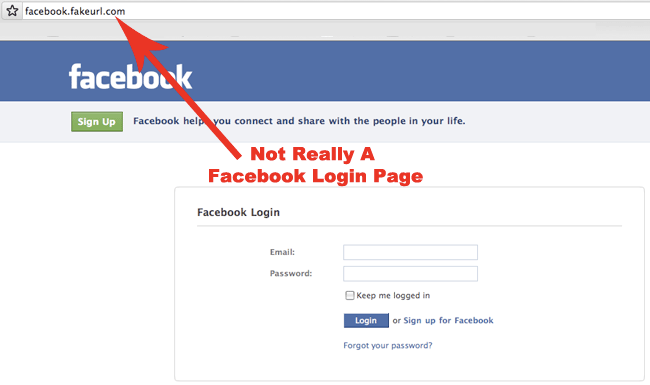
The most successful method of hacking a Facebook account is phishing. It allows not only hackers but also people without technical knowledge to easily crack an account password in just a few minutes. This is a type of Internet fraud, the purpose of which is to gain access to confidential user data - logins and passwords. Phishing is the most common method of hacking Facebook passwords. It is easy for those with little technical knowledge to create a phishing page, which is why it is so popular. A page of a supposed website is duplicated in order to steal the user's password or other sensitive information such as credit card information. nine0003
nine0003
After a user lands on a fake page that is indistinguishable from the original, scammers try various psychological tricks to induce him to enter his username and password on the fake page. The page has a different but similar URL, such as fakebook.com and faecbook.com.
How does it work?
A programmer is creating a Facebook login page with some scripts. It places this fake login page at https://www.facebouk.com/make-money-online-tricks. The hacker sends a message to one of the users: “Hi, I found a free trick to make money online, be sure to check out https://www.facebouk.com/make-money-online-tricks-free.” The user follows the link, sees the Facebook login page, and enters their username and password. His data at this time is sent to the programmer. nine0003
Hackers can contact you in a variety of ways - email, Facebook private message, or website ads - but any of the links will take you to the social network login page. Pay attention to the URL of the page you clicked on, as they are always different from the original. Also check if the address bar has the HTTPS security symbol. HTTPS differs from regular HTTP in that it provides additional security in the transfer of information between the user and the site. nine0003
Also check if the address bar has the HTTPS security symbol. HTTPS differs from regular HTTP in that it provides additional security in the transfer of information between the user and the site. nine0003
2. Social engineering
This is the second most common method of hacking Facebook accounts. It does not require a lot of knowledge to use it. Social engineering is basically the process of gathering information about someone whose account needs to be hacked. The information may include the user's date of birth, the user's or relatives' mobile phone number, pseudonym, mother's name, place of residence, etc.
How does it work?
When registering with Facebook, we are asked to answer a security question. This is a way to confirm the rights to an account in case of loss of access to it. The most common questions - What is your nickname? What was the name of your first grade teacher? Where you were born? It can also be any non-standard question thought up by the user. After receiving such information from a person, we can hack into his account using the forgotten password option. nine0003
After receiving such information from a person, we can hack into his account using the forgotten password option. nine0003
The security question prevents you from easily logging into someone else's FB account, but setting a weak password makes it vulnerable. The most common passwords are mobile number, nickname, name and date of birth, pet's name, girl's or boyfriend's name.
If you want to protect your account, the answer to the security question must be known only to you, and the password must be strong enough. The good thing is that Facebook has a 24-hour account lockout period before granting access to someone who successfully answered the security question. So you can prevent a hack attempt by logging into your account during the day. nine0003
In addition, FB provides a "Login Notifications" option in the security settings. Enter your mobile or email and get notified when your account is logged in from a new or unknown device.
3. Simple password capture
This is another common method to steal passwords from Facebook users. Most people are not aware of this method, but traditional hackers use it to break into accounts.
Most people are not aware of this method, but traditional hackers use it to break into accounts.
How does it work?
In this case, the hacker aims to figure out your password on other low-quality websites where you are a member. The fact is that many of us use the same password for several sites, including Facebook. Sites that have poor security are poorly protected and it is easy for hackers to break into your account. In addition, many people use the same email address and password for such low-quality websites, making it easier for hackers to do so. nine0003
Most website developers store passwords in their database in plain text format without even thinking about encryption or security. Therefore, never trust low-quality sites, and come up with a unique password for Facebook.
4. Key Logger
This is a software or hardware device that logs various user actions - keystrokes on the computer keyboard, mouse movements and clicks, etc. Thus, any confidential information typed on the mobile keyboard, vulnerable to hacking. nine0003
Thus, any confidential information typed on the mobile keyboard, vulnerable to hacking. nine0003
How does it work?
Hardware keyloggers are miniature devices that can be attached between the keyboard and the computer or built into the keyboard itself. They log all keystrokes made on the keyboard. At the same time, the registration process is absolutely invisible to the end user. Hardware keyloggers do not require any program to be installed on the computer in order to successfully intercept all keystrokes.
When a hardware keylogger is attached, it doesn't matter at all whether the computer is on or off. Its operating time is not limited, since it does not require an additional power source for its operation. nine0003
Modern keyloggers can take screenshots, record the cursor position, monitor the clipboard, intercept incoming messages in all popular services, and much more. You don't have to be afraid of keyloggers when you use your personal computer, because only you have access to it. But you need to be careful when you use a public computer, not a mobile keyboard user.
But you need to be careful when you use a public computer, not a mobile keyboard user.
5. Malicious applications
Please note that all apps you use on Facebook are owned by third party publishers. Of course, there are some exceptions, such as Instagram. A malicious application that asks for your permission will spam your Facebook profile.
How does it work?
Whenever you log in to some applications through Facebook, you must be careful, because third-party applications do not belong to the social network. When you do this, a corresponding warning appears. As soon as you click OK, your personal data becomes vulnerable or certain actions can be performed on your FB account on your behalf - post photos, statuses or information, share a link, etc. Don't give access to apps if you don't trust them. You can also edit the information you provide to the application. nine0003
6. Browser vulnerability
These are security bugs that exist in older versions of mobile and desktop browsers. They allow attackers to steal files from your computer, gain access to your accounts.
They allow attackers to steal files from your computer, gain access to your accounts.
How does it work?
A shared origin policy browser vulnerability could allow a hacker to read the response of any page, such as Facebook, and he can perform any action on your account. One of these vulnerabilities is the Android SOP bypass, which was found by Rafay Baloch in the Chrome browser for Android versions lower than 4.4. nine0003
To be on the safe side, you should update your browser and operating system regularly. Using older versions is always risky.
7. Self XSS Scam
Self XSS is also known as Scripting Self Cross Site. This is a web security vulnerability that allows hackers to inject certain scripts into web pages used by other users. A victim of hackers accidentally executes a script and runs malicious code in their own web browser. nine0003
How does it work?
A hacker promises to help you hack someone else's Facebook account, but instead tries to inject malicious Javascript into your browser console.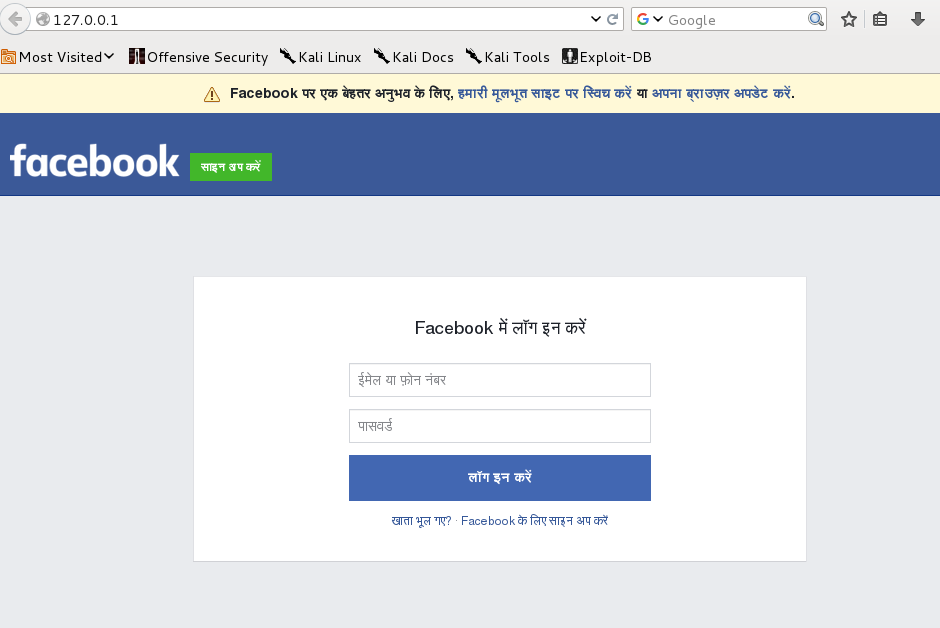 This gives him the ability to manipulate your account. Basically, this technique is used to add you to certain groups, post something on your wall, etc. Never copy and paste someone else's code into your browser or your account will be hacked.
This gives him the ability to manipulate your account. Basically, this technique is used to add you to certain groups, post something on your wall, etc. Never copy and paste someone else's code into your browser or your account will be hacked.
8. Trojan
This is a malicious program that enters the computer as legitimate software and misleads users. The Trojan records the keystrokes on your computer and sends them to the hacker.
How does it work?
The Trojan may contain software that you consider legal, a PDF file, or an AVI multimedia file. The program runs in the background collecting information. The Trojan can also record your Facebook password and send it to a hacker without your knowledge. To protect yourself, do not install programs, do not open files from unknown sources, do not install other people's flash drives, and update your antivirus regularly. nine0003
9. Malicious mobile application
The Facebook mobile application operates through an API that uses an access token stored in the internal memory of your mobile device for authentication. If someone is able to steal your access token, they can gain full access to your account.
If someone is able to steal your access token, they can gain full access to your account.
How does it work?
The Facebook interface does not require a username or password each time to retrieve user data. This only requires a secret access token, which the mobile app stores in your phone's memory. Mobile apps that have administrator rights can access data from other apps. nine0003
To protect yourself from malicious mobile apps, you should only install mobile apps from trusted developers. Also, don't give apps admin rights, log out of your Facebook account every time on your mobile device, and change your password more often.
10. Facebook Hacking Software
People who try to hack a Facebook account usually download software stored on different websites. In fact, such programs do not exist. All they do is crack your own Facebook password. nine0003
How does it work?
The software will collect the victim's passwords.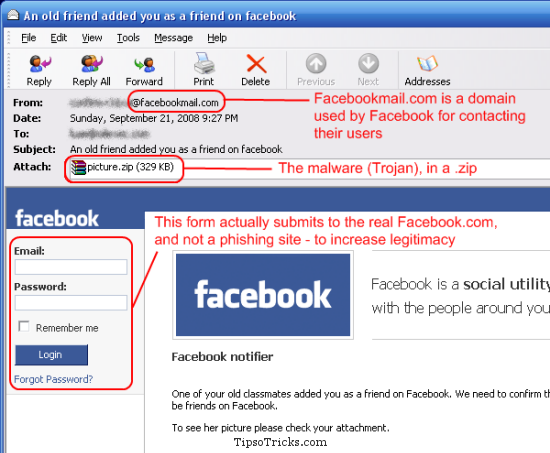 Some programs will require you to enter your Facebook username and password and store them in their password database. You may also be asked for administrator rights in order to install a keylogger and obtain confidential information. Never download or install such software, as the only victim will be yourself.
Some programs will require you to enter your Facebook username and password and store them in their password database. You may also be asked for administrator rights in order to install a keylogger and obtain confidential information. Never download or install such software, as the only victim will be yourself.
4 ways to hack facebook accounts (protect yourself now)
News
By Andrew Parish Reading 5 min Views 16 Published
Among all the popular and active social media platforms, Facebook is one of the first. When Facebook first appeared, it revolutionized how people communicate online. It was amazing what a simple account registration could do. Since September 2006, the social networking site has not lost its popularity.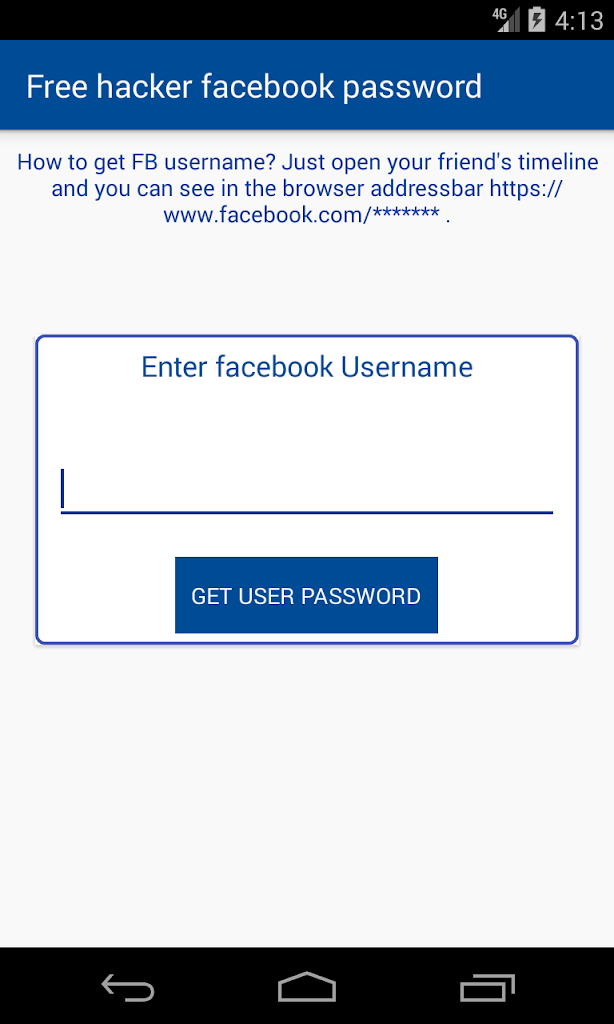 Despite the conflicts that Facebook has had to deal with in recent years, it is still the most popular site with 2.45 billion users worldwide. nine0003
Despite the conflicts that Facebook has had to deal with in recent years, it is still the most popular site with 2.45 billion users worldwide. nine0003
The Facebook controversy, however, should not be brushed aside. Consider that on Facebook you and your friends share everything. A lot of personal data and messages pass through the site's server in a matter of minutes. Imagine that all this data falls into the hands of third parties and what they can do with it. All this data not only puts your identity at risk, but also makes you more susceptible to being hacked.
Actually, hacking a Facebook account is quite difficult. But it can be as simple as running software on your computer. Let's discuss how someone can hack your Facebook account and how you can prevent it. nine0003
Content
- How to hack someone's Facebook account?
- Using a keylogger
- YouTube video: 4 ways to hack facebook accounts (protect yourself now)
- Phishing
- Reset password
- Man in the middle attack
How to hack someone's Facebook account?
Using a keylogger
A keylogger is a program that records your keystrokes as you make them.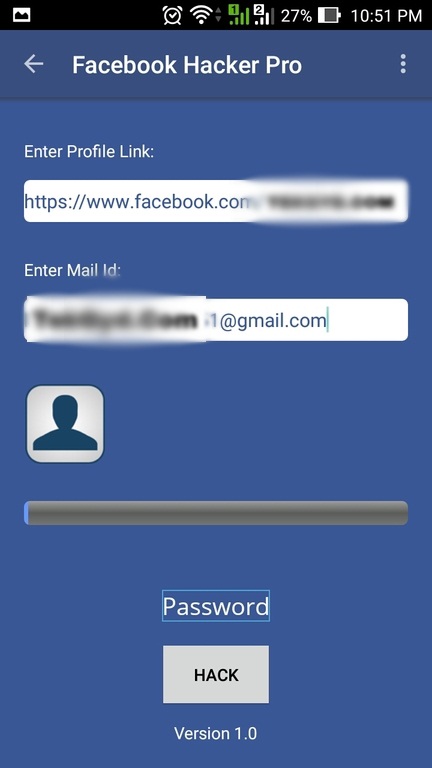 It is also done by someone who is close to the subject, and most often without their knowledge. This software is downloaded and installed manually on the user's device. Once installed, it starts recording keystrokes in the background from the moment you turn on your computer. The program can be configured to send logs to an email address. There are many software offerings in this category. nine0003
It is also done by someone who is close to the subject, and most often without their knowledge. This software is downloaded and installed manually on the user's device. Once installed, it starts recording keystrokes in the background from the moment you turn on your computer. The program can be configured to send logs to an email address. There are many software offerings in this category. nine0003
Hardware keyloggers work in a similar way, only they work after connecting a USB drive with software to the device. Instead of an email, the USB drive will save a summary of your clicks. There are also many options here, such as Keyllama or something more complex, such as Wi-Fi enabled keyloggers.
How to protect yourself
- Use a firewall. This is necessary because keyloggers use the Internet to transmit information, and the firewall will monitor and block access if it detects that something is wrong. nine0162
- Use a strong password manager. Password managers store your passwords in such a way that they automatically fill in the field when necessary.
 This ensures that you never type the password, which means that the keylogger will not be able to record it.
This ensures that you never type the password, which means that the keylogger will not be able to record it. - Change your passwords often. This is one surefire way to make it impossible for hackers to control your online accounts.
Read - How to remove the Shortcut virus from a USB stick
YouTube video: 4 ways to hack facebook accounts (protect yourself now)
Phishing
This method is different and harder to stop. Phishing is when you create a login page that is identical to the one you are about to hack. In this case, the login page looks exactly like Facebook. The data entered on this page will be sent directly to the hacker. The easiest thing about phishing is that you can send it to your victim's screen in several ways. The tricky part is that you need to create an account with a web host and create a fake login page exactly like the one on Facebook. nine0003
The tricky part is that you need to create an account with a web host and create a fake login page exactly like the one on Facebook. nine0003
How to protect yourself
- The simplest and most important way: don't click on links you don't trust. Check the URL carefully.
- Install an ad blocker. Phishing is not limited to email. Ads and pop-ups are other common ways hackers can use to attack you
- Use antivirus software vigilantly and follow web security protocols. nine0162
Reset your password
It is very easy for anyone to hack into your account by clicking on the "reset password" button. Most often this is done by people close to you.
- The first step in this case is to find out the email id used to log into Facebook. If you don't already know this, look for the "contact information" section of the Facebook page. If that doesn't help, use tools like TheHarvester that hackers use to find email addresses. nine0162
- Click on "Forgot Password" and then enter your email address.
 Click on 'This is my account'.
Click on 'This is my account'.
- Facebook will ask if you want to reset your password via email. If this is not possible, click ‘No longer have access to these?’
- Then the question ‘How can we reach you?’ will appear. Here you will have to enter an address that is not associated with any other Facebook account.
- He will ask a security question. It's easy or difficult, depending on how well you know the person. nine0162
- If none of this helped you, then the last option left is to ask friends for help. Facebook will ask you to choose 3-5 friends who will receive the passwords you enter on the next page.
How to protect yourself
- Use a separate email address for Facebook and don't list it on the site
- Make sure security questions are unique and can't be guessed even by good friends.
Man-in-the-middle attack
Man-in-the-middle attack is when you trick a victim into connecting to an insecure WIFI connection.