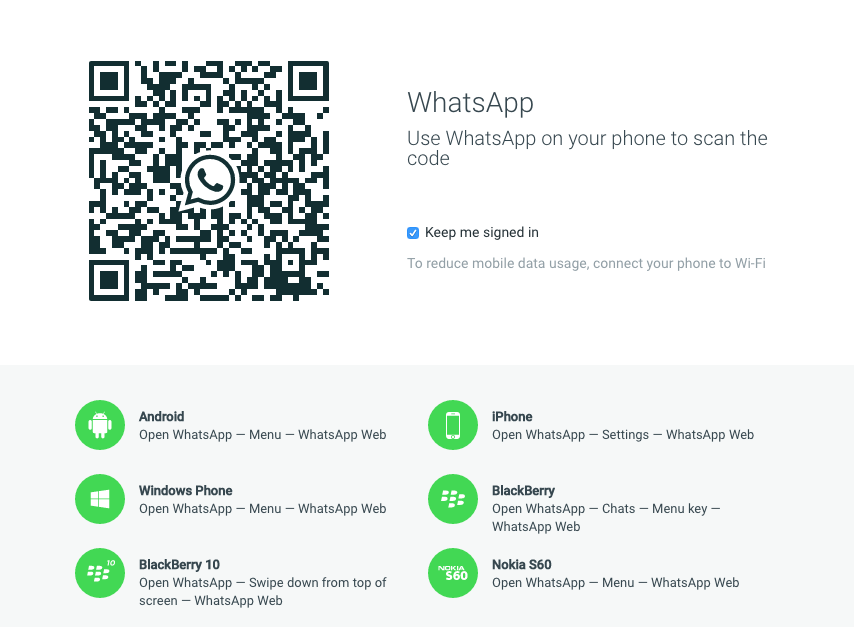
How to guess a password on instagram
How any Instagram account could be hacked in less than 10 minutes
Graham CLULEY
July 15, 2019
Ad One product to protect all your devices, without slowing them down.
Free 90-day trial
A security researcher has been awarded $30,000 after discovering a serious vulnerability that could potentially have put any Instagram account at risk of being hacked.
Following a recent increase in rewards offered for the discovery of critical account takeover vulnerabilities in Facebook and Instagram, Indian security researcher Laxman Muthiyah chose to take a close look at the photo-sharing service.
As he describes in a blog post, Muthiyah explored whether there might be a vulnerability in how Instagram handled password reset requests for users who have forgotten their login credentials.
Mutiyah found that when users asked for a password reset via Instagram’s web interface, the site would email a reset link to the user’s email account.
After a few minutes of testing Mutiyah couldn’t find any bugs, and so turned his attention instead to how smartphone users recover access to their Instagram accounts.
What Mutiyah found was that Instagram offered the option for users locked out of their accounts to request that a six-digit secret security code be sent to their mobile phone number or email account. If that passcode is entered, a user can regain access to their Instagram account.
In theory, if a hacker could enter the six-digit security code they would be able to break into the Instagram account (and reset the password locking out the legitimate owner.)
Now, that passcode could potentially be stolen if a hacker had somehow managed to gain access to their target’s email account, or had hijacked control of their victim’s mobile phone number via a SIM swap scam. But Mutiyah wondered if there might be another way to break into accounts if neither of those options were available.
Mutiyah realised that all a hacker would need to do was enter the correct six digit code – a code that could be any combination between 000000 and 999999 – within the ten minute window Instagram would accept the code before expiring it.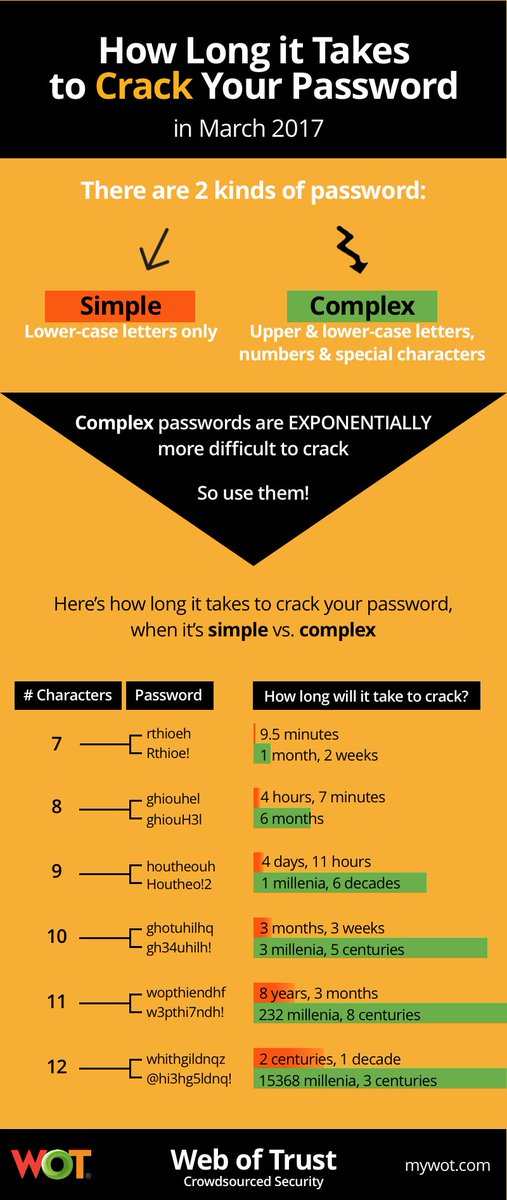
Up to one million numbers to be entered within ten minutes, in order to change an Instagram account’s password.
Of course, the likes of Facebook and Instagram aren’t going to simply sit quietly as an automated script tries a brute force attack to guess the correct security code. Instead they have rate-limiting in place to detect when multiple attempts have been made to get past the security check and slow down subsequent attempts – meaning the ten minute window of opportunity expires.
In Mutiyah’s tests he discovered that when he cycled through 1000 attempts to guess an Instagram account’s security codes, 250 of them went through and the subsequent 750 requests were rate limited.
However, after a few days of testing the researcher was able to discover that Instagram’s rate limiting mechanism could be bypassed by rotating IP addresses (in other words, not using the same computer to brute force the recovery code) and sending concurrently from different IP addresses:
“Sending concurrent requests using multiple IPs allowed me to send a large number of requests without getting limited.The number of requests we can send is dependent on concurrency of reqs and the number of IPs we use. Also, I realized that the code expires in 10 minutes, it makes the attack even harder, therefore we need 1000s of IPs to perform the attack.”
Mutiyah says that he used 1000 different machines and IPs to achieve easy concurrency, and sent 200,000 requests in his tests. He shared a YouTube video with Facebook and Instagram’s security team to demonstrate the attack in action:
Of course, 200,000 requests isn’t quite the million requests that would be necessary to guarantee the correct recovery passcode would be entered to allow an Instagram account to be hijacked.
Mutiyah’s investigation concludes that in a real attack, 5000 IP addresses would be needed to hack an Instagram account. Although that sounds like a large number, it can actually be easily achieved at a low price (Mutiyah says there would be approximately US $150 cost if a cloud provider like Google or Amazon was used).
Although that sounds like a large number, it can actually be easily achieved at a low price (Mutiyah says there would be approximately US $150 cost if a cloud provider like Google or Amazon was used).
All Instagram users should be grateful that Laxman Muthiyah chose to responsibly disclose the security vulnerability to Instagram’s security team rather than monetize his discovery by selling it to online criminals.
It’s easy to imagine that a technique like this would be very attractive to many hackers interested in compromising Instagram accounts, and they might be prepared to pay much more than the $30,000 Muthiyah received in the form of a bug bounty.
All internet users are reminded to better secure their online accounts with strong, unique passwords and to enable two-factor authentication wherever possible.
The top 12 password-cracking techniques used by hackers
Skip to ContentSkip to Footer
IT Pro is supported by its audience. When you purchase through links on our site, we may earn an affiliate commission. Learn more
Learn more
In-depth
- Security
Some of the most common, and most effective methods for stealing passwords
by: Dale Walker
14 Nov 2022
14 Nov 2022
For many years, passwords were considered to be an acceptable form of protecting privacy when it came to the digital world. However, as cryptography and biometrics started to become more widely available, the flaws in this simple method of authentication became more noticeable.
It’s worth taking into account the role of a leaked password in one of the biggest cyber security stories of the last two years, the SolarWinds hack. It was revealed that ‘solarwinds123’, a password created and leaked by an intern, had been publicly accessible through a private GitHub repository since June 2018, enabling hackers to plan and carry out the massive supply chain attack.
Despite this, even if the password hadn’t been leaked, it wouldn’t have been hard for attackers to guess it. In the words of US politician Katie Porter, most parents utilise a stronger password to stop their children from “watching too much YouTube on their iPad”.
In the words of US politician Katie Porter, most parents utilise a stronger password to stop their children from “watching too much YouTube on their iPad”.
Passwords that are weak or easy to guess are more common than you might expect: recent findings from the NCSC found that around one in six people uses the names of their pets as their passwords, making them highly predictable. To make matters worse, these passwords tend to be reused across multiple sites, with one in three people (32%) having the same password to access different accounts.
It should come as no surprise that passwords are the worst nightmare of a cyber security expert. To remedy this issue, there are steps worth taking, like implementing robust multi-layer authentication. It is also worthwhile mitigating risks to consider the steps cyber criminals must take to hack your account and “know your enemy”. We’ve put together the top 12 password-cracking techniques used by attackers to enable you and your business to be better prepared.
12 password-cracking techniques used by hackers:
1. Phishing
Shutterstock
Phishing is among the most common password-stealing techniques currently in use today and is often used for other types of cyber attacks. Rooted in social engineering tactics, its success is predicated on being able to deceive a victim with seemingly legitimate information while acting on malicious intent.
Businesses are highly aware of the widespread phishing attempts on their employees and often conduct phishing training exercises on them, both with explicit notice and on unwitting individuals. Usually carried out through email, success with phishing can also be achieved with other communication forms such as over SMS text messaging, known as ‘smishing’.
Phishing typically involves sending an email to a recipient while including as many elements within the email as possible to make it appear legitimate i.e. company signatures, correct spelling and grammar, and more sophisticated attacks recently attach onto existing email threads with phishing coming later in the attack chain.
From there, attackers will try and encourage the user into downloading and opening a malicious document or another type of file - usually malware - to achieve whatever the attacker wants. This could be stealing passwords, infecting them with ransomware, or even staying stealthily hidden in the victim’s environment to act as a backdoor for future attacks performed remotely.
Related Resource
The long road ahead to ransomware preparedness
Getting to the bigger truth
Free Download
Computer literacy has increased over the years and many users are well trained in how to spot a phishing email. The telltale clues are now widely known, and people know when and how to report a suspicious email at work. Only the very best campaigns are genuinely convincing, like with the aforementioned email hijack campaigns.
The days of emails from supposed princes in Nigeria looking for an heir, or firms acting on behalf of wealthy deceased relatives, are few and far between these days, although you can still find the odd, wildly extravagant, claim here and there.
Our recent favourite is the case of the first Nigerian astronaut who is unfortunately lost in space and needs us to act as a man in the middle for a $3 million dollar transfer to the Russian Space Agency – which apparently does return flights.
2. Social engineering
Speaking of social engineering, this typically refers to the process of tricking users into believing the hacker is a legitimate agent. A common tactic is for hackers to call a victim and pose as technical support, asking for things like network access passwords in order to provide assistance. This can be just as effective if done in person, using a fake uniform and credentials, although that’s far less common these days.
Successful social engineering attacks can be incredibly convincing and highly lucrative, as was the case when the CEO of a UK-based energy company lost £201,000 to hackers after they tricked him with an AI tool that mimicked his assistant’s voice.
3. Malware
Keyloggers, screen scrapers, and a host of other malicious tools all fall under the umbrella of malware, malicious software designed to steal personal data. Alongside highly disruptive malicious software like ransomware, which attempts to block access to an entire system, there are also highly specialised malware families that target passwords specifically.
Alongside highly disruptive malicious software like ransomware, which attempts to block access to an entire system, there are also highly specialised malware families that target passwords specifically.
Keyloggers, and their ilk, record a user’s activity, whether that’s through keystrokes or screenshots, which is all then shared with a hacker. Some malware will even proactively hunt through a user’s system for password dictionaries or data associated with web browsers.
4. Brute force attack
Brute force attacks involve hackers using a variety of methods, usually on a trial-and-error basis, to guess their way into a user’s account. This could see attackers simply trying to use commonly used passwords like ‘password123’ against a known username, for example.
A brute force attack can also take the form of an attacker making educated guesses. For example, the username may already be known and the attacker may even know the victim personally, so guesses related to known birth dates, favourite sports teams, and family members’ names could all provide clues to the correct password, such as LiverpoolFC97.
They are somewhat similar to dictionary attacks but often lack the associated sophistication, automation, and computational complexity.
5. Dictionary attack
Shutterstock
Dictionary attacks are similar to brute force methods but involve hackers running automated scripts that take lists of known usernames and passwords and run them against a login system sequentially to gain access to a service. It means every username would have to be checked against every possible password before the next username could be attempted against every possible password.
The method is computationally demanding and as a result, often quite time-consuming. With the strongest password encryption standards, the time to conduct a dictionary attack increases often to an untenable level.
There are fears that the advent of quantum computing may render passwords useless given the computational power they possess, and even consumer-grade equipment is threatening the password too. Nvidia’s RTX 4090 GPU, for example, has been shown to take under an hour to crack every single eight-character password when running eight of them in tandem. This is around 200 billion different possibilities, including different letter capitalisations, symbols, and numbers placed in different orders in the password.
Nvidia’s RTX 4090 GPU, for example, has been shown to take under an hour to crack every single eight-character password when running eight of them in tandem. This is around 200 billion different possibilities, including different letter capitalisations, symbols, and numbers placed in different orders in the password.
6. Mask attack
Where dictionary attacks use lists of all possible phrase and word combinations, mask attacks are far more specific in their scope, often refining guesses based on characters or numbers – usually founded in existing knowledge.
For example, if a hacker is aware that a password begins with a number, they will be able to tailor the mask to only try those types of passwords. Password length, the arrangement of characters, whether special characters are included, or how many times a single character is repeated are just some of the criteria that can be used to configure the mask.
The goal here is to drastically reduce the time it takes to crack a password, and remove any unnecessary processing.
7. Rainbow table attack
Whenever a password is stored on a system, it’s typically encrypted using a ‘hash’, or a cryptographic alias, making it impossible to determine the original password without the corresponding hash. In order to bypass this, hackers maintain and share directories that record passwords and their corresponding hashes, often built from previous hacks, reducing the time it takes to break into a system (used in brute force attacks).
Rainbow tables go one step further, as rather than simply providing a password and its hash, these store a precompiled list of all possible plain text versions of encrypted passwords based on a hash algorithm. Hackers are then able to compare these listings with any encrypted passwords they discover in a company’s system.
Much of the computation is done before the attack takes place, making it far easier and quicker to launch an attack, compared to other methods. The downside for cyber criminals is that the sheer volume of possible combinations means rainbow tables can be enormous, often hundreds of gigabytes in size.
8. Network analysers
Network analysers are tools that allow hackers to monitor and intercept data packets sent over a network and lift the plain text passwords contained within.
Such an attack requires the use of malware or physical access to a network switch, but it can prove highly effective. It doesn’t rely on exploiting a system vulnerability or network bug, and as such is applicable to most internal networks. It’s also common to use network analysers as part of the first phase of an attack, followed up with brute force attacks.
Of course, businesses can use these same tools to scan their own networks, which can be especially useful for running diagnostics or for troubleshooting. Using a network analyser, admins can spot what information is being transmitted in plain text, and put policies in place to prevent this from happening.
The only way to prevent this attack is to secure the traffic by routing it through a VPN or something similar.
9. Spidering
Related Resource
The long road ahead to ransomware preparedness
Getting to the bigger truth
Free Download
Spidering refers to the process of hackers getting to know their targets intimately in order to acquire credentials based on their activity.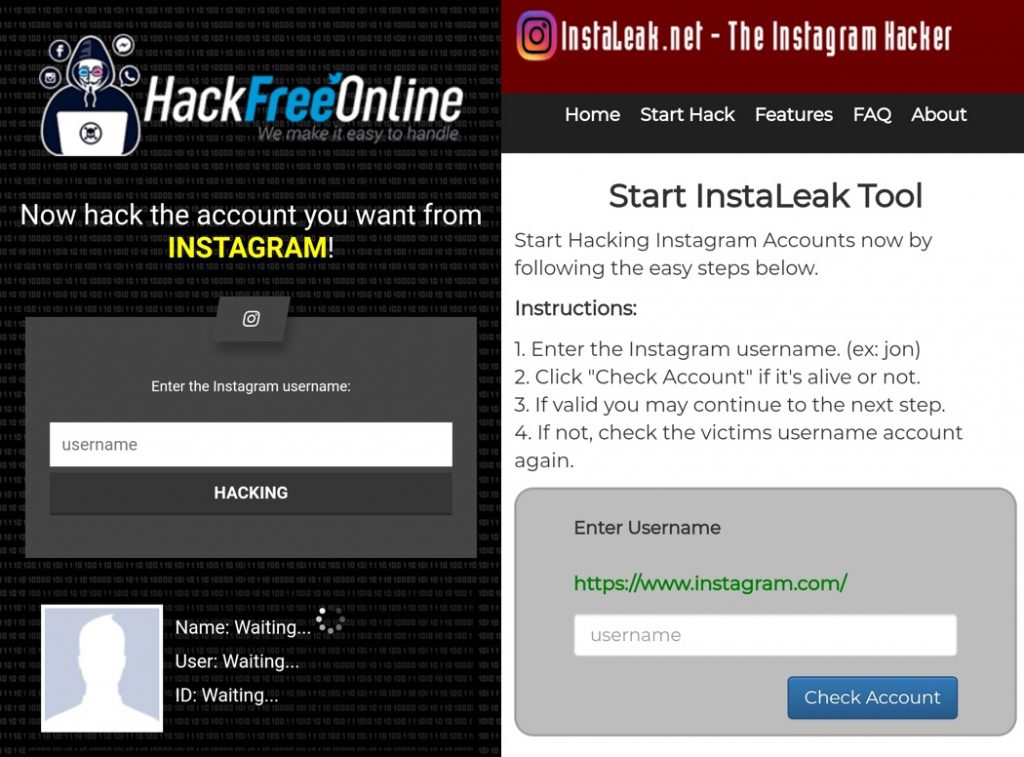 The process is very similar to techniques used in phishing and social engineering attacks, but involves a far greater amount of legwork on the part of the hacker - although it’s generally more successful as a result.
The process is very similar to techniques used in phishing and social engineering attacks, but involves a far greater amount of legwork on the part of the hacker - although it’s generally more successful as a result.
How a hacker might use spidering will depend on the target. For example, if the target is a large company, hackers may attempt to source internal documentation, such as handbooks for new starters, in order to get a sense of the sort of platforms and security the target uses. It’s in these that you often find guides on how to access certain services, or notes on office Wi-Fi usage.
It’s often the case that companies will use passwords that relate to their business activity or branding in some way - mainly because it makes it easier for employees to remember. Hackers are able to exploit this by studying the products that a business creates in order to build a hitlist of possible word combinations, which can be used to support a brute force attack.
As is the case with many other techniques on this list, the process of spidering is normally supported by automation.
10. Offline cracking
It’s important to remember that not all hacking takes place over an internet connection. In fact, most of the work takes place offline, particularly as most systems place limits on the number of guesses allowed before an account is locked.
Offline hacking usually involves the process of decrypting passwords by using a list of hashes likely taken from a recent data breach. Without the threat of detection or password form restrictions, hackers are able to take their time.
Of course, this can only be done once an initial attack has been successfully launched, whether that's a hacker gaining elevated privileges and accessing a database, by using a SQL injection attack, or by stumbling upon an unprotected server.
11. Shoulder surfing
Far from the most technically complex method in this list, shoulder surfing is one of the most rudimentary but effective techniques available to hackers, given the right context and target.
Somewhat self-explanatory, shoulder surfing simply sees hackers peering over the shoulder of a potential target, looking to visually track keystrokes when entering passwords. This could take place in any public space like a coffee shop, or even on public transport such as a flight. An employee may be accessing in-flight internet to complete a task before landing and the hacker could be sitting nearby, watching for an opportunity to note down a password to an email account, for example.
This could take place in any public space like a coffee shop, or even on public transport such as a flight. An employee may be accessing in-flight internet to complete a task before landing and the hacker could be sitting nearby, watching for an opportunity to note down a password to an email account, for example.
If you work from public places on a regular or even semi-regular basis, it is worth considering using a device fitted with technology to prevent prying eyes from seeing what’s on the display. HP’s EliteBooks often come with the option to configure a device with a Sure View privacy screen, for example. Other third-party options are also available from online retailers that can simply be placed over most laptop displays, and they’re affordable too.
12. Guess
If all else fails, a hacker can always try and guess your password. While there are many password managers available that create strings that are impossible to guess, many users still rely on memorable phrases. These are often based on hobbies, pets, or family, much of which is often contained in the very profile pages that the password is trying to protect.
These are often based on hobbies, pets, or family, much of which is often contained in the very profile pages that the password is trying to protect.
The best way to remove this as a potential avenue for criminals is to maintain password hygiene and make use of password managers, many of which are free.
- phishing
- ransomware
- social engineering
- malware
- Security
- Security
Featured Resources
Getting board-level buy-in for security strategy
Why cyber security needs to be a board-level issue
Free Download
Technology Ecosystem benchmark report
The evolution of the IT industry
Free Download
Can't choose between public and private cloud? You don't have to with IaaS
Enjoy a cloud-like experience with on-premises infrastructure
Free Download
How organisations drive employee empowerment and business results with leading digital technology
What you can achieve with a leading approach to digital work
Free Download
Recommended
Uber says compromised third-party to blame for data breach
data breaches
Uber says compromised third-party to blame for data breach
13 Dec 2022
13 Dec 2022
Can't choose between public and private cloud? You don't have to with IaaS
Whitepaper
Can't choose between public and private cloud? You don't have to with IaaS
9 Dec 2022
9 Dec 2022
Enhancing cyber security in an expanding landscape
Whitepaper
Enhancing cyber security in an expanding landscape
8 Dec 2022
8 Dec 2022
Getting board-level buy-in for security strategy
Whitepaper
Getting board-level buy-in for security strategy
30 Nov 2022
30 Nov 2022
Most Popular
LastPass customer password vaults stolen, targeted phishing attacks likely
Security
LastPass customer password vaults stolen, targeted phishing attacks likely
23 Dec 2022
23 Dec 2022
Linux fixes maximum-severity kernel vulnerability
vulnerability
Linux fixes maximum-severity kernel vulnerability
23 Dec 2022
23 Dec 2022
The case for consolidating your comms and IT support
Sponsored
The case for consolidating your comms and IT support
14 Dec 2022
14 Dec 2022
Skip to HeaderSkip to Content
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil. " The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
" The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act. nine0003
What could have happened
First, let's figure out how a stranger could gain access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on. nine0003
nine0003
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password may have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password. nine0003
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It's possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account. nine0003
Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account. nine0003
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there. nine0003
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing. nine0003
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices. On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings.
 This will reset the access tokens.
This will reset the access tokens. - Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them. If they managed to do this, change it back to yours. nine0052
- Set a new password that is strong and one that you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware. Attention to security settings along with good protection will make your account your fortress. nine0052
Tips
Christmas and security
Many famous break-ins began during the Christmas holidays. A few simple tips will reduce your risk of becoming the next victim.
A few simple tips will reduce your risk of becoming the next victim.
Is it safe to use Avast in 2023?
Avast solutions have a good reputation, but several incidents cast doubt on their reliability. We tell you whether you can trust Avast products.
Football cyberthreats
How to watch the World Cup and not become a victim of fraud.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site. I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons. nine0052
A hacker hacked Instagram in 10 minutes and got $30,000.
Cybersecurity expert Laxman Mutiya found a way to hack any Instagram account in ten minutes - he announced this on his blog. According to Mutiiya, the vulnerability was in a password recovery system where a one-time numeric code is sent to a user to verify their identity.
According to Mutiiya, the vulnerability was in a password recovery system where a one-time numeric code is sent to a user to verify their identity.
Information security researcher Laxman Mutiya told on his blog how he managed to hack Instagram in 10 minutes. While Facebook, which owns the photo hosting, is constantly trying to improve security and prevent outside interference, Mutiya's example proves that this problem can be worked on indefinitely.
An expert discovered a vulnerability in the password recovery system for his Instagram account. The fact is that when a user enters his phone number to resume access to the profile, Instagram sends him a six-digit numeric code that must be entered to verify his identity. nine0003
Laxman Mutiya decided that if he could try a million different codes at this stage, then one would definitely work, which would lead to a password change on any Instagram account.
Nevertheless, the expert rightly decided that the photo service would most likely have protection against such a blunt attack.
Indeed, Instagram has limited the number of shift requests a user can send. Then, by calculation, Mutiya determined that for a successful hack, he would need 5 thousand IP addresses, each of which would send 200 thousand requests. According to the hacker, this is not so difficult to implement if you use the Google or Amazon cloud service. In this case, the entire attack will cost the attacker $150. nine0003
Laxman Mutiya sent his research to the Facebook administration, which was convinced of the insecurity of the existing system. As follows from a letter sent by the leadership of the social network, the vulnerability in Instagram was eliminated, and Mutiya himself received $30,000 as a "bug bounty" - compensation for identified shortcomings.
The expert also gave some advice to those who use Instagram to protect themselves and their data.
He recommends changing your password regularly, using only unique and varied combinations, and be sure to use two-factor identification so that any manipulations with the account are made only with the user's approval. nine0003
nine0003
In May of this year, it became known about the massive leak of personal information of bloggers and celebrities from Instagram - in total, about 50 million people suffered from it. A database containing the data of millions of Instagram stars using popular photo hosting has been discovered on the Internet, TechCrunch reported. This database, located in the public cloud of Amazon Web Services, was in the public domain and was available to everyone.
As it turned out, each of the entries contained personal data of Instagram bloggers and influencers, including their biography, profile photo, number of followers, geolocation, as well as email and mobile phone number. nine0003
Shortly after the leak was reported in the foreign press, the database went offline and Facebook announced its own investigation.
“We will conduct an investigation to understand where the data, including email addresses and phone numbers, got into the network - from Instagram or other sources.