How to hack whatsapp calls and sms
How Hackers Broke WhatsApp With Just a Phone Call
You've heard the advice a million times. Don't click links in suspicious emails or texts. Don't download shady apps. But a new Financial Times report alleges that the notorious Israeli spy firm NSO Group developed a WhatsApp exploit that could inject malware onto targeted phones—and steal data from them—simply by calling them. The targets didn't need to pick up to be infected, and the calls often left no trace on the phone's log. But how would a hack like that even work in the first place?
WhatsApp, which offers encrypted messaging by default to its 1.5 billion users worldwide, discovered the vulnerability in early May and released a patch for it on Monday. The Facebook-owned company told the FT that it contacted a number of human rights groups about the issue and that exploitation of this vulnerability bears "all the hallmarks of a private company known to work with governments to deliver spyware." In a statement, NSO Group denied any involvement in selecting or targeting victims but not its role in the creation of the hack itself.
So-called zero-day bugs, in which attackers find a vulnerability before the company can patch it, happen on every platform. It's part and parcel of software development; the trick is to close those security gaps as quickly as possible. Still, a hack that requires nothing but an incoming phone call seems uniquely challenging—if not impossible—to defend against.
WhatsApp wouldn't elaborate to WIRED about how it discovered the bug or give specifics on how it works, but the company says it is doing infrastructure upgrades in addition to pushing a patch to ensure that customers can't be targeted with other phone-call bugs.
"Remote-exploitable bugs can exist in any application that receives data from untrusted sources," says Karsten Nohl, chief scientist at the German firm Security Research Labs. That includes WhatsApp calls, which use the voice-over-internet protocol to connect users. VoIP applications have to acknowledge incoming calls and notify you about them, even if you don't pick up. "The more complex the data parsing, the more room for error," Nohl says. "In the case of WhatsApp, the protocol for establishing a connection is rather complex, so there is definitely room for exploitable bugs that can be triggered without the other end picking up the call."
"The more complex the data parsing, the more room for error," Nohl says. "In the case of WhatsApp, the protocol for establishing a connection is rather complex, so there is definitely room for exploitable bugs that can be triggered without the other end picking up the call."
VoIP calling services have been around for so long that you'd think any kinks in the basic call connection protocols would be worked out by now. But in practice, every service's implementation is a little bit different. Nohl points out that things get even trickier when you are offering end-to-end encrypted calling, as WhatsApp famously does. While WhatsApp bases its end-to-end encryption on the Signal Protocol, its VoIP calling functionally likely also includes other proprietary code as well. Signal says that its service is not vulnerable to this calling attack.
According to Facebook's security advisory, the WhatsApp vulnerability stemmed from an extremely common type of bug known as a buffer overflow. Apps have a sort of holding pen, called a buffer, to stash extra data. A popular class of attacks strategically overburdens that buffer so the data "overflows" into other parts of the memory. This can cause crashes or, in some cases, give attackers a foothold to gain more and more control. That's what happened with WhatsApp. The hack exploits the fact that in a VoIP call the system has to be primed for a range of possible inputs from the user: pick up, decline the call, and so on.
Apps have a sort of holding pen, called a buffer, to stash extra data. A popular class of attacks strategically overburdens that buffer so the data "overflows" into other parts of the memory. This can cause crashes or, in some cases, give attackers a foothold to gain more and more control. That's what happened with WhatsApp. The hack exploits the fact that in a VoIP call the system has to be primed for a range of possible inputs from the user: pick up, decline the call, and so on.
Hackers steal WhatsApp accounts using call forwarding trick
There’s a trick that allows attackers to hijack a victim’s WhatsApp account and gain access to personal messages and contact list.
The method relies on the mobile carriers’ automated service to forward calls to a different phone number, and WhatsApp’s option to send a one-time password (OTP) verification code via voice call.
The MMI code trick
Rahul Sasi, the founder and CEO of digital risk protection company CloudSEK, posted some details about the method saying that it is used to hack WhatsApp account.
BleepingComputer tested and found that the method works, albeit with some caveats that a sufficiently skilled attacker could overcome.
It takes just a few minutes for the attacker to take over the WhatsApp account of a victim, but they need to know the target’s phone number and be prepared do some social engineering.
Sasi says that an attacker first needs to convince the victim to make a call to a number that starts with a Man Machine Interface (MMI) code that the mobile carrier set up to enable call forwarding.
Depending on the carrier, a different MMI code can forward all calls to a terminal to a different number or just when the line is busy or there is no reception.
These codes start with a star (*) or a hash (#) symbol. They are easily found and from the research we did, all major mobile network operators support them.
“First, you receive a call from the attacker who will convince you to make a call to the following number **67* or *405*. Within a few minutes, your WhatsApp would be logged out, and the attackers would get complete control of your account” - Rahul Sasi
The researcher explains that the 10 digit number belongs to the attacker and the MMI code in front of it tells the mobile carrier to forward all calls to the phone number specified after it when the victim’s line is busy.
Once they tricked the victim into forwarding calls to their number, the attacker starts the the WhatsApp registration process on their device, choosing the option to receive the OTP via voice call.
WhatsApp options for receiving one-time password, source: BleepingComputerAfter they get the OTP code, the attacker can register the victim’s WhatsApp account on their device and enable two-factor authentication (2FA), which prevents legitimate owners from regaining access.
Some caveats
Although the method seems simple, getting it to work requires a little more effort, as BleepingComputer found during testing.
First off, the attacker needs to make sure that they use an MMI code that forwards all calls, regardless of the victim device’s state (unconditionally). For example, if the MMI only forwards calls when a line is busy, call waiting may cause the hijack to fail.
During testing, BleepingComputer noticed that the target device also received text messages informing that WhatsApp is being registered on another device..png)
Users may miss this warning if the attacker also turns to social engineering and engages the target in a phone call just long enough to receive the WhatsApp OTP code over voice.
BleepingComputer · OTP message from WhatsApp
If call forwarding has already been activated on the victim device, the attacker must use a different phone number than the one used for the redirection - a small inconvenience that might require more social engineering.
The most clear clue of suspicious activity for the target user occurs after the mobile operators turn on call forwarding for their device, since activation comes with a warning overlayed on the screen that doesn't go away until the user confirms it.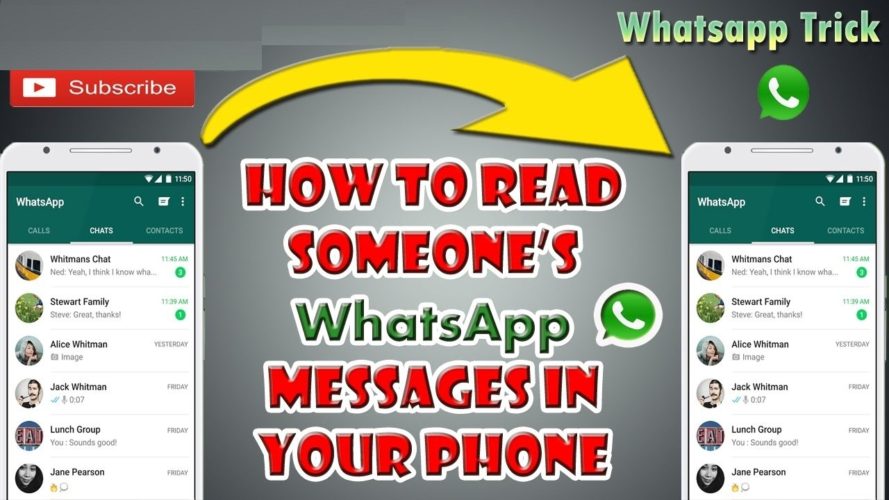
Even with this highly visible warning, threat actors still have a good chance of success because most users are not familiar with the MMI codes or the mobile phone settings that disable call forwarding.
Despite these obstacles, malicious actors with good social engineering skills can devise a scenario that allows them to keep the victim busy on the phone until they get the OTP code for registering the victim WhatsApp account on their device.
BleepingComputer has tested this method using mobile services from Verizon and Vodafone and concluded that an attacker with a plausible scenario is likely to hijack WhatsApp accounts.
Sasi's post refers to Airtel and Jio mobile carriers, each with more than 400 million customers as of December 2020, according to public data.
Protecting against this type attack is as easy as turning on two-factor authentication protection in WhatsApp. This feature prevents malicious actors from getting control of the account by requiring a PIN whenever you register a phone with the messaging app.
This feature prevents malicious actors from getting control of the account by requiring a PIN whenever you register a phone with the messaging app.
A single call is enough to lose your WhatsApp account. A new version of hacking was invented by calling
iXBT.com projects require cookies and analytics services. By continuing to visit project sites, you agree to our Cookie Policy
Information is being disseminated on the web about the emergence of a new type of fraud with accounts of the well-known WhatsApp messenger. In short, your account can be hacked with just one call. CloudSEK specialists dealt with cyber fraudsters.
According to Rahul Sasi, CEO of CloudSEK, this method of accessing an account is quite simple and does not require large investments or resources. Hackers send SMS to certain groups of phones linked to accounts, or write directly to the messenger, or simply notify users to call the WhatsApp "service" phone in order to receive any services or privileges. The proposed phone number contains a combination of numbers "405" or "67" registered in the service departments of service providers around the world. Users do not even realize that this is a fake phone number and calmly call back. After dialing the number, the linked account automatically logs out of WhatsApp, and the hacker receives the necessary login information.
The proposed phone number contains a combination of numbers "405" or "67" registered in the service departments of service providers around the world. Users do not even realize that this is a fake phone number and calmly call back. After dialing the number, the linked account automatically logs out of WhatsApp, and the hacker receives the necessary login information.
Once the victim dials the phone number, the hacker has full access to the user's account. This method of deception appeared in April 2021 and thousands of users became victims at that time.
To protect against this type of interference, you will need to activate two-factor authentication and, if possible, do not answer or call back unknown numbers, especially not from your region.
Source : news.abplive.com
News
Publications
Good afternoon, dear friends! For April 1, I did not come up with a better theme, like the Joker, and in general, how not to celebrate this holiday? In fact, this is our day, Geek's Day, because in German, in the 14th century, . ..
..
Mirror DVR allows you to use video recording capabilities, minimally blocking the view on the windshield. The gadget is installed on a regular mirror, performing its functions and almost no...
Capsule hotels appeared in Japan in the 70s and gained great popularity there. They are a series of numbers from a small isolated volume. Cells for sleep and rest, which fit...
Well-known and popular manufacturer of automotive Neoline gadgets released an interesting novelty - the X-COP 9350d combo device, which combines a radar detector, video recorder and...
Vasyugan swamps is a vast natural complex located on the territory of the Tomsk region and the Khanty-Mansi Autonomous Okrug in Russia. The swamp area is more than 53 thousand square...
In the process of life, each of us accumulates a huge number of different things. So By the time the balconies begin to fill up with bicycles, car tires and other things. And so limited...
5 signs that someone is reading your Whatsapp conversation and remains invisible
How to read other people's Whatsapp messages from your phone
After a series of updates, Whatsapp received an important feature - the ability to work on multiple devices at the same time.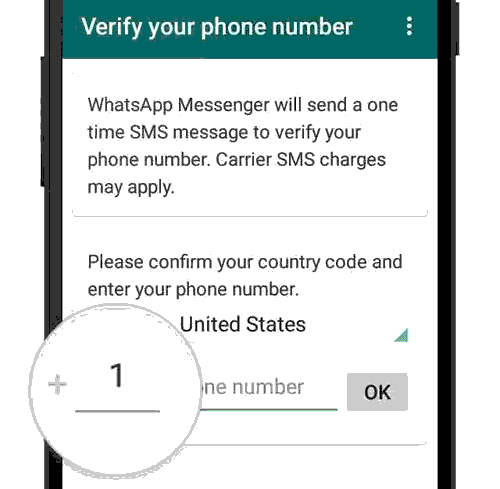 A new opportunity was created for convenience, but it was immediately used for criminal purposes. In Europe and the United States, there are cases when attackers, under the guise of a request for a call, take the victim’s device, scan a special QR code and gain access to the correspondence. The psychological technique works mainly with women and teenagers, but the end of the story is the same for everyone - extortion, theft of intimate photos and the threat to reveal the most intimate secrets to relatives or colleagues. The easiest way to close such a vulnerability is not to give outsiders (and relatives too) your device for a long time or set a password to launch the application.
A new opportunity was created for convenience, but it was immediately used for criminal purposes. In Europe and the United States, there are cases when attackers, under the guise of a request for a call, take the victim’s device, scan a special QR code and gain access to the correspondence. The psychological technique works mainly with women and teenagers, but the end of the story is the same for everyone - extortion, theft of intimate photos and the threat to reveal the most intimate secrets to relatives or colleagues. The easiest way to close such a vulnerability is not to give outsiders (and relatives too) your device for a long time or set a password to launch the application.
How to hack Whatsapp and how to protect it from surveillance
Photo © Shutterstock
Determining that someone else has access to your account is quite simple. You need to go to "Settings" and go to "Associated devices". This menu will show all the devices that use your account. They can be removed, leaving one, two or three reliable means of communication. One of the most vulnerable points of Whatsapp is the so-called "floating" widget - a utility (add-on) for an Android application. The attackers copy the original widgets - a special "floating" algorithm is left inside the program, which does not show activity at the stage of checking the program by store administrators. The delayed activation mechanism starts working a couple of days after installation on the device. The main sign that something is not right with the phone is increased heating and an increase in traffic for Whatsapp.
One of the most vulnerable points of Whatsapp is the so-called "floating" widget - a utility (add-on) for an Android application. The attackers copy the original widgets - a special "floating" algorithm is left inside the program, which does not show activity at the stage of checking the program by store administrators. The delayed activation mechanism starts working a couple of days after installation on the device. The main sign that something is not right with the phone is increased heating and an increase in traffic for Whatsapp.
Erase it immediately: 6 reasons to urgently remove WhatsApp from your phone
How to read deleted Whatsapp messages?
Reading deleted messages is another nuisance that can overtake a user after an outsider intercepts access to his device. The problem is that here the owners of Whatsapp got caught in their own lies. They used to state that a Whatsapp message is automatically deleted from the server as soon as the user deletes it from the device. But over time, it turned out that this is not so: messages are stored for some time both on the devices themselves and on the "third party" in case someone complains about it and the signal has to be responded to. The backdoor was opened by hackers who wrote an application for Android. Once installed on a smartphone, it made it possible to synchronize the messenger with a hacker program and penetrate the notification history, where all messages, including deleted ones, are visible. It is not known whether this vulnerability has been fixed at the moment, but one of the indirect signs that your deleted messages are being restored is their "revival" in the correspondence. At least, such symptoms are reported by foreign users.
But over time, it turned out that this is not so: messages are stored for some time both on the devices themselves and on the "third party" in case someone complains about it and the signal has to be responded to. The backdoor was opened by hackers who wrote an application for Android. Once installed on a smartphone, it made it possible to synchronize the messenger with a hacker program and penetrate the notification history, where all messages, including deleted ones, are visible. It is not known whether this vulnerability has been fixed at the moment, but one of the indirect signs that your deleted messages are being restored is their "revival" in the correspondence. At least, such symptoms are reported by foreign users.
Extensions
Photo © Shutterstock
Messenger extensions are popular exclusively with Android users. In the Apple ecosystem, such programs do not take root, and their verification by moderators before publication often leads to the removal and ban of "developers". Widgets for multitasking, cleaning Whatsapp memory and other third-party applications that require the right to synchronize with contacts and messenger conversations slow down Whatsapp in almost 100% of cases, and in the worst case, steal user data by taking screenshots and uploading data to unknown servers. Avoiding such a "leak" is easy - you should not install anything on your device other than the original Whatsapp.
Widgets for multitasking, cleaning Whatsapp memory and other third-party applications that require the right to synchronize with contacts and messenger conversations slow down Whatsapp in almost 100% of cases, and in the worst case, steal user data by taking screenshots and uploading data to unknown servers. Avoiding such a "leak" is easy - you should not install anything on your device other than the original Whatsapp.
Sending a chat by mail
One of the critical vulnerabilities of Whatsapp was its basic function. Through "sending a chat" you can upload all correspondence with any user to any mail. The program does not ask you to confirm this action - just select the addressee, and a letter with a complete archive of messages will be sent to his email inbox. Deleted text files will not be there, but the title will contain a phrase from the developers: "Messages and calls are end-to-end encrypted. Third parties, including WhatsApp, cannot read your messages or listen to calls.