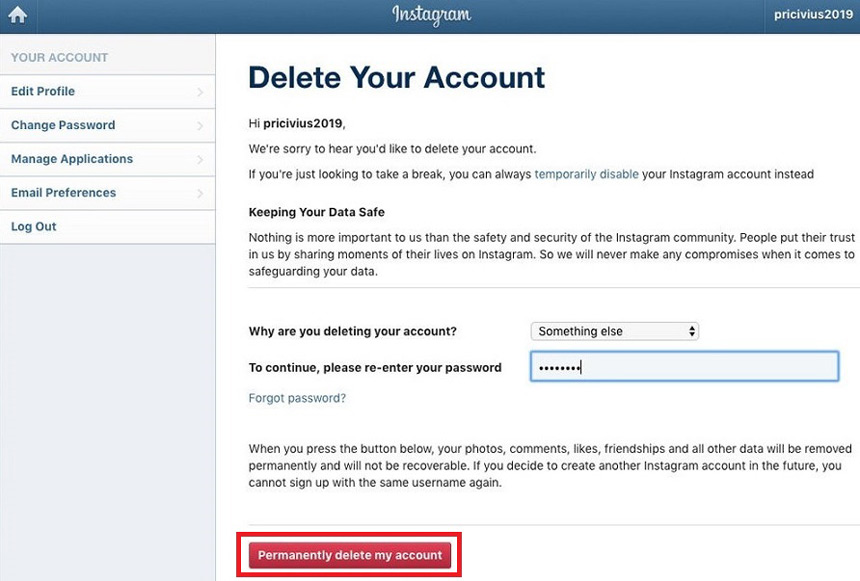
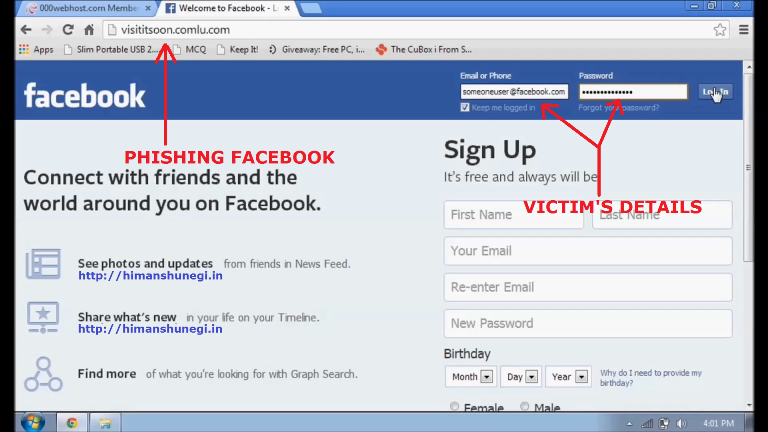
How to hack group in facebook
How to hack a group or a page on Facebook? It's simple - I saw it with my own eyes!
It might be just me watching too many criminals with the investigative journalists as leading characters. Perhaps I felt that otherwise it would not work. Anyway, I spent a large chunk of the last year inside a Facebook group responsible for hacking other groups and accounts.
With my own eyes, I witnessed the permanent removal of numerous Facebook pages and saw popular groups being hacked.
They often belonged to my friends’ friends. I didn’t warn you. I couldn’t do it, I am very sorry.
The members of a Polish Facebook group called “Putin’s Bastards” (so-called бп), which was a group engaged in Internet “trolling” . They probably already knew that there was an infiltrator among them.
So at one point, I decided that I had seen enough of their content.
I didn’t pass another “inner test”, and decided to end my private investigation.
I did it all in order to work out their ways and develop a suitable defense plan that I can share with you. Unfortunately, before I managed to take decent screenshots of more serious actions of the group (a day after a popular Polish newspaper called “Gazeta Wyborcza” published an article about the group), the group admins created private chats to catch the infiltrator.
Instead of waiting, I could’ve watched them as they went. Unfortunately, I didn’t think about it back then – I was busy analysing the events and the group disappeared in one day, breaking up into several smaller groups (the abovementioned private chats).
Why do people hack other people’s groups?Before the described above happened, I was really fed up with what I was experiencing after a few months of being a member of that group. The content wasn’t religiously inappropriate, racist or hateful. It was however wrong on all kinds of levels – I felt deeply disgusted with the horrible memes posted by the members.
I couldn’t explain to myself why or how anyone could derive any pleasure from such activities.
Taking over a vegan group to write about meat, a weight loss group to call names those who share their progress, or a group for moms. Endlessly entertaining, isn’t it?
Especially when the new administrator is one of the bullies and the former administrator … well, they didn’t even realize that they are no longer the administrator.
I was speechless seeing so much hatred resulting purely from boredom and the lack of anything better to do.
Seriously, they didn’t even do it for money as some online trolls have done before.
The group members posted tons of stupid content (including the memed) but sometimes they would openly ask each other about harming new people:
Do you know any losers who have nice groups cause I am stuck at home doin’ nothin’ today?
(* I will explain the meaning of the quote in the following paragraphs)
Who hacks Facebook groups?After I read all this rubbish, one more conclusion came to my mind.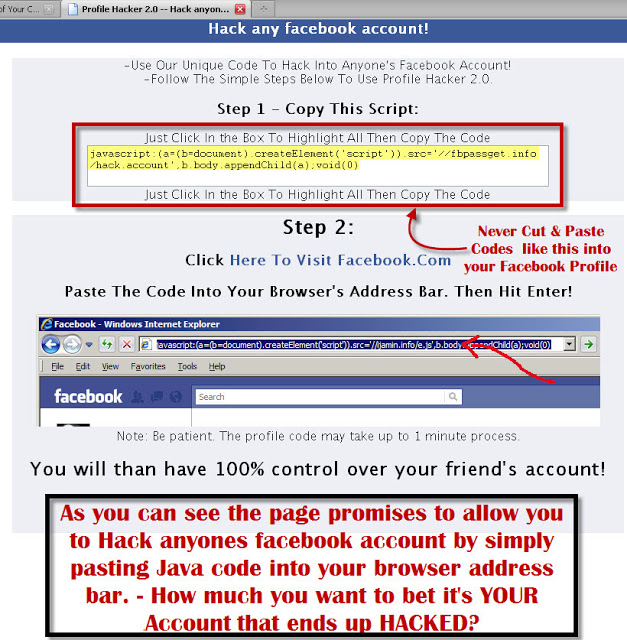 Of course, it was impossible to verify the members of the group. Everyone used false names, and when it turned out that someone allowed someone logged in to a real account to enter the group, it ended up with a permanent ban (I didn’t know that before the infiltration – so I assume my personal data was super helpful here, too).
Of course, it was impossible to verify the members of the group. Everyone used false names, and when it turned out that someone allowed someone logged in to a real account to enter the group, it ended up with a permanent ban (I didn’t know that before the infiltration – so I assume my personal data was super helpful here, too).
Due to false identities, it was impossible to figure out who the Putin’s Bastards really were or what they did. However, this could be deduced from their behavior and their language. The vast majority of them turned out to be middle school or high school students who were looking for ways to kill boredom and build a sense of belonging. How were such young people able to carry out serious hack attacks?
What does the attack look like?Basically, to hack a group or a Facebook page is not that complicated at all. And with the right piece of code, even a newbie could do it.
The mechanism itself is quite simple, and we sometimes let them hack our pages with our curiosity and recklessness.
The same pattern of infecting user’s devices with a prepared virus is known for years. Professionals call it social engineering.
Once widespread in emails, today adapted to the Facebook reality – based on people’s curiosity, it collects its toll every day, especially in conjunction with automated scripts written by the Internet “thieves”, with whom some of you might have had an encounter.
The mechanism is as simple as effective – after clicking on the link included in a very tempting message, we call the code that does all the work for us – it is able to change passwords, ownership of your Facebook group, to manage rolls on Facebook pages and advertising accounts, check your card details, photos or even message content.
Wystarczy sugerujący komentarz, aby wzbudzić ciekawość ofiary i skłonić ją do kliknięcia w link. Nie dajmy się zmanipulować!Sometimes it may be a good old conversation leading to the photos of naked breasts being sent out, or a simple photo we are supposedly tagged in.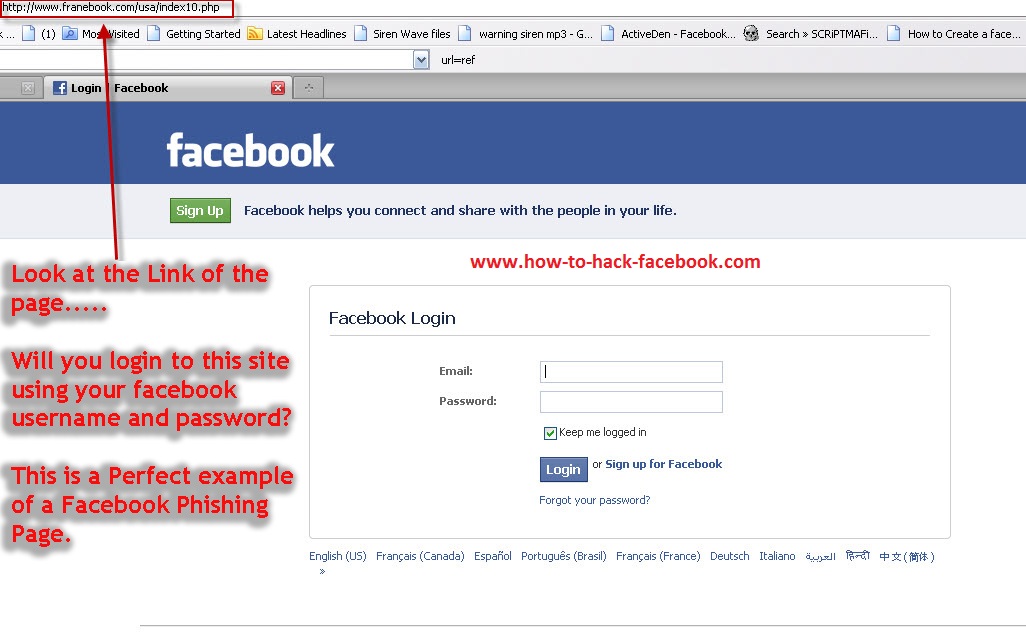
We used to be pursued by hackers to paste such codes ourselves, but nowadays clicking a link does the job for us.
Very simple and convenient, right?
Po ostatniej fali ataków za pomocą kodów javascript Facebook sam zaczął przestrzegać przed wklejaniem czegokolwiek do konsoli.How to recognize the “attack” and how to successfully prevent it?
Not long after I left the group, I received numerous suspicious friend requests. They looked like this:
It’s nothing more than taking the least resistance path and trying to get me into a conversation that ends with sending me a virus.
Of course, nothing will happen if you accept an invitation from such a stranger. You will also be fine when you talk to them. The most important thing is to stay alert and:
- Do not click on suspicious links. How to recognize them? Basically, any link sent by a stranger should be treated as such. If someone really wants us to see what is happening on a given page, we can always ask for a screenshot via messenger, much safer than following the unknown link.
 If they refuse – it should be an obvious sign for you.
If they refuse – it should be an obvious sign for you. - Do not send them any photos. The photos you take on a daily basis with your smartphone have geotags enabled by default, which surprisingly accurately indicate your geographic location. You never know what they might use it for later.
- Do not send any SMS. Even if you’re asked allegedly by your friend. While a few years ago the way automated scripts conducted conversation was obviously limited and after a short discussion (usually receiving answers in broken English)it was obvious you were talking to a bot, the modern bots not only make a lot of sense but can also use fluent and even fancy language.
The guide listed above isn’t limited to Facebook only,
It also concerns suspicious links inside Facebook groups or comments under our posts.
Before you click on any link, read carefully three times to see if you are sure it leads to http://facebook. com instead of http: //faceboọk.com or to https://youtube.com instead of https://yuo.tube.com
com instead of http: //faceboọk.com or to https://youtube.com instead of https://yuo.tube.com
These are just pre-made variations of popular website addresses, which after entering may look almost identical to the originals, but all actions (including the password entered on them) will be registered on the hacker’s server and associated with your account and data.
This type of attack impersonating someone else or a trusted website, combined with the above-mentioned social engineering is usually extremely effective. Mainly because of our curiosity and carelessness.
After all, we are only human, and as they say – curiosity killed the cat.
To stay safe, we all should consider protecting our social media accounts with additional passwords, double verification, one-time SMS codes, and other tools reducing the chances of becoming a cyber victim.
Facebook Group Hack : How Can I Hack Any Facebook Group | by Rohit Kumar
Let’s come to the point without wasting any time.
Here are the 3 ways, I found for hacking any Facebook group.
- Steal the group by social engineering…
- Hack the admin account and grab the group…
- My attack…
Since most of the users are Beware of social engineering… etc so you can’t target everyone, thus it is not possible to target any group and capture. ☹ ☹
The Bullshit ….. As you know hacking individuals is quite difficult, especially if one has little knowledge about techs.
.
As many of you know that if any group has no Admin or moderator Facebook says, “ This group needs an admin. ”
And if you are a member of that group you can claim yourself as an admin.
I thought, Can I create a situation in which the group has no admin or moderator? And I said yes I can… I can create this situation by disabling all the admins’ and moderators’ accounts simultaneously.
Hmmmmmm, There are several steps to do that (Disabling some Facebook accounts simultaneously), But I’m not going to explain it here!
I wanted to go further and I created a new test group, added some members to it including my personal account as a member and I disabled the account (which was the admin of the group), I entered the group with my personal account and I saw that Facebook is saying that this group needs an admin….
So one thing I confirmed is that they have made it in such a way that if a group has not any admin available (no matter if it has admin but his/her account is in a temporarily disabled state), it will be available for new admin claim….
I just claimed myself as an admin…….
Since a disabled account can be recovered by submitting government proof, I recovered my disabled account that was previous admin but wtf I saw there, my previous admin account (Group creator and previous admin) was not acting as an admin anymore to the group after my account recovery, This gave a conclusion to me that using this attack I can target any group… I didn’t stop, I targeted a 1.3 million members group that had 4 admin and one moderator only, I disabled all 5 accounts simultaneously and took that group. One of the admins of that group recovered his account but he found himself no more admin…. he came to me (as I was the new admin of his group) and started begging… I returned back his group and then I thought I should report this issue to Facebook.
I just reported it to Facebook for adding the feature that once a group is being hacked by disabling all the admins and moderators accounts simultaneously, then after recovery of admin account from disabled state he/she will still stay as an admin even after new admin claim has done by me (or any attacker)…
Here is the Initial response . . .
That’s all, they said… it is just an attack which is a misuse of Facebook feature of admin claim when no admin is available. . . Also, he said,“ disabling the users in the manner I described in the report is considered a social engineering attack against Facebook users and infrastructure”…..
I replied to them … I request Facebook for adding the functionality (that is after recovery of the admin account, he/she will still stay as an admin even after a new admin claim by an attacker), they replied…
I understood, they are not going to do it…
So now it’s clear since this issue isn’t related to any software bug, they will not care over it…
Then I closed the report too.
Update (26 August 2019)
And Now This Issue Has Been Fixed By Facebook, so please don’t ask me on my social media accounts to hack or recover any group or page.
Found a way to hack into any Facebook account using a "hole" that is 10 years old
Security Security strategy User Internet Web Services
|
Share
Dangerous Vulnerability
Security researcher Amol Baikar (Amol Baikar) has identified a dangerous vulnerability in Facebook's OAuth authorization protocol. It allows you to access any social network account, as well as other services that are logged in using Facebook. The specialist spoke about this in his personal blog, emphasizing that the described bug has existed for about 9 years.-10 years.
It allows you to access any social network account, as well as other services that are logged in using Facebook. The specialist spoke about this in his personal blog, emphasizing that the described bug has existed for about 9 years.-10 years.
According to Baikar, the problem lies in the implementation of the "Login with Facebook" function, which uses the OAuth 2.0 authorization protocol to exchange authorization tokens between the social network site and other web resources. Thanks to this feature, Facebook account holders can freely use third-party Internet services that provide such an opportunity without additional registration.
The expert explained that an attacker could deploy a special website to intercept OAuth traffic and steal tokens that provide access to visitors' Facebook accounts. As a result, the "hacker" will be able to send messages, post in the feed, change account information, and perform any other actions on behalf of the victim. nine0005
In addition, the cybercriminal gets the opportunity to establish control over accounts on third-party resources, which can be used for authorization using Facebook. Many web services now provide this opportunity, including the social network Instagram, streaming services Netflix and Spotify, and the dating app Tinder.
Many web services now provide this opportunity, including the social network Instagram, streaming services Netflix and Spotify, and the dating app Tinder.
Company response
Baikar informed Facebook about the discovered vulnerability on December 16, 2019. To his surprise, the company acknowledged the presence of the "hole" on the same day. What's more, she immediately released a fix. nine0005
Security researcher Amol Baikar found a way to hack any Facebook account using a decade-old flaw
However, later the researcher found errors in its implementation, about which he notified the company representatives on January 3, 2020. On January 10, Facebook eliminated the shortcomings identified by Baikar.
On February 20, the expert received a $55,000 reward from Facebook as part of the Bug Bounty program for his work.
Facebook incidents and leaks
Over the past few years, Facebook has repeatedly found itself at the center of various scandals due to a careless attitude to the privacy of social network users, as well as the presence of serious vulnerabilities in other company products.
Vladimir Arlazarov, Smart Engines: Personal data should be treated like a state secret
ON
For example, in July 2019, a vulnerability was discovered in the mobile version of Instagram (part of the Facebook ecosystem) that allowed an attacker to reset the password for absolutely any account and gain full control over it. nine0005
In April 2019, Facebook was convicted that when registering on a social network, a user's password to his email address could be requested if the client's email service causes some suspicions in the system. The list of "suspicious" was also the popular Russian service "Yandex.mail".
In March 2019, it was discovered that tens of thousands of company employees could have access to other people's Facebook and Instagram pages, since the passwords of hundreds of millions of users were stored on the company's servers in clear text. Moreover, the social network officially recognized the existence of a problem only after a third-party information security specialist with connections within the company spoke about it on the Internet. nine0005
nine0005
In September 2018, Facebook acknowledged the data breach of over 50 million account holders. The cause of the hack was a serious vulnerability in the Facebook code. It was eliminated as soon as possible, and law enforcement agencies were notified about the incident.
Business told how Russian IT solutions were implemented with grant support
IT industry support
In November 2018, it became known that the social network was unable to repel cybercriminals, as a result of which personal information about more than 120 million network users ended up in the hands of hackers. The data was put up for sale at a price of 10 cents per profile. nine0005
Between 2007 and 2014 The social network transmitted information about its users to the British analytical company Cambridge Analytica, as a result of which 87 million people were affected.
- How to comply with Presidential Decree No.
 250 "On Additional Information Security Measures"
250 "On Additional Information Security Measures"
Dmitry Stepanov
What to do if someone tries to access your Facebook or Instagram
A notification pops up on the smartphone screen: "We detected an unusual login attempt from Rio de Janeiro, Brazil." The first reaction is panic, especially if you live in, say, Vladivostok. What could it be? System failure? Or is someone from the other side of the world really encroaching on your account?
There is no way to panic in such a situation - this will only play into the hands of the burglars. So that you can remain calm and survive this incident with minimal losses, we will arm you with knowledge: we tell you what the matter might be and how to act. nine0005
What could have happened
First, let's figure out how a stranger could get access to your account at all. There are several options here.
Data leak and wildcard attack
A third party site where you registered might have been leaked. Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on. nine0005
Having acquired a list of logins, e-mail addresses and passwords, scammers use them for a substitution attack, that is, they try to enter stolen credentials on many sites. Unfortunately, many people set the same passwords to protect their accounts in different services - this is what criminals are counting on. nine0005
Alternatively, your Facebook or Instagram credentials may have been leaked from the app you trusted them to. For example, in June last year, thousands of passwords from Instagram accounts leaked to the network, the owners of which used the Social Captain service to buy likes and followers. It turned out that he did not encrypt customer data, and anyone could get access to it. It is reasonable to assume that many users of the service have since experienced hacking attempts.
Phishing
It may also be that some time ago you fell for phishing, and your login with a password fell into the hands of scammers directly. They clicked on some link, and on the page that opened, very similar to the Facebook or Instagram login screen, they entered their credentials. So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
So they ended up with the criminal. For example, most recently, our experts discovered a phishing campaign in which victims were lured to phishing pages by the threat of blocking their Facebook account due to copyright infringement.
Password theft
Your password could have been stolen by malware you picked up somewhere. Many Trojans have a built-in keylogger, a program that registers keystrokes on the keyboard. All logins and passwords that the victim enters, the keylogger directly passes into the hands of attackers.
Access token stolen
Someone may have stolen your access token. So that you don't have to enter a password every time you log into Facebook or Instagram, it saves a small piece of information needed to log in to your computer, which is called a token or access token. If an attacker steals the current token, he will be able to log into the account without a username and password. nine0005
Tokens can be stolen in different ways. Sometimes this is done through vulnerabilities in Facebook itself - for example, in 2018, attackers were able to get access tokens to 50 million Facebook accounts. Also, attackers can use browser extensions to steal tokens.
Also, attackers can use browser extensions to steal tokens.
Login from someone else's device
It is possible that you logged into Facebook or Instagram from someone else's device - at a party, in an Internet cafe, in a hotel lobby, and so on - and did not log out after that. Or, for example, they forgot to log out of their account on a device that they had already sold or donated. Now someone has discovered your oversight and logged into your account. nine0005
False alarm (phishing again)
Your account may not have been hacked at all, but they are trying with a fake suspicious login notification. This is the same phishing that we talked about above, but a slightly different version of it. Instead of the threat of blocking, scammers can use fake suspicious login notifications with a link to phishing sites similar to the login page. Attackers expect that the victim in a panic will go to a fake site and enter their username and password there. nine0005
And what to do?
We have sorted out the possible causes, now it's time to act. To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
To get started, log into your account - but in any case not through the link from the notification (as we already know, it can lead to a phishing site), but through the mobile application or by entering the address in the browser manually. If the password does not match and you can no longer log into your account, refer to the detailed instructions on what to do if your account has already been hijacked, which we published earlier.
If you are still allowed into your account, go to your account settings and verify the authenticity of the notification. For each social network, the path to the desired settings item will be different - see how this is done on Facebook and Instagram. Then go to the “Account Logins” section: if there are no suspicious entries there, then everything is in order, and the message about the hack was still phishing. nine0005
If you really see a suspicious one in the list of logins to your account, then it's time to hurry up to take protective measures - timely actions will help soften the blow:
- Log out of your account on all devices.
 On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings. This will reset the access tokens.
On Instagram, you will have to manually end each session in menu Account Logins . And on Facebook, this can be done with a single click in the Security and login section in the settings. This will reset the access tokens. - Make sure that the correct phone number and email address are specified in the account settings: attackers could change the data so that the link or code to change the password is sent to them. If they managed to do this, change it back to yours. nine0067
- Set a new password that is strong and one that you don't use anywhere else. If you're not sure you can remember it, save it in a password manager. By the way, at the same time the program will help you come up with a reliable combination.
- Turn on two-factor authentication to make it harder for attackers to break into your accounts, even if they know your password.
- After that, be sure to check all your devices with a reliable antivirus to make sure that they are free of malware.